Pirate video identification method and system
A technology of pirated video and identification method, applied in the field of video retrieval and comparison, can solve problems such as instability, inconsistent video time, easy jitter, etc., to achieve the effect of improving precision and accuracy, solving rights protection issues, and improving recognition rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
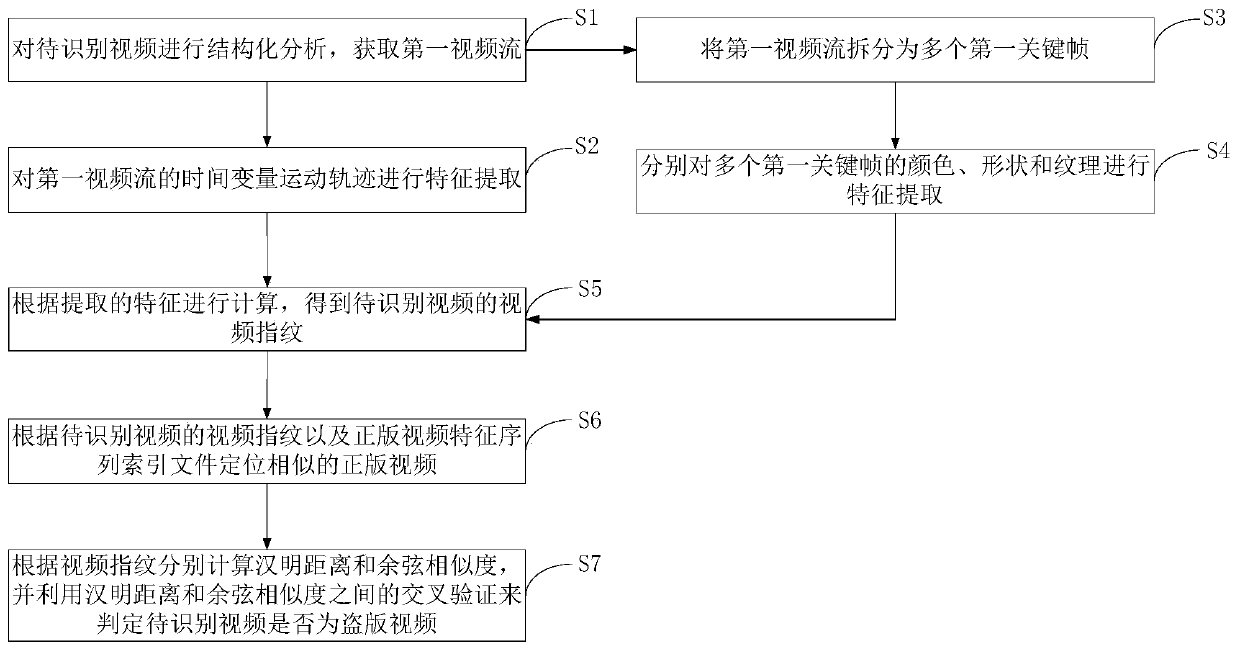
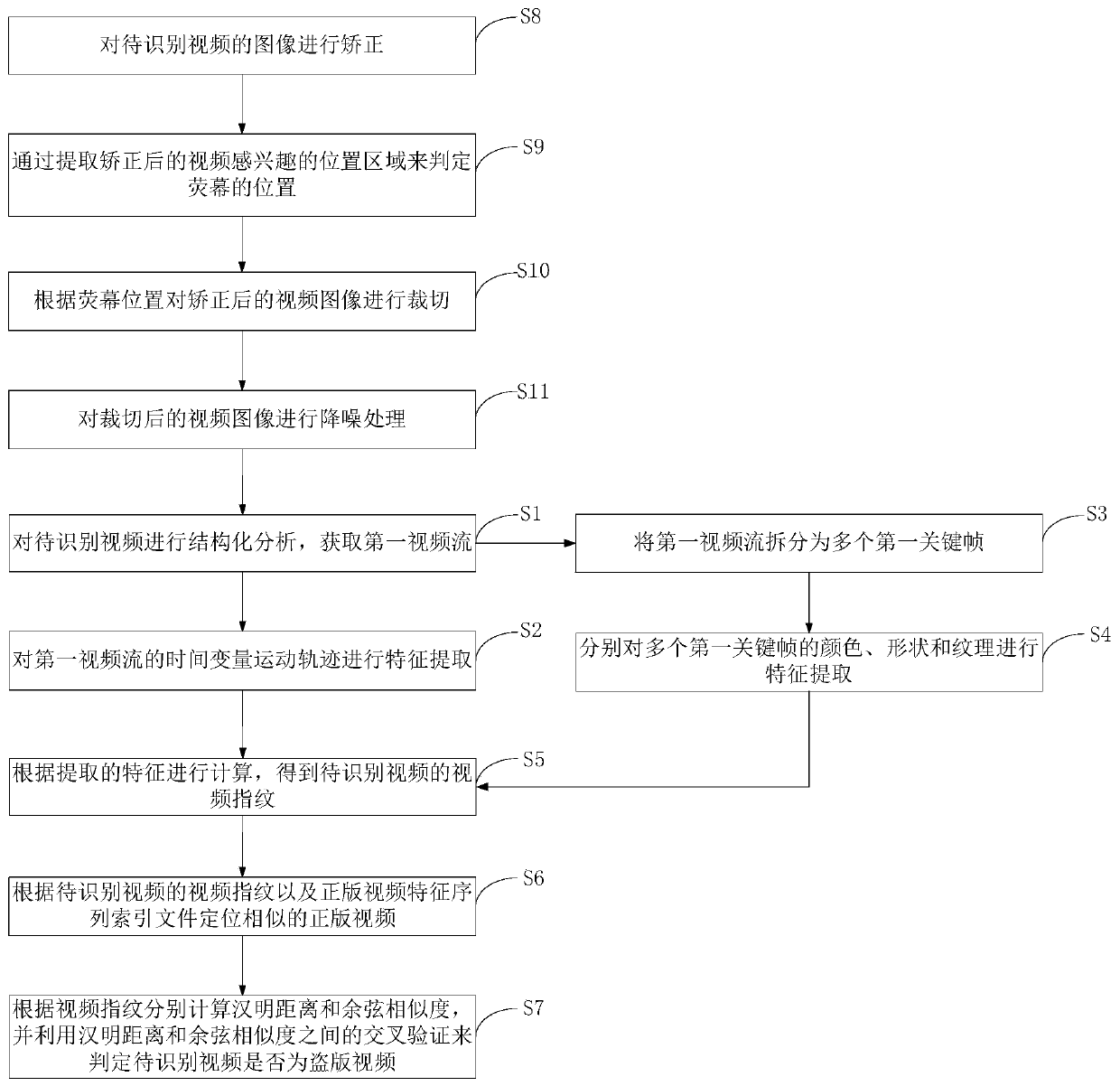
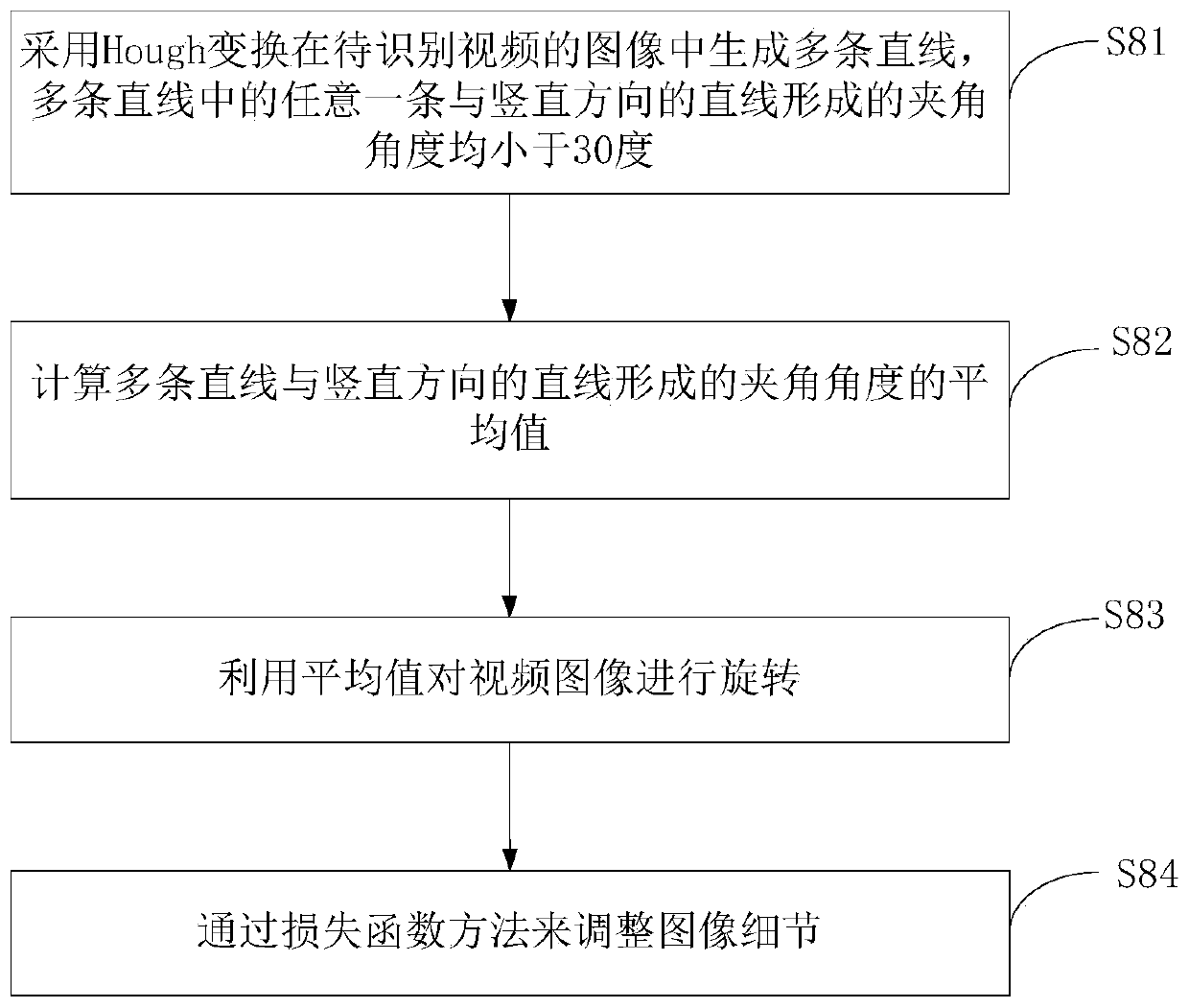
[0030] This embodiment provides a pirated video identification method, such as figure 1 As shown, it mainly includes the following steps:
[0031] Step S1, performing structural analysis on the video to be identified to obtain the first video stream;
[0032] Step S2, performing feature extraction on the time variable motion track of the first video stream;
[0033] Step S3, splitting the first video stream into a plurality of first key frames;
[0034] Step S4, performing feature extraction on the color, shape and texture of multiple first key frames respectively;
[0035] Step S5, calculate according to the feature extracted in step S2 and step S4, obtain the video fingerprint of the video to be identified;
[0036] Step S6, locating similar genuine videos according to the video fingerprint of the video to be identified and the genuine video feature sequence index file;
[0037] In step S7, the Hamming distance and the cosine similarity are respectively calculated accor...
Embodiment 2
[0085] This embodiment provides a pirated video identification system, such as Figure 8 As shown, it mainly includes: a first video stream acquisition module 30, which is used for structural analysis of the video to be identified, and obtains the first video stream; a first feature extraction module 31, connected with the first video stream acquisition module 30, for The time variable motion track of the first video stream carries out feature extraction; The first key frame splitting module 32 is connected with the first video stream acquisition module 30, and is used to split the first video stream into a plurality of first key frames; Two feature extraction modules 33, connected with the first key frame splitting module 32, are used to carry out feature extraction to the color, shape and texture of a plurality of first key frames respectively; the first video fingerprint calculation module 34, respectively with the first feature Extraction module 31 is connected with second...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com