Environment-based vulnerability scanner
A vulnerability scanner and environment technology, applied in the field of environment-based vulnerability scanners, can solve the problem of not having illegal content detection and black chain detection technology, and achieve the effect of improving accuracy and strengthening web page detection standards.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
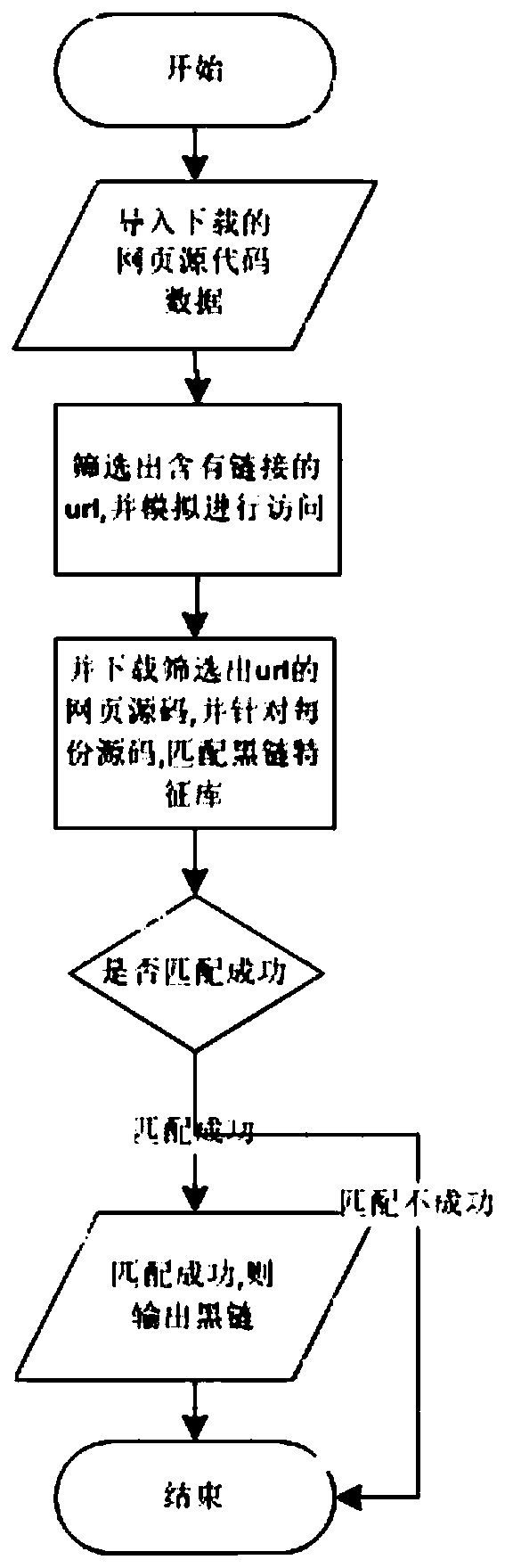
[0032] The environment-based vulnerability scanner provided by the preferred embodiment of the present invention includes the following steps:
[0033] Step A: Custom creation of the violation feature database S 1 , import the Uniform Resource Locator URLx of the existing black chain violation characteristics;
[0034] Step B: Receive the external access request and the URLy, and download the web page file H of the access request 1 ;
[0035] Step C: Create a regular expression REGEX in web page format;
[0036] Step D: Customize and create a web page link feature database S 2 ;
[0037] Step E: Get the web page file H 1 Use the regular expression REGEX(URLz) to detect whether the URLz containing the link on the website conforms to the webpage format;
[0038] Step F: If it is detected by REGEX (URLz) that the URLz conforms to the web page format, then check whether the URLz exists in the violation characteristic database S1 by querying the violation characteristic datab...
Embodiment 2
[0040] In this embodiment, on the basis of Embodiment 1, preferably, the steps B, C and D include the following steps:
[0041] StepBCD 1 : Get the downloaded web page file H 1 The source code of the web page;
[0042] StepBCD 2 : Utilize the regular expression REGEX to match the URLz with the webpage link, and store it in the webpage link characteristic database S2.
[0043] StepBCD 3 : By linking the feature database S from the webpage each time 2 Obtain the URLz of each webpage link in turn, and access the URLz of the webpage link through simulation;
[0044] StepBCD 4 : By accessing the webpage link URLz, download the source code of the webpage of the current link and find out whether the source code of the webpage of the link contains illegal characters.
[0045] StepBCD 4: If it is judged that the webpage link URLz is a black link, the violation feature database S 1 Continue to save the URLz; if it is judged that the webpage link URLz is not a black link, the vi...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com