Intelligent information security anti-intrusion system
An information security and anti-intrusion technology, which is applied to the protection of individual input/output registers, instruments, internal/peripheral computer components, etc. the effect of stealing
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
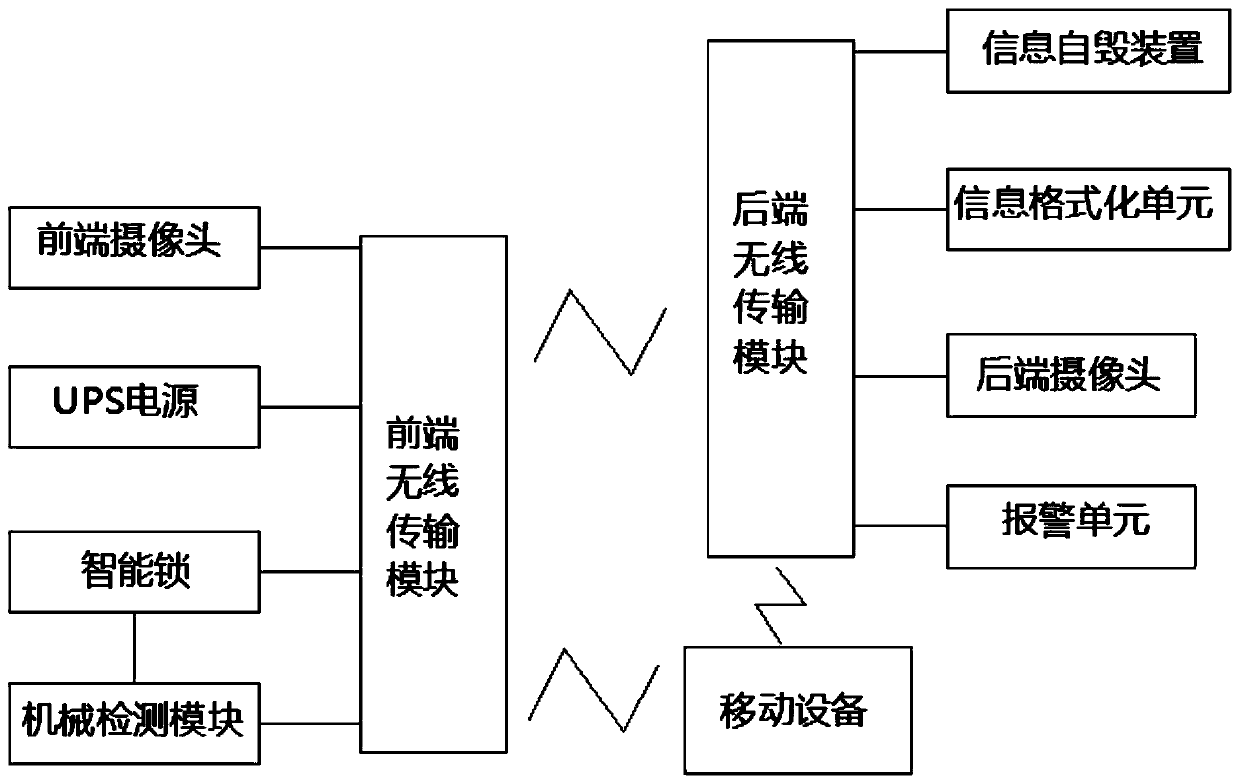
[0029] Example 1: See Figure 1-3 , an intelligent information security anti-intrusion system, comprising:
[0030] Front-end camera: arranged at the front-end smart lock position, used to collect front-end image information;
[0031] UPS power supply: used to provide uninterrupted power supply to front-end equipment;
[0032] Smart lock: used to detect human body information, make a response to open the electronic lock or issue an intrusion command;
[0033] Mechanical detection module: used to detect the security state of the electronic lock, and send an intrusion command when the electronic lock is forcibly destroyed;
[0034] Front-end wireless transmission module: respectively connected to the front-end camera, UPS power supply, smart lock and mechanical detection module, used to send the data transmitted by the smart lock, mechanical detection module and front-end camera to the back-end wireless transmission module and mobile devices;
[0035] Mobile devices: users' m...
Embodiment 2
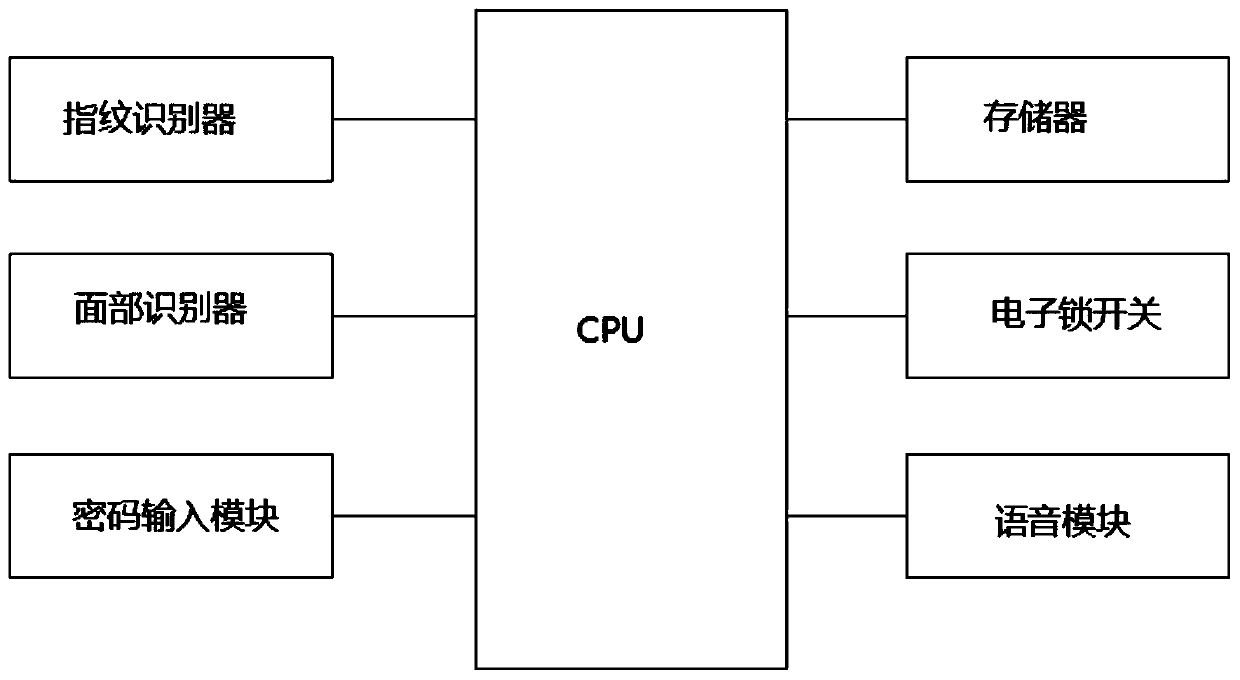
[0042] Embodiment 2, on the basis of embodiment 1, intelligent lock comprises CPU, fingerprint reader, face recognizer, password input module, memory, electronic lock switch and voice module, CPU connects fingerprint recognizer, face recognizer, password respectively Input module, memory, electronic lock switch and voice module. The electronic lock switch can only be turned on when the fingerprint reader, the face recognizer, and the password input module meet the information matching at the same time, and the voice module is used to voice prompt the user for the steps of information verification.
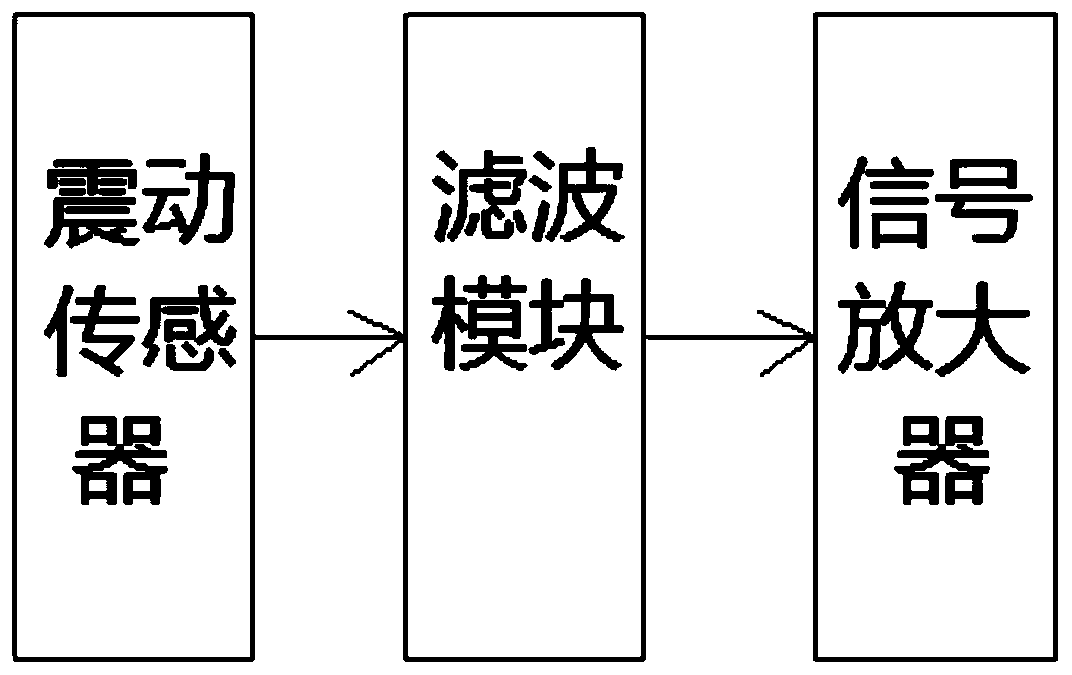
[0043] Embodiment 2. On the basis of Embodiment 1, the mechanical detection module includes a vibration sensor, a filter module and a signal amplifier. The vibration sensor collects the mechanical state signal of the smart lock and transmits it to the filter module. The filter module is also connected to the signal amplifier. When the electronic lock is broken by violence, the mech...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap