Privacy protection method and system supporting range query in data-as-a-service mode
A data service and service model technology, applied in the field of data security, can solve problems such as high space requirements, consumption of computing resources, and high complexity, and achieve the effects of safe data management, data privacy security, and good time efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
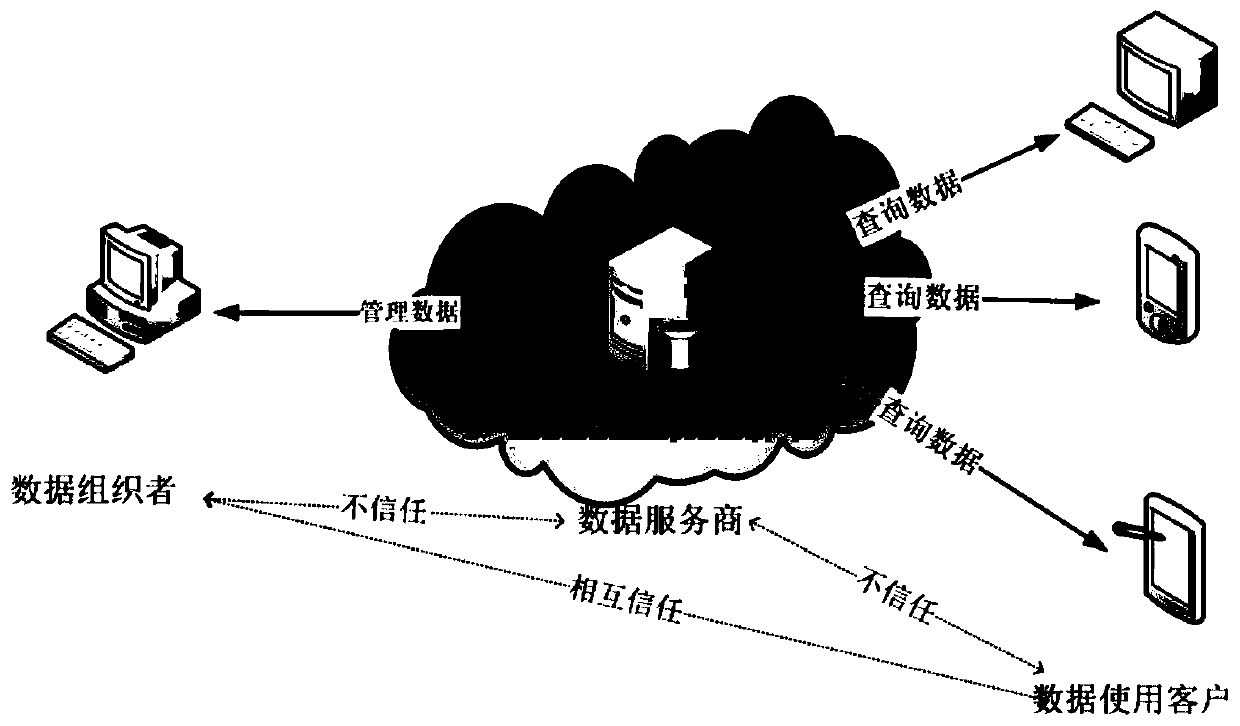
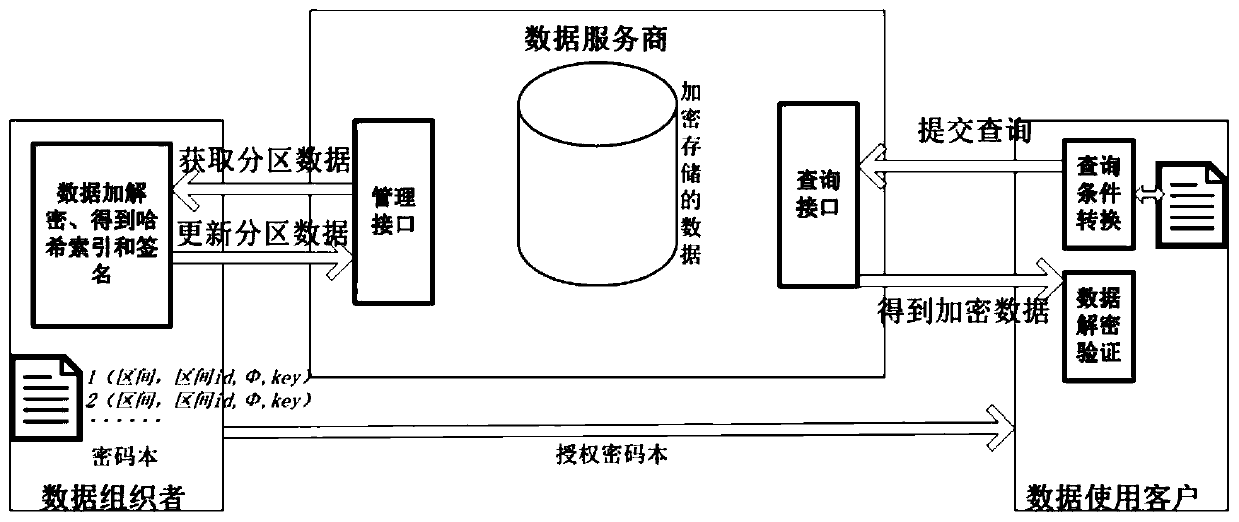
[0039] The main technical points of the present invention include core steps such as value domain division, obtaining hash index, calculating hash signature chain, submitting, querying and verifying data. figure 2 It is an overall schematic flowchart of the solution of the present invention, which is mainly divided into three parts, data organizer, data service provider, and data user. These three parts can also be called data organization end, data server end and data use end respectively. The implementation of each part is described in detail below.
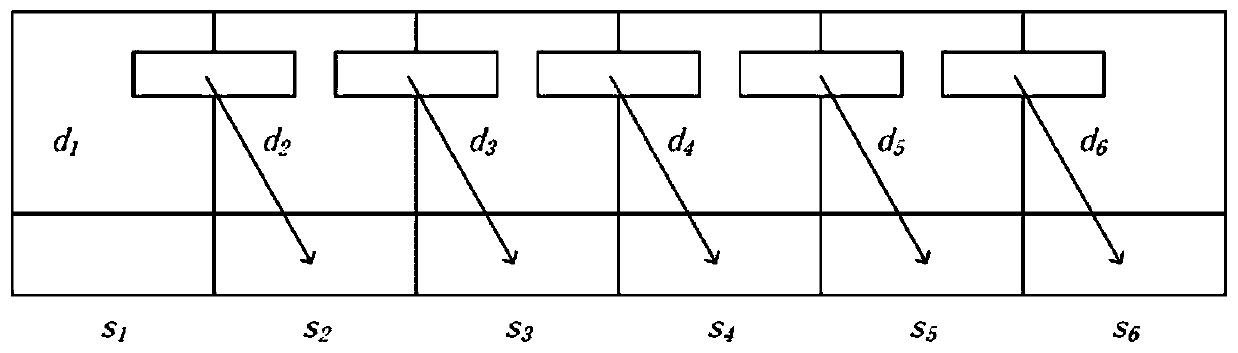
[0040] 1. Value range division.
[0041] The data organizer sets the value range of the index item of the query to be established as U, divides it into N intervals according to its distribution, and assigns an identifier id to each interval i . This identifier can uniquely match a range, and the mapping relationship between each range and its identifier is used as a part of the codebook, and the codebook is owned by the dat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com