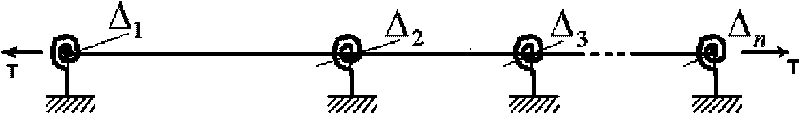Patents
Literature
236results about How to "Strengthen security control" patented technology
Efficacy Topic
Property
Owner
Technical Advancement
Application Domain
Technology Topic
Technology Field Word
Patent Country/Region
Patent Type
Patent Status
Application Year
Inventor
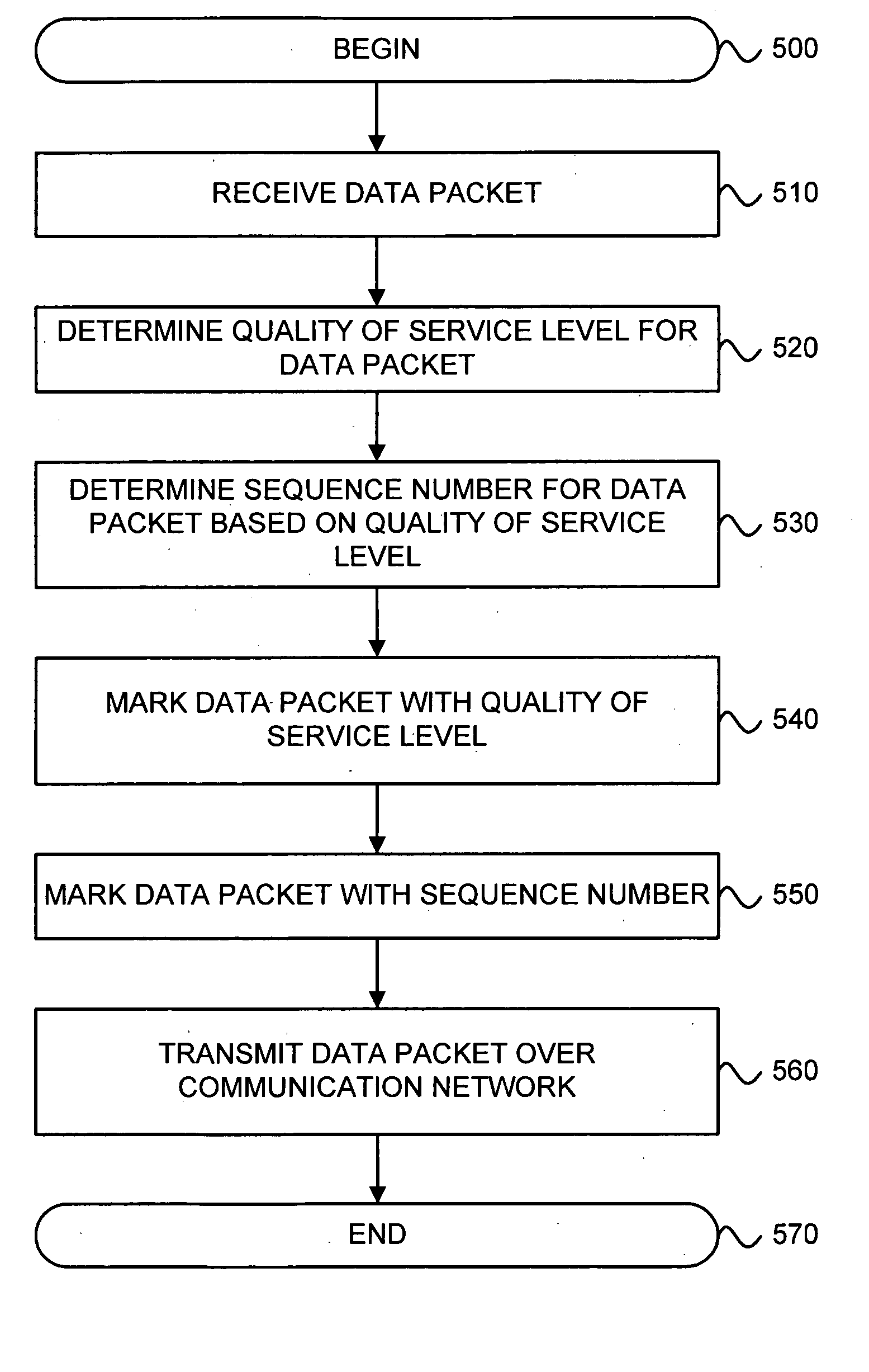
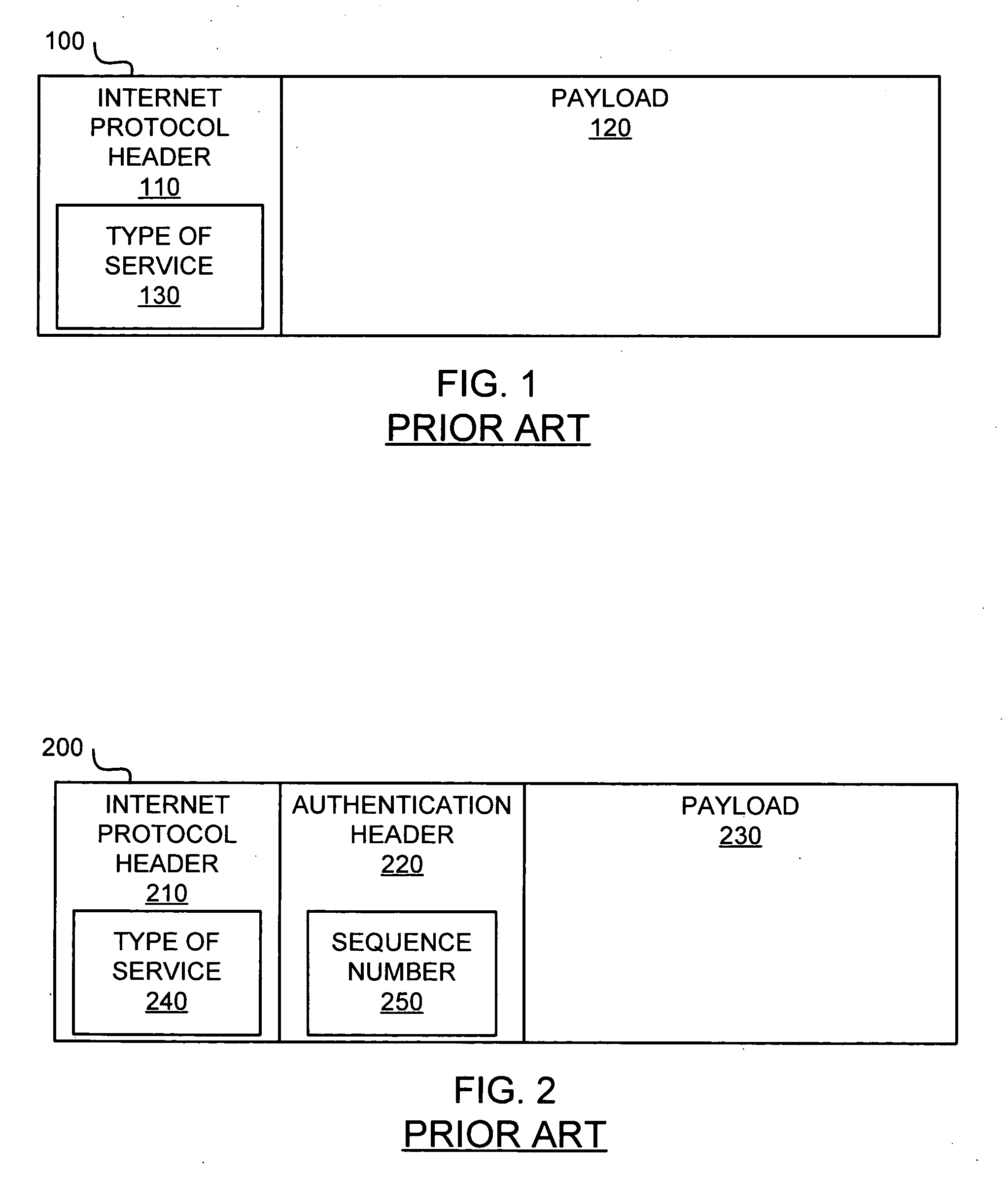
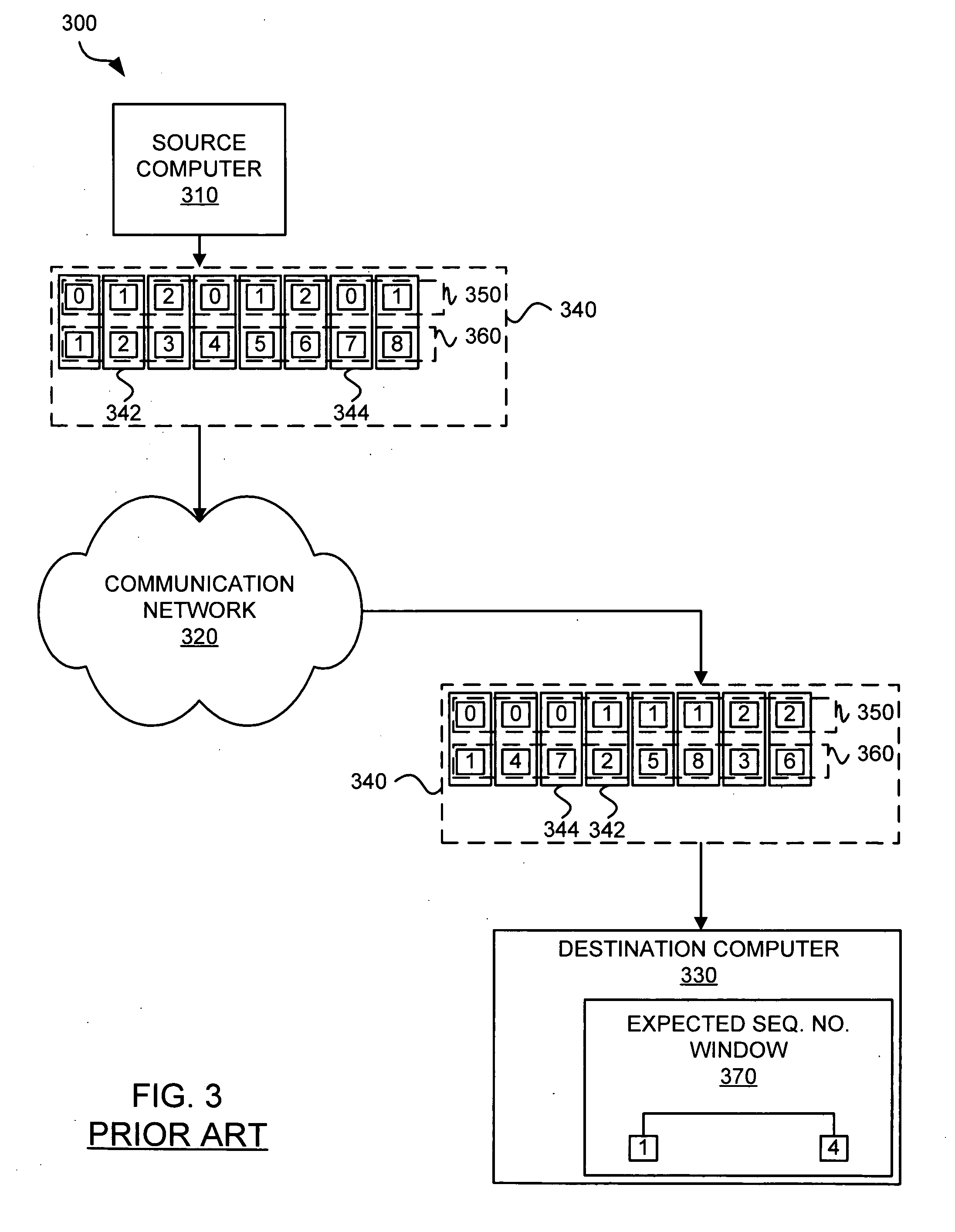
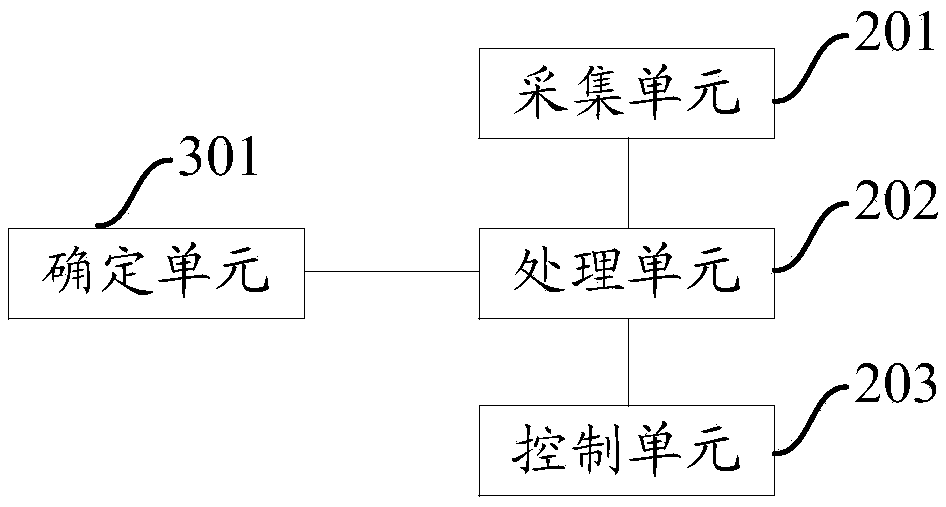
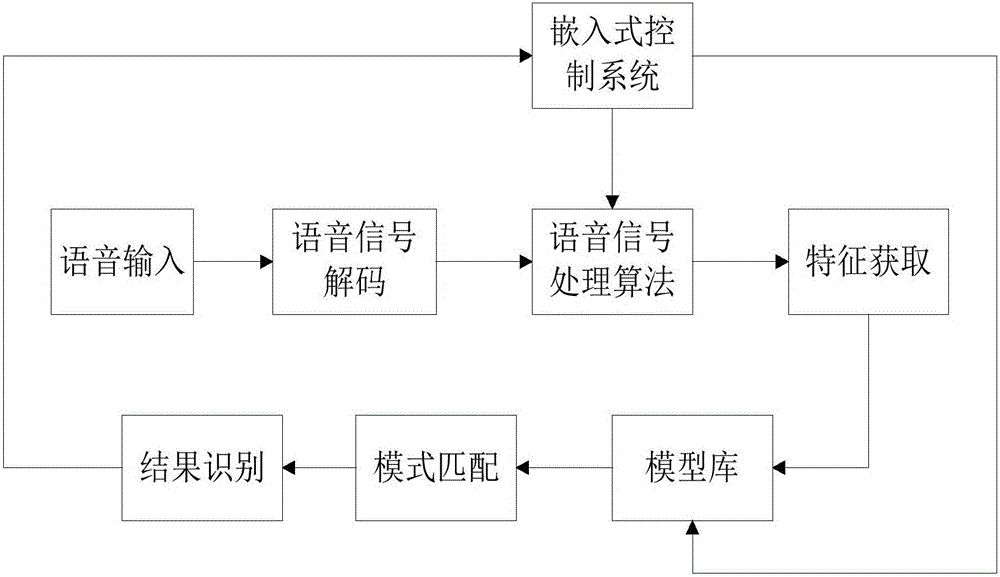
Sequence numbers for multiple quality of service levels
InactiveUS20070115812A1Good communication controlReduce dropError preventionTransmission systemsQuality of serviceData pack
A system for providing communications using sequence numbers for multiple quality of service (QoS) levels includes a first network device. The first network device receives a data packet and determines a QoS level for the data packet. The first network device also determines a sequence number for the data packet based on the QoS level. The first network device then marks the data packet with the sequence number. The system also may include a second network device. The second network device receives from the first network device the data packet marked with the sequence number based on the QoS level of the data packet. The second network device determines an expected sequence number window based on the QoS level of the data packet. The second network device then determines whether the sequence number of the data packet is within the expected sequence number window for the QoS level.
Owner:SILVER PEAK SYSTEMS
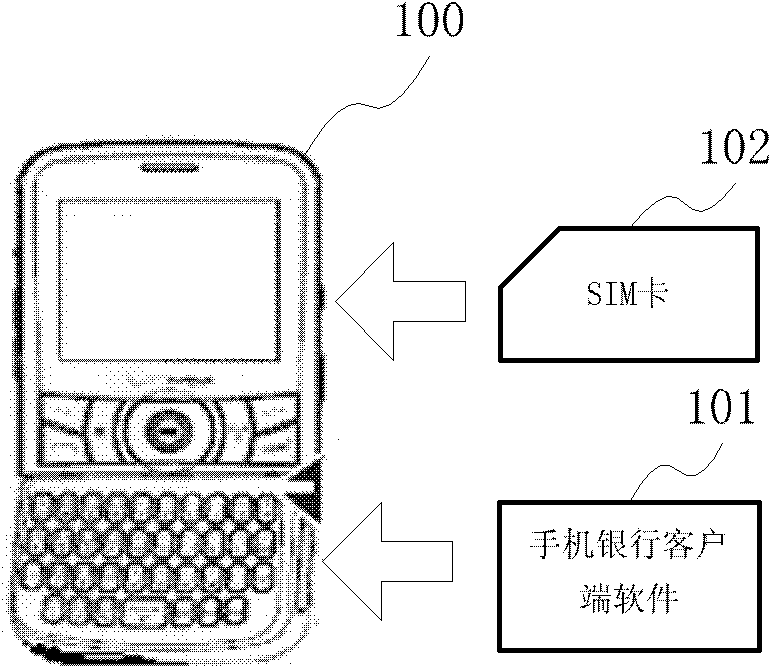
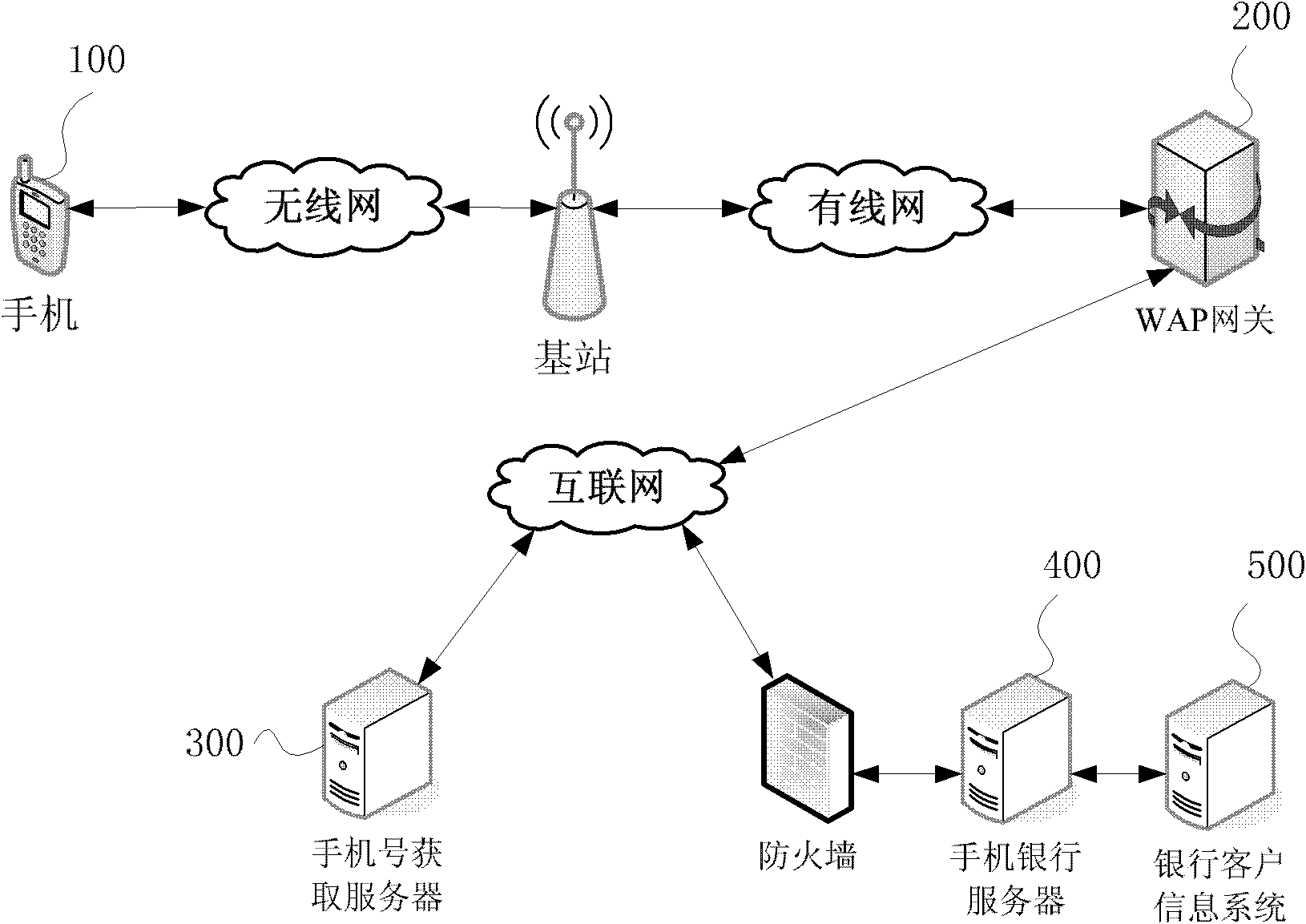
Method and system for authenticating mobile banking client information, and mobile terminal
ActiveCN102143482AImprove securityStrengthen security controlTransmissionSecurity arrangementCustomer informationClient-side
The embodiment of the invention provides a method and a system for authenticating mobile banking client information, and a mobile terminal. The method comprises a mobile banking customer information binding step and a mobile banking login information authenticating step, wherein the mobile banking customer information binding step comprises the following sub-steps of: establishing a binding relationship between mobile phone subscriber identity module (SIM) card information and mobile banking registered customer information, and establishing a binding relationship between mobile phone hardware information and the mobile banking registered customer information; and the mobile banking login information authenticating step comprises the following sub-steps of: acquiring the SIM card information and the hardware information of a login mobile phone, and judging whether the SIM card information and the hardware information of the login mobile phone are matched with the mobile phone SIM card information and the hardware information in the corresponding binding relationship, if so, passing the login information authentication, otherwise, failing to pass the login information authentication. The problem of security of mobile banking system information at the client is solved.
Owner:INDUSTRIAL AND COMMERCIAL BANK OF CHINA
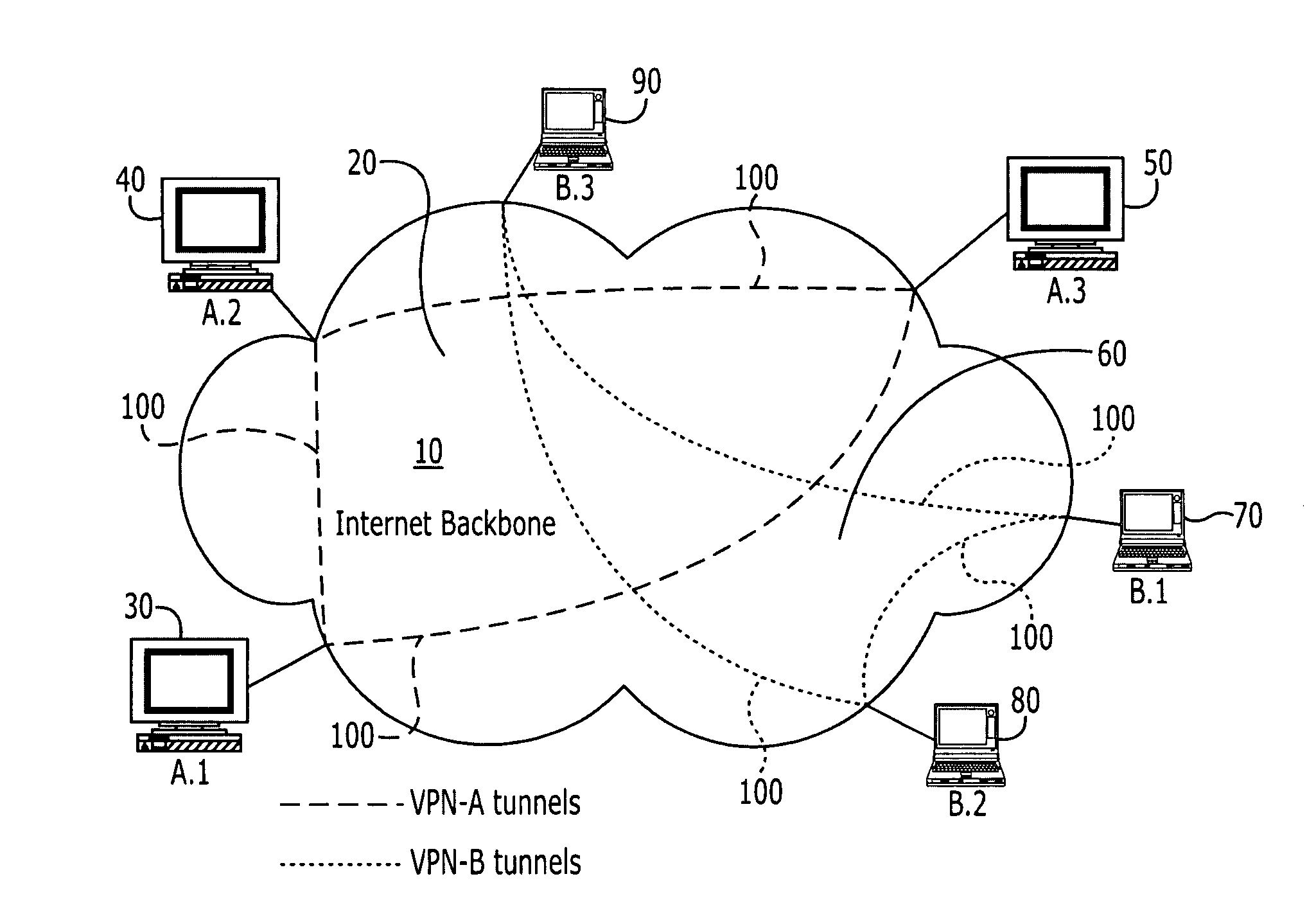
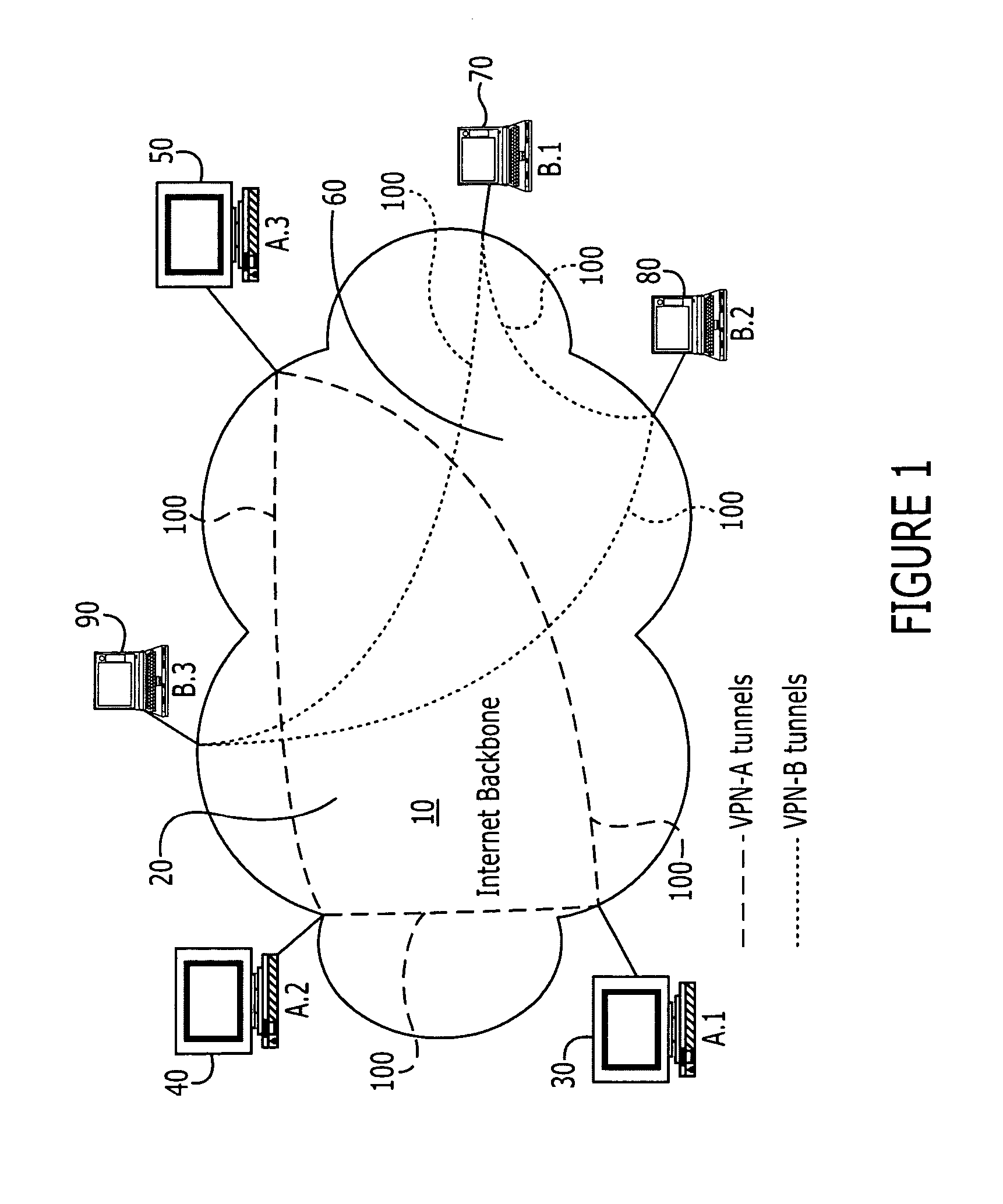
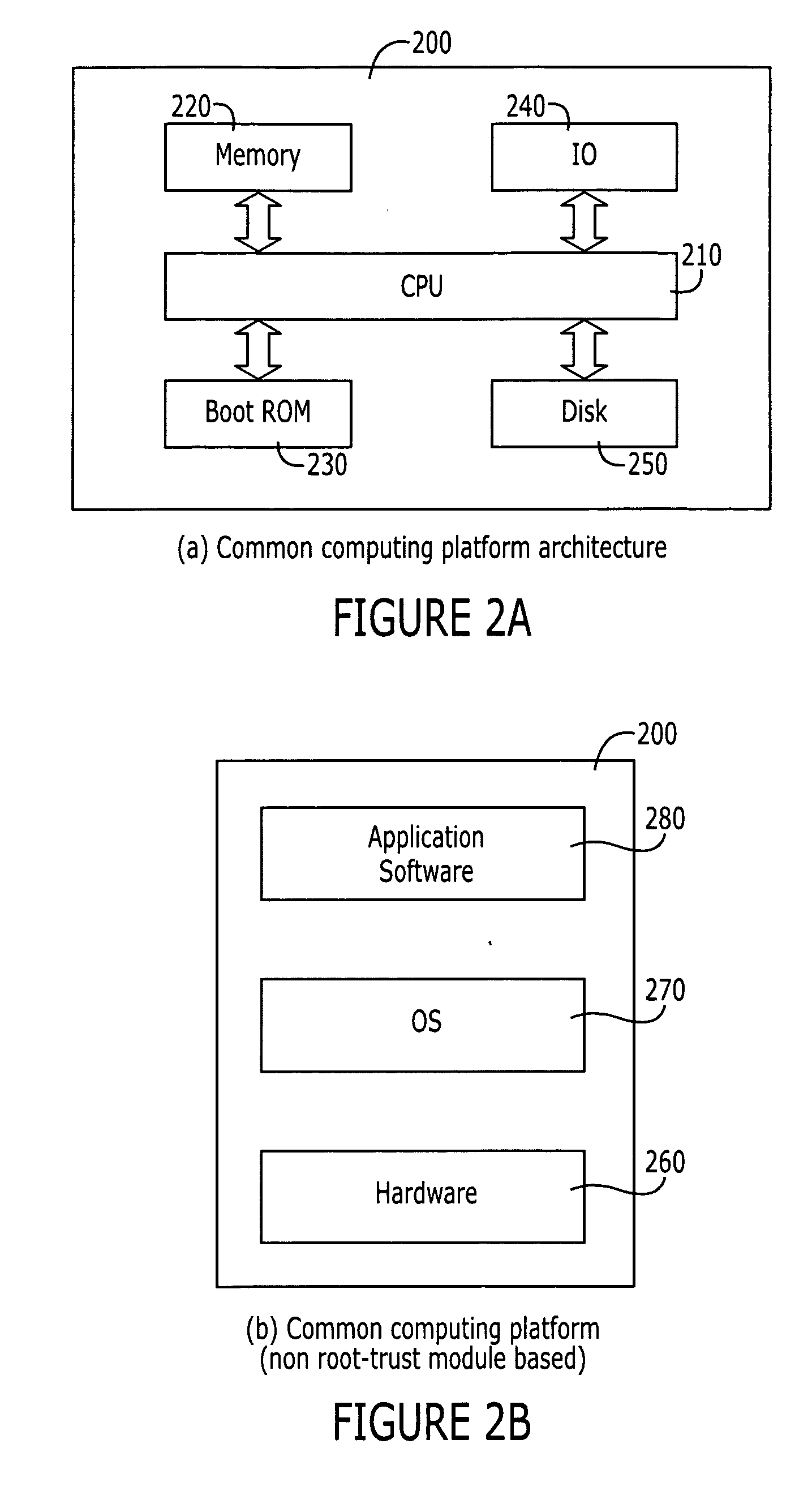
Virtual private network based on root-trust module computing platforms
InactiveUS20050132229A1Improve securityReduce usageDigital data processing detailsUser identity/authority verificationPrivate network
A Virtual Private Network (VPN) system that includes a plurality of terminals, services and servers, part or all of which are root-trust module based platforms. The system provides the management of root-trust based platforms in the network, and enables verification among the platforms.
Owner:NOKIA CORP
Database access agent method and system based on SSL/XML
InactiveCN101848245AStrengthen security controlIncrease flexibilityMultiprogramming arrangementsTransmissionData accessClient-side
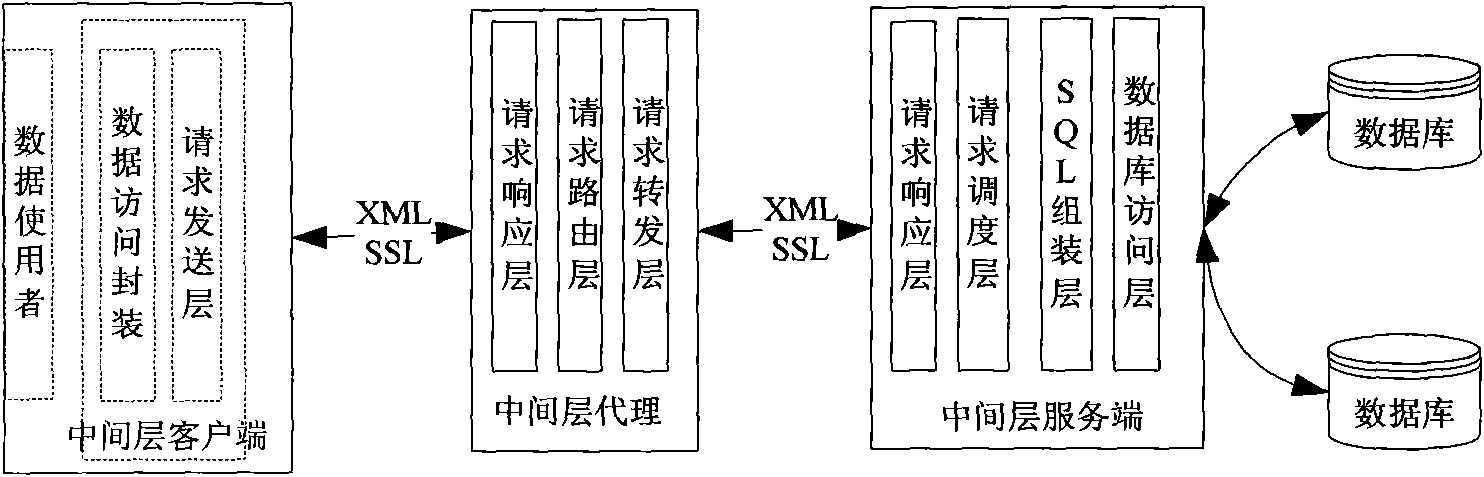
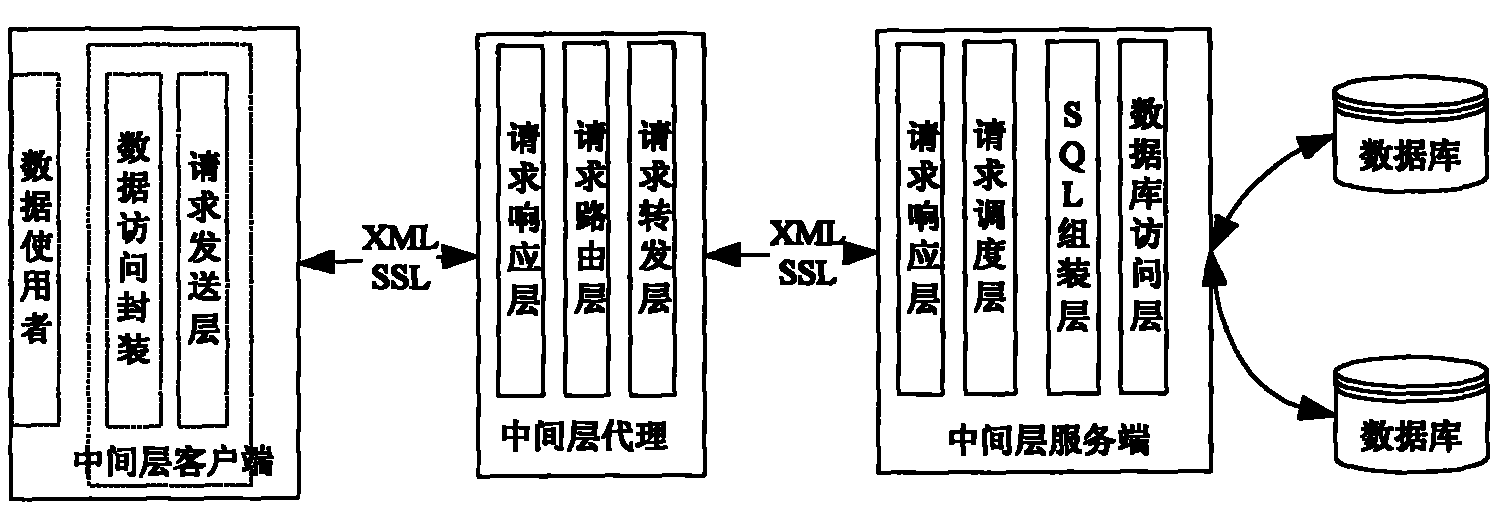
The invention relates to a database access method and a database access system, in particular to a database access agent method and a database access agent system based on SSL / XML. An intermediate layer client is an access operation interface for providing a database record set to a final user, which supports inquiry of the database record set, local cache and navigation and updating, deleting and other operations of the database records; an intermediate layer agent is used for linking the intermediate layer client and an intermediate layer server; the intermediate layer agents can be cascaded with each other to provide a data access channel to the database intermediate layer; the intermediate layer server is used for receiving a database access request, analyzing the database operation according to the request, accessing the database and returning the result of the database operation to the intermediate layer client through the intermediate layer agent. The invention can effectively support the database access over a plurality of hosts.
Owner:DATCENT TECH
Intelligent electronic door control method, system and equipment
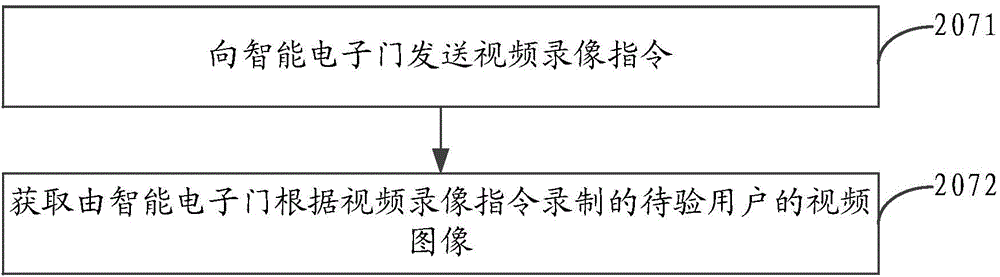
InactiveCN104537746AStrengthen security controlAvoid controlClosed circuit television systemsDigital data authenticationData matchingThird party
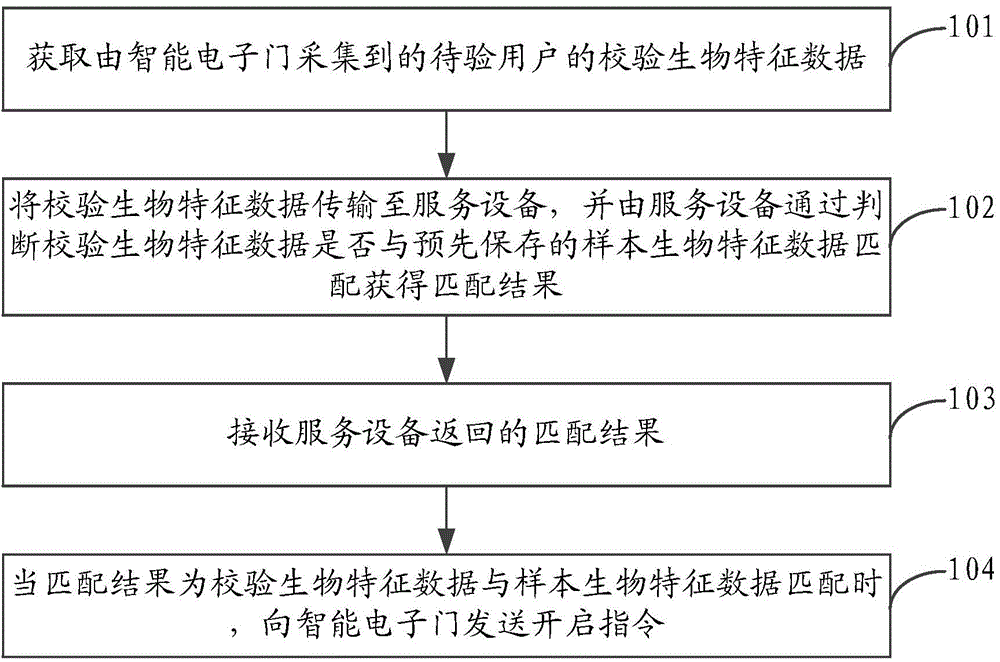
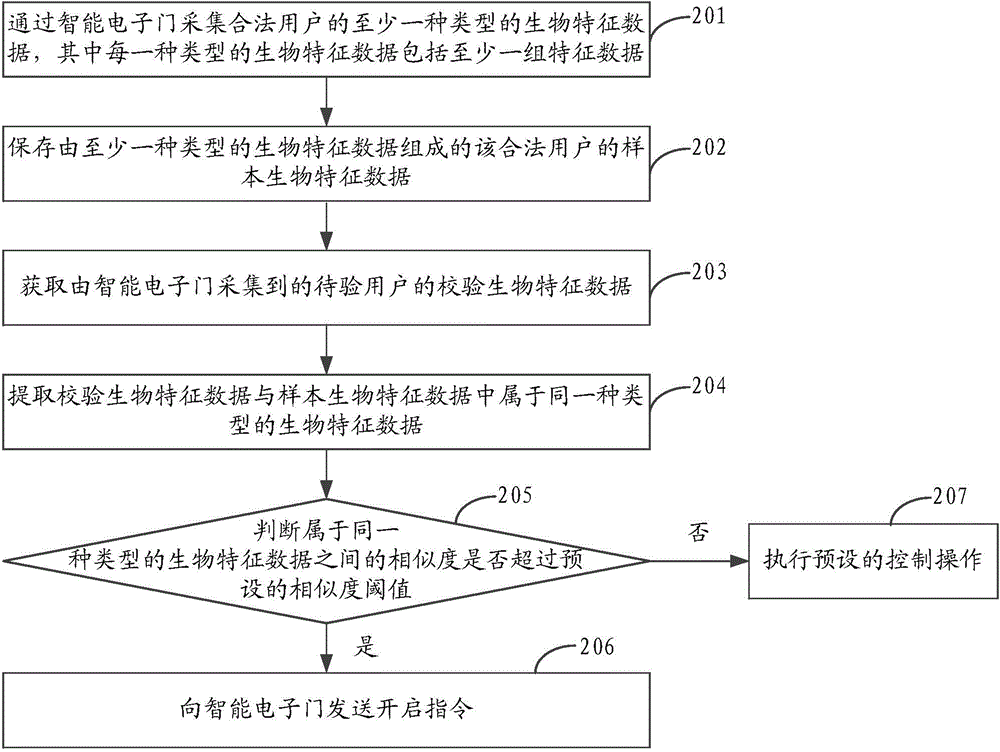
The invention discloses an intelligent electronic door control method, system and equipment. The method comprises the steps that verifying biological feature data of a user to be verified collected by an intelligent electronic door are obtained; the verifying biological feature data are transmitted to service equipment, and matching results are obtained by the fact that the service equipment judges whether the verifying biological feature data are matched with pre-stored sample biological feature data; the matching results returned by the service equipment are received; and when the matching results are matched with the verifying biological feature data and the sample biological feature data, opening instructions are sent to the intelligent electronic door. The biological feature data have lifelong invariance and uniqueness, so that whether a user is legal is identified by comparing of the biological feature data, so that opening of the intelligent electronic door is controlled, verifying through forged identity information by a malign third party can be avoided, and the control safety of the intelligent electronic door can be effectively improved.
Owner:XIAOMI INC
Security control system and security control method for cloud data
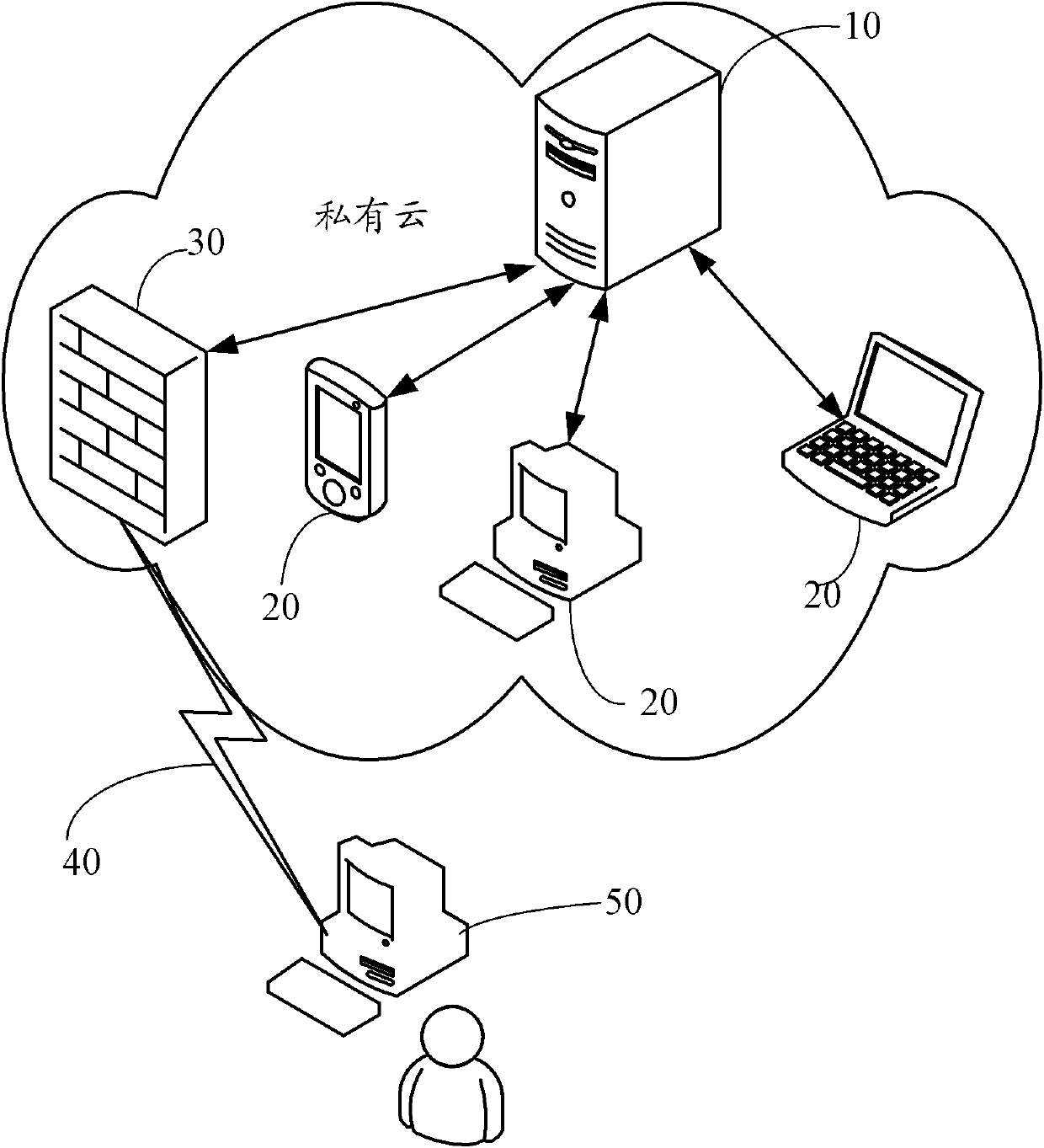
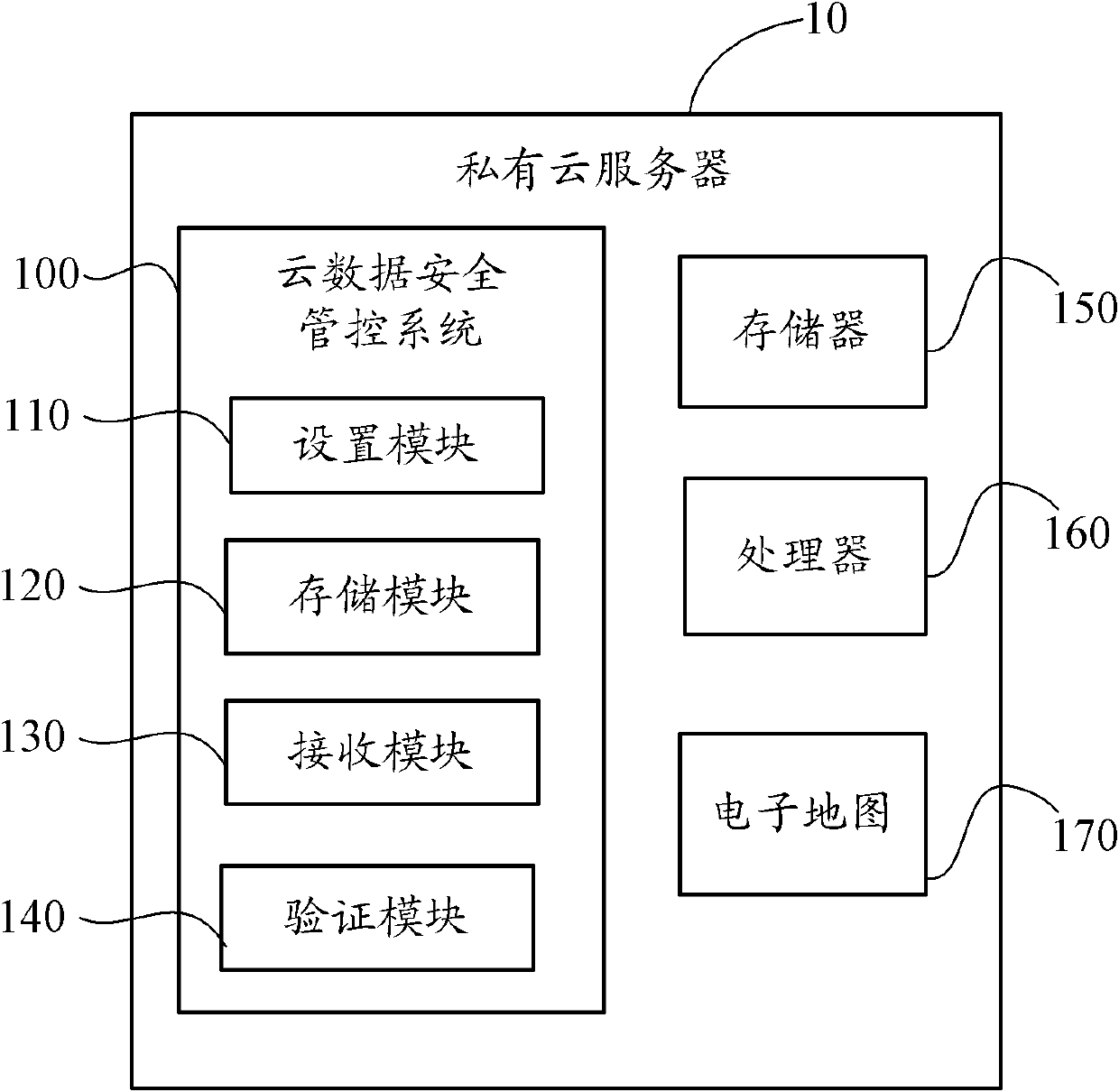
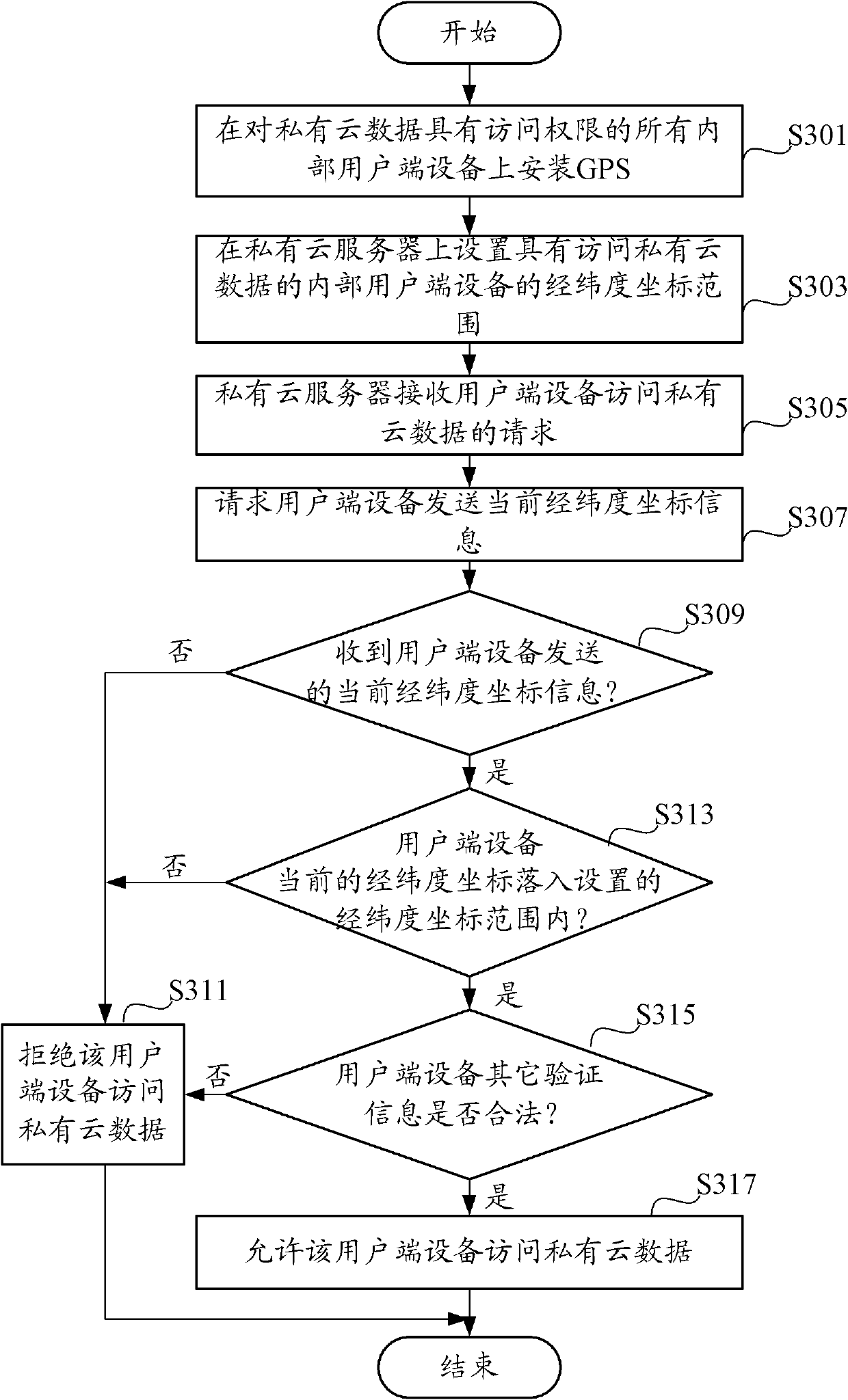
InactiveCN102571703AStrengthen security controlAvoid attackTransmissionCloud dataGlobal Positioning System
The invention provides a security control system for cloud data. The security control system is applied to a private cloud server. Enterprise internal customer premises equipment accesses the private cloud server through an internal network; the private cloud server is used for storing private cloud data; and each internal customer premises equipment is provided with a global positioning system. The security control system can be used for carrying out multiple validation on the client by combining with current longitude and latitude attribute coordinate information and other permission control. If anyone validation of the customer premises equipment is failed, the security control system for the cloud data refuses an access request of the client equipment. If the current longitude and latitude attribute coordinate information and the other permission control information of the customer premises equipment respectively pass the validation, the security control system for the cloud data allows the customer premises equipment to access the private cloud data. The invention also provides a security control method for the cloud data.
Owner:HONG FU JIN PRECISION IND (SHENZHEN) CO LTD +1
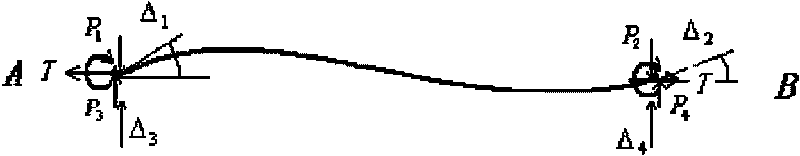
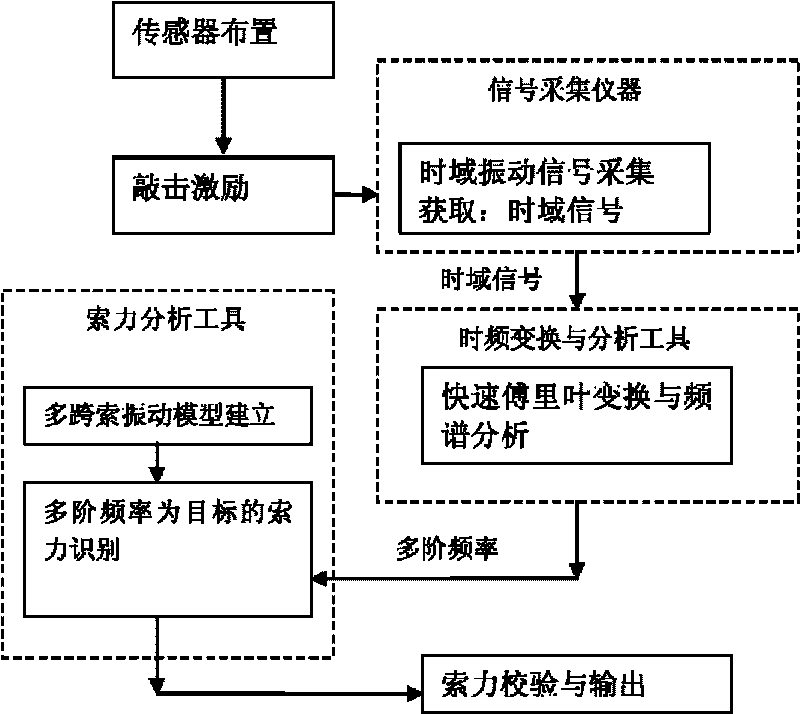
Method for measuring rope force of multi-span steel stay rope by using multi-frequency method
InactiveCN101762346AEasy to operateThe technology implementation process is simple and convenientForce measurement by measuring frquency variationsSpecial data processing applicationsEngineeringMeasurement precision
The invention relates to a method for measuring a multi-span steel stay rope by using a multi-frequency method. The implementation process thereof comprises the following steps: acquiring a time-domain vibration signal, obtaining self vibration frequency passing through n plus 1 order by fast Fourier transform and frequency spectrum analysis, then establishing a frequency characteristic equation with a jack stay rope structural vibration model, establishing a least square method optimization objective function according to the frequency characteristic equation, taking the obtained self vibration frequency of n plus 1 order into the objective function, and obtaining the rope force and the restriction rigidity of the jack stay. The method solves the problem that the traditional dynamic measurement method can be not used for detecting the rope force of the rope with the jack stay, and has simple and convenient technical implementation process, high measurement accuracy of rope force and the like. The method can be widely applied in measurement of rope force of the stay rope with the jack stay in the construction period of a prestress steel structure and measurement of rope force of various restriction ropes in the process of safety maintenance of the engineering.
Owner:BEIJING ACAD OF BUILDING ENG
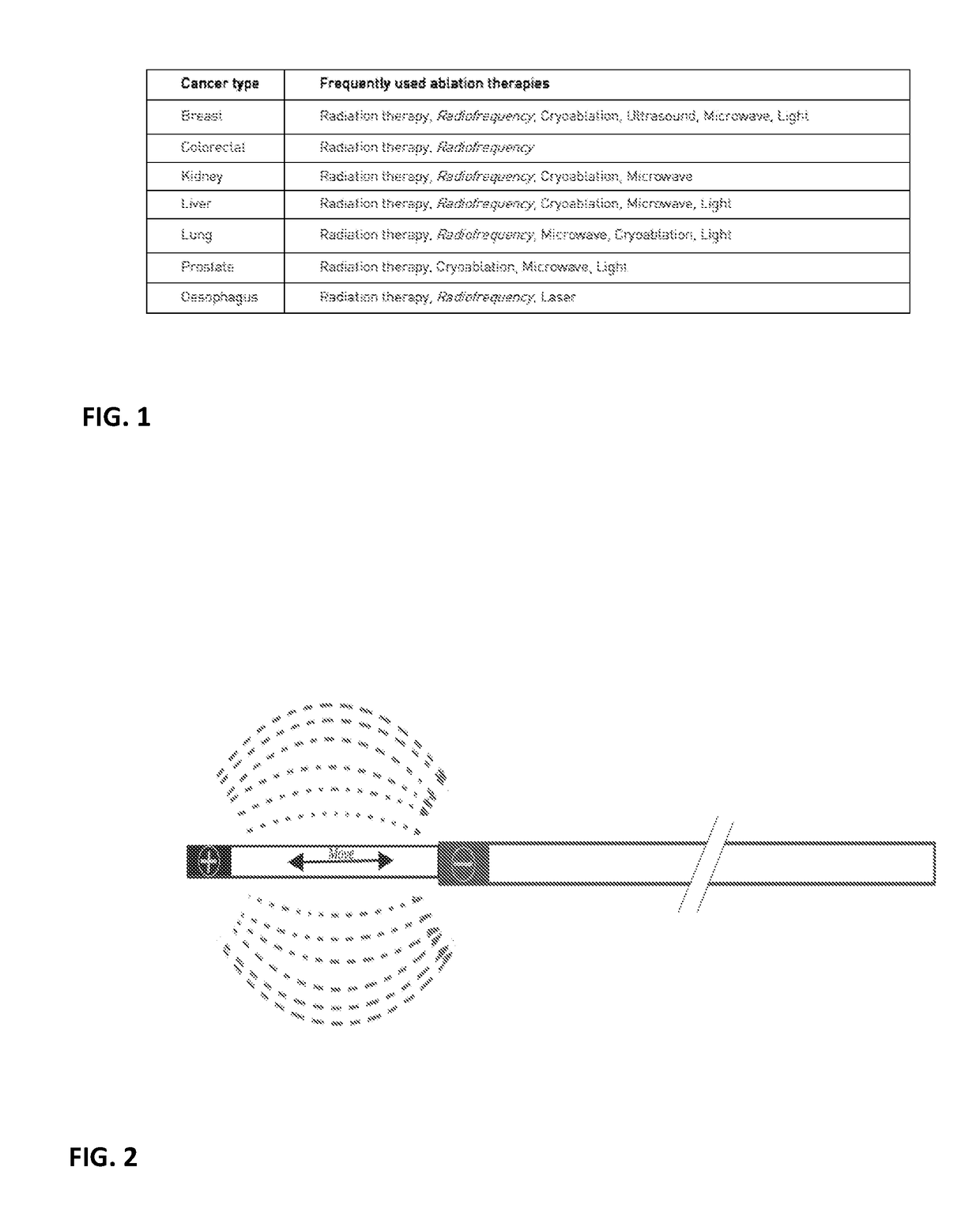
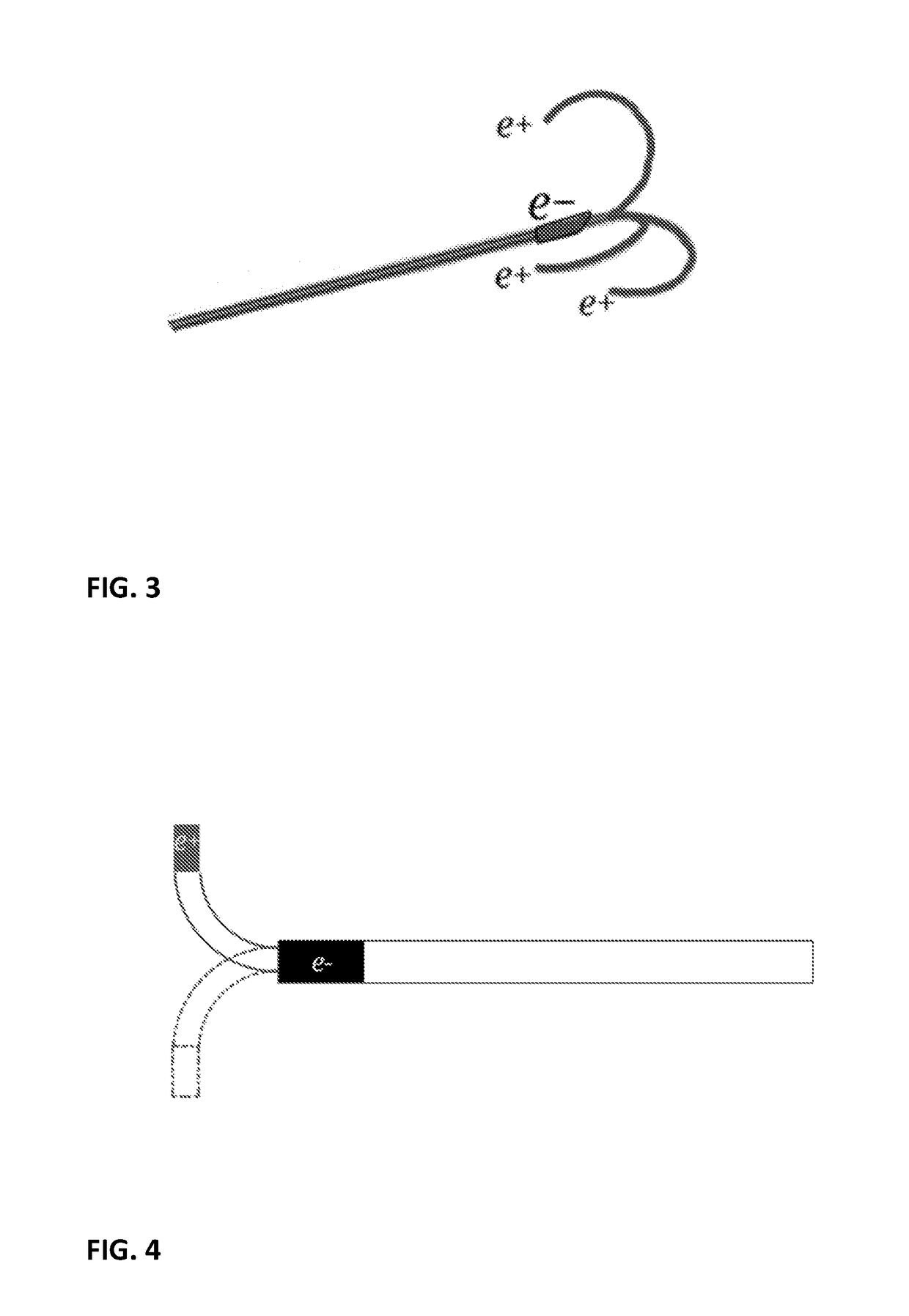
Electromagnetic Tissue Ablation Device
ActiveUS20180280070A1Reduce riskGood curative effectSurgical needlesCatheterBiomedical engineeringTissue ablation
Electromagnetic (EM) tissue ablation device comprising an EM field generator unit, at least two coaxial elongated elements (i.e. an external one and an internal one) and a mechanism for varying the EM field, wherein said internal element is a part of said generator and said mechanism being adapted to vary the EM field for a specific tissue area.
Owner:MYRA MEDICAL SARL +1
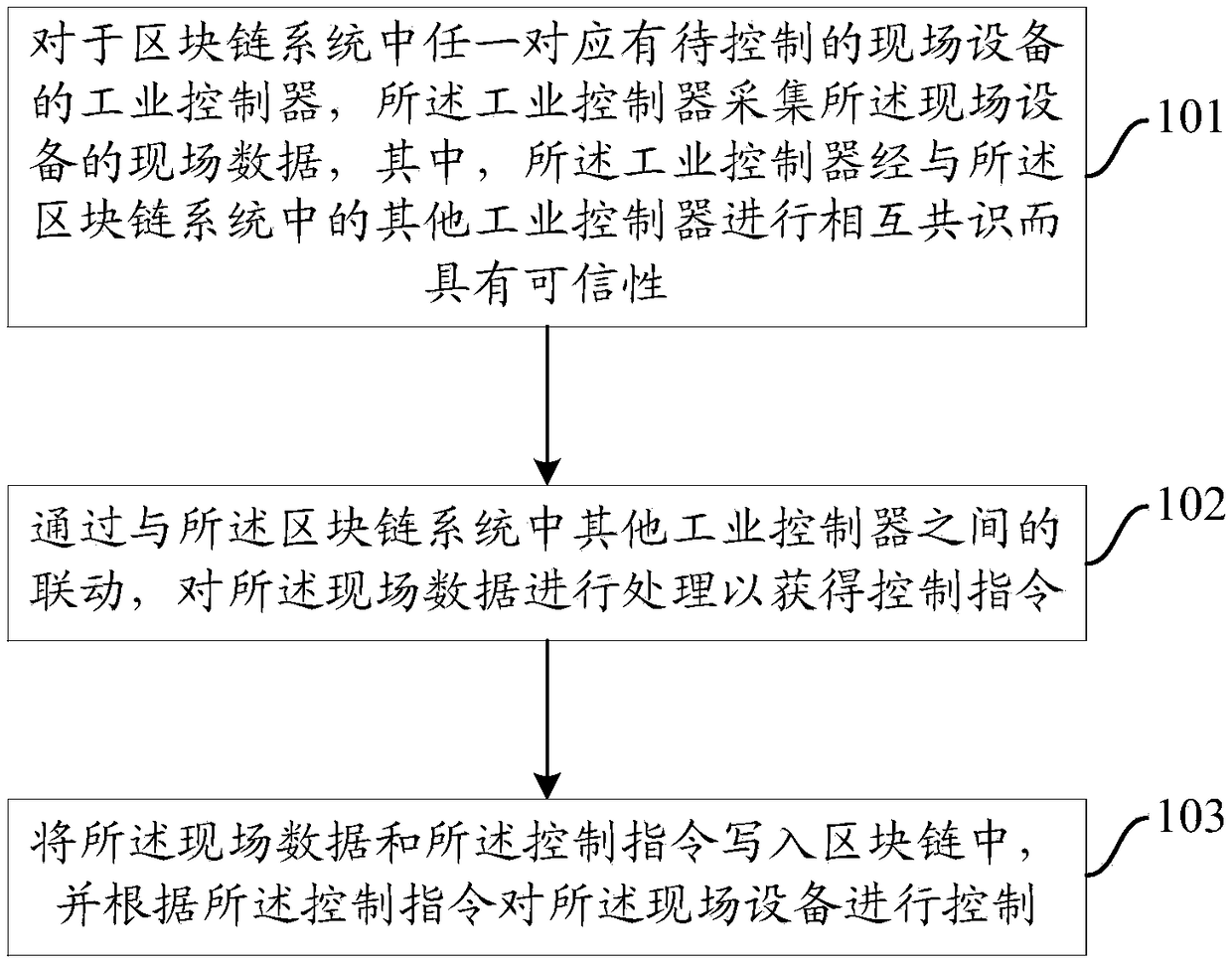
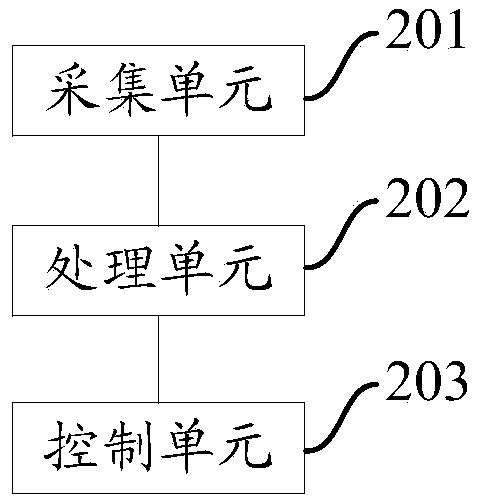
Industrial field device control method, device and system based on edge calculation
ActiveCN109164780AStrengthen security controlNo data communication involvedTotal factory controlProgramme total factory controlEmbedded systemBlockchain
Owner:北京八分量信息科技有限公司
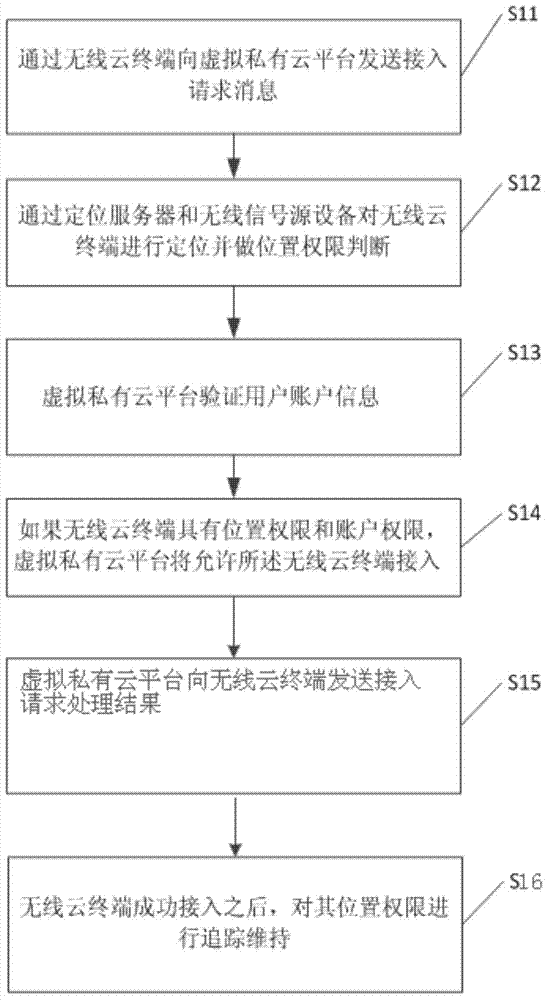
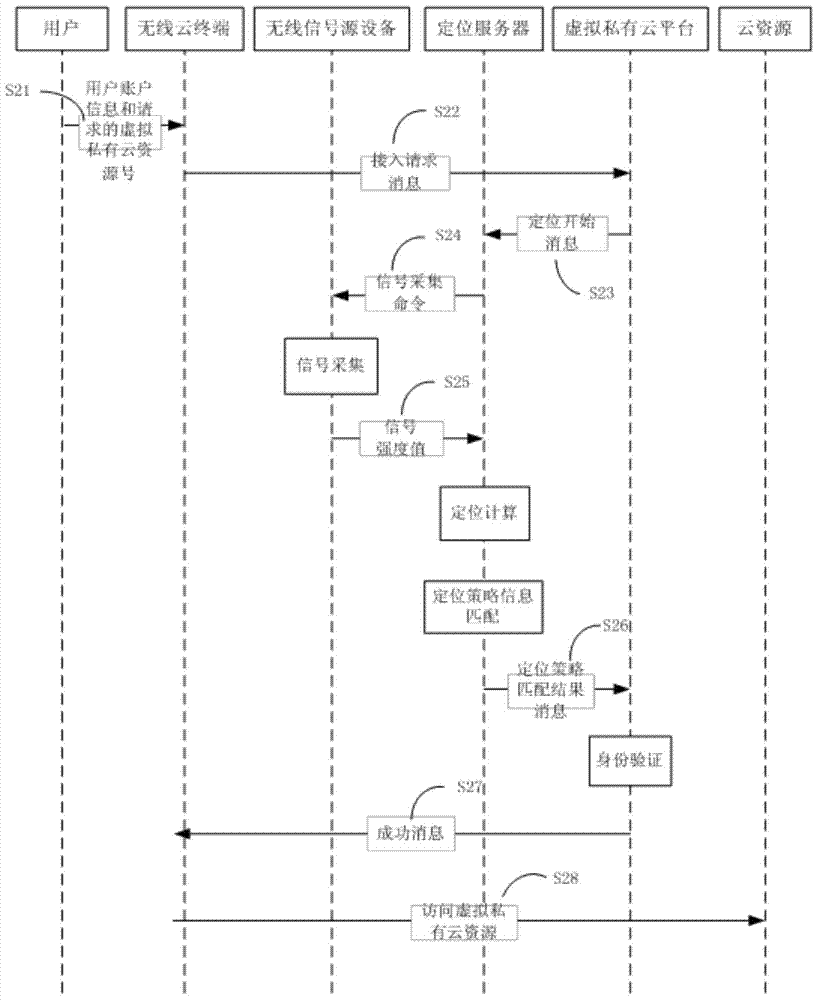
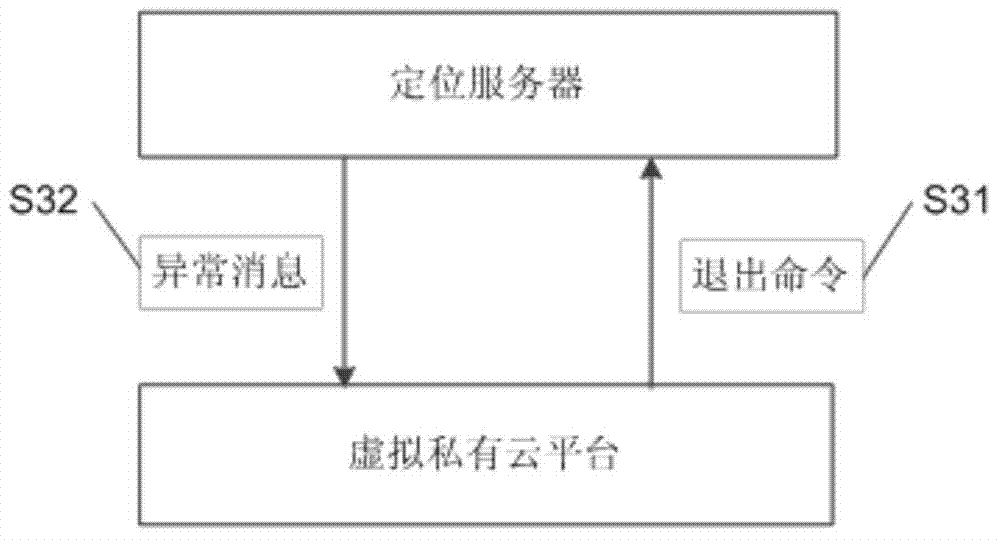
Virtual private cloud platform and virtual private cloud secure access method and system
ActiveCN103945330AStrengthen security controlLocation information based serviceTransmissionAccess methodSecurity management
The invention relates to a virtual private cloud platform and a virtual private cloud secure access method and system. The method comprises that when the virtual private cloud platform receives an access request of a user, a location server and a wireless signal source device perform position location and perform authority determination on a wireless cloud terminal and continue to verify the information of the account of the user if position admission is passed; if the wireless cloud terminal has position authority and account authority, a virtual private cloud allows the wireless cloud terminal to access required sources; after successful access is achieved, the virtual private cloud platform still locates and traces the accessed wireless cloud terminal to prevent attack of the wireless cloud terminal moving into illegal positions. The virtual private cloud platform and the virtual private cloud secure access method and system can narrow an attackable region into a designated range to strengthen the security management and control of the virtual private cloud.
Owner:重庆智载科技有限公司
Control method and system of air-conditioner
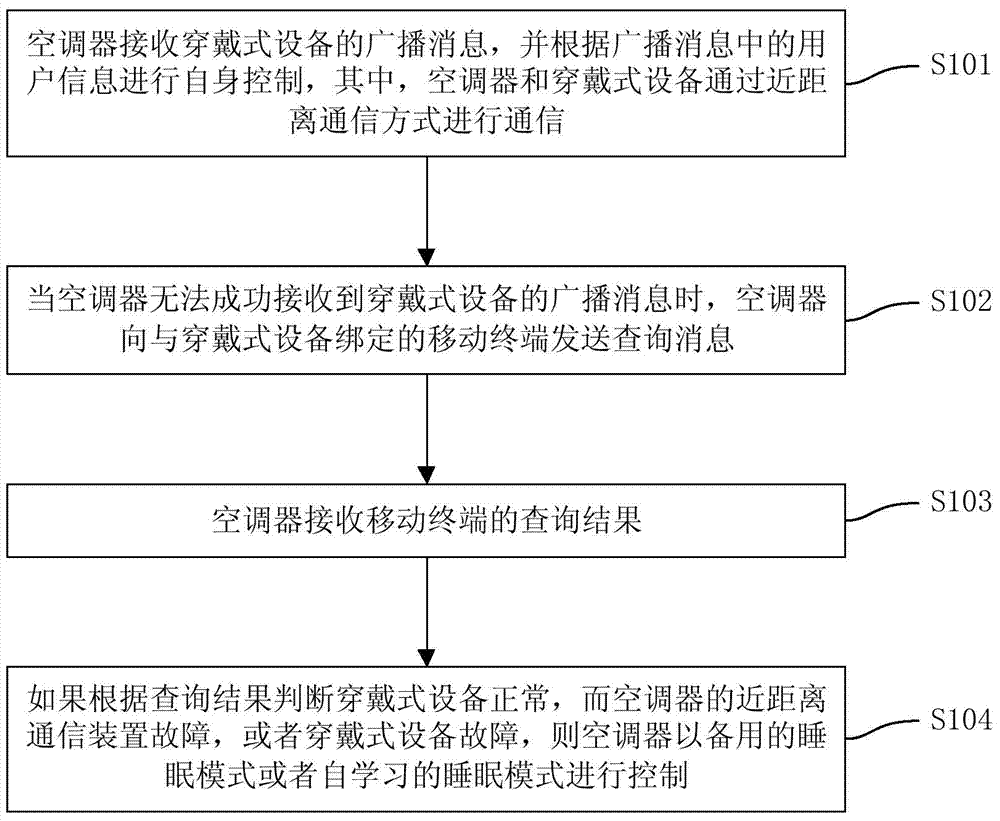
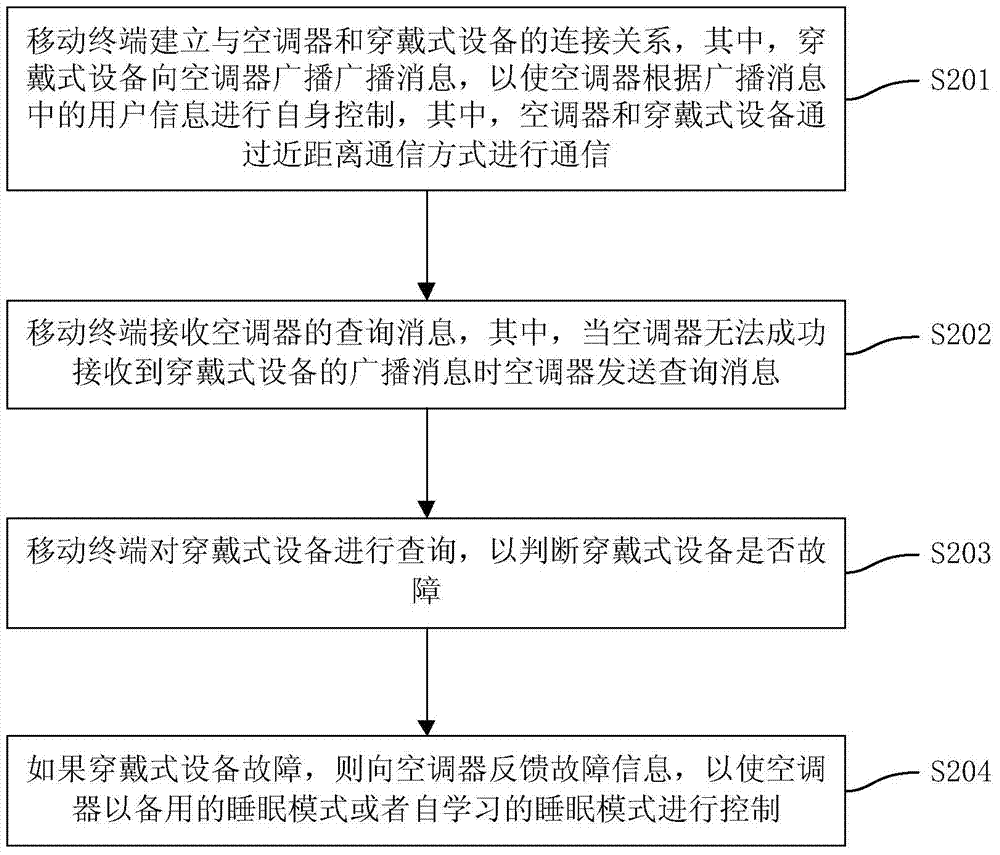
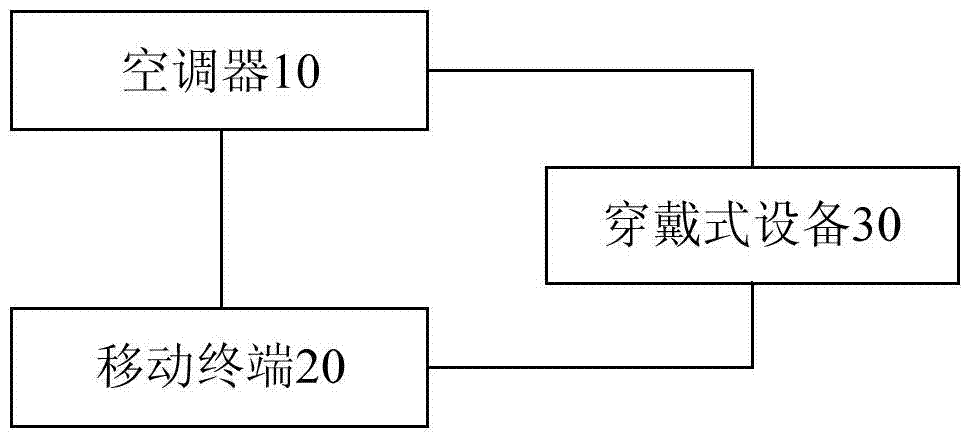
ActiveCN104748311AGuaranteed uptimeAvoid issues such as unsafe factorsMechanical apparatusSpace heating and ventilation safety systemsComputer terminalBroadcasting
The invention discloses a control method and system of an air-conditioner. The air-conditioner comprises an indoor unit, and the indoor unit is provided with a shell, an air inlet, an air outlet, a passage, a draught fan and a heat exchanger, wherein the air inlet and the air outlet are communicated through the passage, and the draught fan and the heat exchanger are arranged in the passage. The method includes the steps that the air-conditioner receives a broadcasting message of wearable equipment and performs self-control according to user information in the broadcasting message, wherein the air-conditioner and the wearable equipment communicate with each other in a near field communication mode; when the air-conditioner can not successfully receive the broadcasting message of the wearable equipment, the air-conditioner sends a query message to a movable terminal bound to the wearable equipment; the air-conditioner receive a query result of the movable terminal; if the wearable equipment is judged to be normal and a near field communication device of the air-conditioner or the wearable equipment breaks down according to the query result, the air-conditioner performs control in a standby sleep mode or a self-learning sleep mode. The method can guarantee that the air-conditioner can operate normally in case of equipment failures, and improve control safety.
Owner:MIDEA GRP CO LTD +1
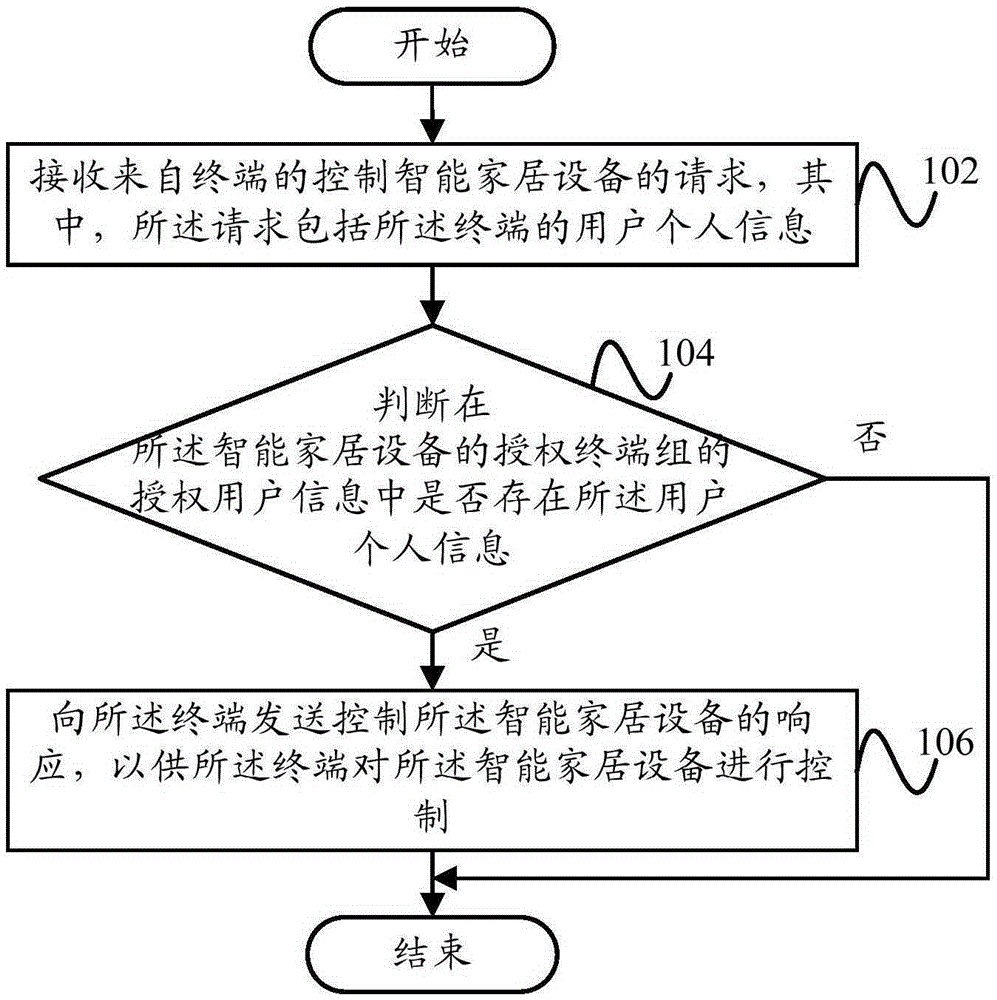
Control method of intelligent household equipment, control apparatus and terminal thereof
InactiveCN105610781AAvoid controlStrengthen security controlData switching by path configurationAuthorizationEmbedded system
The invention provides a control method of intelligent household equipment, a control apparatus of the intelligent household equipment and a terminal thereof. The control method of the intelligent household equipment comprises the following steps of receiving a request of controlling the intelligent household equipment from the terminal, wherein the request includes personal user information of the terminal; determining whether the personal user information exists in authorization user information of an authorization terminal group of the intelligent household equipment; when a determination result is yes, sending a response of controlling the intelligent household equipment to the terminal so that the terminal controls the intelligent household equipment. In the technical scheme of the invention, a condition that the terminal which is not in the authorization terminal group controls the intelligent household equipment is avoided so that safety of the intelligent household equipment is effectively increased and a user experience is improved.
Owner:YULONG COMPUTER TELECOMM SCI (SHENZHEN) CO LTD
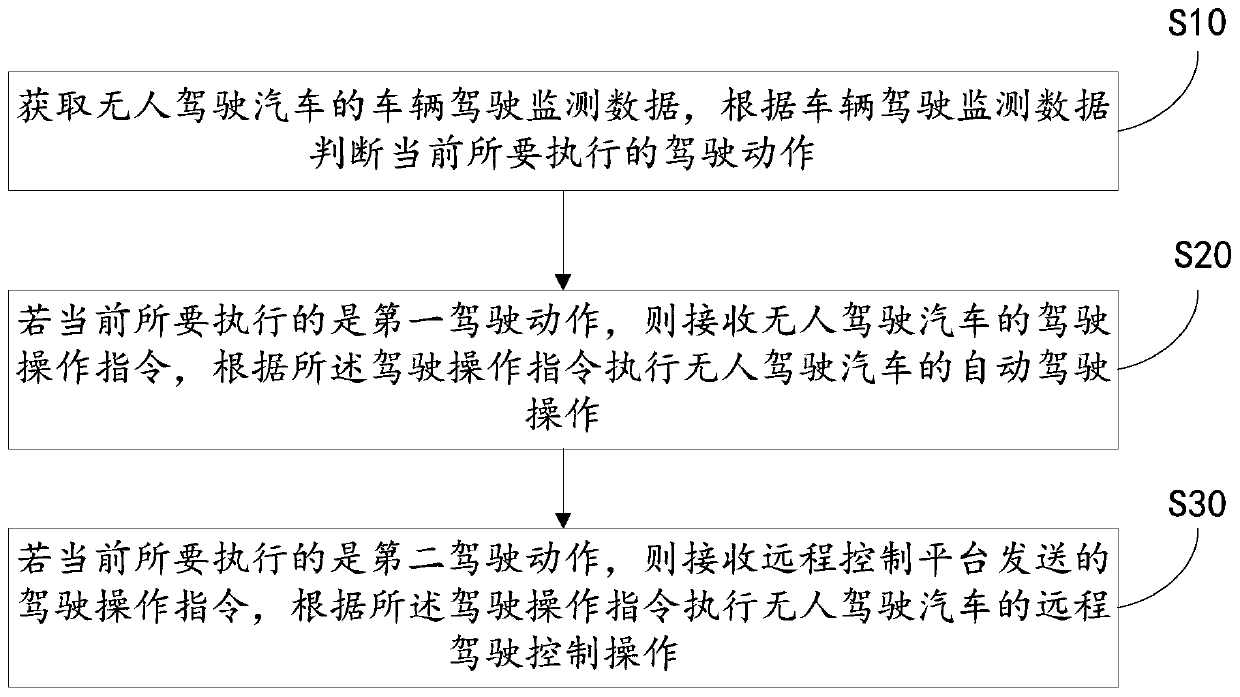
Control method of pilotless automobile, automobile and storage medium
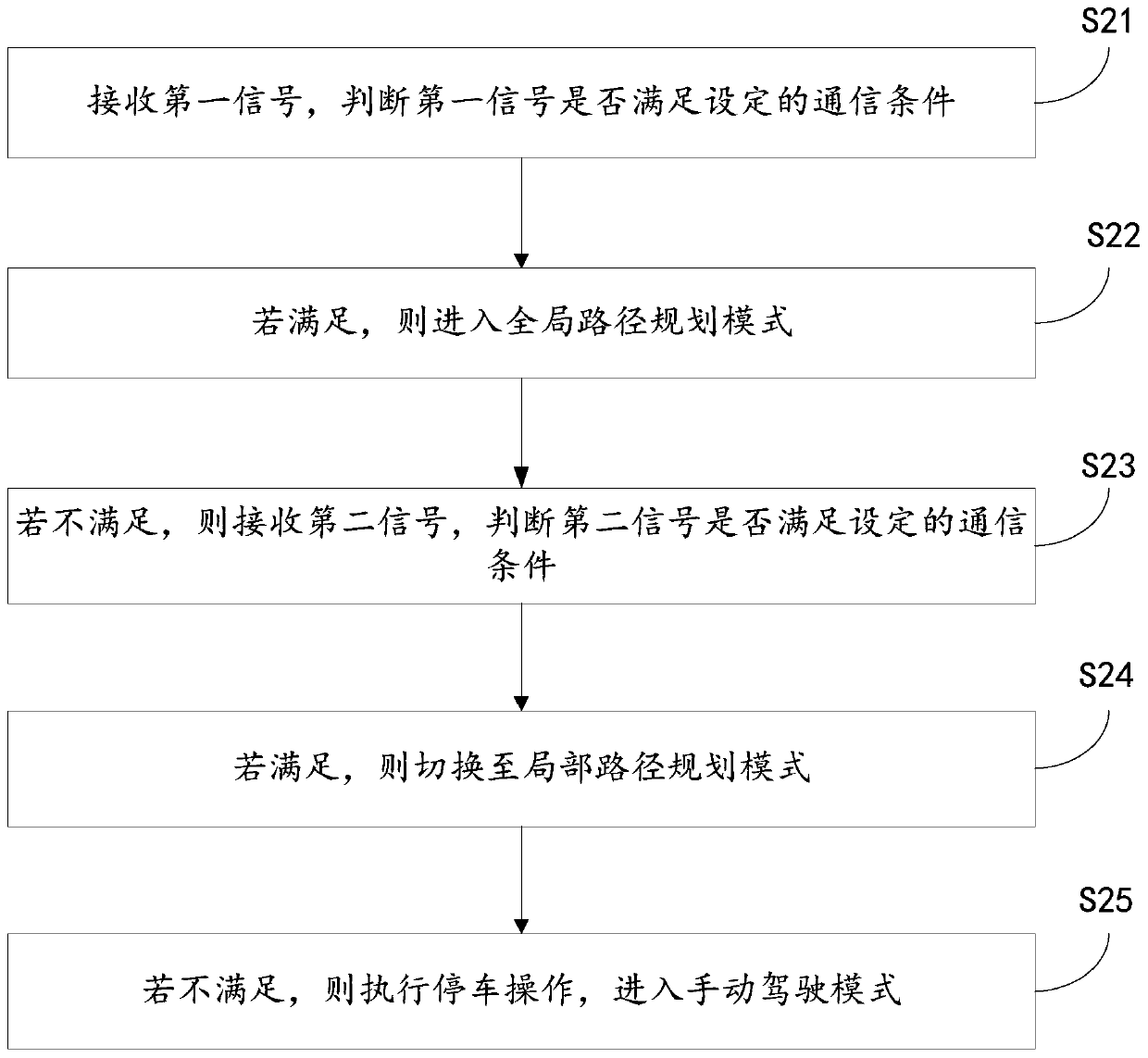
InactiveCN111580522AStrengthen security controlLow costInternal combustion piston enginesTotal factory controlControl engineeringVehicle driving
The invention discloses a control method of a pilotless automobile, an automobile and a storage medium, and the control method comprises the steps: obtaining the automobile driving monitoring data ofa pilotless automobile, and judging a driving action to be executed at present according to the automobile driving monitoring data; if the current to-be-executed action is the first driving action, receiving a driving operation instruction of the pilotless automobile, and executing automatic driving operation of the pilotless automobile according to the driving operation instruction; and if the second driving action needs to be executed currently, receiving a driving operation instruction sent by a remote control platform, and executing remote driving control operation of the pilotless automobile according to the driving operation instruction. The technical problems that when an automatic driving technology and a remote control driving technology are independently used for the pilotless automobile, the investment cost of the automobile is high, and the control precision is poor are solved, and the technical effects of improving the control safety and reducing the automobile cost are achieved.
Owner:DONGFENG LIUZHOU MOTOR
Credible computing system
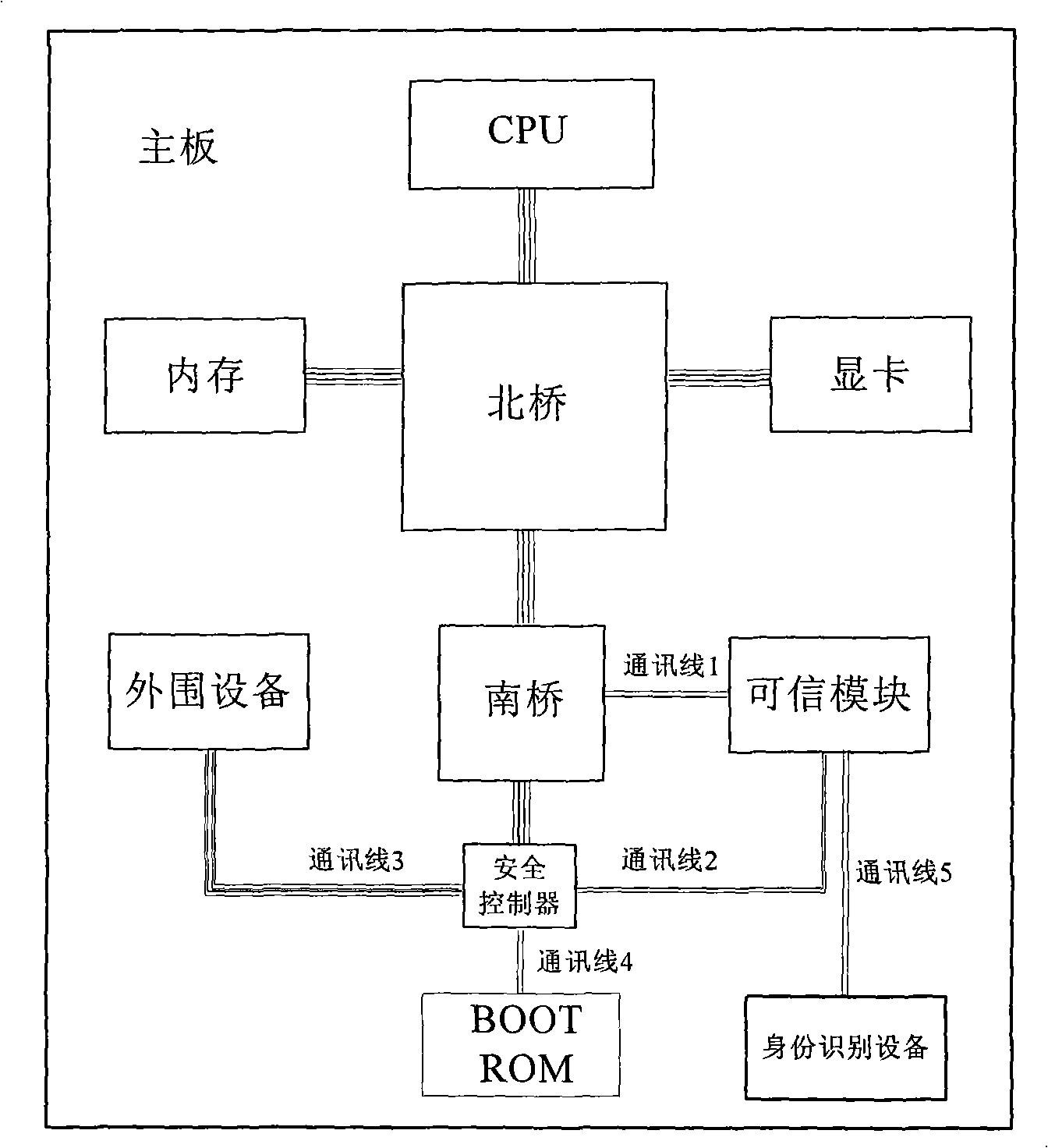
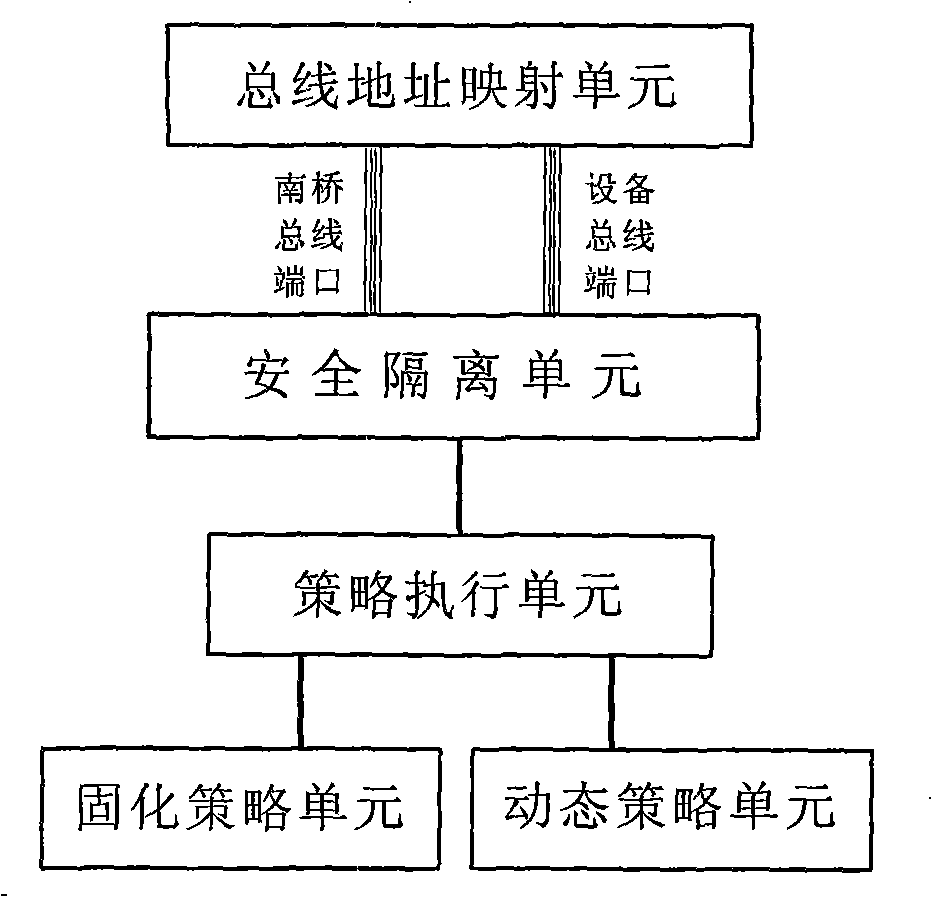
InactiveCN101281570AImprove securityIncrease flexibilityPlatform integrity maintainanceStrategy executionAddress mapping
The invention provides a trusted computing system, belonging to the field of information security. The invention is characterized in that a safety controller is provided, the security controller is connected to a system mainboard south bridge controller by communication lines, and a BOOT ROM is connected to the security controller by communication lines; the security controller is also connected to a trusted security module and mainboard peripheral equipment by communication lines; the security controller includes a bus address mapping unit, a security isolation unit, a strategy execution unit, a solidified strategy unit and a dynamic unit. By the cooperation of the trusted security module and the security controller, an access control strategy for the mainboard peripheral equipment is provided, a method for real-time protection of BIOS code management operation is provided, and a function for real-time virus diction of communication data of mainboard peripheral equipment is also provided.
Owner:BEIJING UNIV OF TECH
System and method for database access control
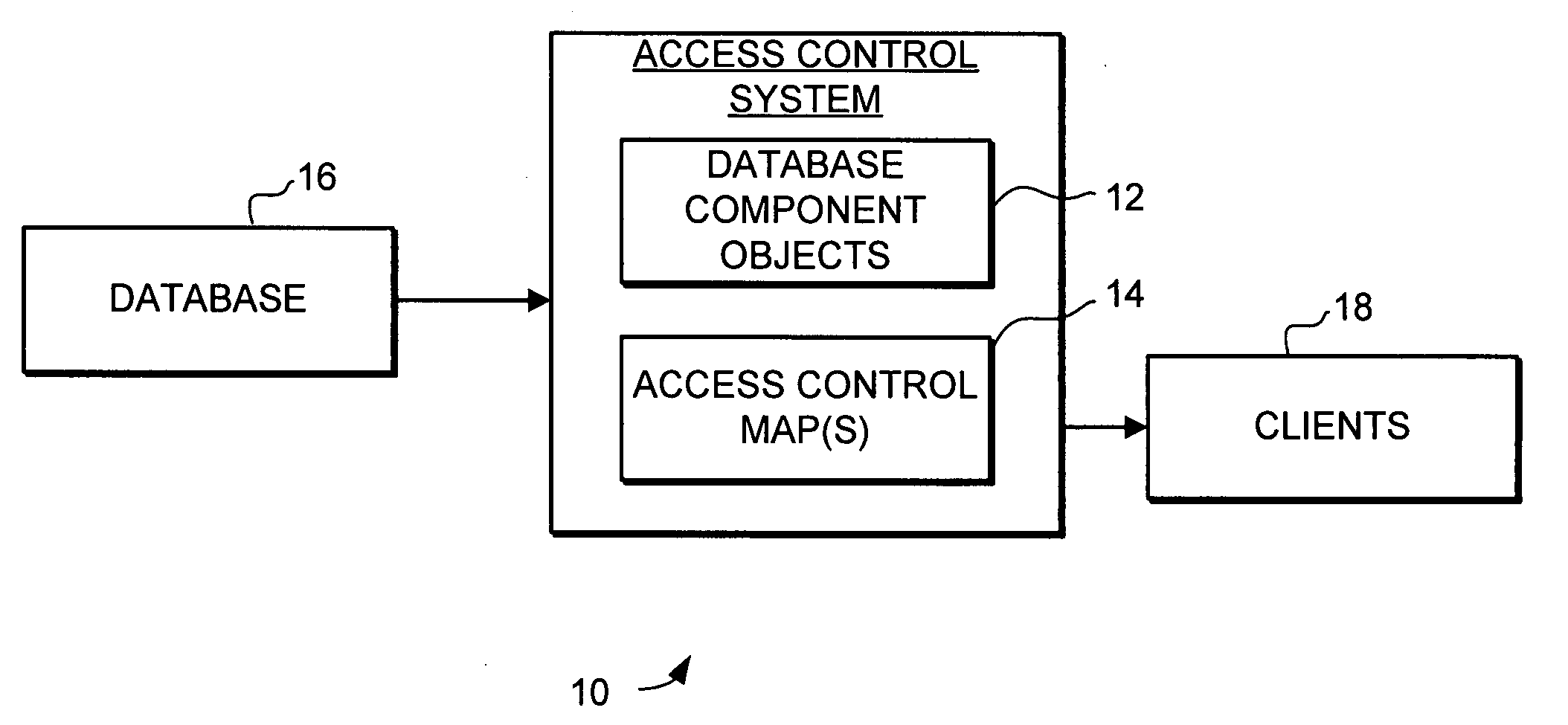
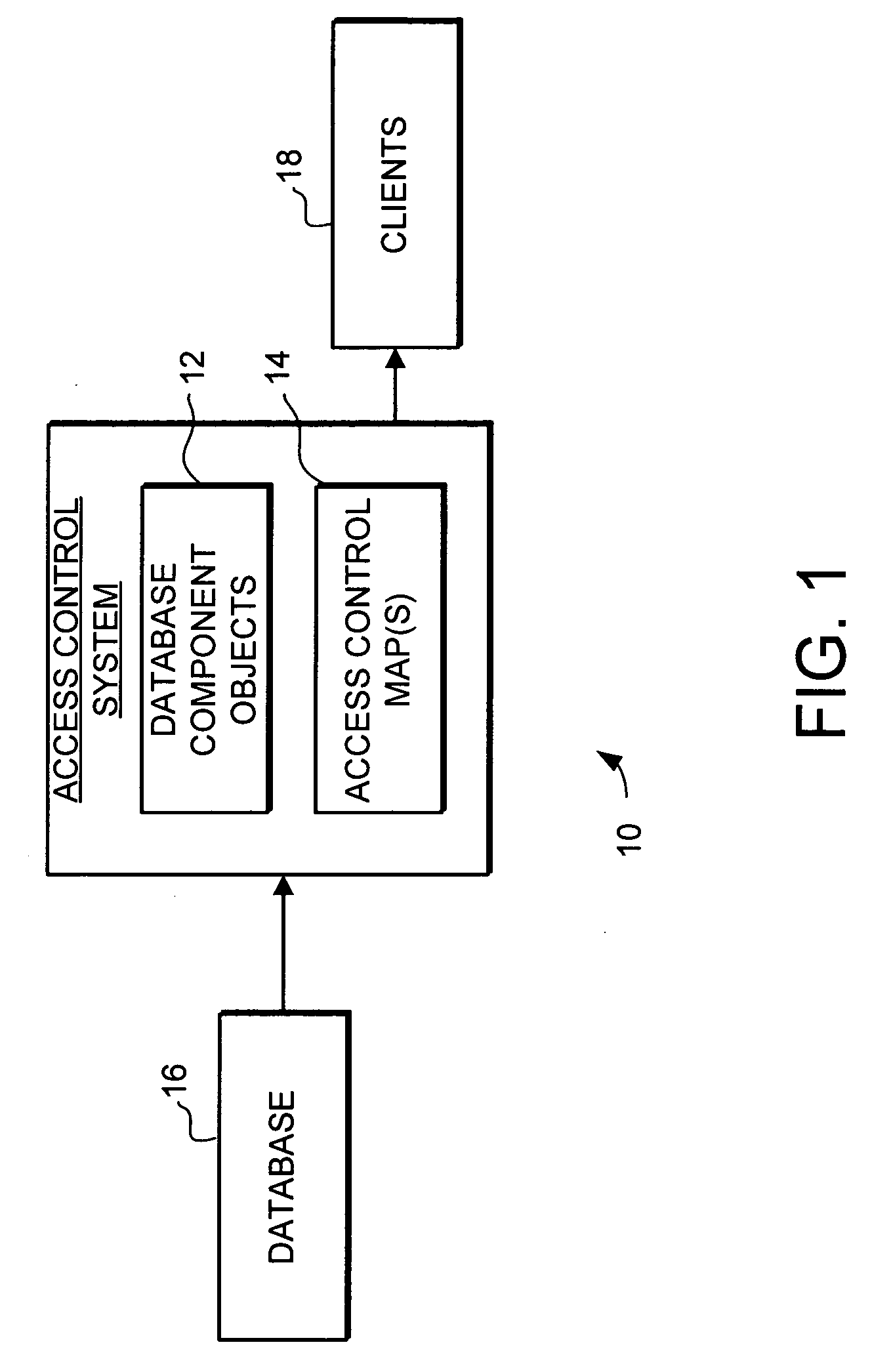
InactiveUS20060230041A1Facilitates individual controlFacilitate selective access controlDigital data processing detailsComputer security arrangementsGranularityControl system
A system and method for controlling access to components in a database is provided. The system and method provides flexible access control with variable granularity using a generalized mapping model (GMM) transform of data from one or more databases into a plurality of GMM objects, and mapping the GMM objects to access control settings using an access control mapping. The database access control system and method uses the structures of objects created by the GMM transform to identify and facilitate selective access control to any part or combination of components in the database, including the data and implicit relationships among data. The system and method facilitates individual control of the security permissions and conditions for the components using one or more access control maps to define which data components and relationships different access control procedures are applied.
Owner:MOTOROLA INC
Video monitoring image recognition system based on video encryption, compression and image recognition
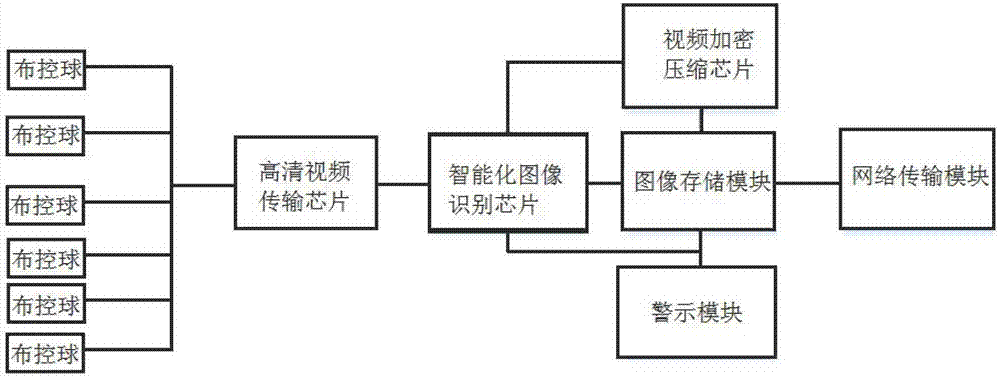
InactiveCN107426533ARealize the alarm functionEasy to collect evidenceTelevision system detailsImage analysisVideo monitoringVideo transmission
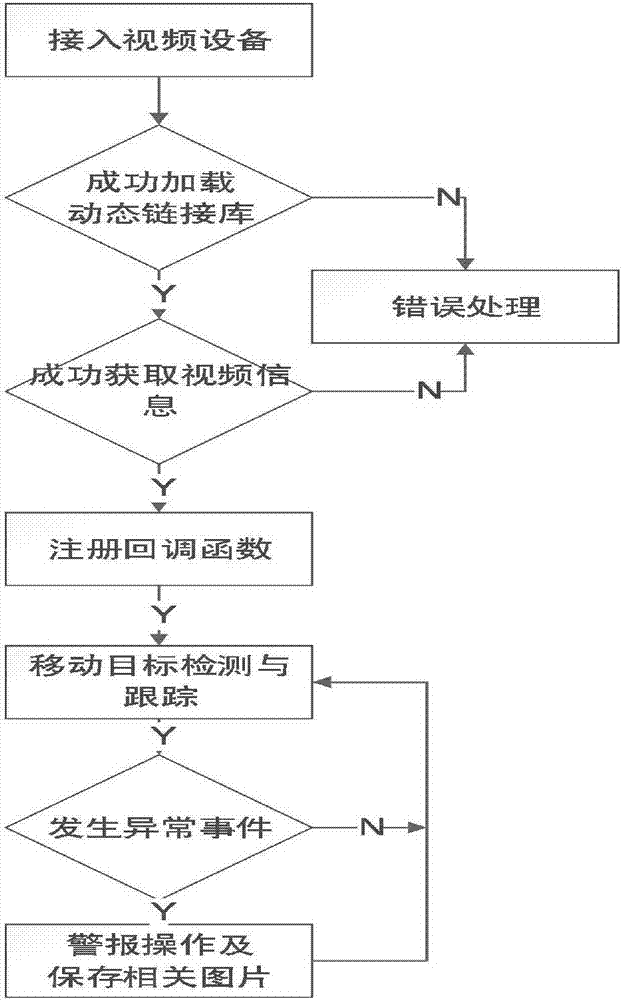
The invention relates to a video monitoring image recognition system based on video encryption, compression and image recognition, which comprises a high-definition video transmission chip, a video encryption and compression chip, an intelligent image recognition chip, an image storage module, a warning module and a network transmission module. The networked monitoring balls acquire the onsite information of the monitored areas; the high-definition video transmission chip obtains the video information of the monitoring balls simultaneously; the high-definition video transmission chip obtains the videos; and through the intelligent image recognition chip, the images are analyzed; and then, the video encryption and compression chip uses the network transmission module to transmit the videos to a video monitoring platform. The system is designed on the basis of the OpenCV functional characteristics; when a moving target is detected, intelligent analysis is made, which not only achieves the alarm function, but also stores the alarm videos for convenient evidence collection, and through the use of the wireless communication technology and the video encryption and compression technology, the related videos and other information are sent to an intelligent video monitoring system so as to facilitate the secure control on a power construction site by the management personnel.
Owner:STATE GRID TIANJIN ELECTRIC POWER +1
Mobile X-ray unit
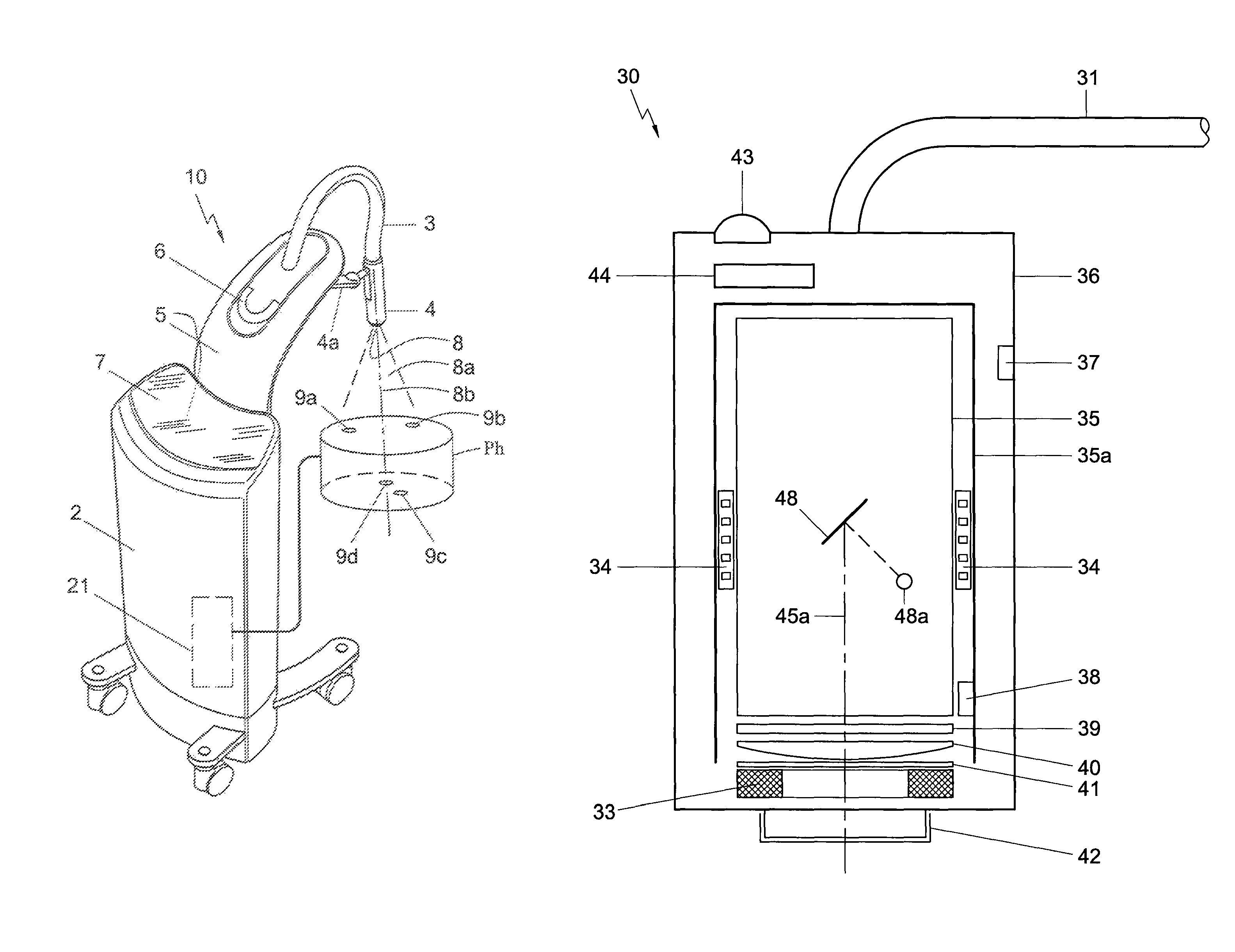
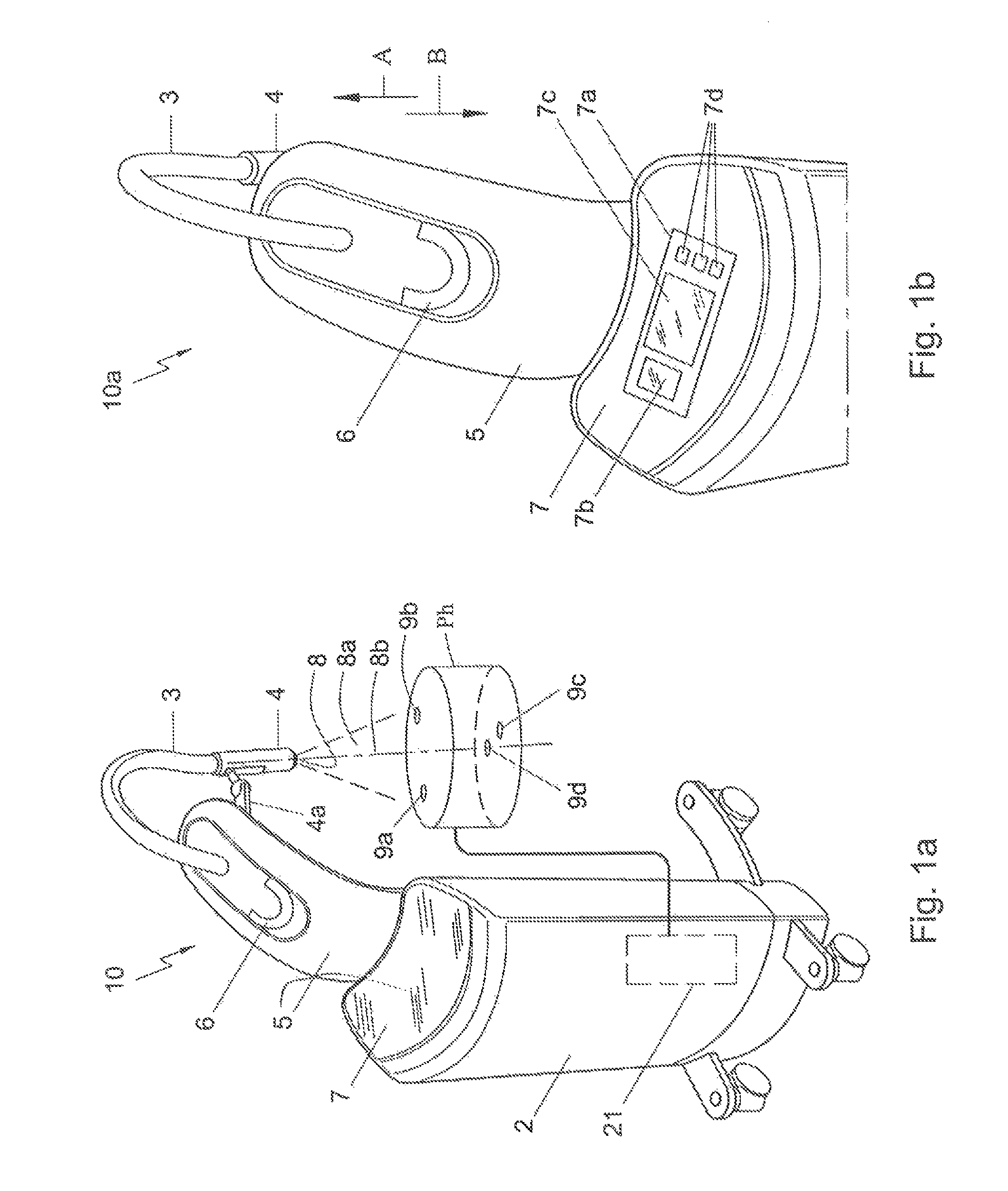
ActiveUS8929511B2Efficiently determinedStrengthen security controlX-ray apparatusRadiation diagnosticsEngineeringX-ray generator
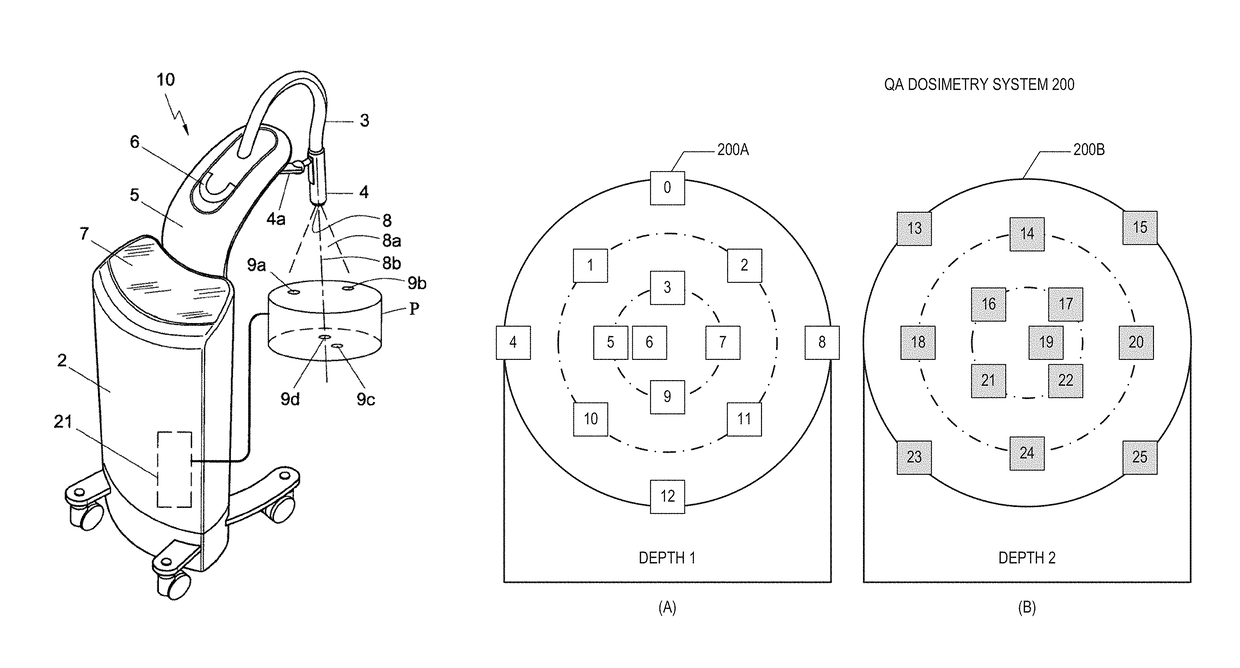
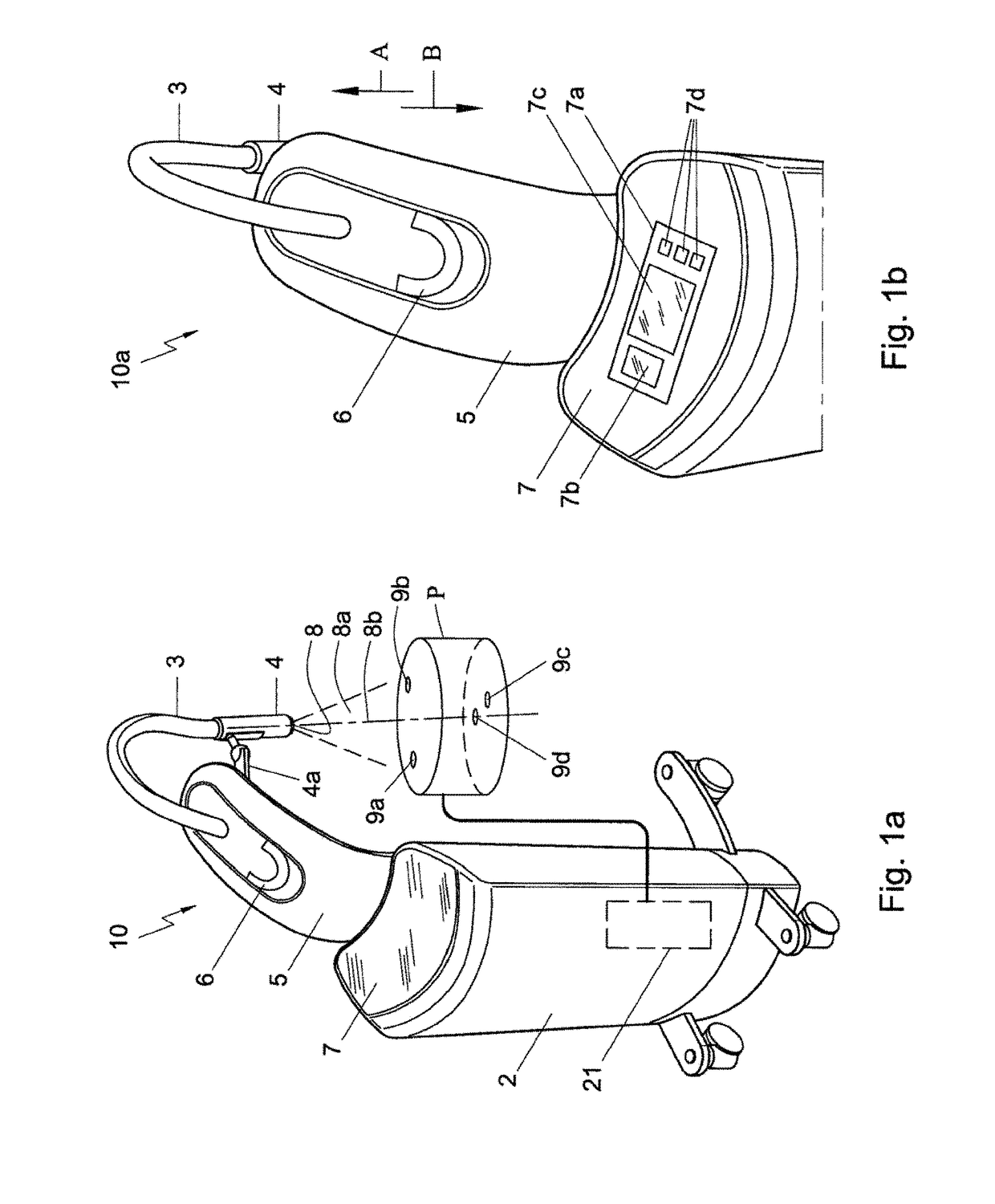
One embodiment of the present disclosure is directed to a mobile X-ray unit. The mobile X-ray unit may include a base for accommodating a control unit configured to control an X-ray applicator and a power supply configured to supply power to the X-ray applicator. The mobile X-ray unit may further include an articulated arm associated with the base. The arm may be configured to support the X-ray applicator. The X-ray applicator may have an X-ray tube for emitting an X-ray beam for irradiating an object. The mobile X-ray unit may further include a phantom-based dosimetry system configured to perform a dosimetry check of the X-ray beam.
Owner:NUCLETRON OPERATIONS
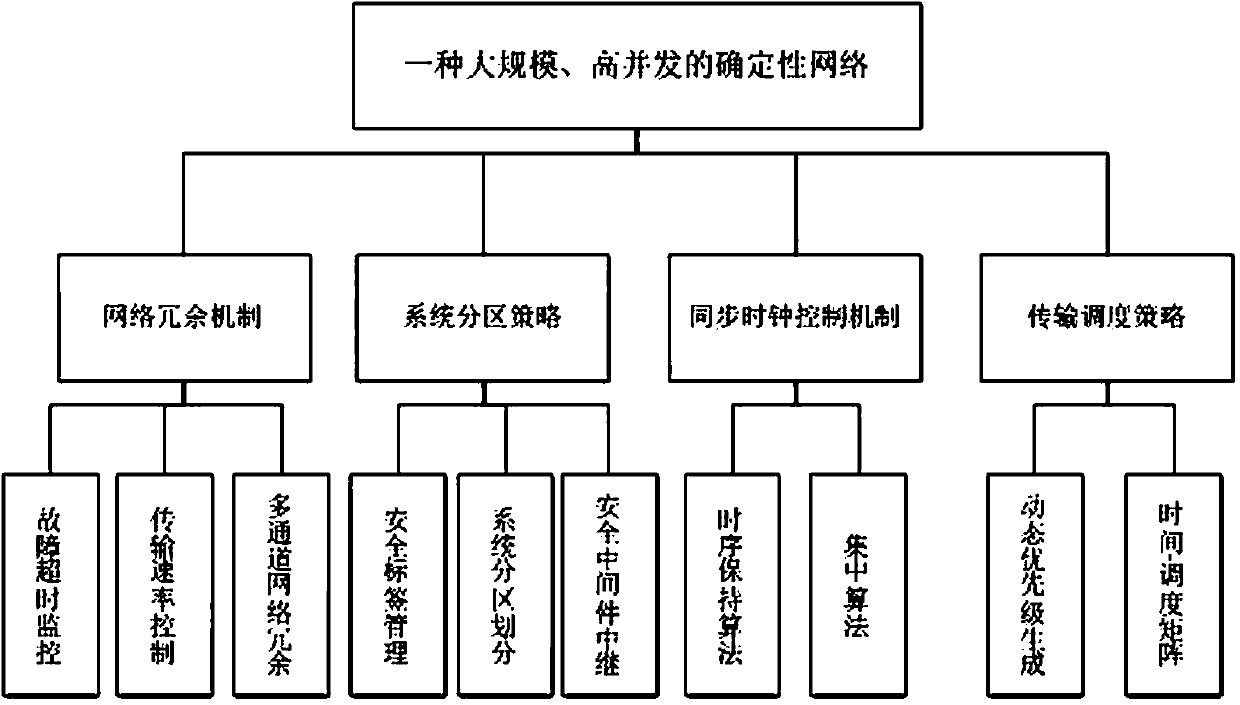
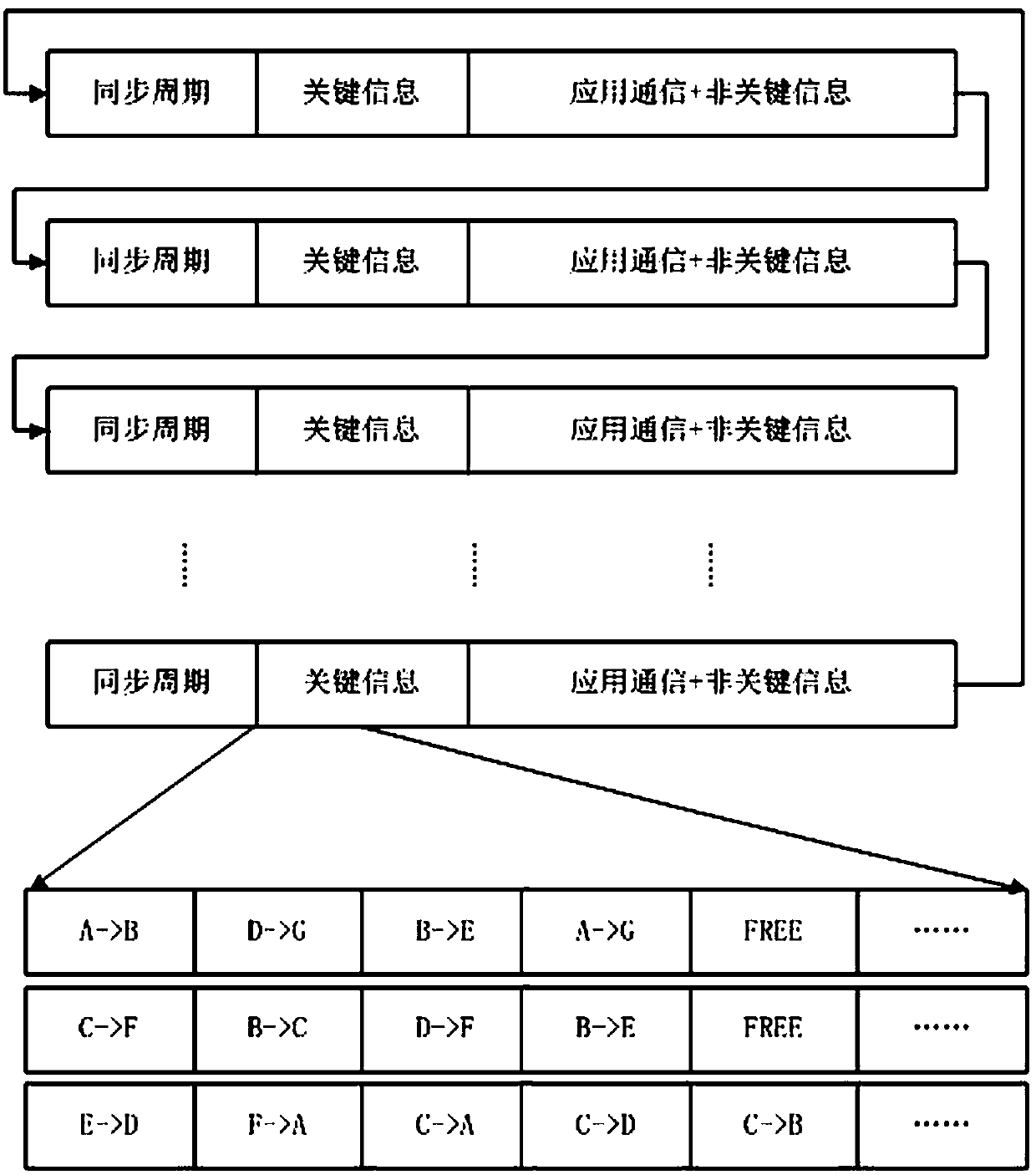
Large-scale and high-concurrency deterministic network system
ActiveCN108847961AImprove concurrencyImprove securityTime-division multiplexData switching networksTraffic capacityControl system
The invention discloses a large-scale and high-concurrency deterministic network system, and belongs to the technical field of network communication systems. The large-scale and high-concurrency deterministic network system comprises a network redundancy system, a system partition policy system, a synchronous clock control system and a transmission scheduling policy system; the network redundancysystem ensures the network reliability through fault monitoring and rate control; the system partition policy system is used for performing isolation control of service traffic and improving the scaleand concurrency of the network; the synchronous clock control system provides a clock reference for the determinacy of the network for ensuring the synchronization of a local clock of a global network device; and the transmission scheduling policy system generates a scheduling optimization policy through priority configuration for rationally utilizing network bandwidth resources, improving the message concurrency and expanding the network scale at the same time.
Owner:NO 54 INST OF CHINA ELECTRONICS SCI & TECH GRP
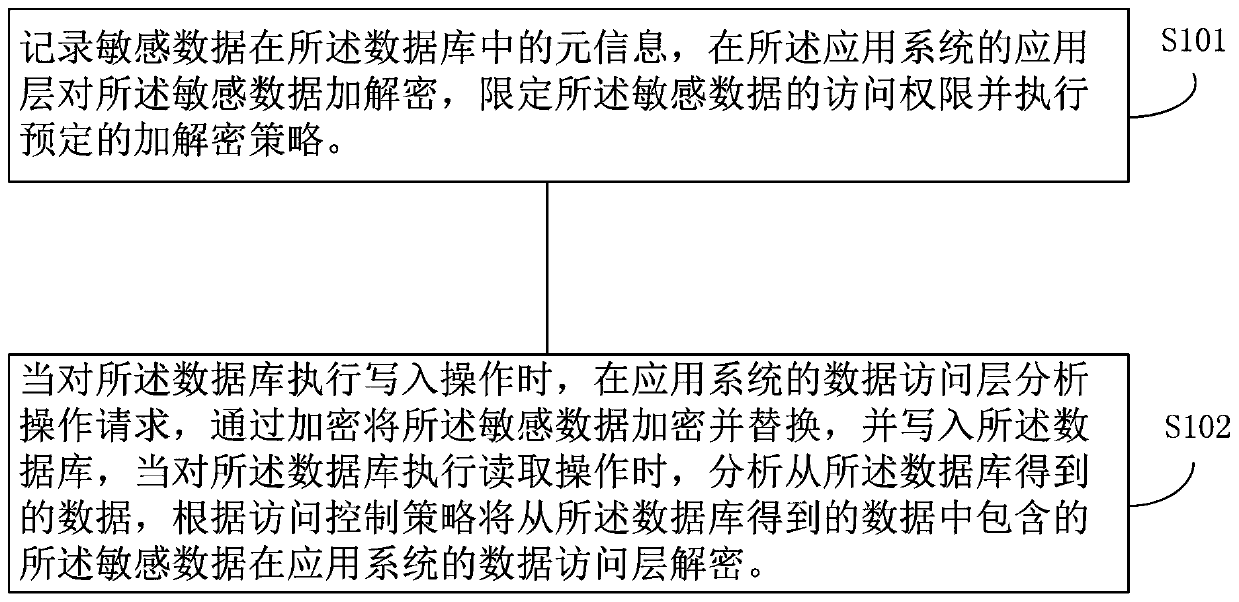
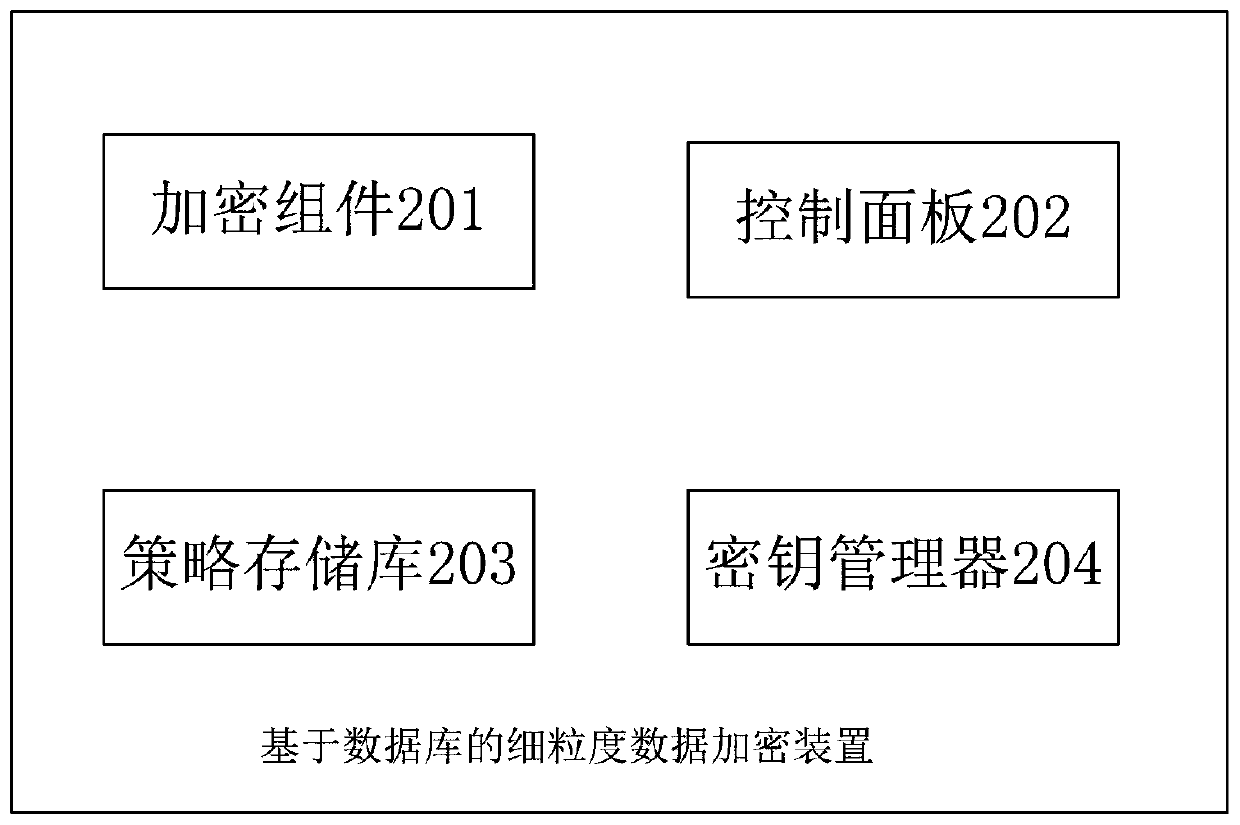
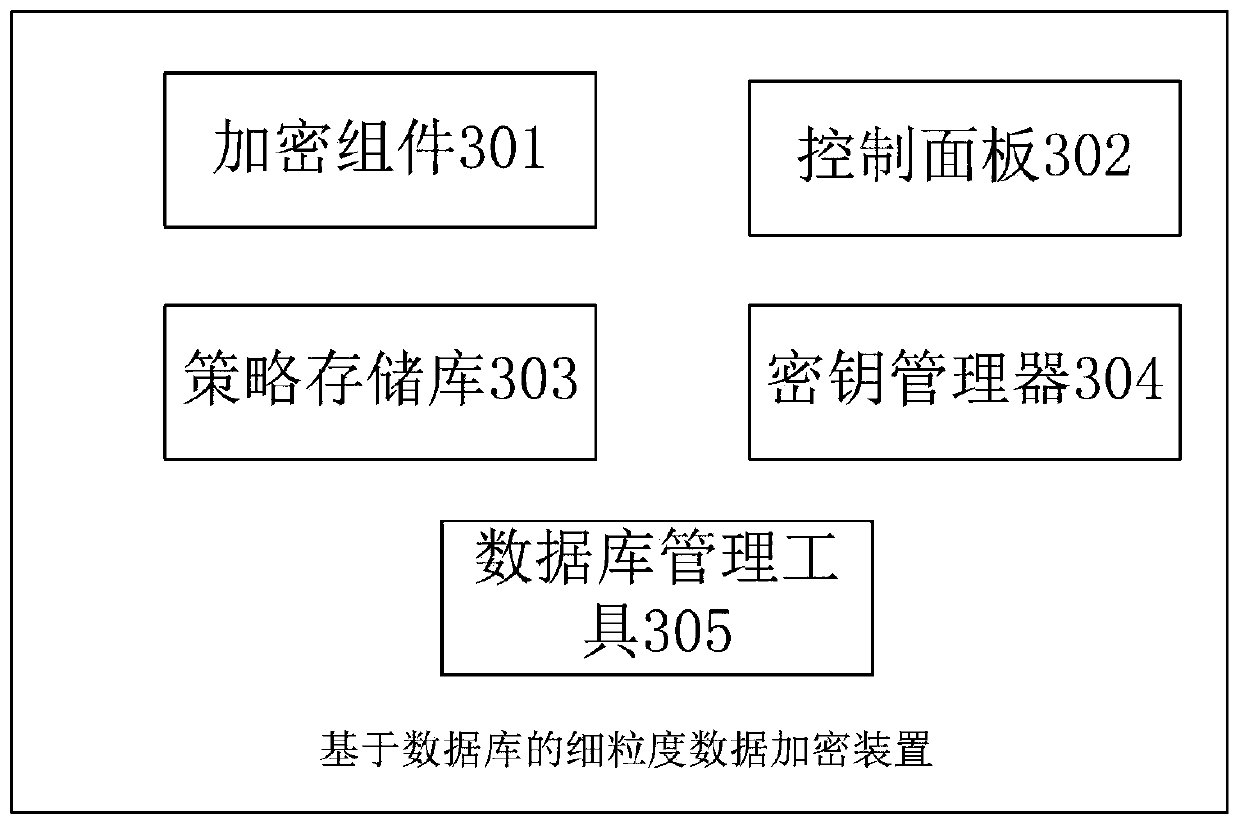
Fine-grained data encryption method, system and device based on database
ActiveCN110889130AStrengthen security controlPrevent leakageDigital data protectionStorage securityCiphertext
The invention provides a fine-grained data encryption method and device based on a database. The device comprises a data encryption assembly and a data encryption management assembly, the data encryption component is installed in each application needing to access the database in the form of a plug-in, monitors the process of the application at any time, intercepts the operation of the applicationon the database, and is used for restoring the entity information in the context of the application process, encrypting and decrypting the data by taking the columns or rows in the database tables asthe grain sizes and decrypting or desensitizing the sensitive data according to the entity permission, and the data encryption management component is connected with the data encryption component through a network and is used for managing the entity access permission, the encryption and decryption strategies and the encryption and decryption keys of the sensitive data in the database. Accordingto the present invention, the sensitive data is encrypted and decrypted by taking the rows or columns in the database tables as the grain sizes in a data access layer of the application system, and the sensitive data originally submitted to a database driving layer in a plaintext form is replaced with ciphertext, so that the transmission security and the storage security of the data are ensured.
Owner:BEIJING LIANSHI NETWORKS TECH CO LTD
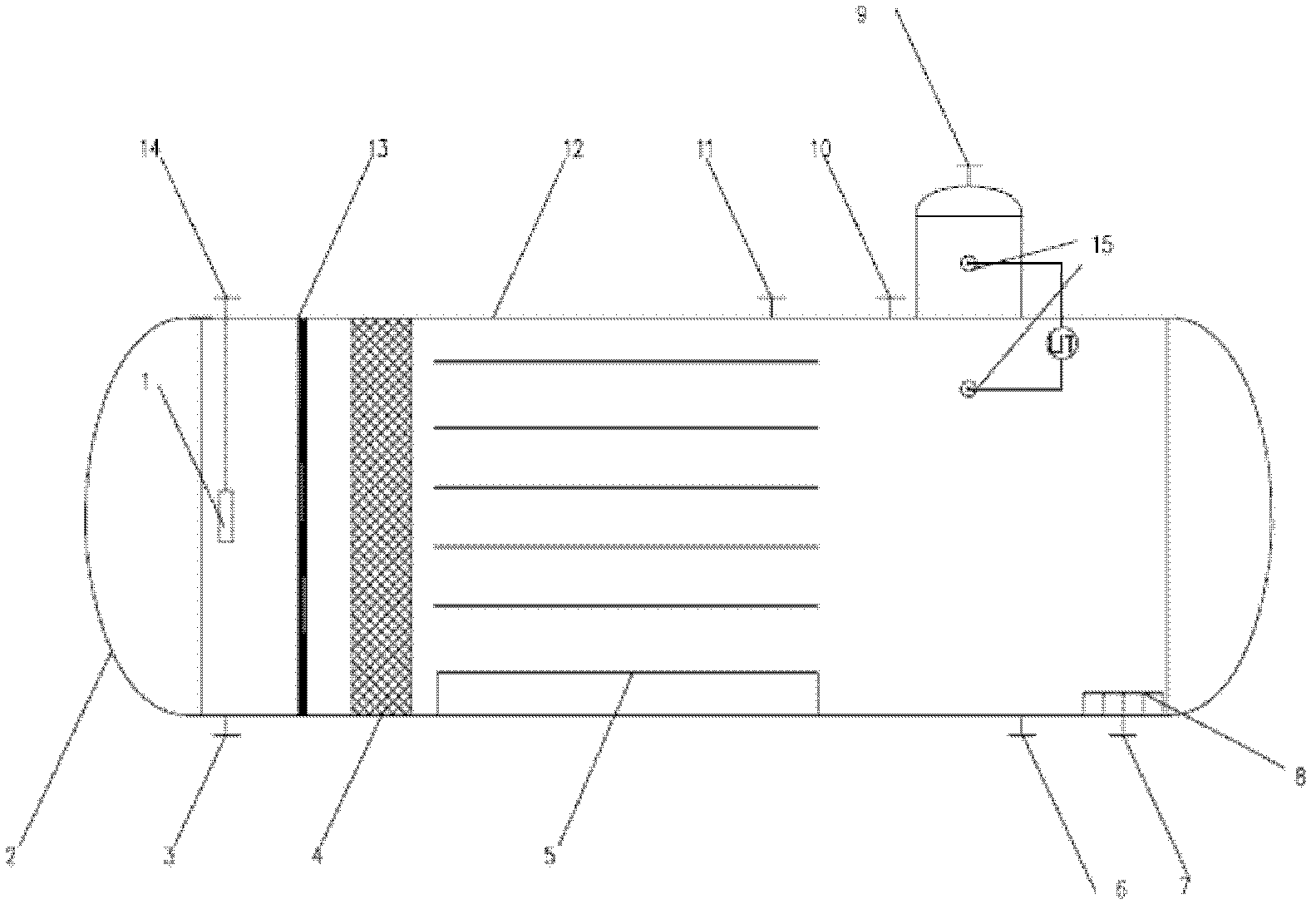
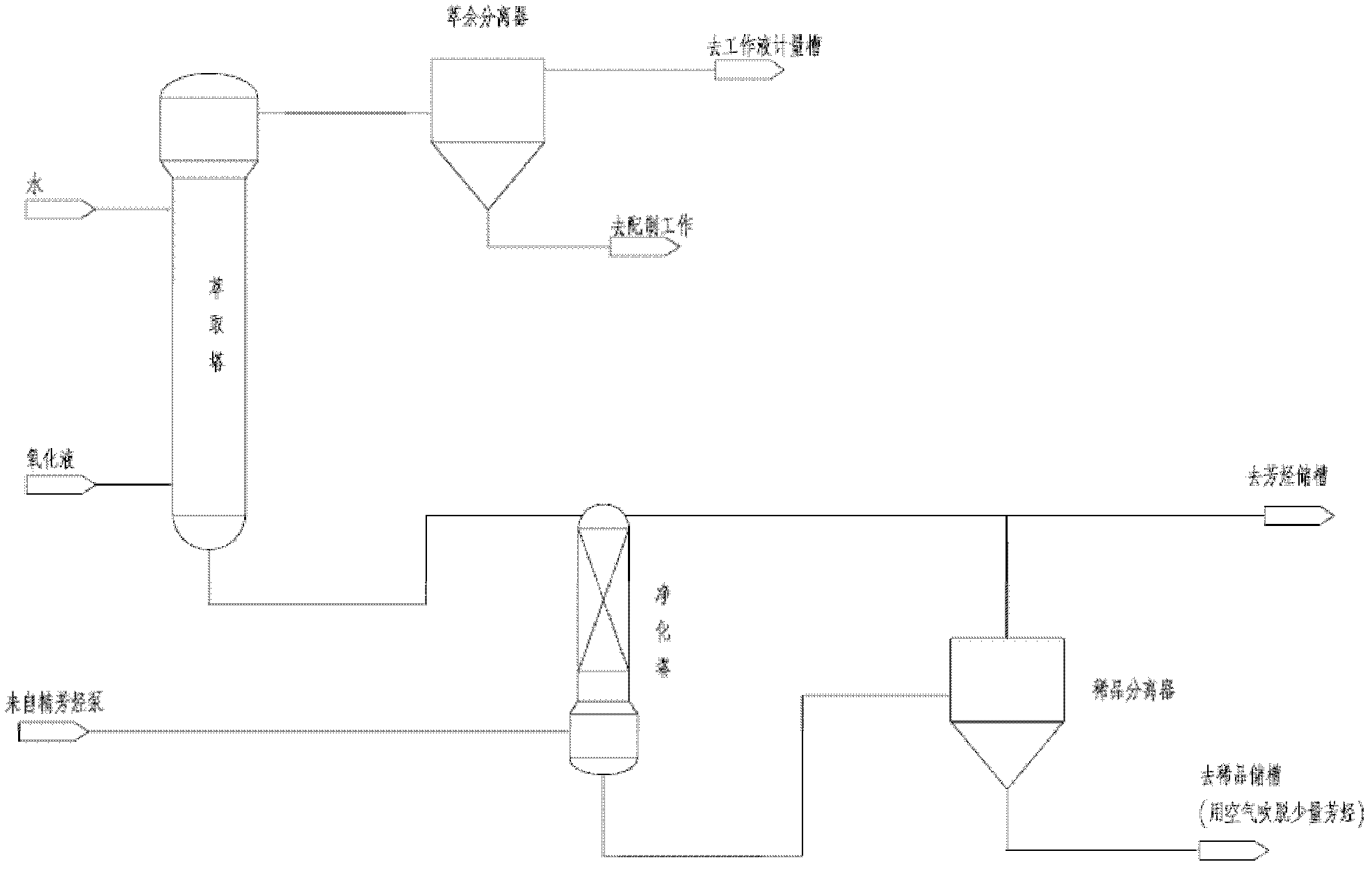
Device and process applied to hydrogen peroxide extraction
ActiveCN102491281AExtended stayShort stayPeroxides/peroxyhydrates/peroxyacids/superoxides/ozonidesFiberProcess engineering
The invention provides a device and process applied to hydrogen peroxide extraction. The device comprises a stock solution tank, a separating tank, a liquid distributor, a rectifier, a liquid drop multiplication fiber filler assembly, a special plate group separating assembly and an anti-vortex baffle plate assembly, wherein the liquid drop multiplication fiber filler assembly and the special plate group separating assembly are arranged in the separating tank; the separating tank is provided with a small dispersed phase discharge barrel for stabilizing a two-phase interface and preventing discharging inclusion of a dispersed phase; and the anti-vortex baffle plate assembly is arranged in the separating tank and is used for preventing discharging vortex, stabilizing flow field in the separating tank and enhancing a separating effect. The separating equipment can reach dozens of ppm in maximum. Due to the adoption of a rare product phase separator, separating time is shortened, equipment size is reduced, and the load of subsequent air blow-off aromatic hydrocarbon and the emission of aromatic hydrocarbon can be lowered.
Owner:SHANGHAI ANHORN ENVIRONMENTAL TECH CO LTD
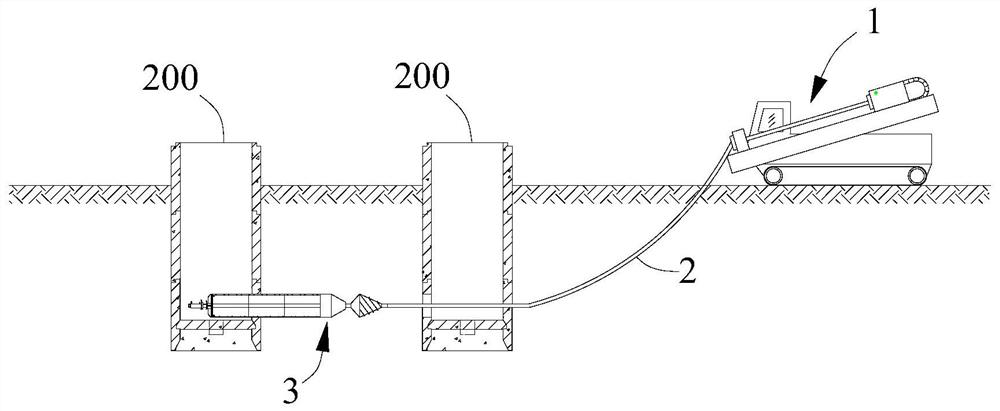
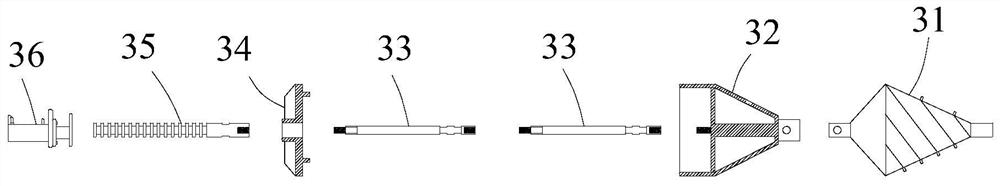
Jacking-pulling construction method
The disclosure provides a jacking-pulling construction method. The jacking-pulling construction method comprises the following steps of: well site production, that is, a pipe jacking-pulling working well is made by using a precast reinforced concrete pipe well through the undrained caisson construction, the bottom of the pipe jacking-pulling working well is sealed by using concrete underwater, andthe water level inside the well is more than 1 meter higher than the water level outside the well; guide hole drilling, that is, a directional drilling machine is connected to a first end of a jacking-pulling drill pipe, and a second end of the jacking-pulling drill pipe is connected to a guide bit, so as to drill a guide hole according to a predetermined trajectory; reaming stage, in which the guide bit is disassembled, a reverse drill bit is installed to the second end of the jacking-pulling drill pipe, and reverse reaming is performed along the hole through which the jacking-pulling drillpipe passes; and pipeline laying, that is, a front end fixing cap, a short force transmission rod, a rear anchor top plate, a rear anchor short rod, a hydraulic jack and a self-locking socket pipe areinstalled to the end of the reverse drill bit, and jacking-pulling installation construction is carried out on the self-locking socket pipe. The scheme provided by the disclosure achieves the effectsof high construction accuracy, short construction period and small construction area.
Owner:GUANGDONG NO 1 CONSTRUCTION ENGINEERING CO LTD
Intelligent medical robot for lower limb rehabilitation therapy
PendingCN107374911AHigh control precisionAchieving Adaptive ControlDiagnosticsChiropractic devicesHuman bodyExoskeleton robot
The invention provides an intelligent medical robot for lower limb rehabilitation therapy. A movement suspension system is mounted above a movement transmission system through a stand column; weight reduction and position holding of a patient subjected to lower limb rehabilitation therapy are implemented by the suspension system; the patient uprightly walks on the movement transmission system under the driving effect of a lower limb exoskeleton robot system; the lower limb exoskeleton robot system is connected with a rotating system by a gravity center self-balancing system; the height of the lower limb exoskeleton robot system is adjusted according to change of center of gravity of the patient during walking of the patient; and a sensor system acquires equipment parameters and human body parameters, and transmits the equipment parameters and the human body parameters to an embedded control system to be displayed. The intelligent medical robot for lower limb rehabilitation therapy is high in control precision and high in intelligence, and can be used for rehabilitation training of upright walking of the patient.
Owner:中航创世机器人(西安)有限公司
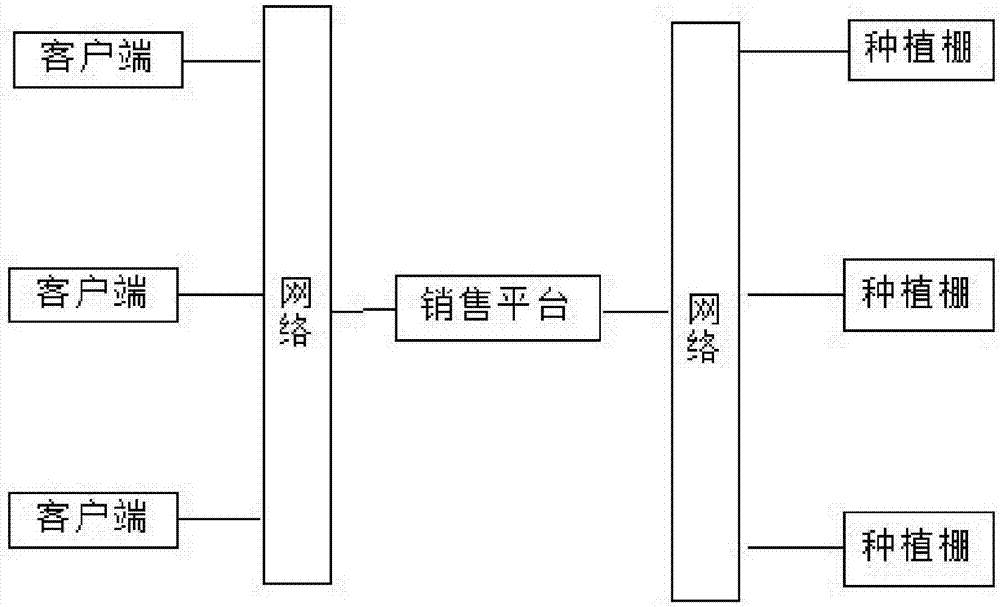
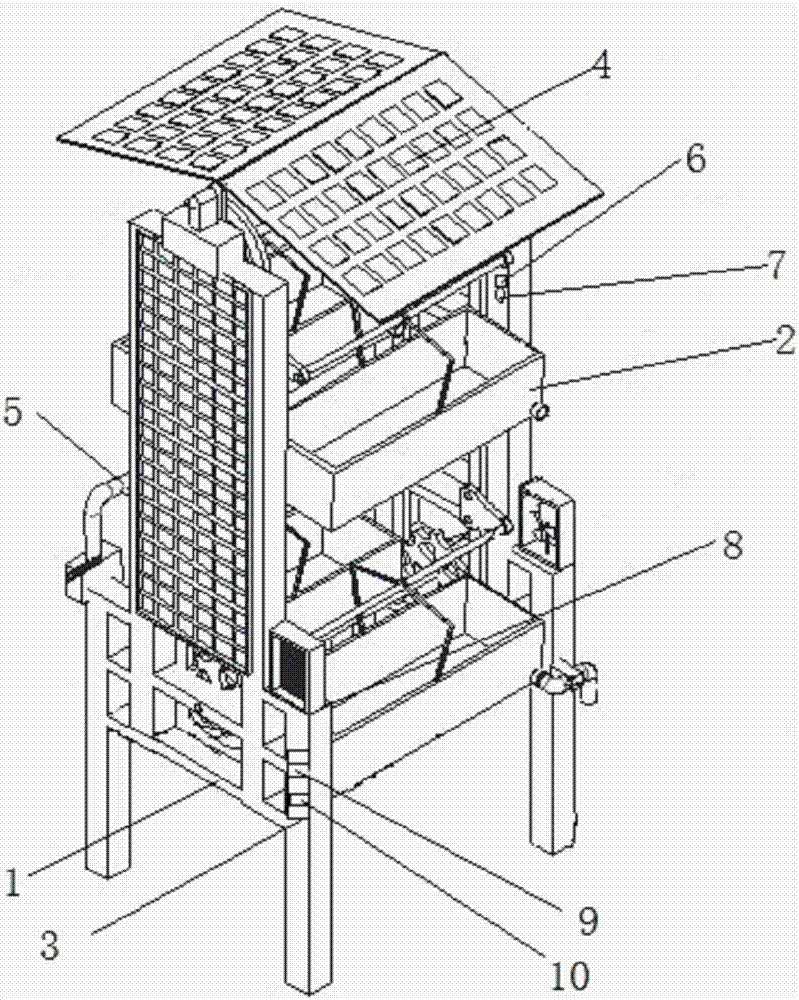
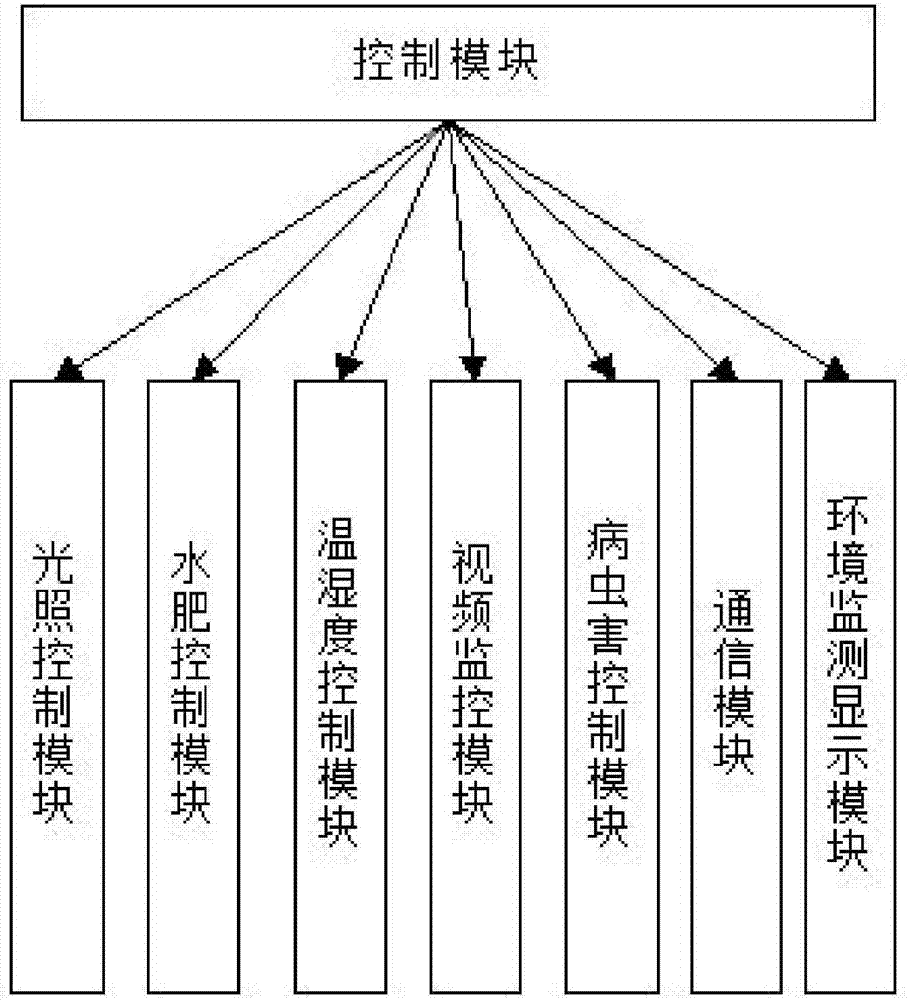
Nuisance free vegetable video online sales platform based on stereo agriculture
PendingCN107330807AImprove experienceImprove participationClosed circuit television systemsBuying/selling/leasing transactionsVideo monitoringInsect disease
The invention provides a nuisance free vegetable video online sales platform based on stereo agriculture, and belongs to the agriculture technical field; the nuisance free vegetable video online sales platform comprises an equipment end, a network, a sales platform and a client end; the equipment end comprises a stereo agriculture plantation apparatus, and a plurality of planting units, an illumination control module, an irrigation control module, a fertilization control module, a humiture control module, a video monitoring module and an insect disease control module arranged on the plantation apparatus; the sales platform and the client end are connected with the equipment end; consumers invoke the video monitoring module of the equipment end to select and place orders; clients can remotely check the vegetable plating, growth and management conditions, thus truly monitoring the source, and controlling the food safety; clients can select vegetables through the videos, and can monitor a plucking, packaging and transportation process, thus realizing visualization trading between vegetable product suppliers and consumers, building a novel fruit vegetable product supply mechanism, improving the food safety control intensity, and ensuring the consumers to eat healthy.
Owner:HUBEI UNIV OF SCI & TECH
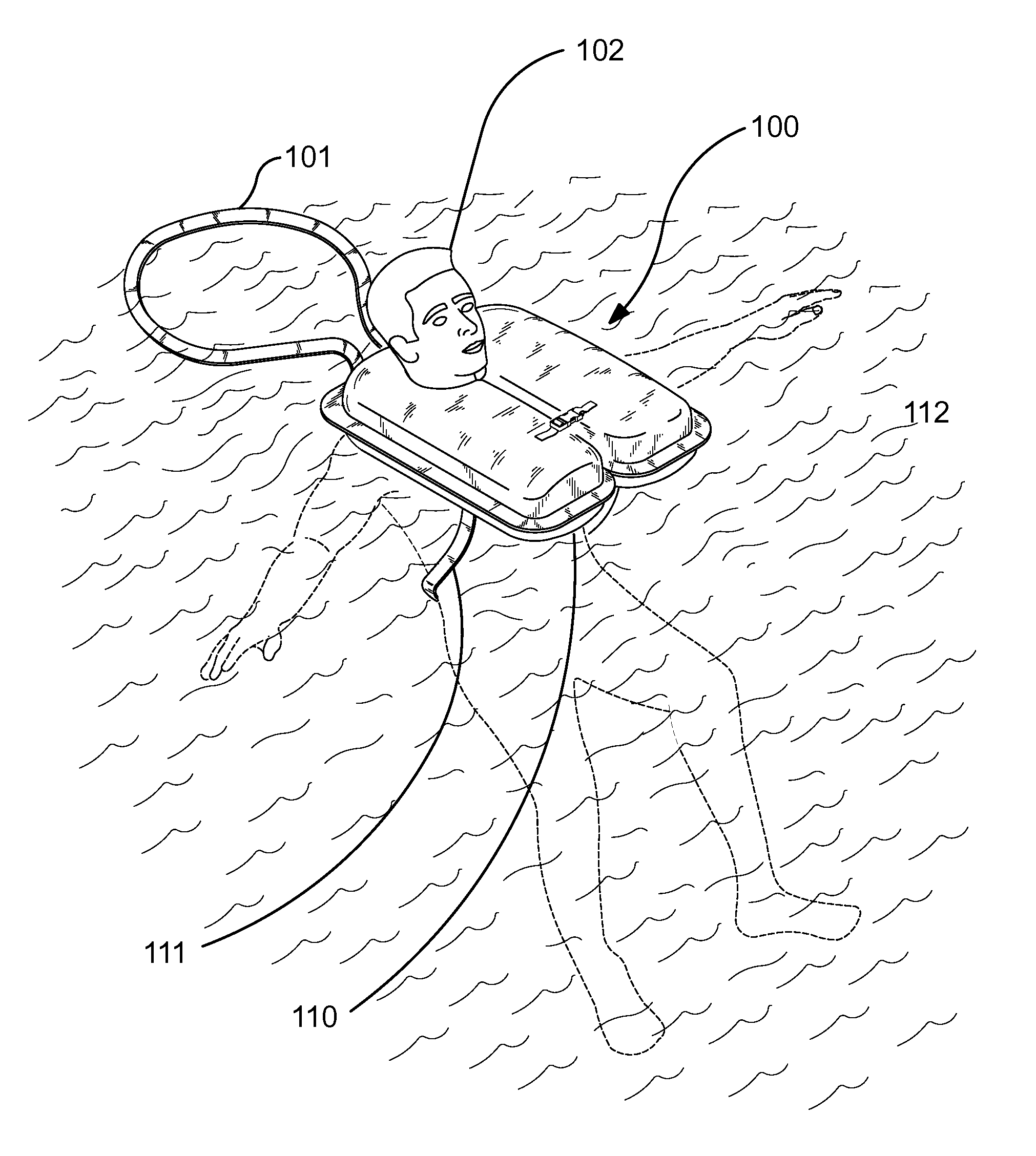
Multi-functional, personal flotation device
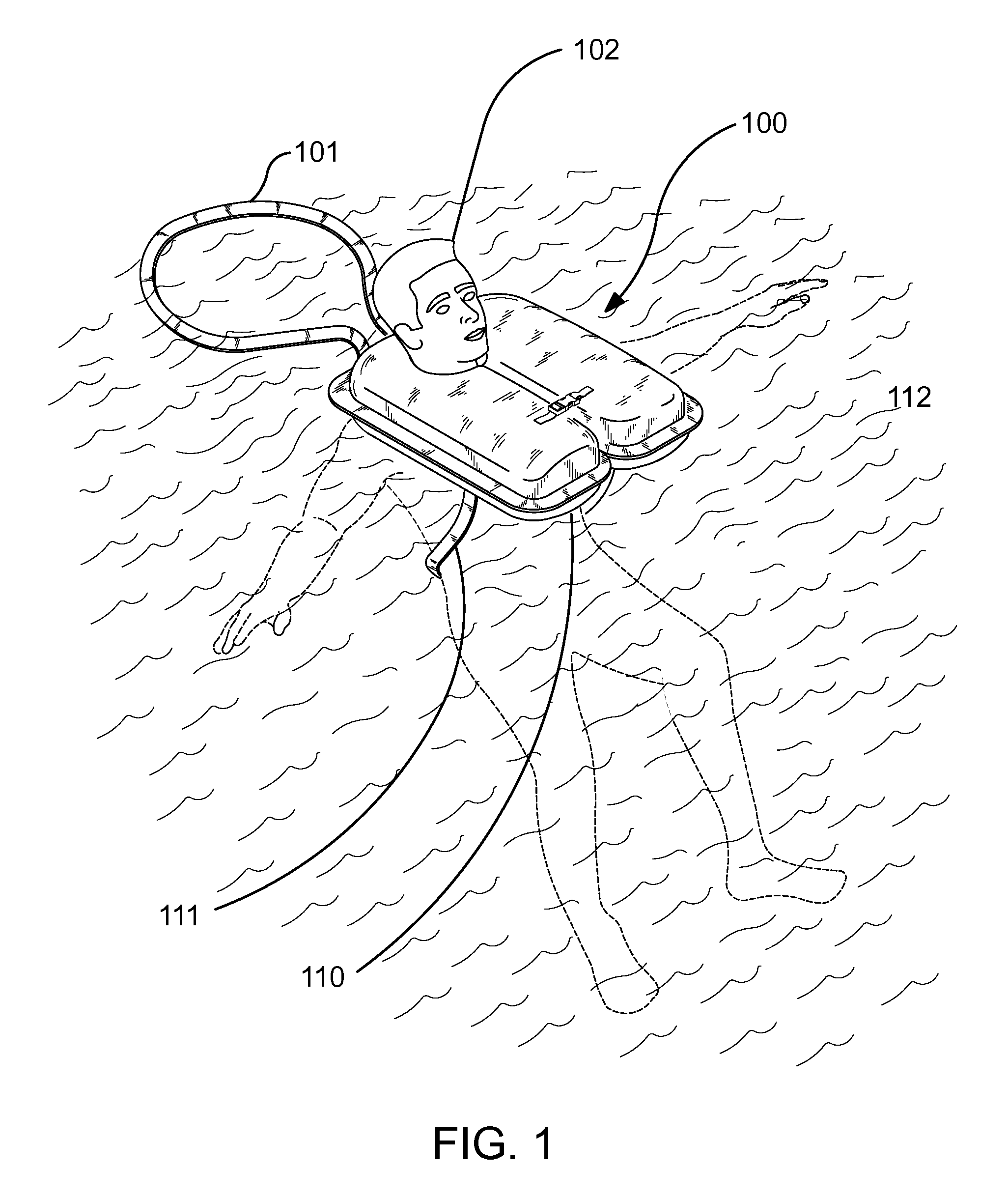
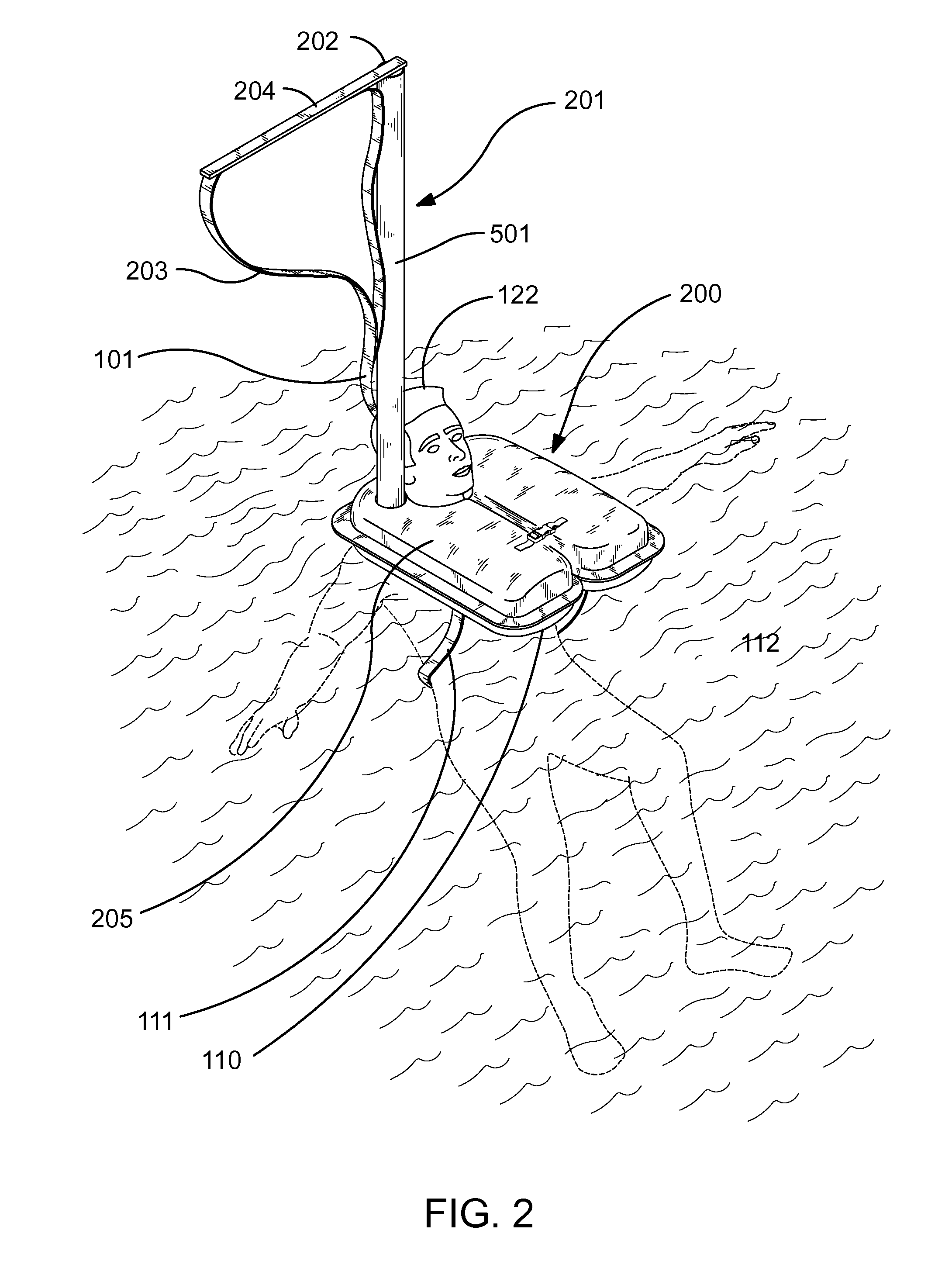
InactiveUS7927162B1Strengthen security controlGaining controlLife-buoysVessel signalling devicesTetheringCombined use
A multi-functional, personal flotation device provides a life preserver for a person in combination with an integrated tethering system to aid in retrieval of the wearer. The integrated tethering system may be used alone or in conjunction with an integrated signaling device. The integrated signaling device extends when the life preserver is use. The integrated tethering system facilitates the recovery of a person wearing the multi-functional, personal flotation device. The integrated signaling device or the integrated tethering system may also include a sound or a visual alarm.
Owner:DOUBLEDAY MARC D
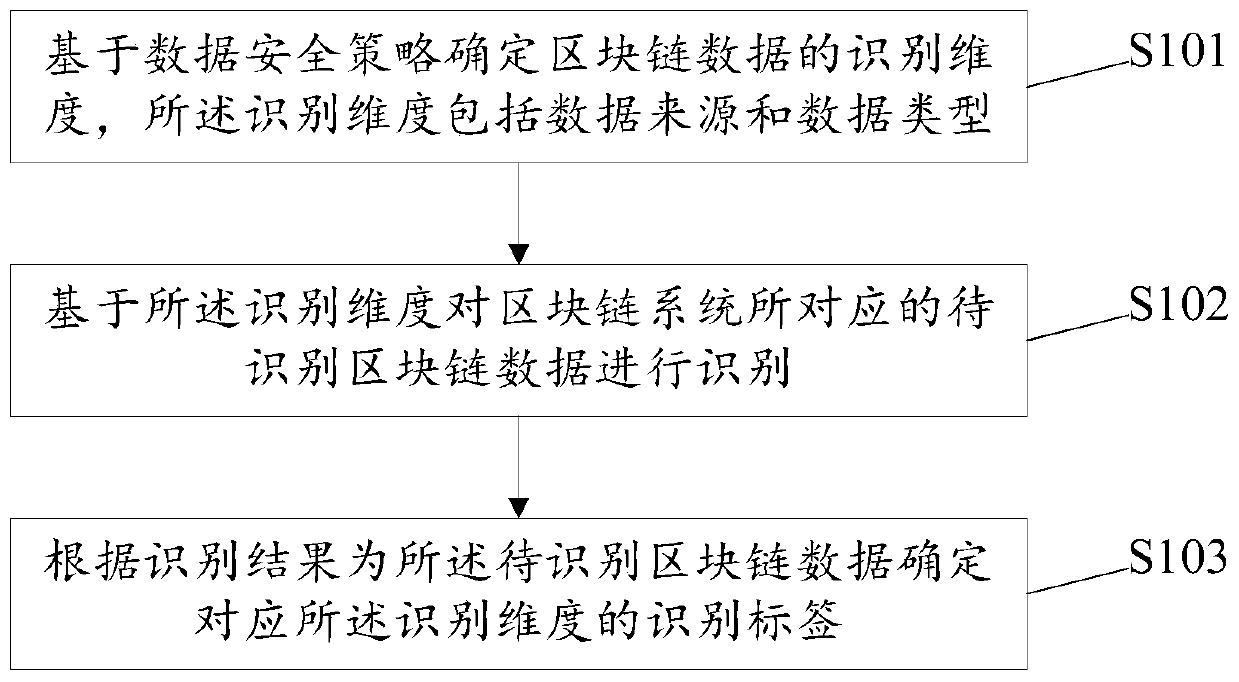
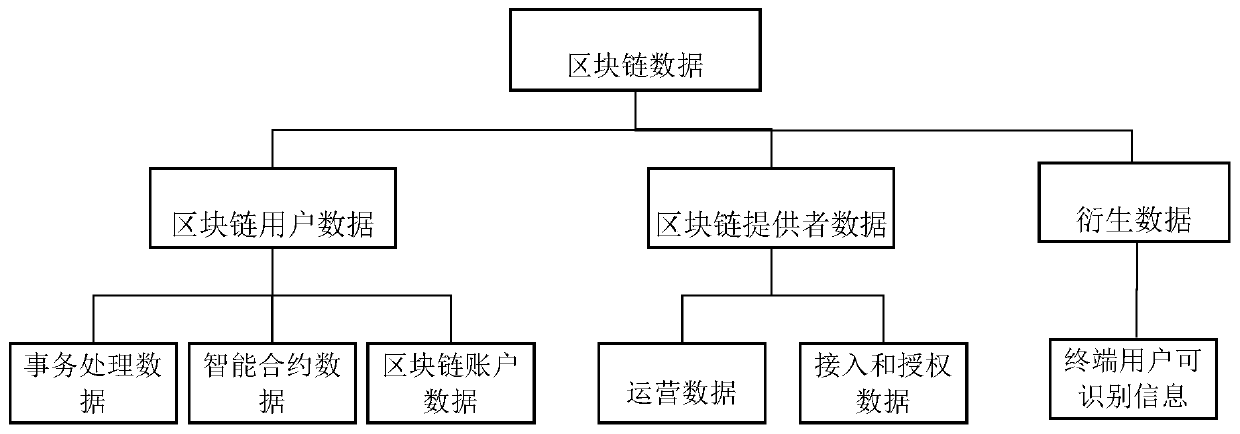
Data safety policy-oriented blockchain data recognition method and related device
The embodiment of the invention discloses a data safety policy-oriented blockchain recognition method and a related device. The method comprises the following steps: determining an recognition dimension of blockchain data according to a data safety policy, wherein the recognition dimension comprises a data source and a data type of the blockchain data; and identifying the to-be-identified block chain data in the block chain system according to the recognition dimension, wherein the recognition result is that an recognition tag corresponding to the recognition dimension is determined for the to-be-identified block chain data. The recognition tag identifies the data source and the data type of the blockchain data; therefore, the blockchain data is identified according to the recognition tag;different types of blockchain data in the blockchain system can be classified from two dimensions of a data source and a data type, so that management is performed according to different data safetylevels based on different types of blockchain data, and safety management and control of the blockchain system are improved.
Owner:CHINA ELECTRONICS STANDARDIZATION INST
Mobile X-ray unit
ActiveUS9724066B2Efficiently determinedStrengthen security controlMaterial analysis using wave/particle radiationRadiation diagnostics testing/calibrationDosimeterX-ray generator
One embodiment of the present disclosure is directed to a mobile X-ray unit. The mobile X-ray unit may include an X-ray applicator for emitting an X-ray beam for irradiating an object. The mobile X-ray unit may further include a phantom-based dosimetry system configured to perform a dosimetry check of the X-ray beam. The phantom-based dosimetry system may include two sets of dose meters, each set being positioned on a surface at a distinct depth. The mobile X-ray unit may also include a dosimetry control unit configured to receive measurements from the two sets of dose meters and determine whether the dosimetry check is passed based on the measurements.
Owner:NUCLETRON OPERATIONS
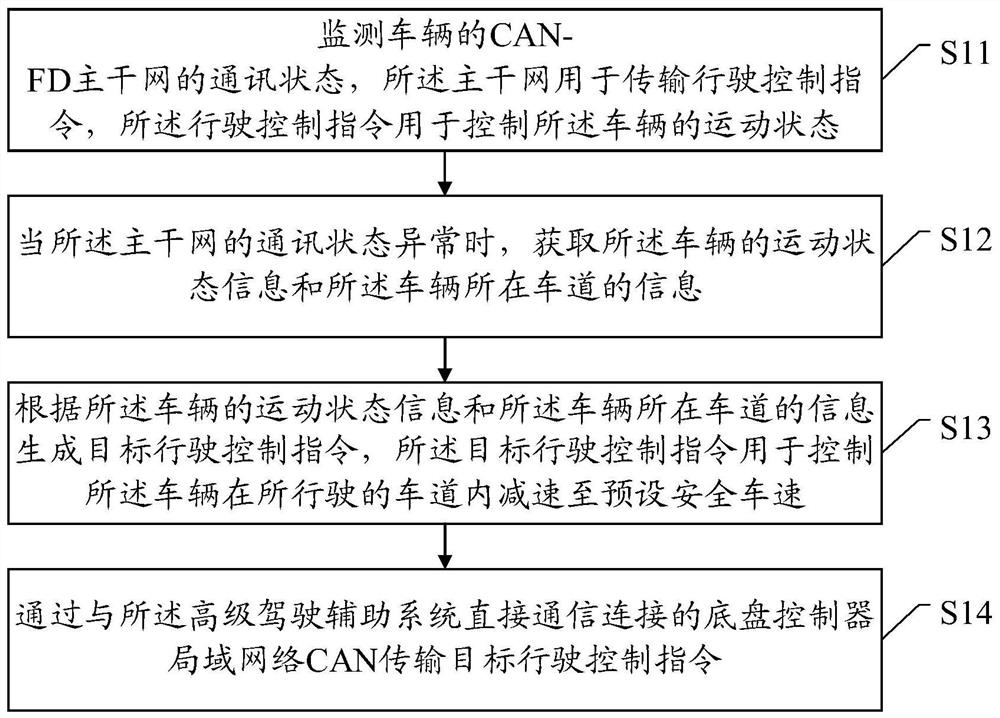
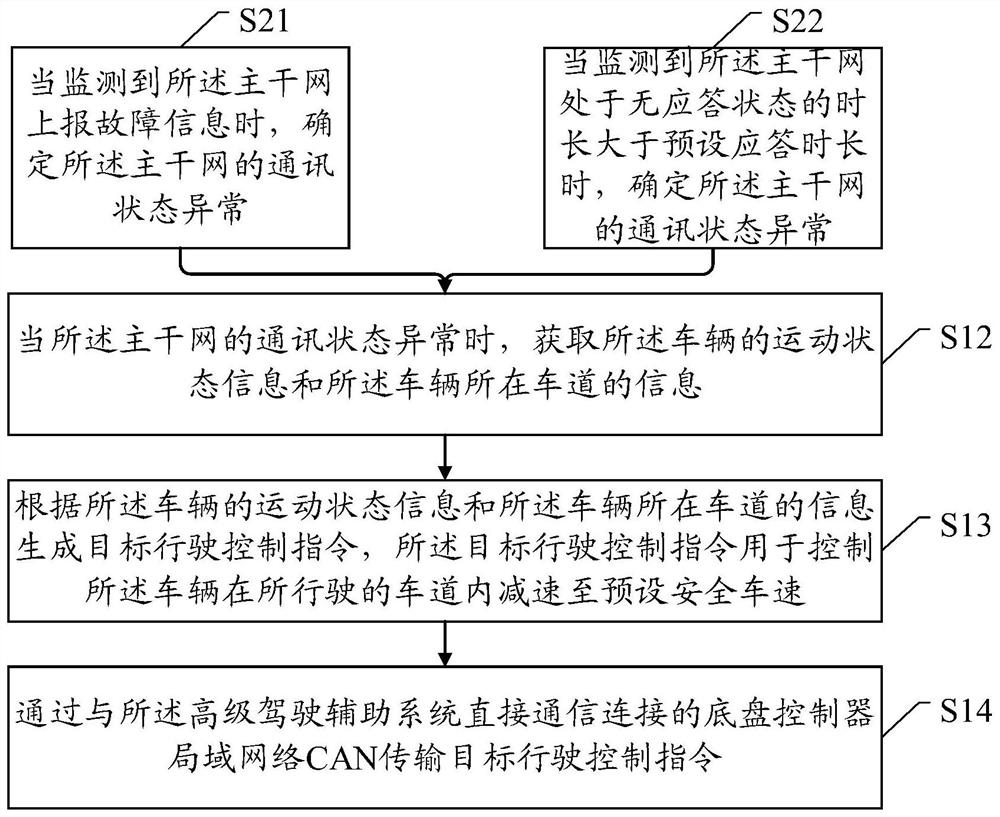
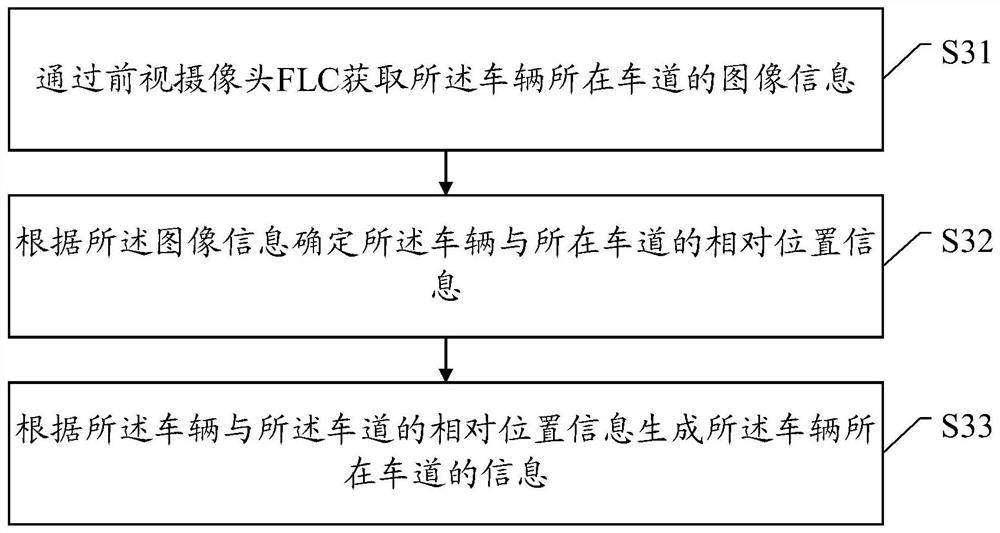
Vehicle safety control method, device and system
The invention discloses a vehicle safety control method, device and system. The method, the device and the system are used for solving the problem that a vehicle is out of control due to backbone network communication faults. The method comprises the steps that the communication state of a CAN-FD backbone network of a vehicle is monitored, wherein the backbone network is used for transmitting a driving control instruction, and the driving control instruction is used for controlling the motion state of the vehicle; when the communication state of the backbone network is abnormal, motion state information of the vehicle and information of a lane where the vehicle is located is acquired; a target driving control instruction is generated according to the motion state information of the vehicleand the information of the lane where the vehicle is located, wherein the target driving control instruction is used for controlling the vehicle to decelerate to a preset safe vehicle speed in the driving lane; and a target driving control instruction is transmitted through a chassis controller area network (CAN) which is in direct communication connection with the advanced driving assistance system. According to the scheme, after abnormal communication of the backbone network is monitored, vehicle safety control is directly achieved through the CAN, the probability of traffic accidents caused by out-of-control of the vehicle is reduced, and the vehicle control safety is improved.
Owner:EVERGRANDE NEW ENERGY AUTOMOTIVE INVESTMENT HLDG GRP CO LTD
Method and system for providing password resources and host machine
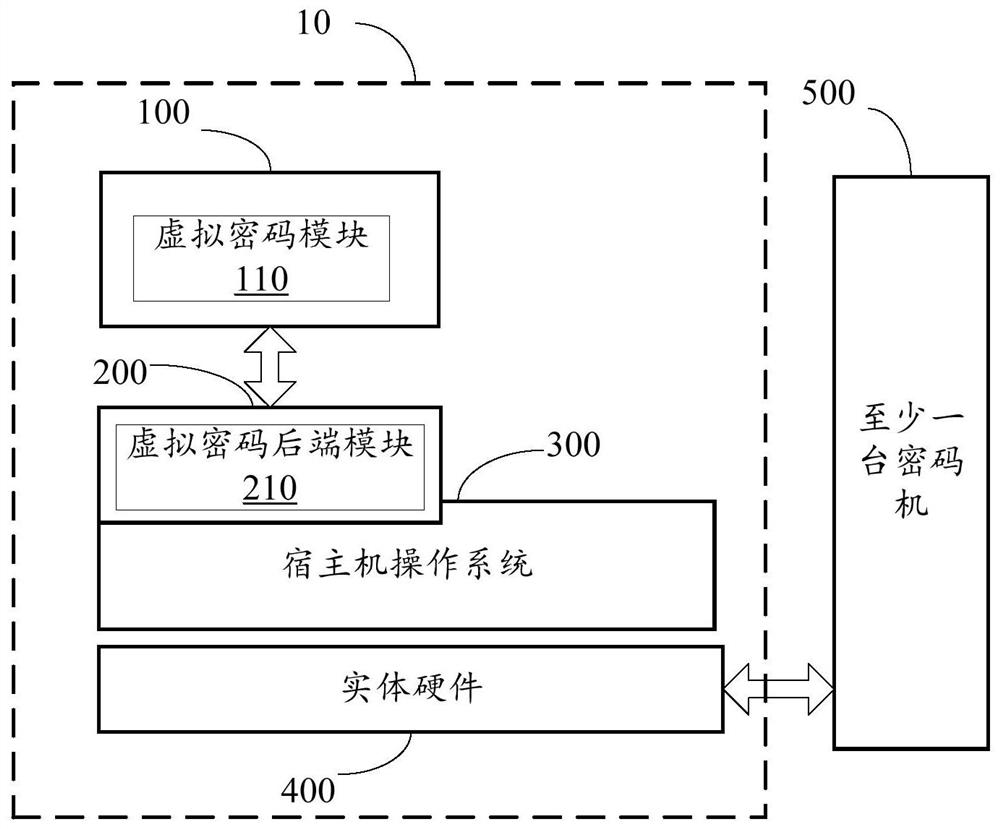
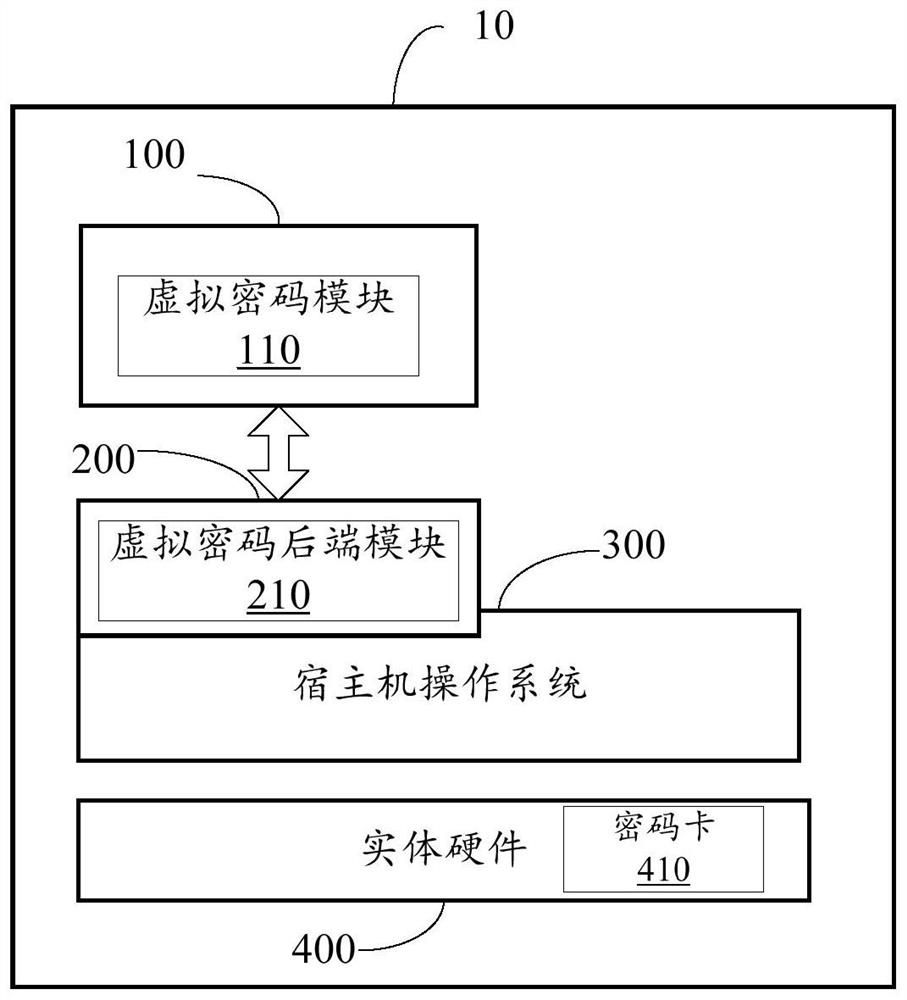
PendingCN111782344AEasy security controlEasy to achieve complianceDigital data protectionDigital data authenticationPasswordSoftware engineering
The embodiment of the invention provides a method and system for providing password resources and a host machine, at least one virtual machine runs on the host machine, and the host machine comprisesa virtual password module running on the virtual machine; and a virtual password back-end module which is configured to map a password function of a password function component to the virtual passwordmodule, and the password function comprises password calculation or key management. According to the embodiment of the invention, password calculation and key management presented by the virtual password module are completed in password resources on the host machine side, so that compliance is easier to realize, and security control is easier to perform.
Owner:BEIJING CERTIFICATE AUTHORITY
Household electrical appliance control and household safety system for the blind and control method thereof
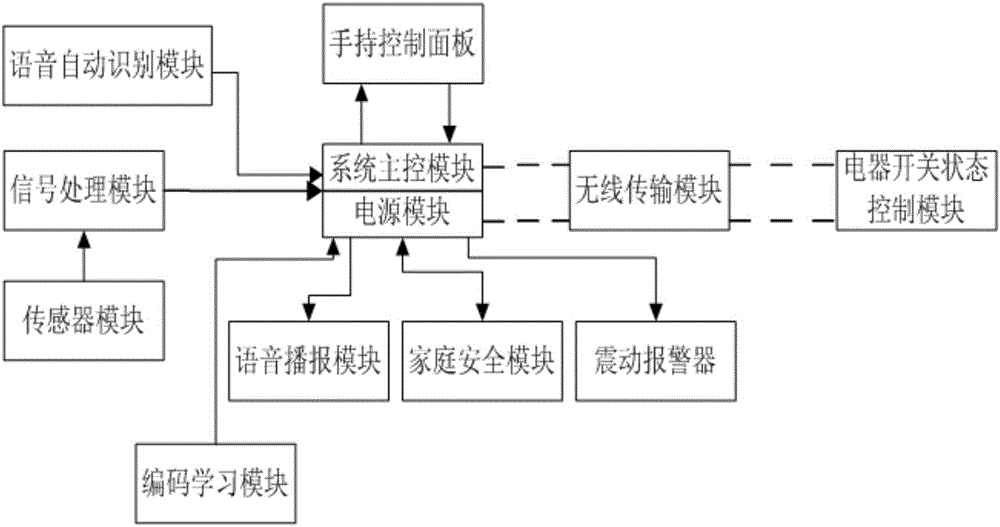
InactiveCN105843063AAddressing Security Control IssuesAvoid controlComputer controlProgramme total factory controlRemote controlOperability
The invention discloses a household electrical appliance control and household safety system for the blind and a control method thereof. The system comprises a system main control module, a handheld control panel, a wireless transmitting module, an electrical appliance switch state control module, a sensor module, a signal processing module, a voice automatic recognizing module, a code learning module, a voice broadcasting module, a household safety module and a power supply module. For an electrical appliance with a remote control, the remote control, the code learning module and the system main control module are connected so that the control panel is controlled through buttons. For an electrical appliance with no remote control, the handheld control panel sends orders to the system main control module through the pressing buttons to control the switch of the electrical appliance. The voice automatic recognizing module also does corresponding control. The sensor module acquires the environmental conditions inside a room, and infrared detection is available to check the opening and closing of a door and a window. With that, the check results are delivered to the blind through the voice broadcasting module. These designs enable the blind to conduct real time check on the household electrical appliance safety. With high safety performances and good operability, the system makes the blind stay safe at home.
Owner:西安众恒科技有限公司
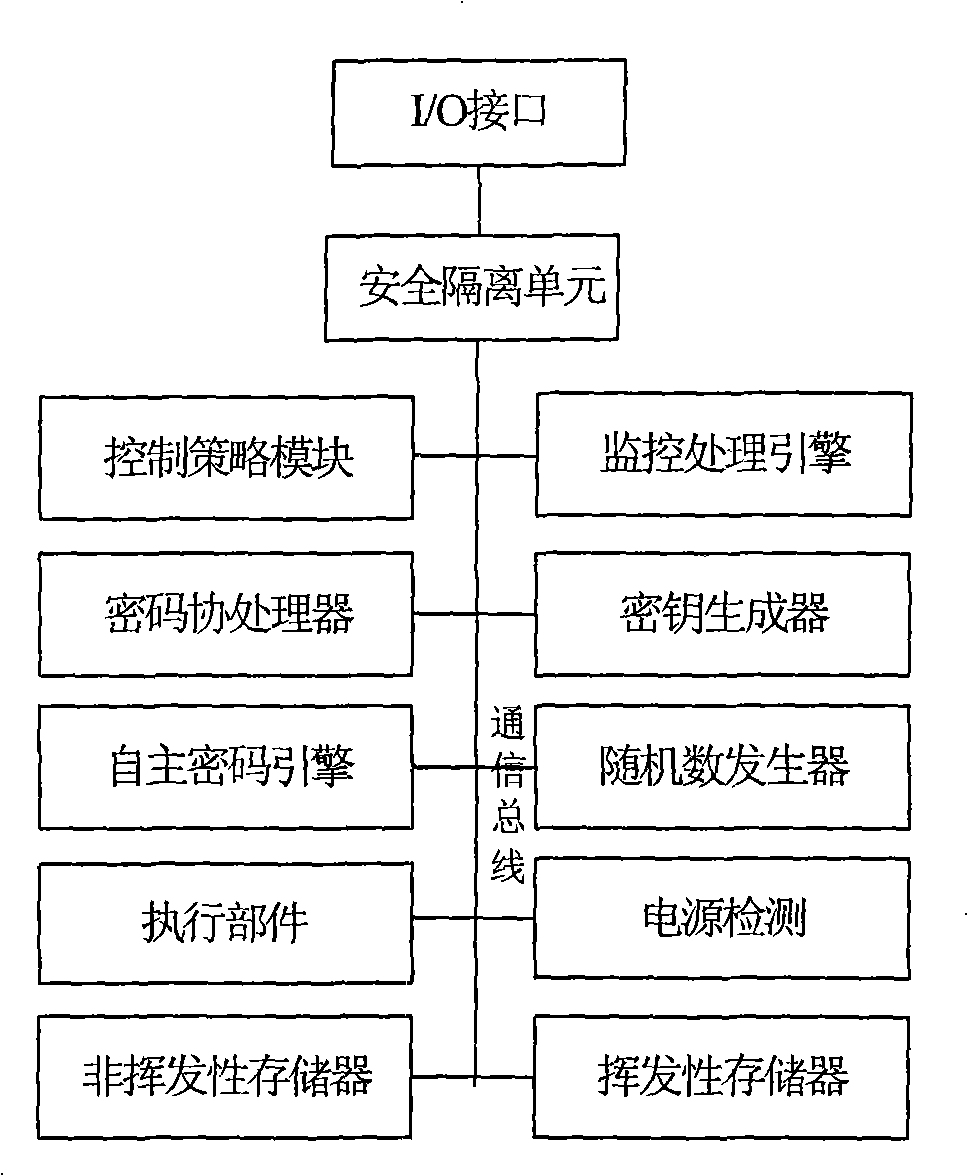
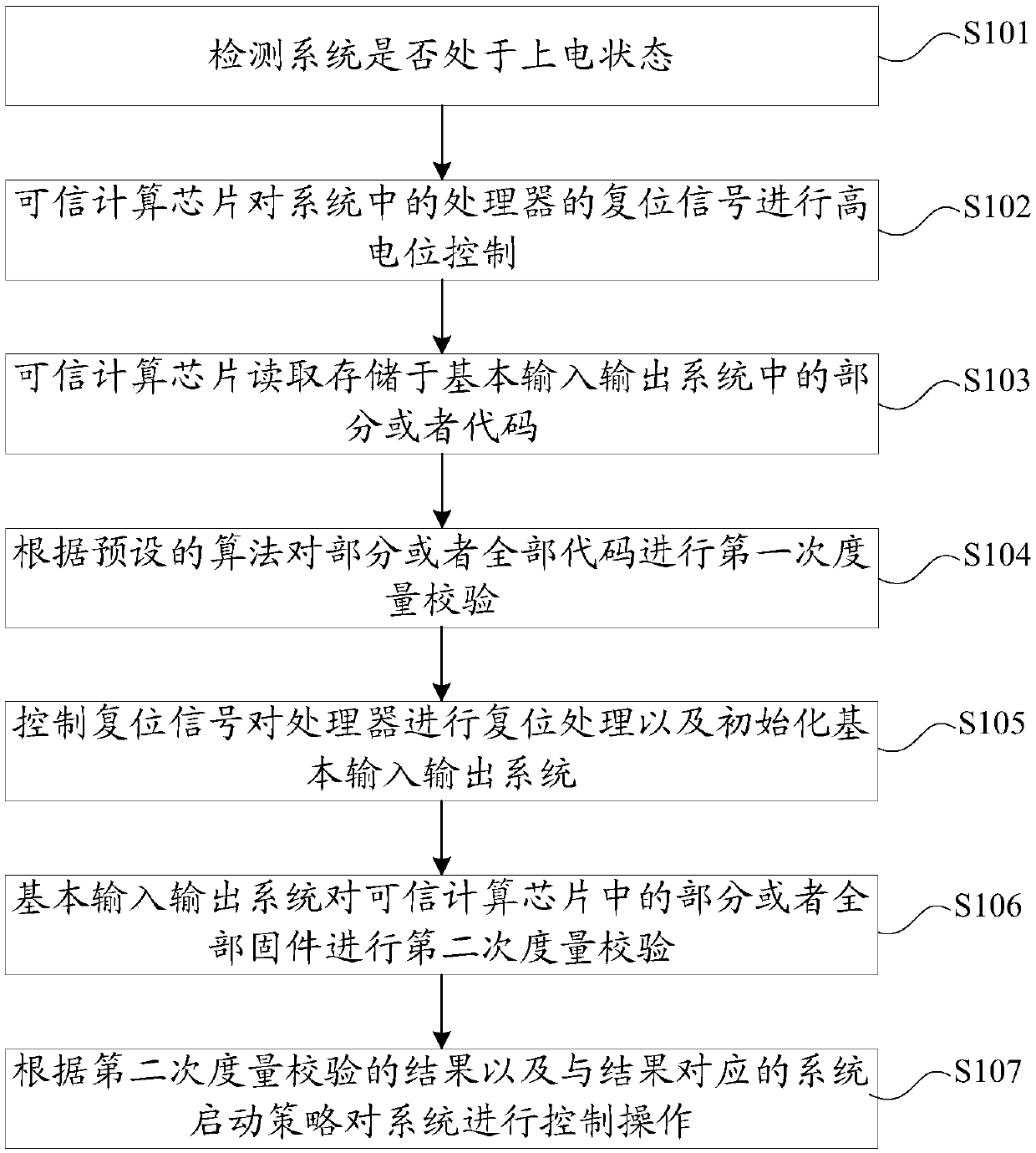
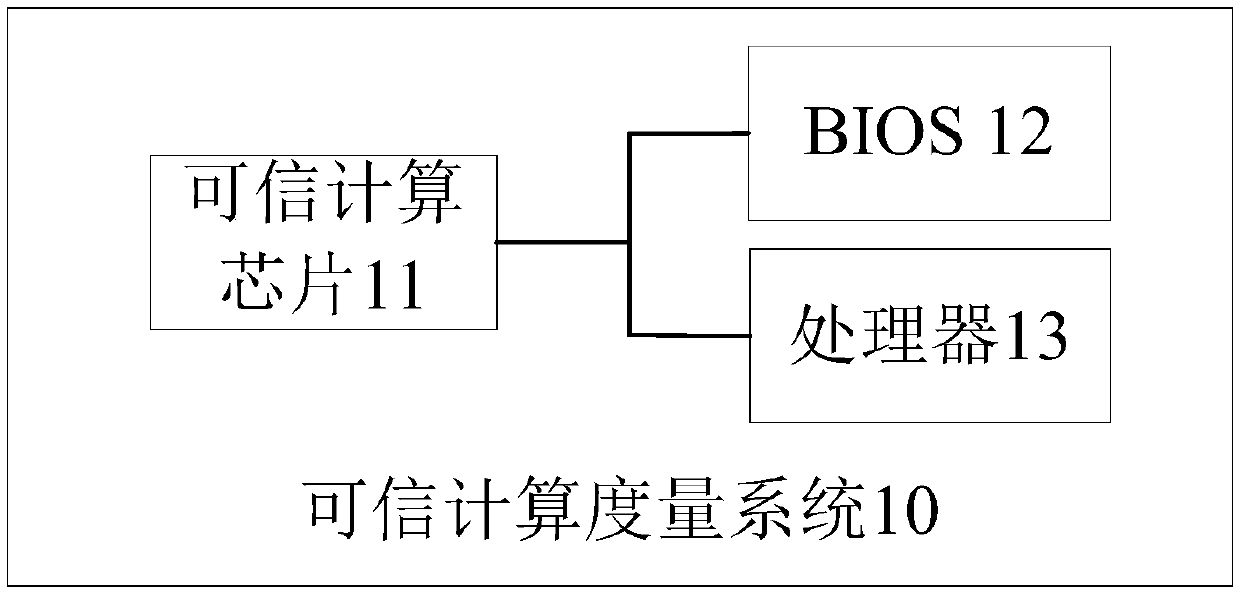
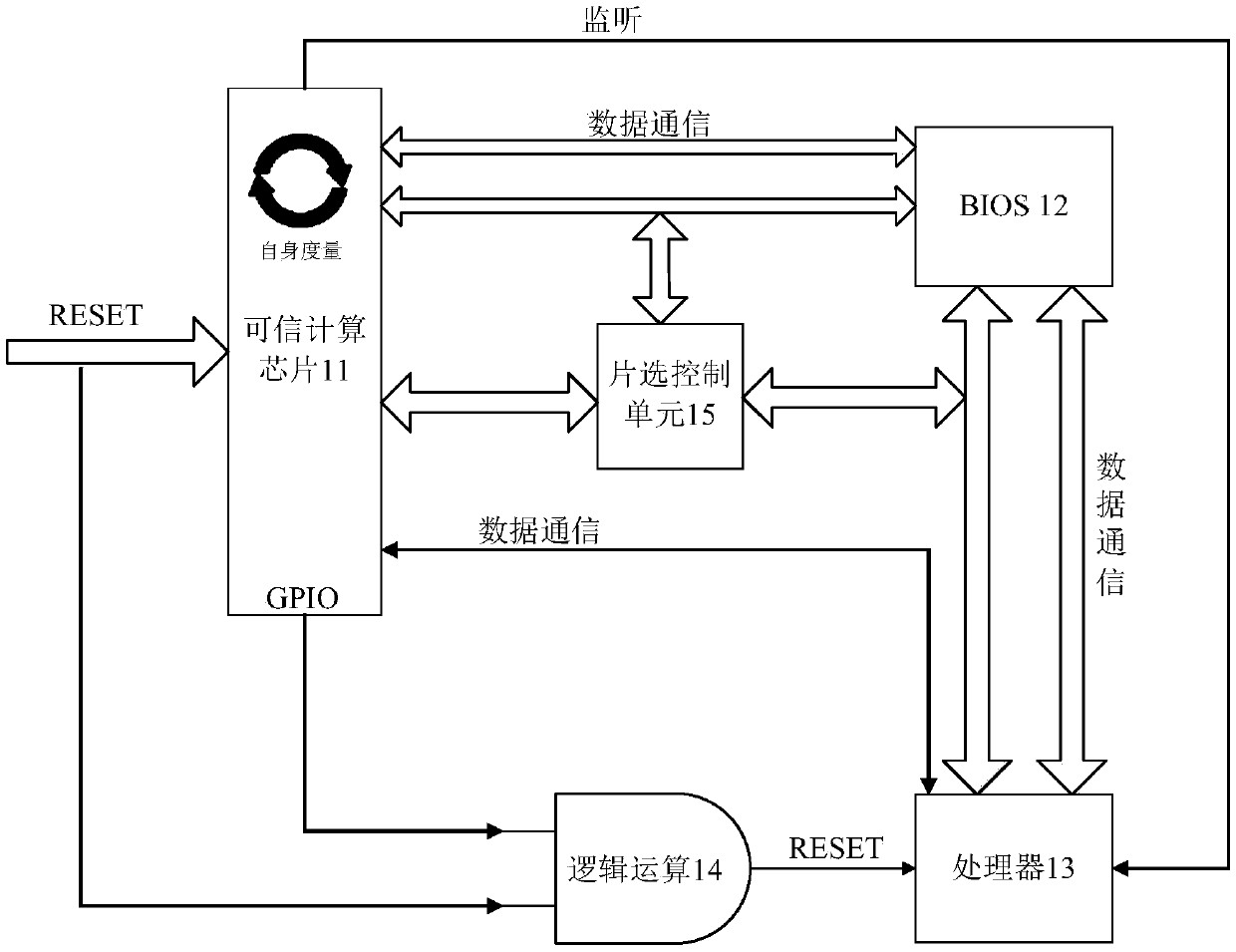
Trusted computing measurement method and system and computer readable storage medium
PendingCN110659498AStrengthen security controlImprove accuracyPlatform integrity maintainanceOperational systemTrusted Computing
The invention provides a trusted computing measurement method and system and a computer readable storage medium. High-potential control is carried out on a reset signal of a processor in a system before the system is powered on and a BIOS is initialized, so thata processor cannot be reset, according to a preset algorithm, the first measurement verification on codes in the BIOS can be carried out,and when the verification is passed, controlling a reset signal to reset the processor and initialize a BIOS, the second measurement verification is carried out on firmware in the trusted computing chip by the BIOS, and finally the control operation is carried out on the system according to a system starting strategy corresponding to a result of the second measurement verification. Through the mutual metric verification, the accuracy of metric calculation in the system is improved, the BIOS exception is judged in advance, the effective security control of the computer before the operating system is started is enhanced, and the problem that data is still tampered in an existing one-way trusted calculation metric mode is solved.
Owner:NATIONZ TECH INC
Features
- R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
Why Patsnap Eureka
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Social media
Patsnap Eureka Blog
Learn More Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com