Credible computing system
A trusted computing and trusted technology, applied in the field of information security, can solve the problem of not taking into account the need for real-time updating of BIOS codes, and achieve the effect of improving request response speed and data transmission time, improving flexibility, and realizing security protection.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
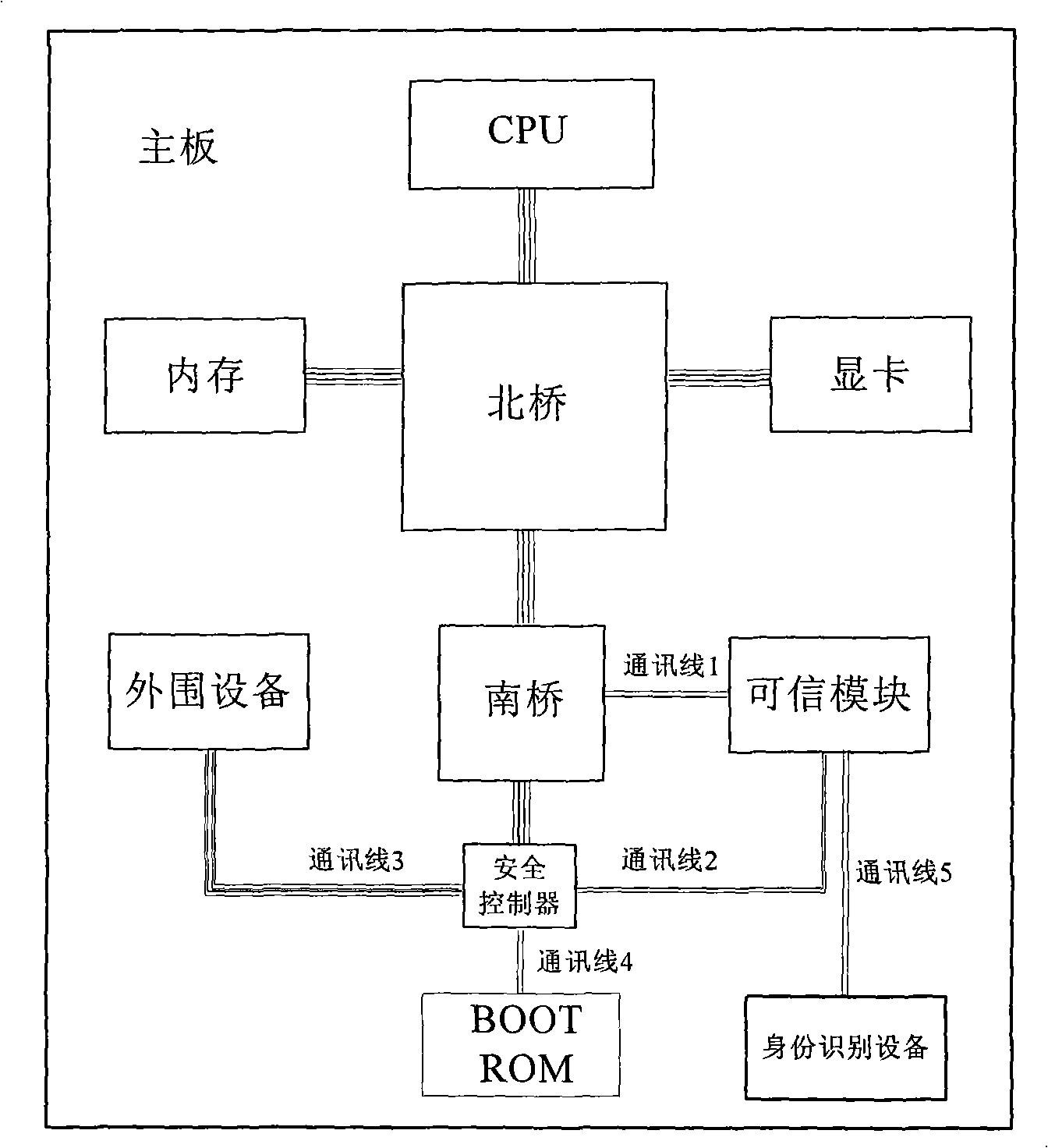
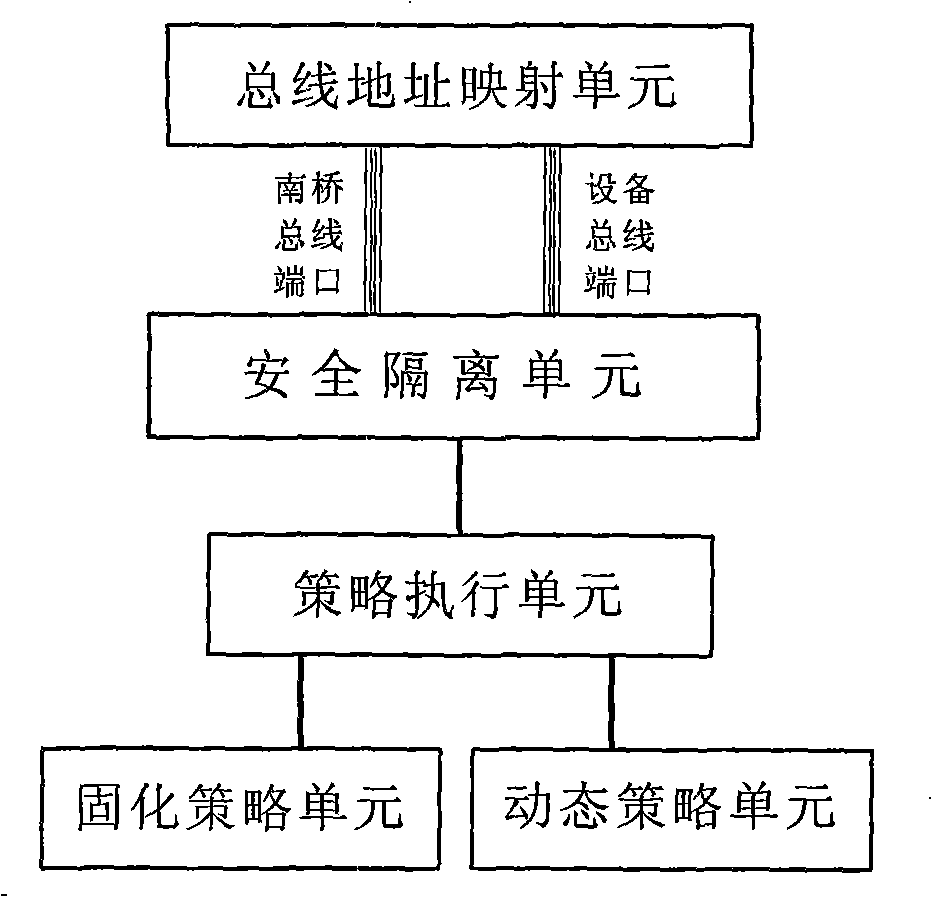
[0045] Computer hardware modifications, such as figure 1 Shown:
[0046] 1) A safety controller is set on the computer hardware platform, and the control signal line is connected to the south bridge device controller of the computer main board through the data line.
[0047]2) BOOT ROM and motherboard peripherals are connected to the output terminal of the safety controller through data lines and control signal lines.
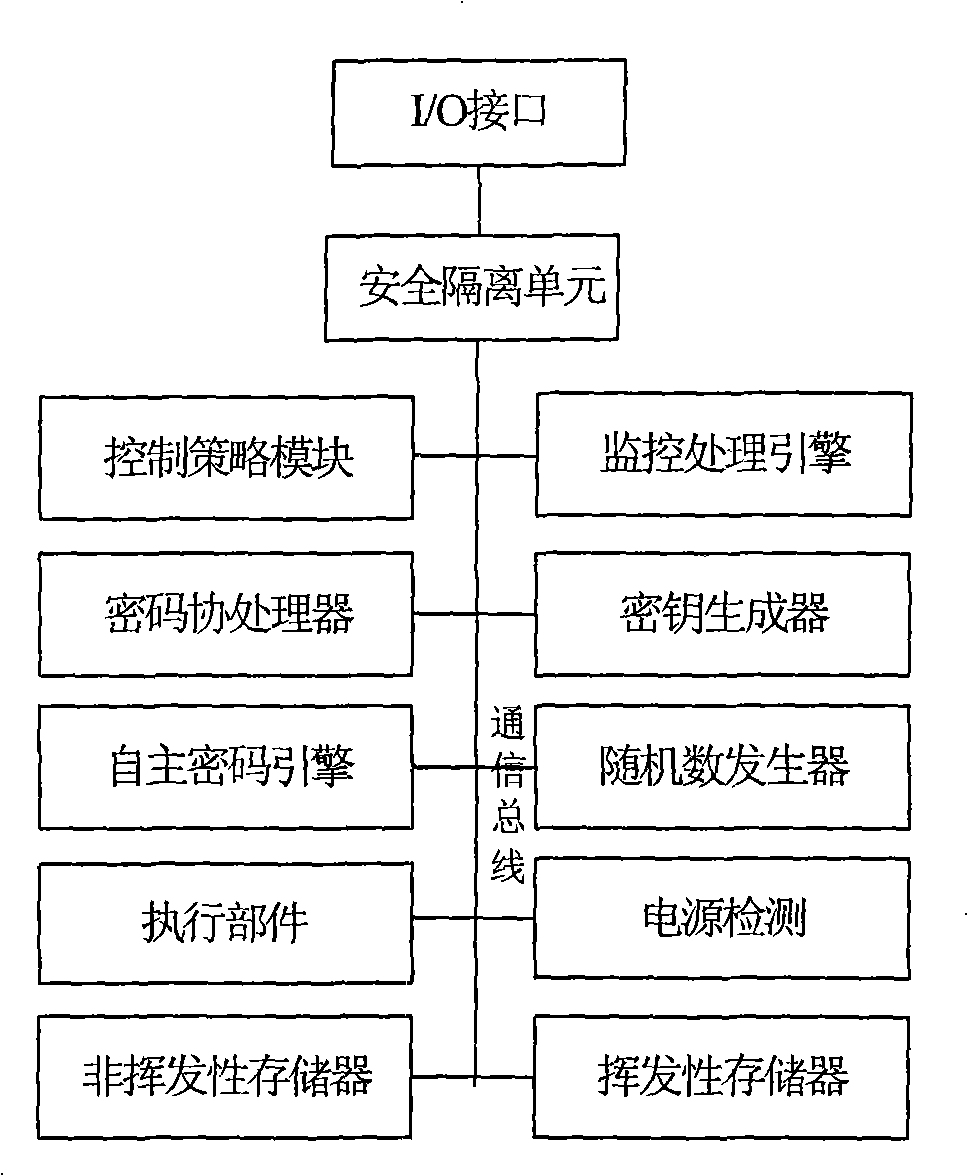
[0048] 3) As a slave device, the trusted security module is connected to the south bridge device controller of the computer through its LPC communication interface or USB communication interface.
[0049] 4) The trusted security module is used as the control terminal and is connected with the security controller through the communication bus for control and data transmission.
[0050] 5) BOOT ROM, security controller, BIOS backup storage unit, identification device and trusted security module use the same power system, and this power system is independent fro...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com