Information security transmission system and method with group decryption authority control
An information security and authority control technology, applied in transmission systems, digital transmission systems, and key distribution, can solve the problems of low encryption strength, shortened cracking time, and low encryption strength of encryption methods, so as to improve anti-quantum computing capabilities and ensure Strong implementation effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
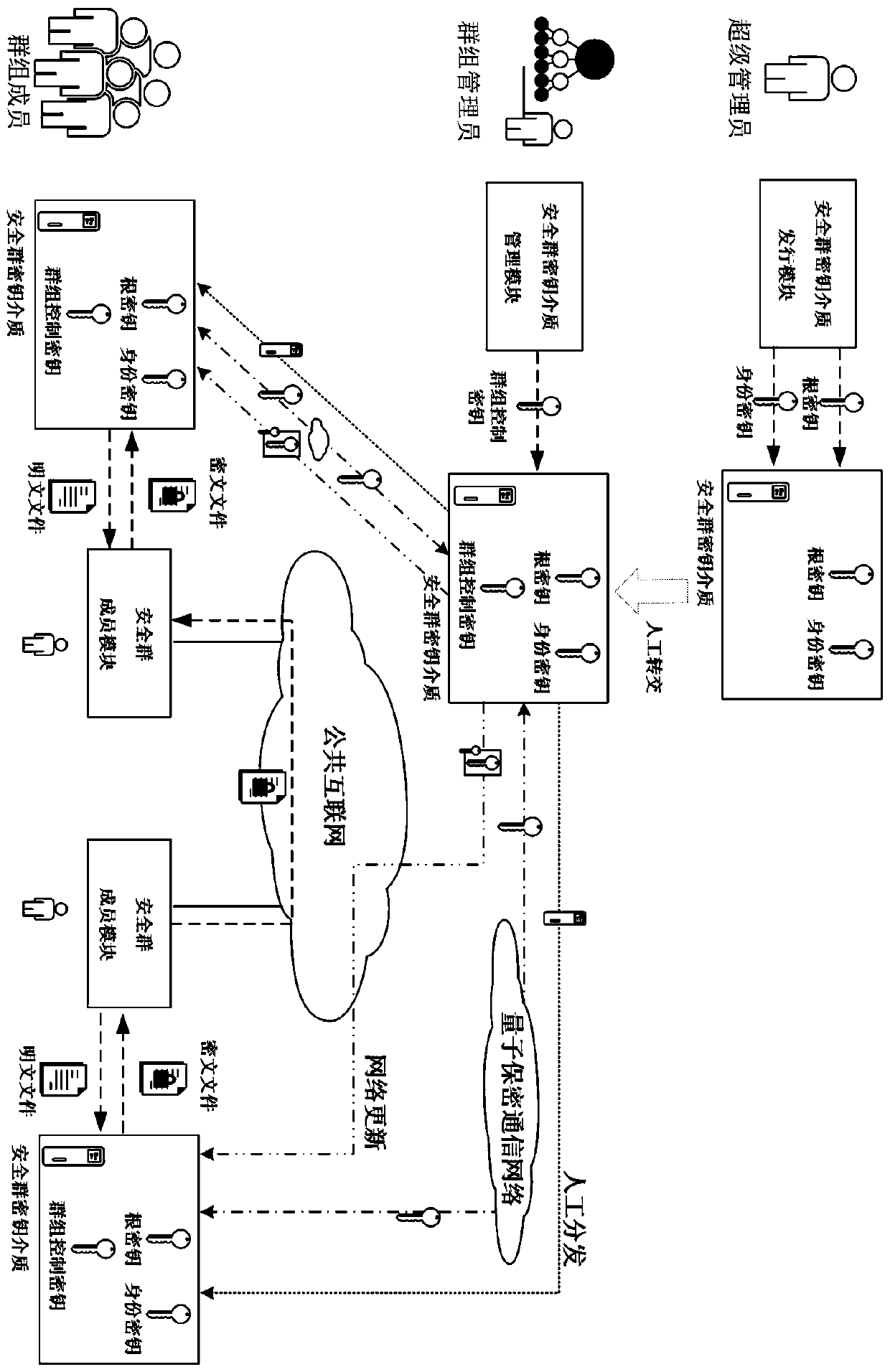
[0085] Embodiment 1: In the embodiment of the present invention, the super administrator is the information security administrator of a multinational company, the group administrator is the marketing department manager of the company, and the group members are the marketing personnel of the marketing department; the marketing department manager needs to regularly Summarize the latest customer information of all marketing personnel, and regularly release market task assignments to all market personnel, and send documents such as bidding quotations to specific market personnel when necessary; market personnel have the need to report and receive relevant documents at home and abroad, And the network used is the public Internet, security cannot be guaranteed.
[0086] According to an information security transfer method with group decryption authority control described in the present invention, this embodiment includes the following steps:
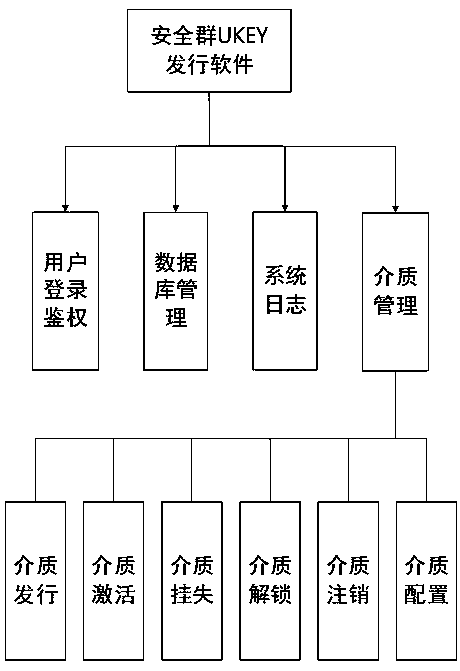
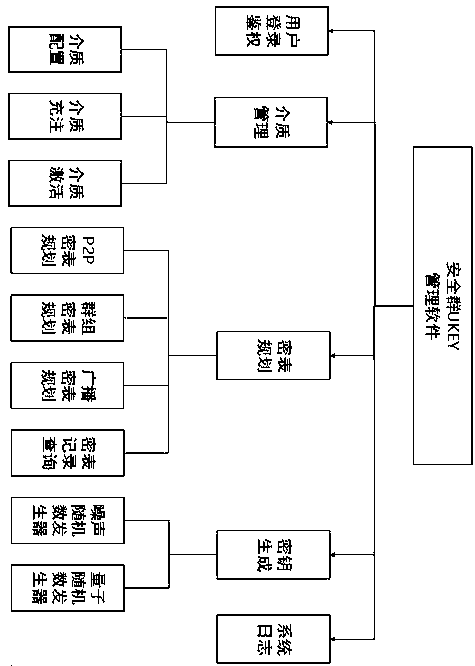
[0087] Step 1: Security group UKEY init...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com