High-interaction SSH honeypot implementation method
An implementation method and high-interaction technology, applied in electrical components, transmission systems, etc., can solve the problems of low interaction of medium and low interaction SSH honeypots, update and change SSH attacks, and insufficient decoy, so as to improve the value of honeypots, The effect of reducing complexity and facilitating intuitive observation
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0029] The present invention will be further described below in conjunction with the accompanying drawings. The following examples are only used to illustrate the technical solution of the present invention more clearly, but not to limit the protection scope of the present invention.
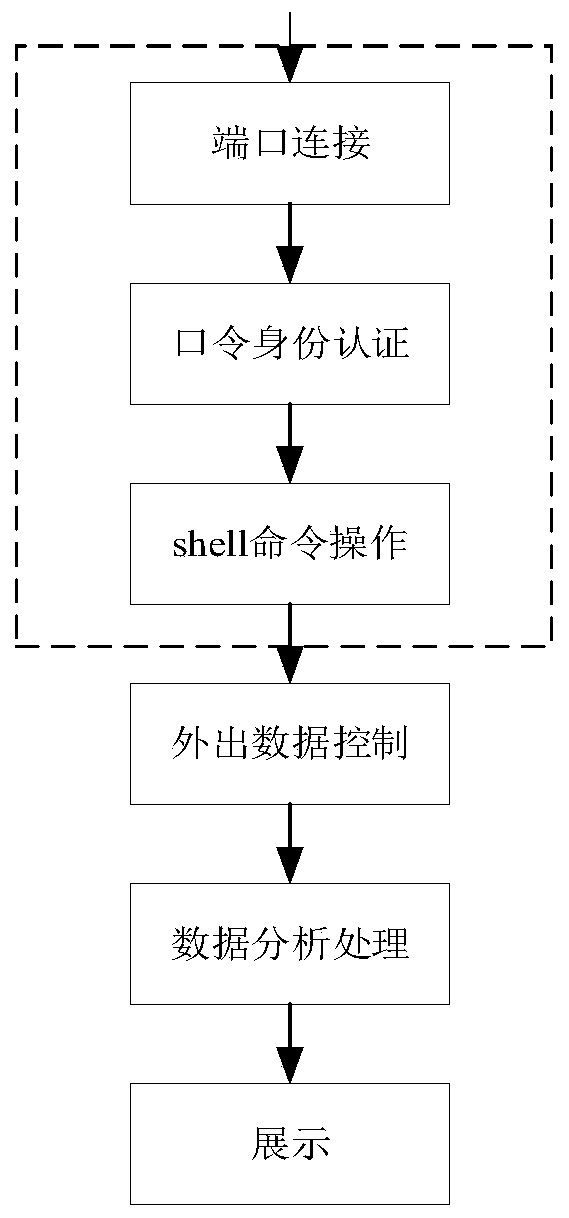
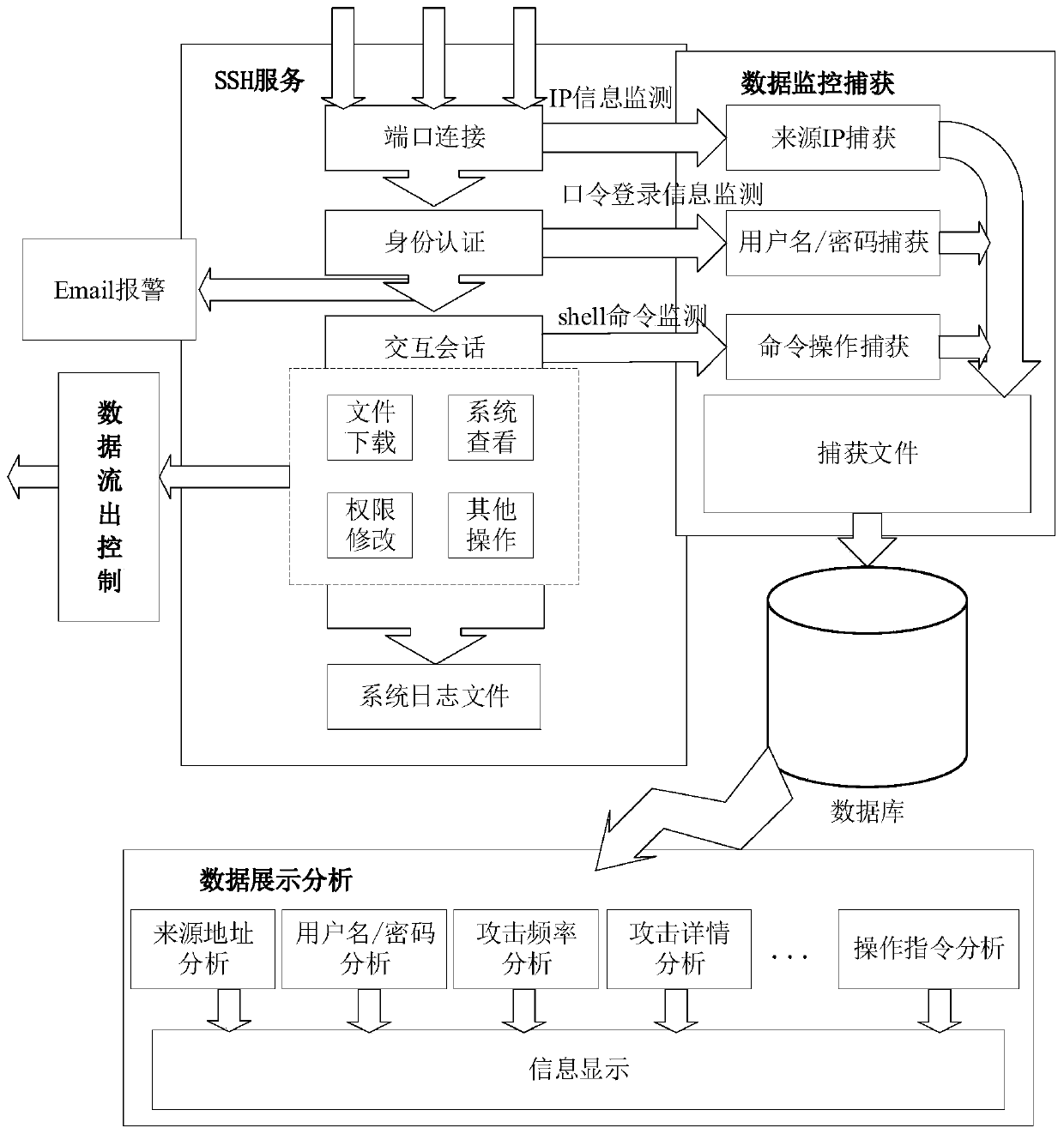
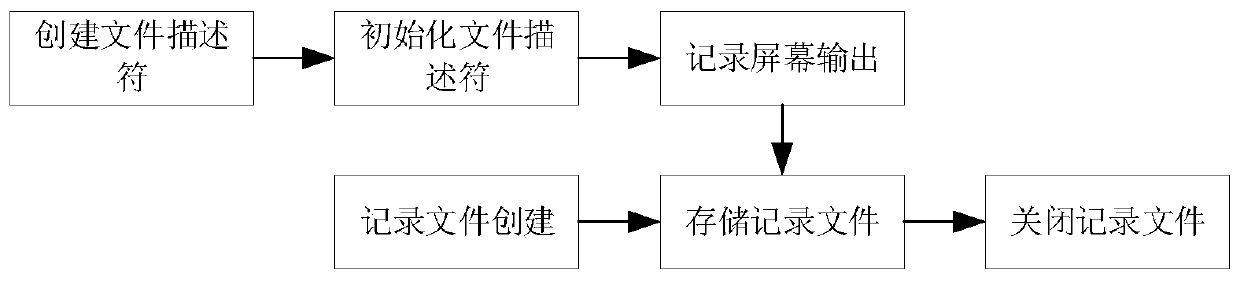
[0030] Such as figure 1 and figure 2 As shown, a kind of highly interactive SSH honeypot implementation method provided by the present invention: comprises the following steps:
[0031] Step 1: Try to connect to the SSH port of the system to determine whether there is SSH service, and if there is SSH service, go to step 2.
[0032] Step 2: Use the logit function and the authctxt structure in OpenSSH to capture the authenticated username / password during password identity authentication. The specific operation steps are: (1) decrypt the password information on the server; (2) store the password in the authctxt structure (3) record the user name and password in the authctxt structure through the...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com