Industrial control intrusion detection method based on multi-classification GoogLeNet-LSTM model
A technology of intrusion detection and intrusion detection system, which is applied in the field of security, can solve problems such as inability to perform timing detection, difficulty in intrusion behavior, and high false alarm rate, and achieve the effects of improving timing detection capabilities, high use value, and high detection efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] The present invention will be described in detail below in conjunction with specific embodiments shown in the accompanying drawings.
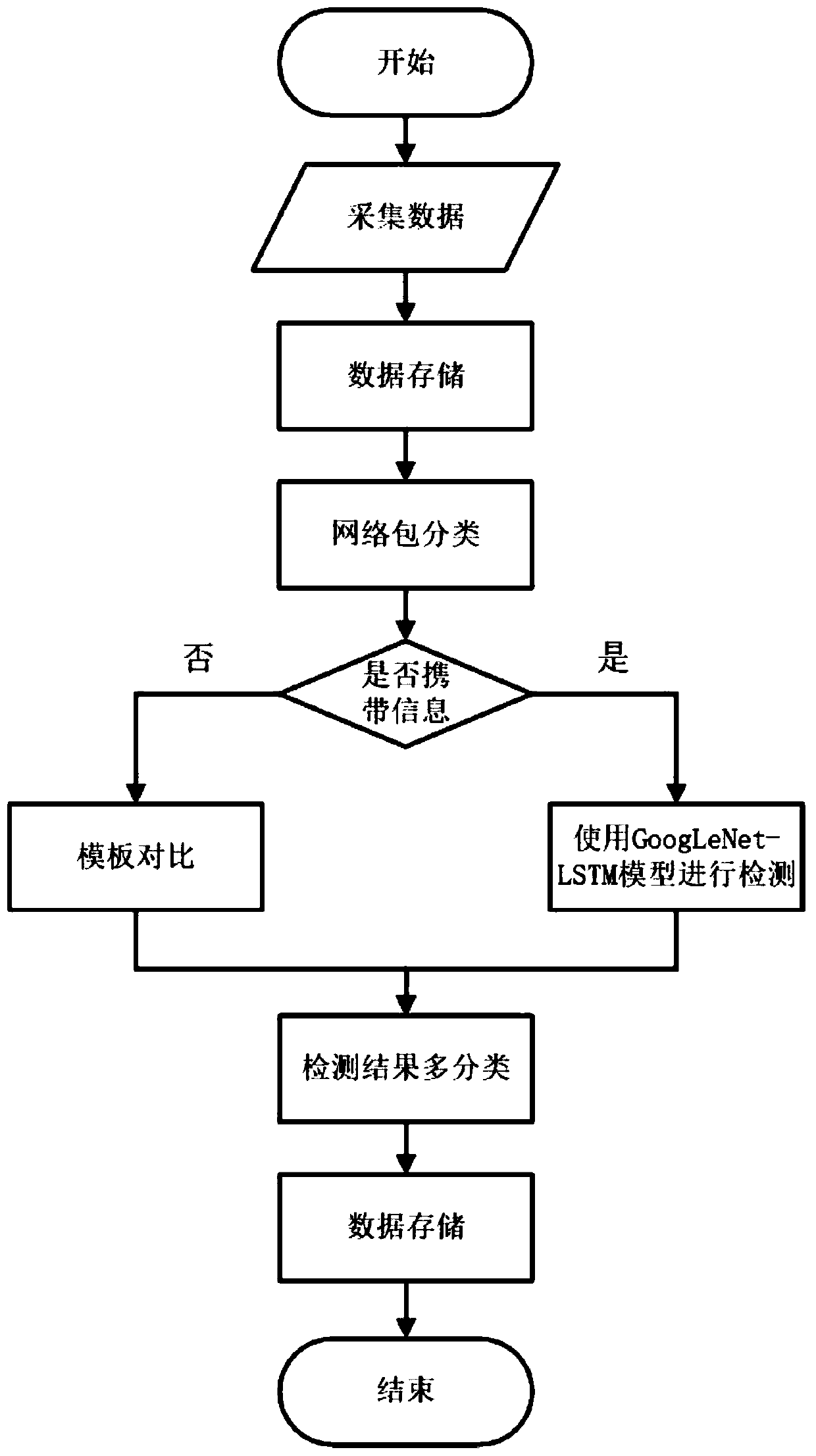
[0025] figure 1 It is an industrial control intrusion detection method diagram based on the multi-classification GoogLeNet-LSTM model, including:
[0026]The data acquisition module uses the SCADA system to capture industrial control data. The collected data includes not only the system status data obtained by reading the sensor, but also the control data from the host. The collected data is divided into two types: training data and test data. The collected network packets carrying data and the network packets not carrying data used as requests and confirmations are stored in the cache sequence for subsequent intrusion detection, information addition and network packet storage.
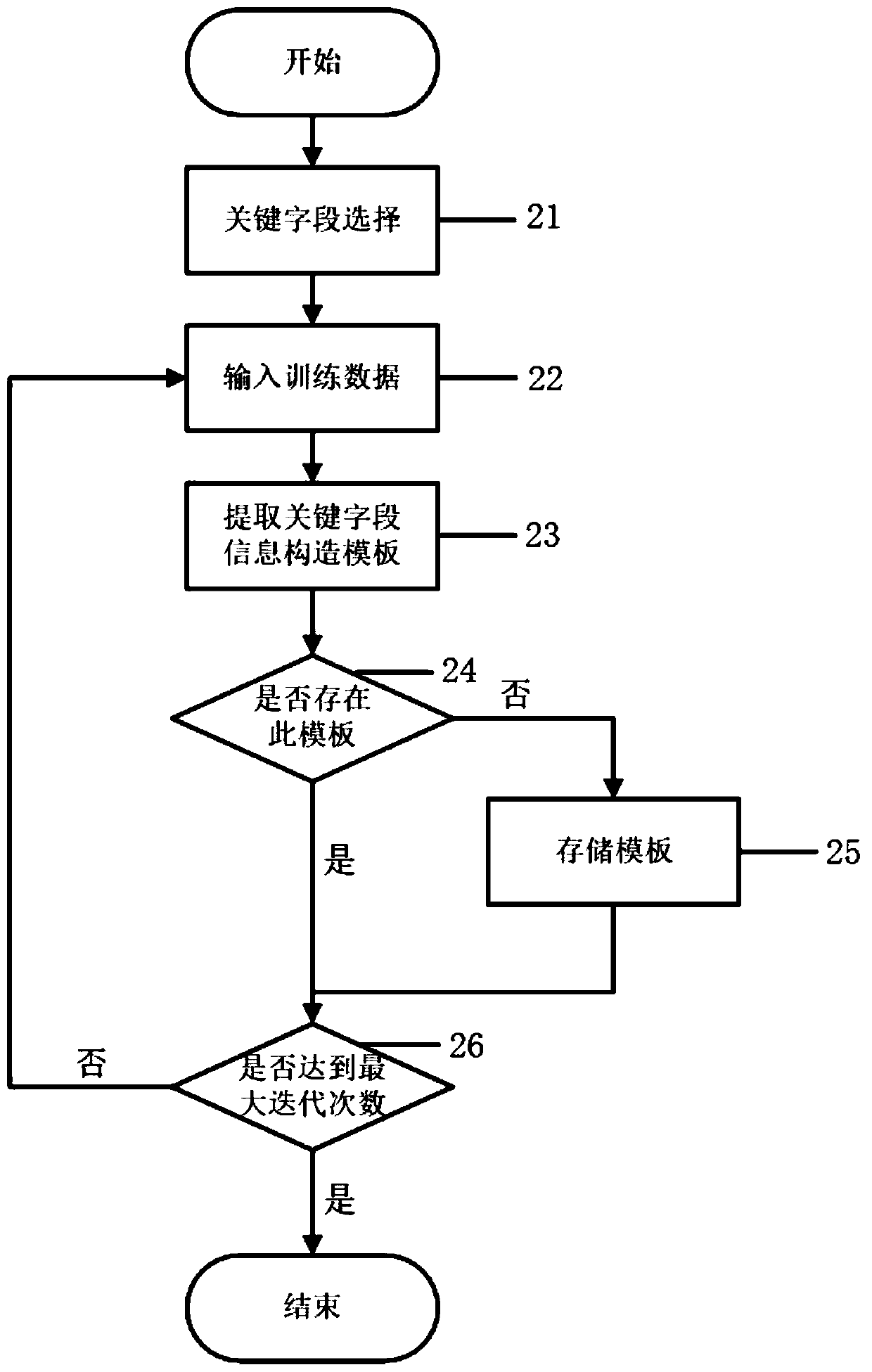
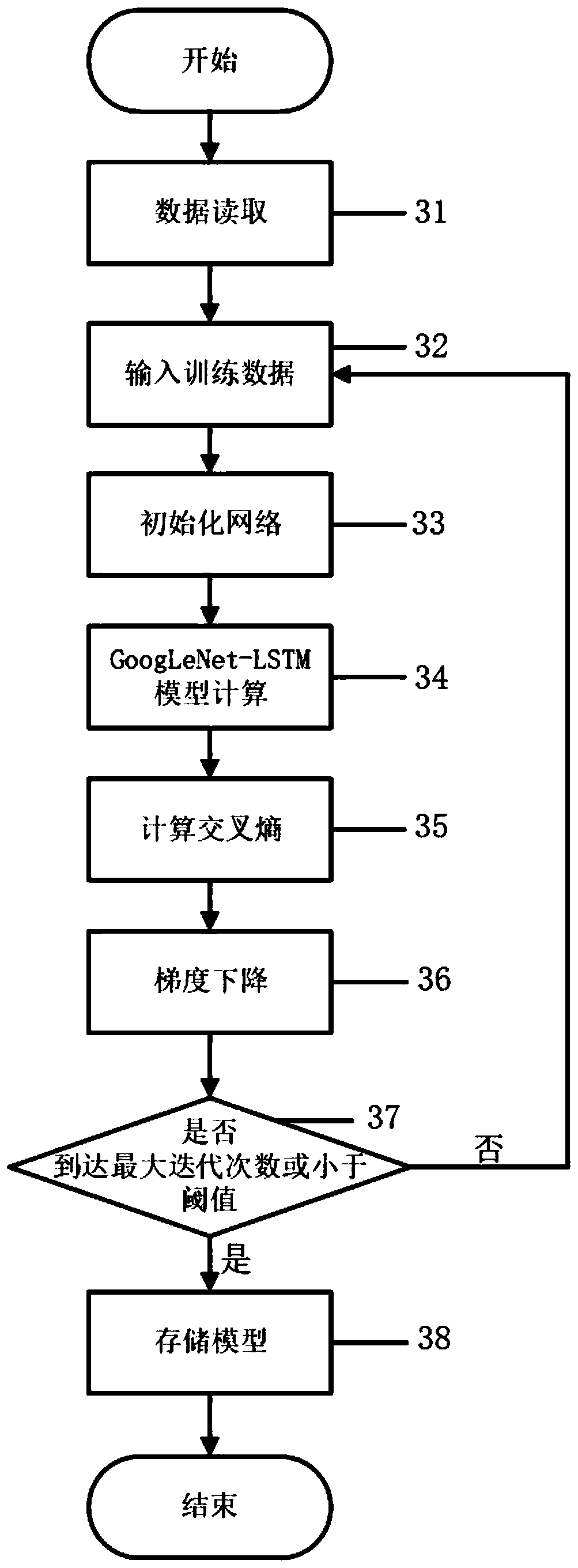
[0027] The network packet classification module judges the category and function of the network packet according to the key field values in the network pack...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com