Image stitching tampering detection method
An image mosaic and detection method technology, which is applied in the field of image analysis, can solve the problems of tampering targets in areas that are easy to be ignored, and the inability to accurately locate tampered areas in stitched images, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
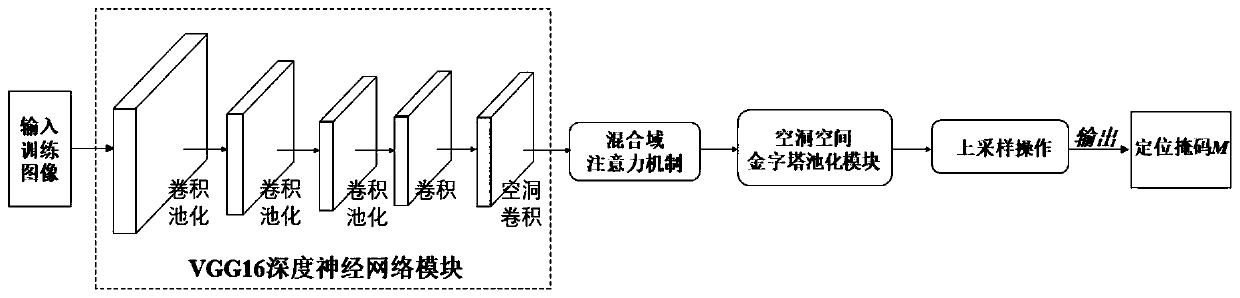
[0095] The specific steps of the detection method for image mosaic tampering based on the hybrid domain attention mechanism and the empty space pyramid pooling module in this embodiment are as follows:
[0096] In the first step, the depth feature map F of the input image is extracted:
[0097] Adjust the size of the input image I to 256×256 pixels, and extract the depth feature map F of the input image through the VGG16 deep neural network module, as shown in the following formula (1),
[0098] F=VGG16(Resize(I)) (1),
[0099] In formula (1), VGG16( ) is the VGG16 deep neural network module, and Resize( ) is a function to adjust the size of the input image;
[0100] The above VGG16 deep neural network module includes convolution, hole convolution, Relu, pooling operations,
[0101] The convolution operation is as follows formula (19),
[0102] F_out=(F_in+2pad-k_size) / stride+1 (19),
[0103] In formula (19), F_out is the result after the convolution layer, F_in is the inp...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com