Safe and credible Ethernet interface system and implementation method
A technology of interface system and implementation method, which is applied in the field of safe and reliable Ethernet interface system, and achieves the effect of good popularization and wide application range
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
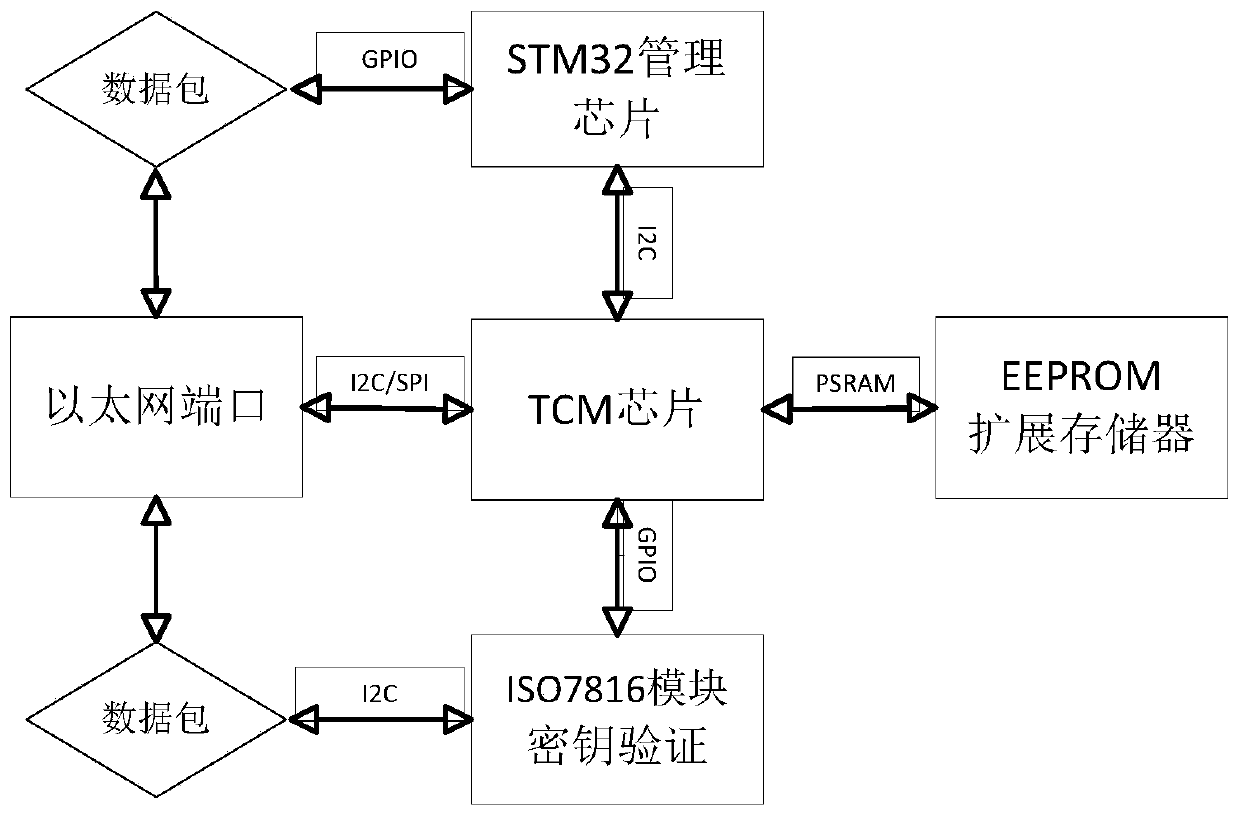
[0034] as attached figure 1 As shown, the safe and trusted Ethernet interface system of the present invention has a structure including a TCM chip, an EEPROM extended memory, a key verification module, an STM32 management chip and an Ethernet port. The TCM chip communicates with the STM32 management chip through the I2C bus, and the STM32 The management chip manages the Ethernet communication data packets through the GPIO bus. The TCM chip is embedded with a key verification module. The key verification module communicates with the Ethernet device through the I2C bus. The TCM chip manages the data communication of the Ethernet port through the I2C / SPI bus. Read and write data through PSRAM data bus and external EEPROM expansion memory. Among them, the key verification module adopts the ISO7816 module.
[0035] The TCM chip is used to read device information and determine whether the device has a security key. The specific process is as follows:
[0036] If the security key i...
Embodiment 2
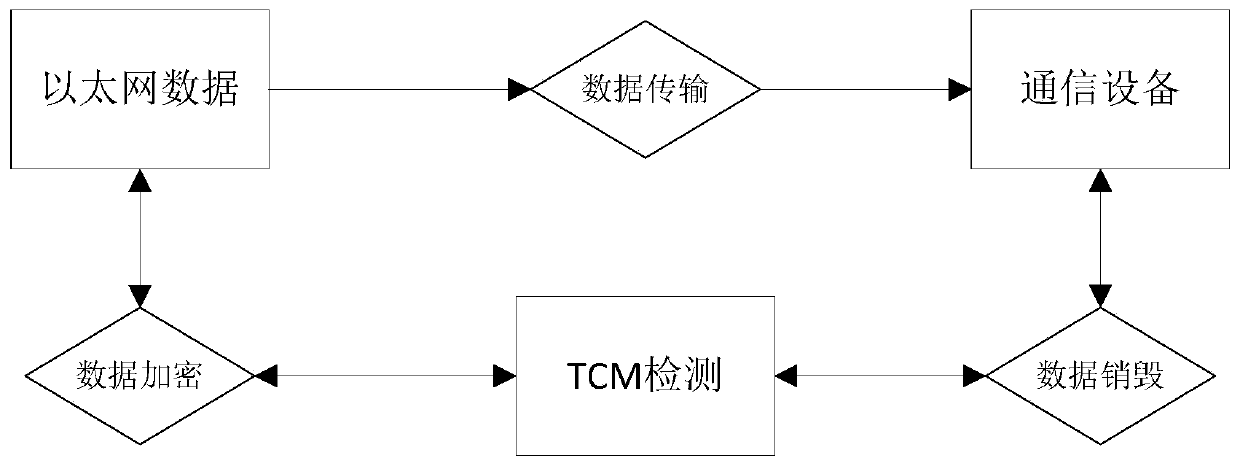
[0040] as attached figure 2 As shown, the implementation method of the safe and trusted Ethernet interface of the present invention, the implementation method is to monitor and protect the communication data of the Ethernet port in real time through the TCM chip, and finally realize the safety and reliability of the data communication; the specific steps are as follows:
[0041] S1. After the TCM chip detects the data communication of the Ethernet port, it reads the internal information of the communication device through the embedded key verification module, judges that the communication device has no security key and verifies:
[0042] ①. If the communication device has a security key and the verification is passed, execute step S2;
[0043] ②. If the communication device does not have a security key or the security key has not been verified, skip to step S3;
[0044] ③. If the TCM chip detects that the computer has repeatedly used a communication device that has not been ...
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap