Big data computer network security protection device and control method thereof
A security protection device and computer network technology, applied in computer security devices, digital data protection, computing, etc., can solve problems such as poor scalability, increased storage and maintenance costs, and low data encryption security, so as to save storage costs and improve Data encryption efficiency and high security performance
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
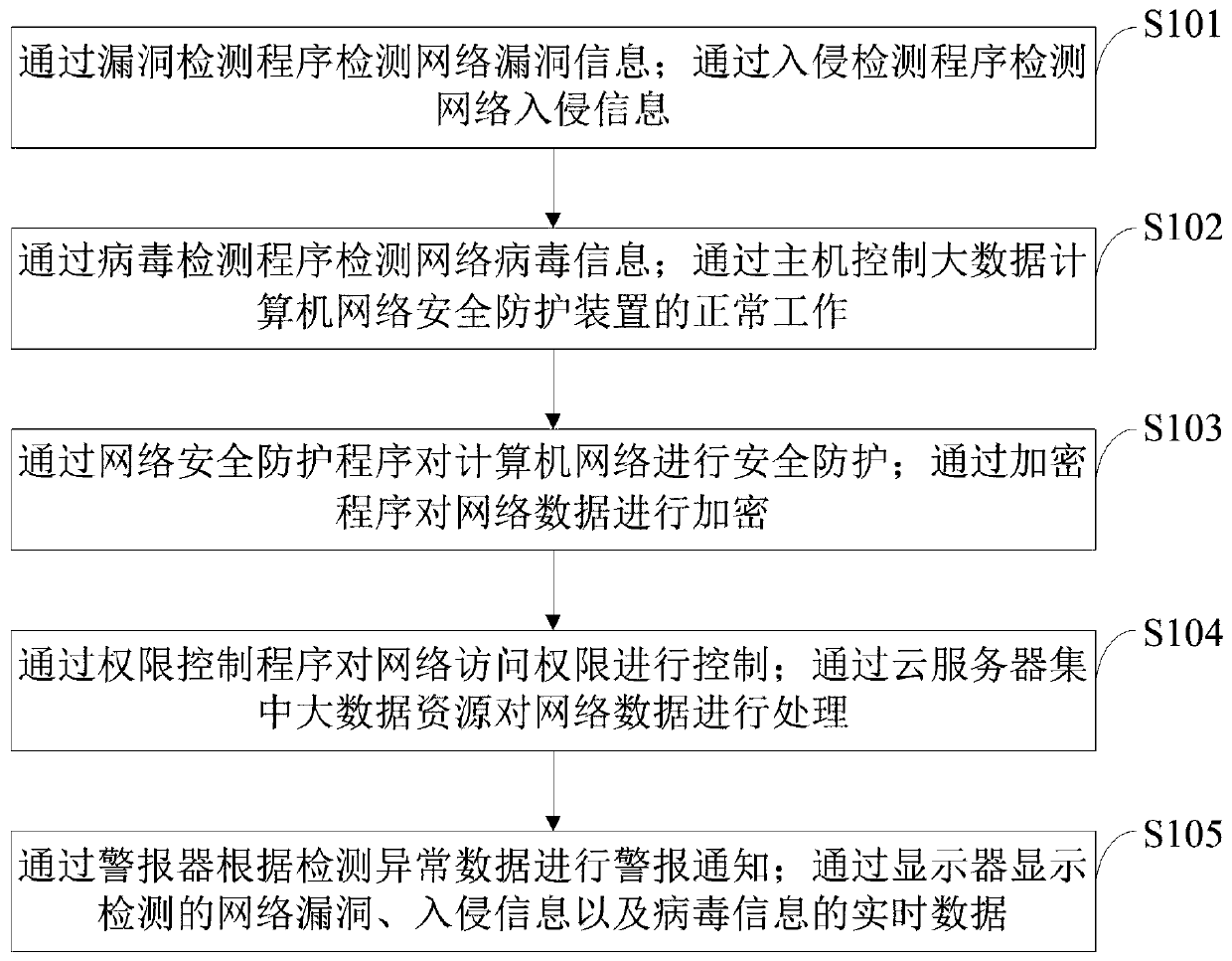
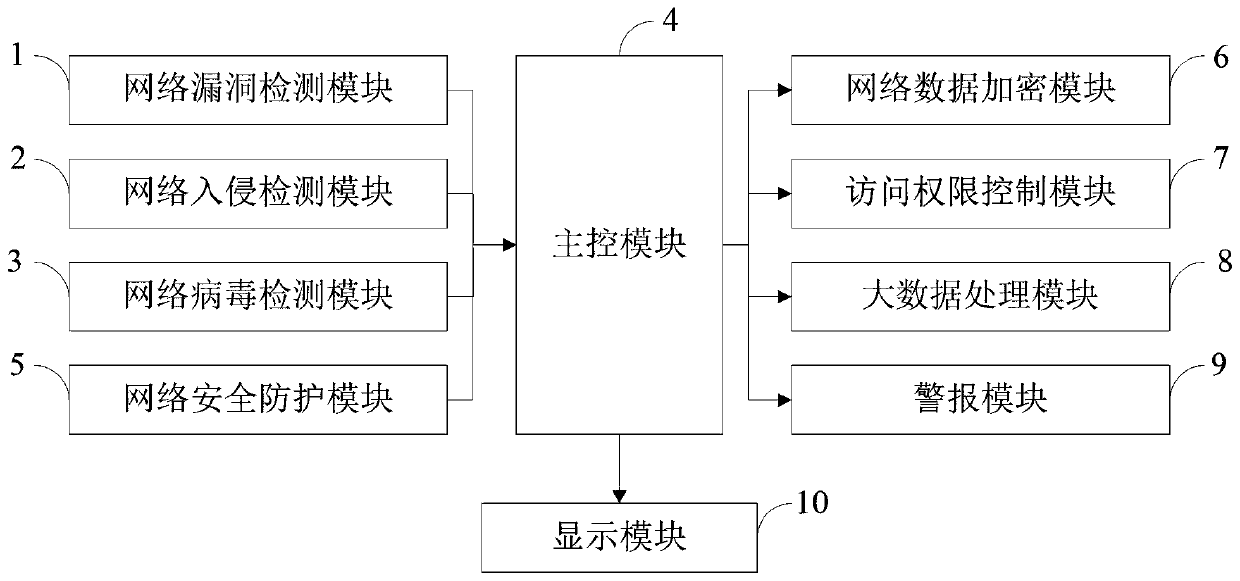
[0077] The control method of the big data computer network security protection device provided by the embodiment of the present invention is as follows figure 1 As shown, as a preferred embodiment, the method for performing security protection on a computer network through a network security protection program provided by the embodiment of the present invention includes:
[0078] (1) Obtain multi-dimensional data; the multi-dimensional data includes network vulnerability information, intrusion information, and virus information.
[0079] (2) Preprocessing the acquired multi-dimensional data to generate data to be analyzed.
[0080] (3) Analyze the data to be analyzed and generate an early warning report, which is used to forecast threats.
[0081] (4) Analyzing the data to be analyzed and generating an early warning report includes at least situational awareness, real-time analysis and early warning, or network intrusion attack path and threat source analysis.
[0082] (5) The situation...
Embodiment 2
[0086] The control method of the big data computer network security protection device provided by the embodiment of the present invention is as follows figure 1 As shown, as a preferred embodiment, the method for encrypting network data through an encryption program provided by the embodiment of the present invention includes:
[0087] (I) Configure the data collector parameters, collect the network information data through the data collector and save it in the local storage, and perform feature extraction on the collected network information data.
[0088] (II) The background terminal sends a key acquisition request to the front-end database server, where the key acquisition request includes the characteristic data to be encrypted.
[0089] (III) The background terminal generates key data according to the feature data to be encrypted, and stores the key data in the data monitoring and early warning system.
[0090] The method for storing data in the local storage in step (I) provided ...
Embodiment 3
[0096] The control method of the big data computer network security protection device provided by the embodiment of the present invention is as follows figure 1 As shown, as a preferred embodiment, the method for controlling network access authority through an authority control program provided by the embodiment of the present invention includes:
[0097] 1) The user access address of the target resource is generated in advance through an authorization control program, the user access address is used for public release; the user access address carries at least the original address information and access authority information of the target resource.
[0098] 2) Receive an access request to the target resource, the access request includes the user access address of the target resource.
[0099] 3) Parse out the original address information and access authority information of the target resource from the user access address.
[0100] 4) Obtain the user ID of the current visitor, and deter...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com