Defect detection method and device based on configuration analysis engine, and computer readable storage medium
A technology of analysis engine and defect detection, applied in computer-readable storage medium, in the field of defect detection based on configuration analysis engine, which can solve problems such as security vulnerabilities
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
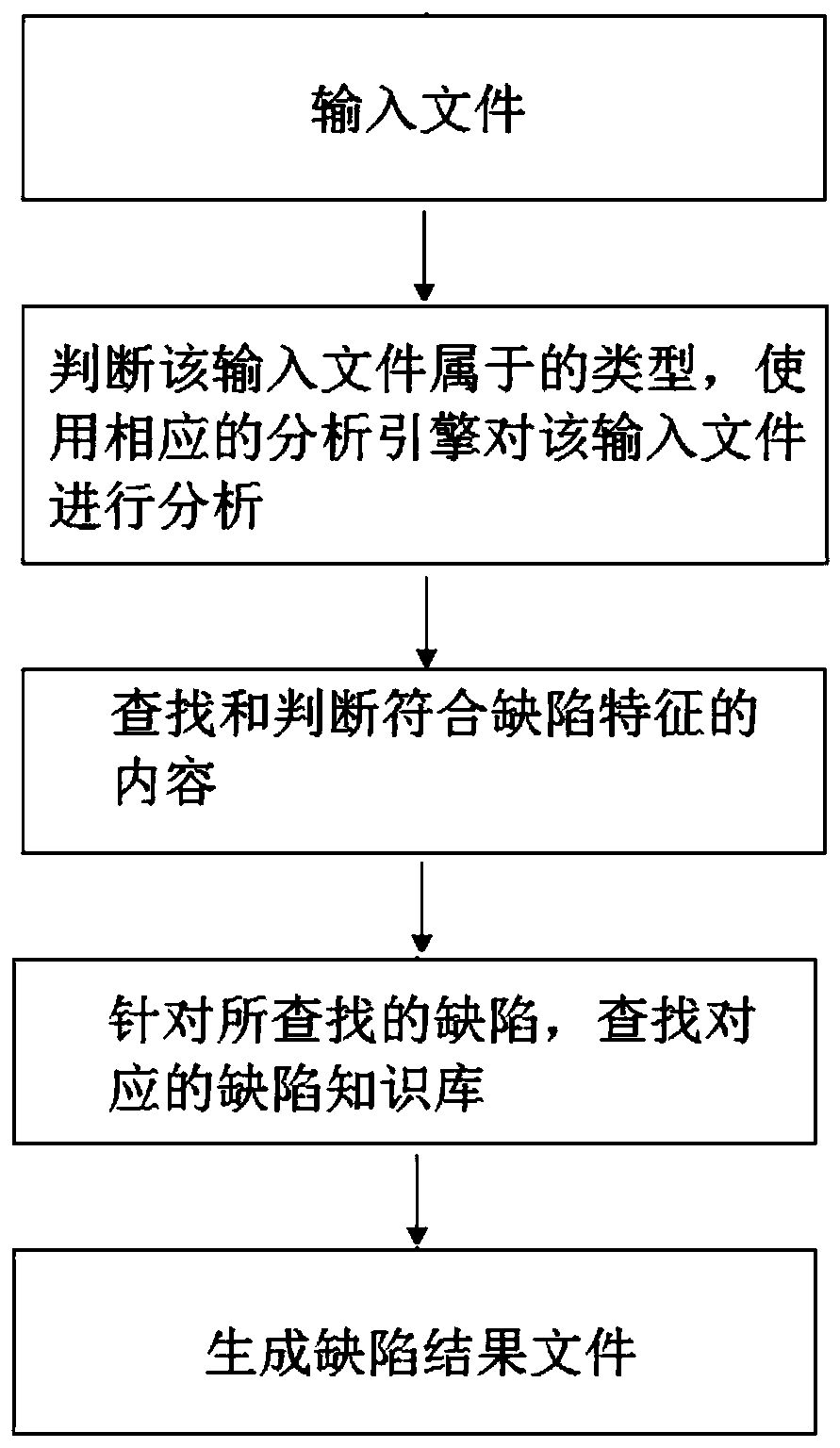
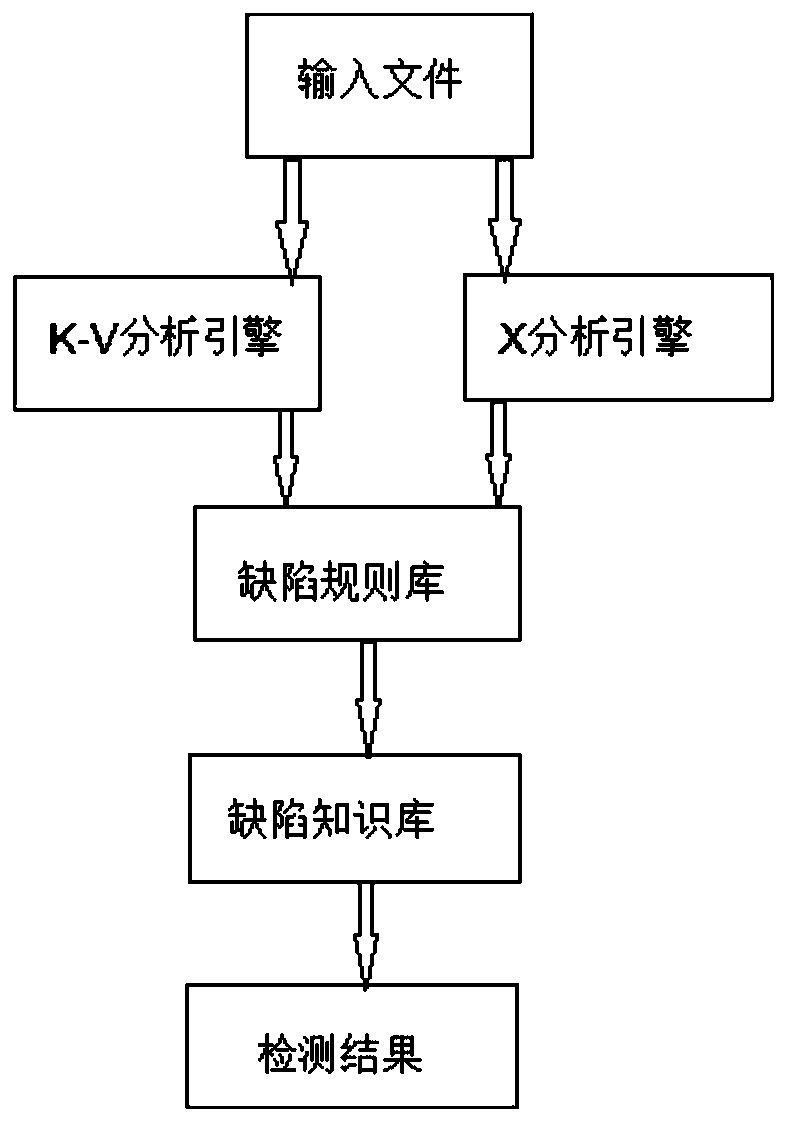
[0037] figure 1 A flowchart showing a defect detection method based on a configuration analysis engine provided by an embodiment of the present invention. An embodiment of the present invention provides a defect detection method based on a configuration analysis engine, the method comprising: Step 1: input a file; Step 2: determine the type of the input file, and use a corresponding analysis engine to analyze the input file; Step 3: Find and judge the content that meets the defect characteristics; Step 4: Find the corresponding defect knowledge base for the found defect; Step 5: Generate a defect result file. Optionally, in step 2, if the input file is a property file, the K-V analysis engine utilizes the java.util.Properties class to parse the input file, and then obtains all Key-Values of the input file after parsing right value. Optionally, in step 3, use the K-V analysis engine to load the K-V rule to analyze whether the value of each Key-Value pair in the value of ...
Embodiment 2
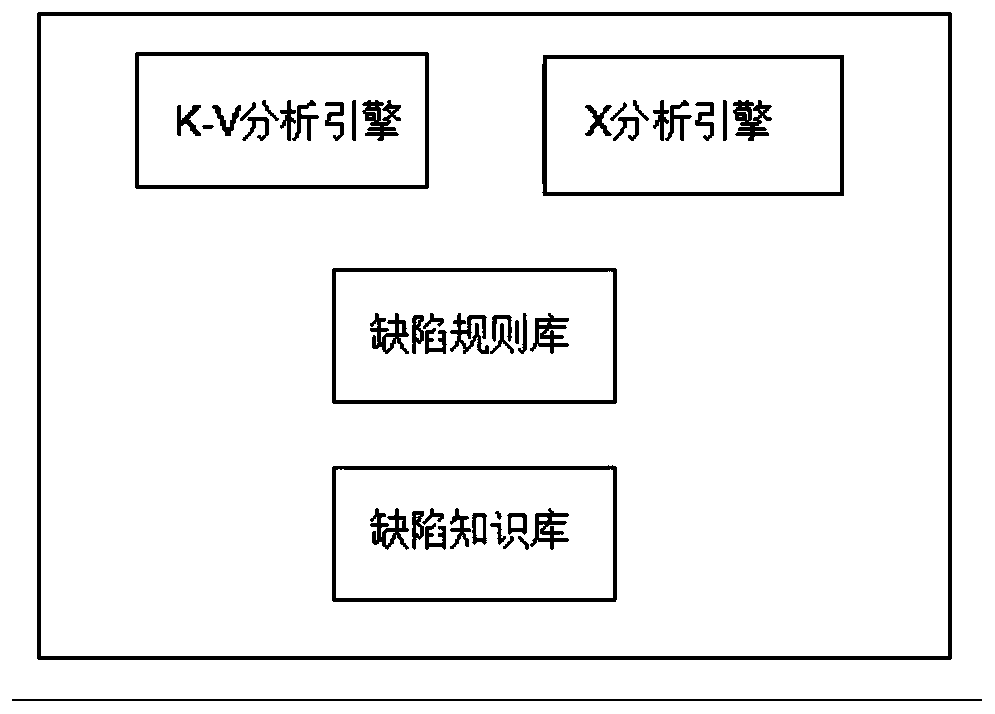
[0052] According to an embodiment of the present invention, the present invention provides a defect detection device based on a configuration analysis engine, such as Figure 4 As shown, it includes: a memory 10, a processor 12, and a computer program stored on the memory 10 and operable on the processor 12. When the computer program is executed by the processor 12, the above embodiment 1 is realized. The steps of the configuration analysis engine based defect detection method described in .
Embodiment 3
[0054] According to an embodiment of the present invention, the present invention provides a computer-readable storage medium, and the computer-readable storage medium stores a program for implementing information transmission, and when the program is executed by a processor, the above-mentioned embodiment 1 is implemented. The steps of the defect detection method based on configuration analysis engine.
[0055] The technical scheme of the present invention uses data nodes to record data information, which is simple, easy to expand, and easy to use. The data in the data information table is sorted by name, which can realize quick search and is more convenient to use. All node information is stored in the data information table, and all subsequent data operations can directly look up the table instead of looking up the syntax tree, which greatly improves the efficiency of use. Data crossing nodes are recorded separately as multiple data links, which is not easy to cause co...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com