Implementation method of post-quantum key exchange protocol and application thereof
A technology of quantum key and implementation method, applied in key distribution, can solve problems such as slow exchange speed, and achieve the effect of reducing transmission bandwidth, computing time, and simplifying complexity
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
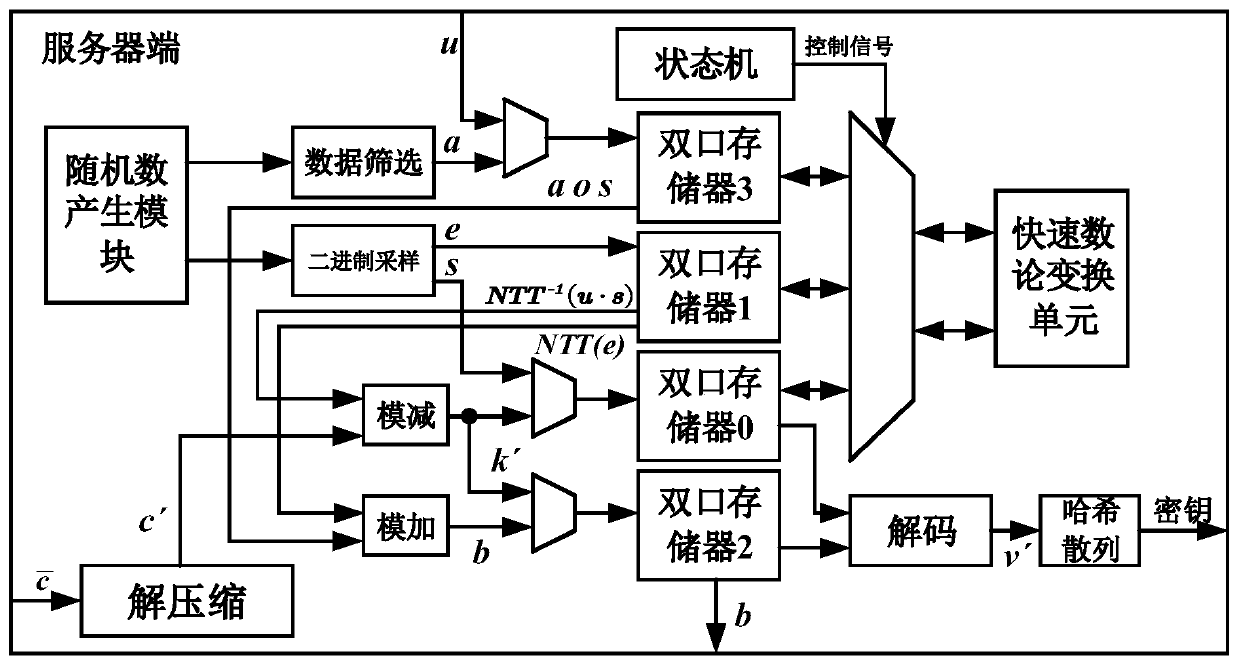
[0039] An implementation method 100 of a post-quantum key exchange protocol, such as figure 1 shown, including:
[0040] Step 110, the client generates a public polynomial based on its Trivium module and based on generator polynomial Then send a data request signal to the server to receive the polynomial sent by the server And receive the data request signal sent by the server to send sent to the server for calculation public polynomial of Generated by the random number generated by the server using its Trivium module, where
[0041] Step 120, the client generates the key μ and the polynomial based on its Trivium module And based on another data request signal received from the server, the Sent to the server, for the server based on Generate the key μ and adjust its Trivium module state to synchronize with the current client Trivium module.
[0042] When executing this method for the first time, it is necessary to initialize the Trivium modules on the cli...
Embodiment 2
[0057] A client, including a processor for implementing the post-quantum key exchange protocol, configured to execute the method for implementing the post-quantum key exchange protocol as described in Embodiment 1 above. The relevant technical solutions are the same as those in Embodiment 1, and will not be repeated here.
Embodiment 3
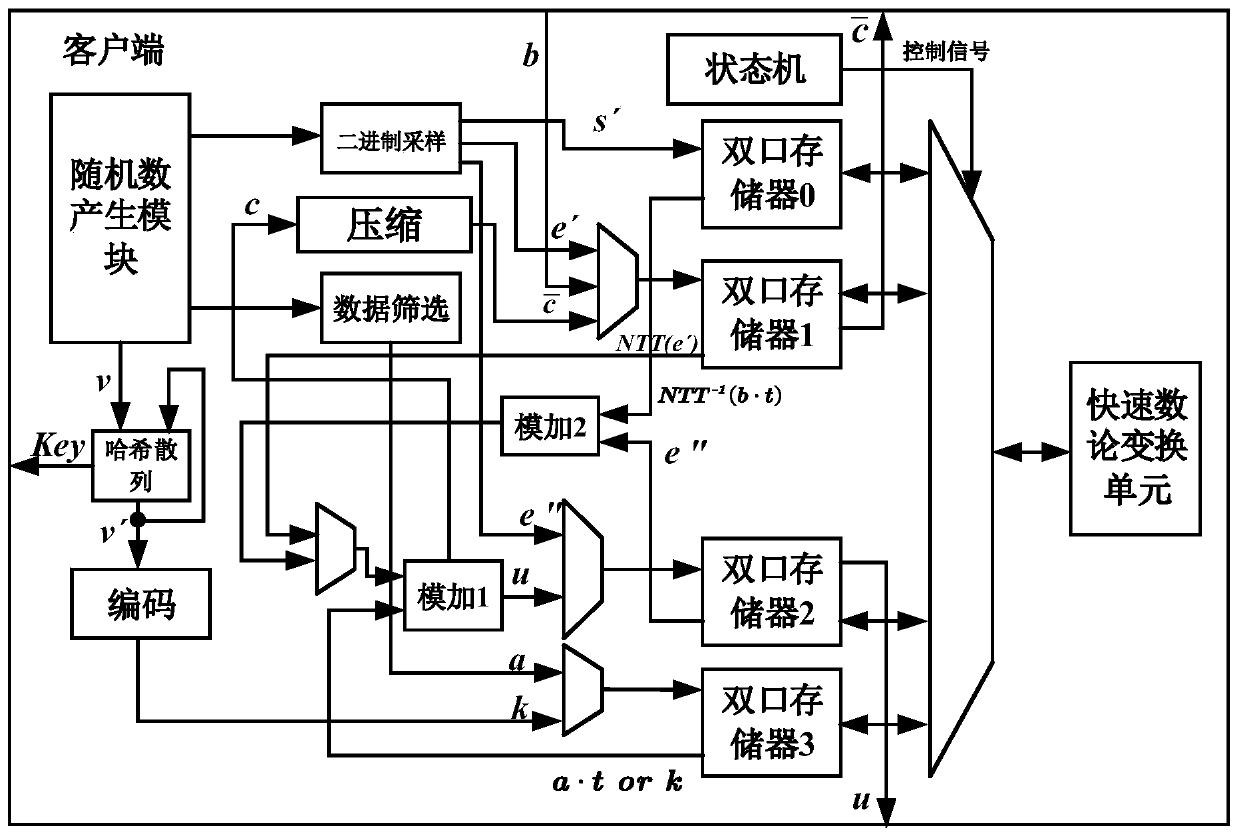
[0059] A method for implementing a post-quantum key exchange protocol, comprising:
[0060] The server side generates a public polynomial based on its Trivium module and based on generator polynomial Then receive the data request signal sent by the client to send to the client And send a data request signal to the client to receive the client sent for calculation of Generated by the random number generated by the client using its Trivium module, where
[0061] The server side is based on Generate a polynomial m, and send another data request signal to the client to receive the polynomial corresponding to the key μ sent by the client Based on m and polynomial generate key μ;
[0062] The server side controls its Trivium module to continue working for a certain period of time, so that the state of its Trivium module is the same as that of the client.
[0063] When executing this method for the first time, it is necessary to initialize the Trivium modules on...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com