Universal security cooperation system
A collaborative system and security technology, applied in the parts of the TV system, image communication, TV, etc., can solve the problem of not being able to make full use of the work efficiency of remote collaborative applications, and achieve the effect of eliminating network attacks
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
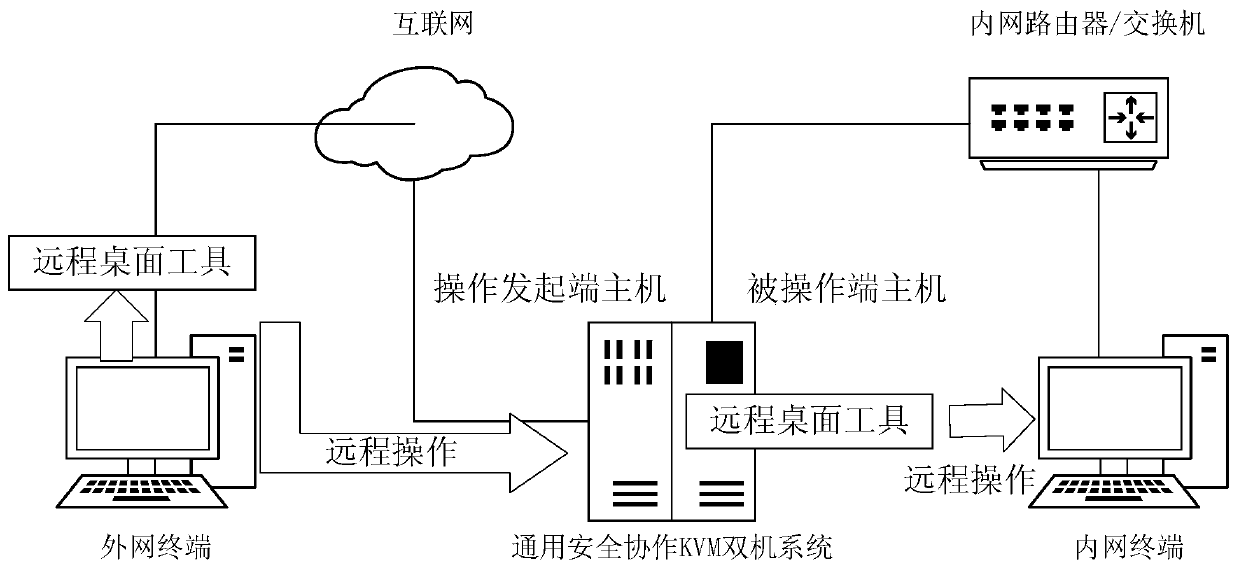
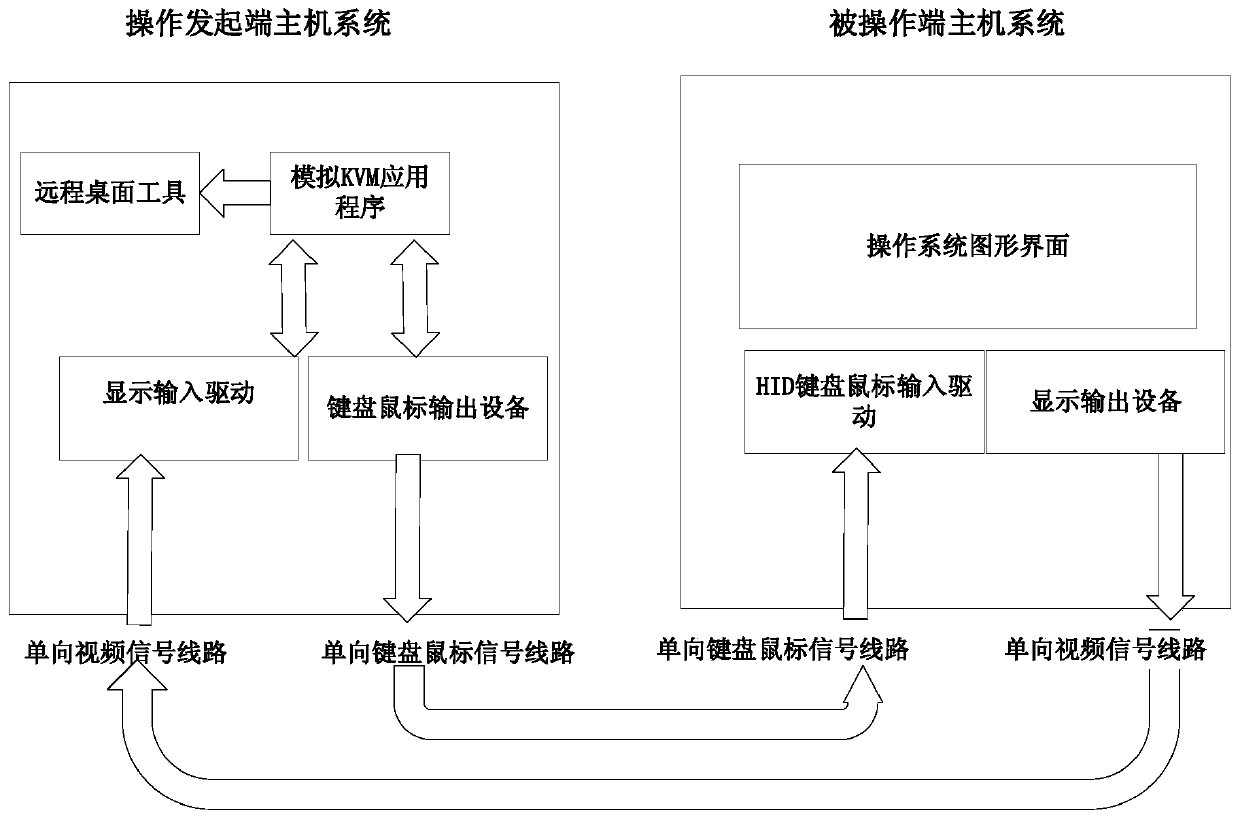
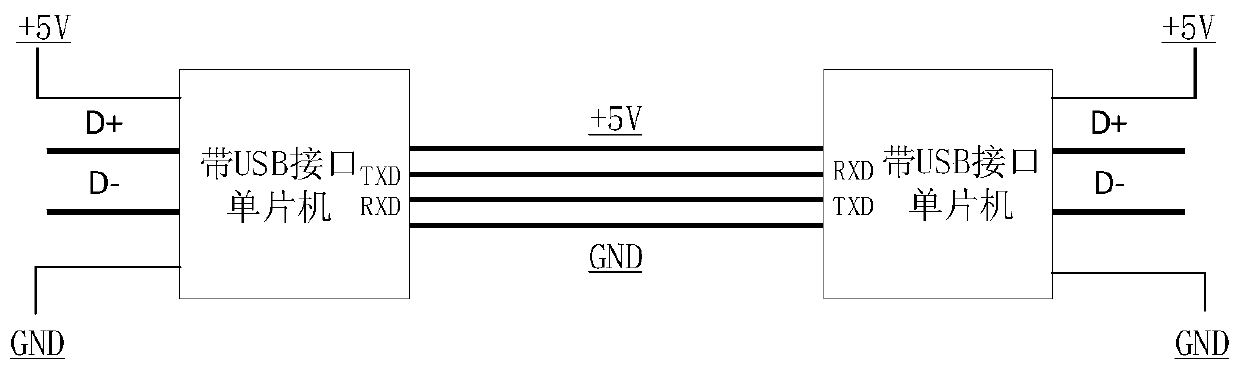
[0023] The present invention proposes a computer system that can not only satisfy remote collaborative maintenance, but also ensure that it will not bring the three most threatening network security risks of information leakage, network attack or virus infection, which can be called a universal security collaborative KVM system. The present invention includes an operation initiator host and an operated host, runs a KVM application program on the operation initiator host, simulates a KVM system, displays screen images transmitted from the operated host through a one-way video line, and intercepts application graphics Mouse and keyboard operation on the interface, write the mouse and keyboard operation code into the one-way mouse and keyboard communication line. Install a HID device driver program on the host computer at the operated end, implement a keyboard and mouse device on the hardware layer, and convert the mouse and keyboard operations from the operation initiator forward...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com