Working method of permission authentication system based on CAS
A working method and authority authentication technology, applied in the field of CAS-based authority authentication system, which can solve the problem that CAS service does not perform user authority authentication.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
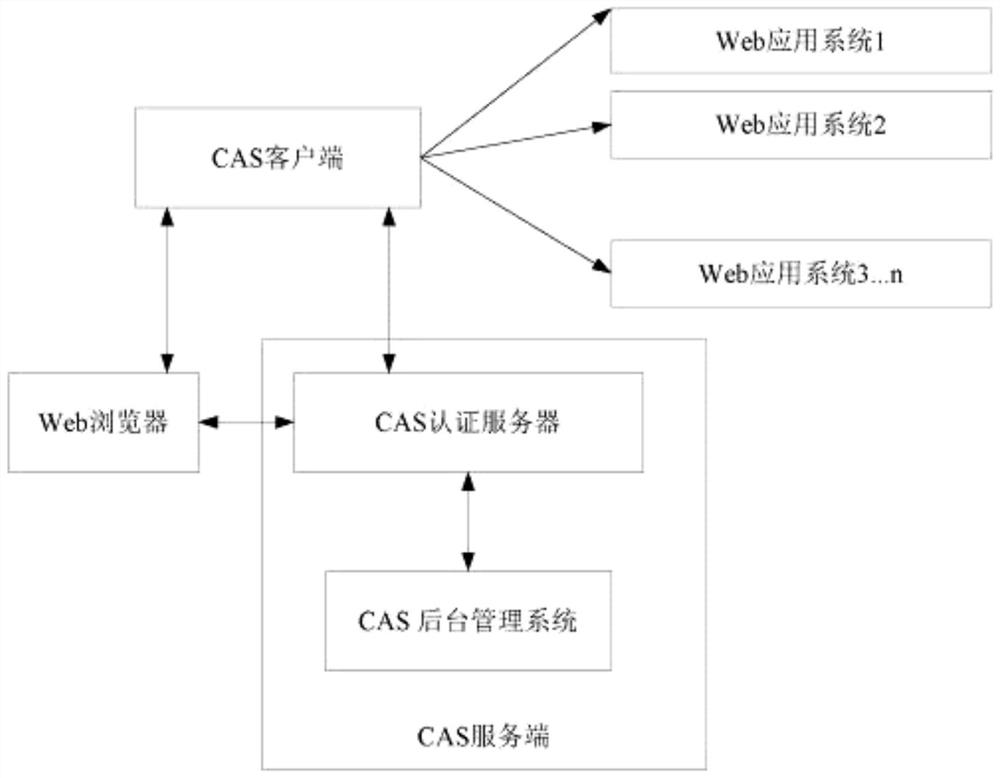
[0057] image 3 A schematic diagram of the authority authentication system architecture provided by Embodiment 1 of the present invention; image 3 Shown:
[0058] The CAS client is deployed together with multiple web application systems, and the protected resources of multiple web application systems are protected in the form of Filter. The user can access the corresponding web application system through the web browser of the CAS client. When the user logs in for the first time, the CAS server generates a credential ticket, which is stored in the server session and the client cookie respectively. , the client will automatically bring the ticket data to the server for verification, and if the verification is successful, it will log in automatically. As for whether the ticket will be forged and cause security problems, the CAS framework has already dealt with it, because the docking system needs to use the https security protocol for access, so there is no need to worry abou...
Embodiment 2
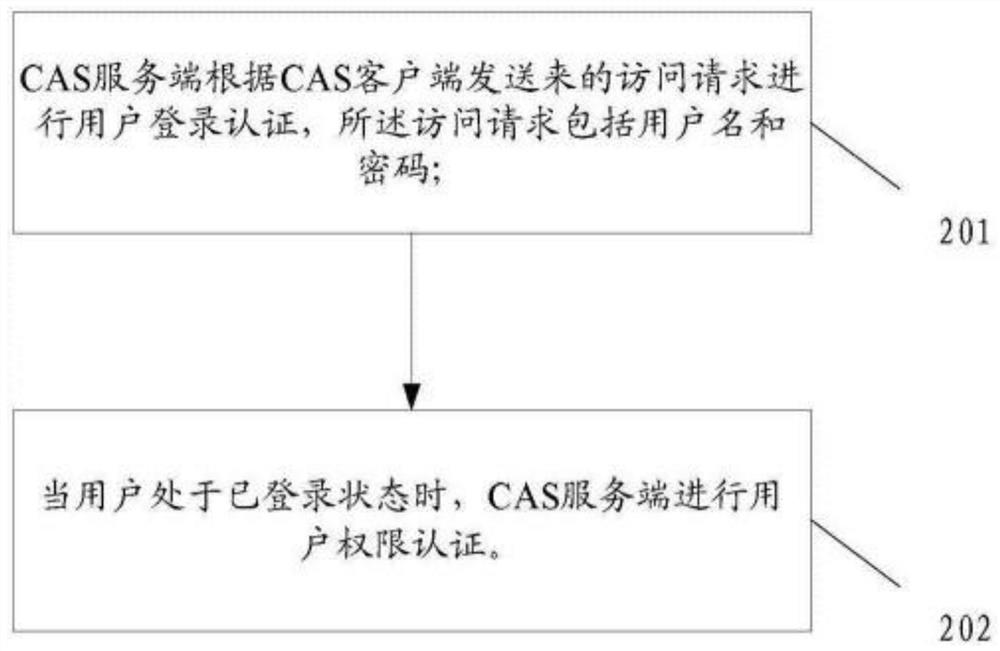
[0063] Such as Figure 4 As shown, an authority authentication method provided by an embodiment of the present invention includes:
[0064] Step 401, the CAS client receives the access request sent by the user through the web browser;
[0065] The access request may be a request to access a certain web application system, such as directly inputting a certain web application system address in the address of the web browser, or it may be a request to access the application system corresponding to the CAS client.
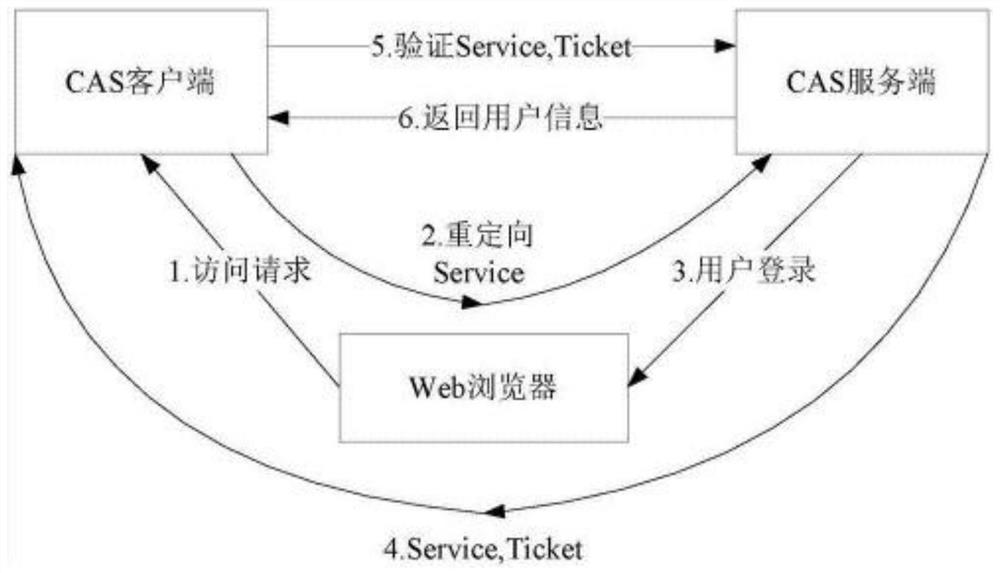
[0066] Step 402, the CAS client directly goes to the CAS server to perform user login authentication, and the CAS server judges whether the user has logged in; if the user is logging in for the first time, then execute as follows figure 1 Steps 1-5 in the single sign-on process shown in the prior art are then executed in step 403, and if the user is already logged in, step 403 is directly executed;
[0067] Step 403, when the user is in the logged-in state, the CAS s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com