Face recognition anti-spoofing method, system and terminal based on infrared rays
A face recognition and anti-spoofing technology, applied in the field of face recognition, can solve the problems of unknown feasibility, inconvenient, complicated use, etc.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
[0101] Aiming at the problems existing in the prior art, the present invention provides an infrared-based face recognition anti-spoofing method.
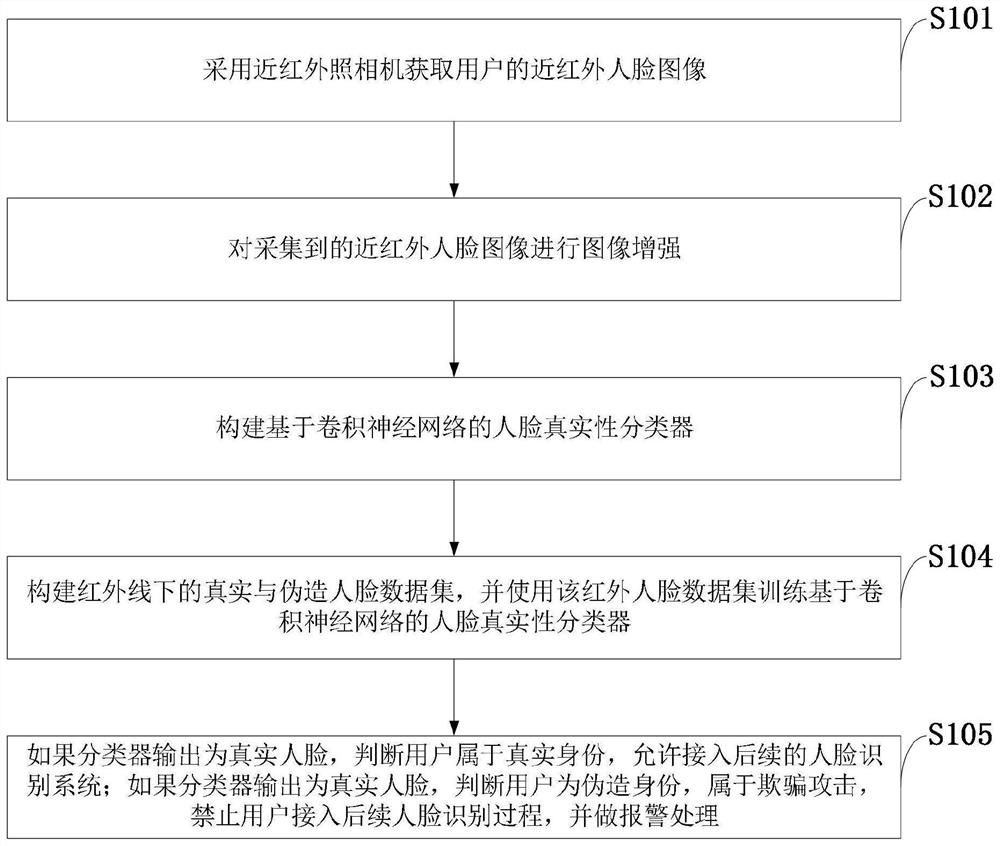
[0102] Such as figure 1 As shown, the infrared-based face recognition anti-spoofing method provided by the present invention comprises the following steps:
[0103] S101: Obtain a near-infrared face image of the user by using a near-infrared camera;
[0104] S102: Perform image enhancement on the collected near-infrared face image;
[0105] S103: constructing a face authenticity classifier based on a convolutional neural network;
[0106] S104: Construct a dataset of real and fake faces under near-infrared rays, and use the dataset of near-infrared rays of faces to train a face authenticity classifier based on a convolutional neural network;
[0107] S105: User anti-spoofing test, if the output of the classifier is a real face, it is judged that the user belongs to the real identity, allowing access to the subsequent face recogni...
Embodiment 2
[0153] On the basis of the above-mentioned embodiment 1, the embodiment of the present invention provides a face recognition anti-spoofing system based on near-infrared face anti-spoofing, such as Figure 8 Shown is a schematic structural diagram of this embodiment.
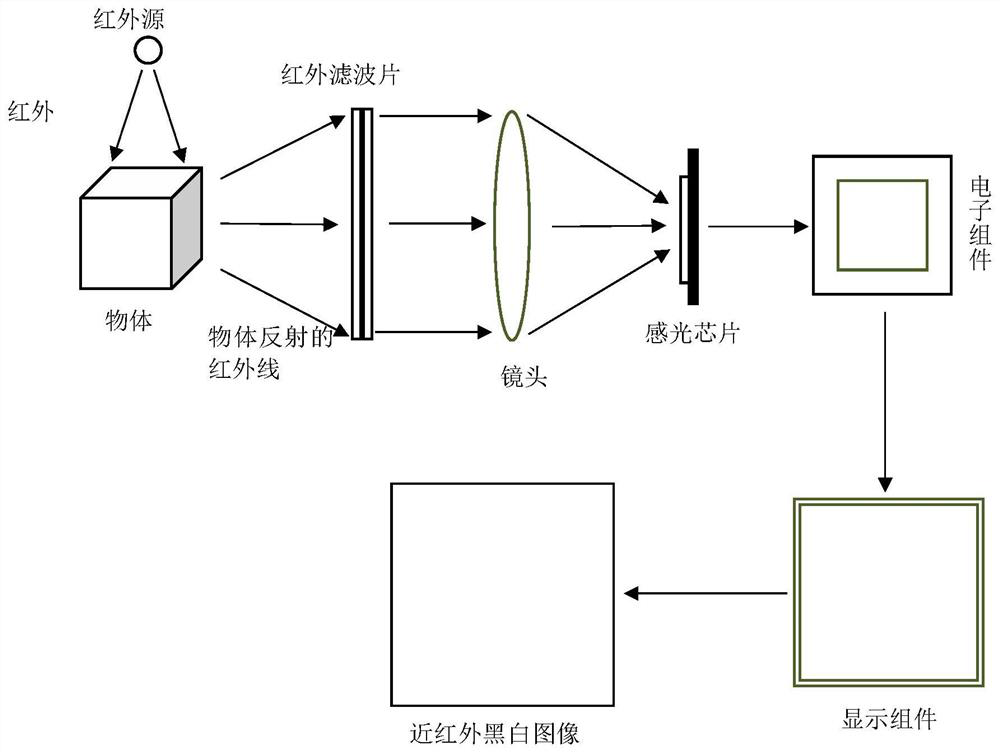
[0154] The system provided by the embodiment of the present invention includes hardware (hardware structure such as Figure 8 (a) shown) and software (software structure such as Figure 8 (b) shows) two parts. Wherein the hardware structure includes an infrared image collector, a display, a processor, a memory, an alarm, a communication interface and a communication bus (such as Figure 8 (a) shown). The near-infrared image collector, display, processor, memory, alarm and communication interface are connected through a communication bus to complete mutual data transmission.
[0155] Infrared image collector: used for user's near-infrared face image acquisition;
[0156] Display: display the user data collect...
Embodiment 3
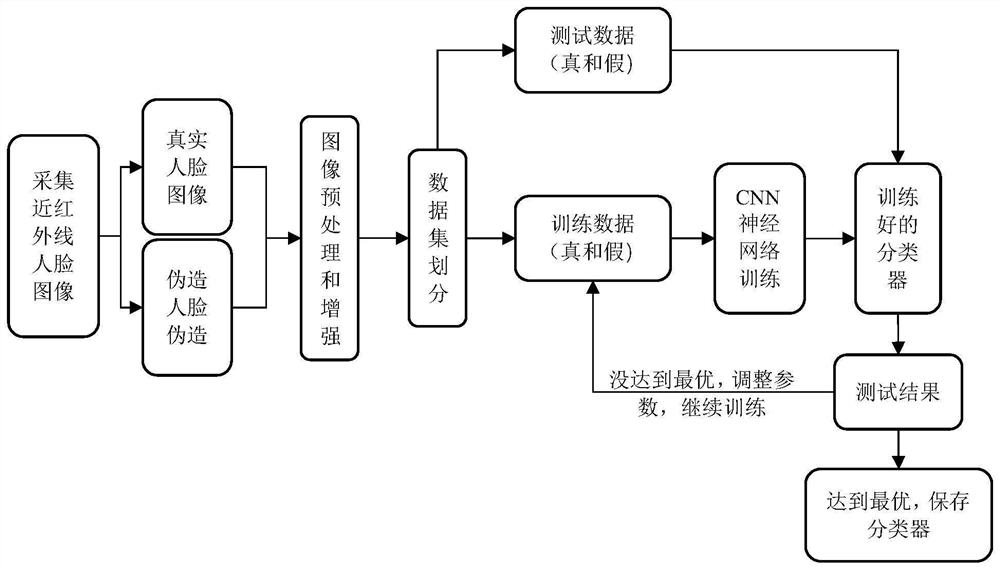
[0167] On the basis of the above-mentioned embodiment 2, the embodiment of the present invention provides a computer program for face recognition anti-spoofing based on infrared rays, such as Figure 9 Shown is a schematic flow chart of this embodiment.
[0168] A computer program based on infrared face recognition and anti-spoofing provided by this embodiment implements the following steps when executed by a processor:
[0169] Step 1. Activate the program and perform necessary initialization.
[0170] Step 2, call the near-infrared image collector to collect the face image, and output the image to the monitor of the computer.
[0171] Step 3. Preprocessing and enhancing the collected face images.
[0172] Specifically, the preprocessing of the image in Step 3 of this embodiment includes: cropping and scaling the near-infrared face image to the resolution required by the program and image grayscale processing. Image enhancement is the cascaded image enhancement method used...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com