Method and system for improving software compatibility for linux system
A compatibility and software technology, applied in software indicators, software engineering design, software maintenance/management, etc., can solve the problems of complex management, incompatibility, huge workload, etc., achieve short time consumption, improve compatibility, improve The effect of safety features
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
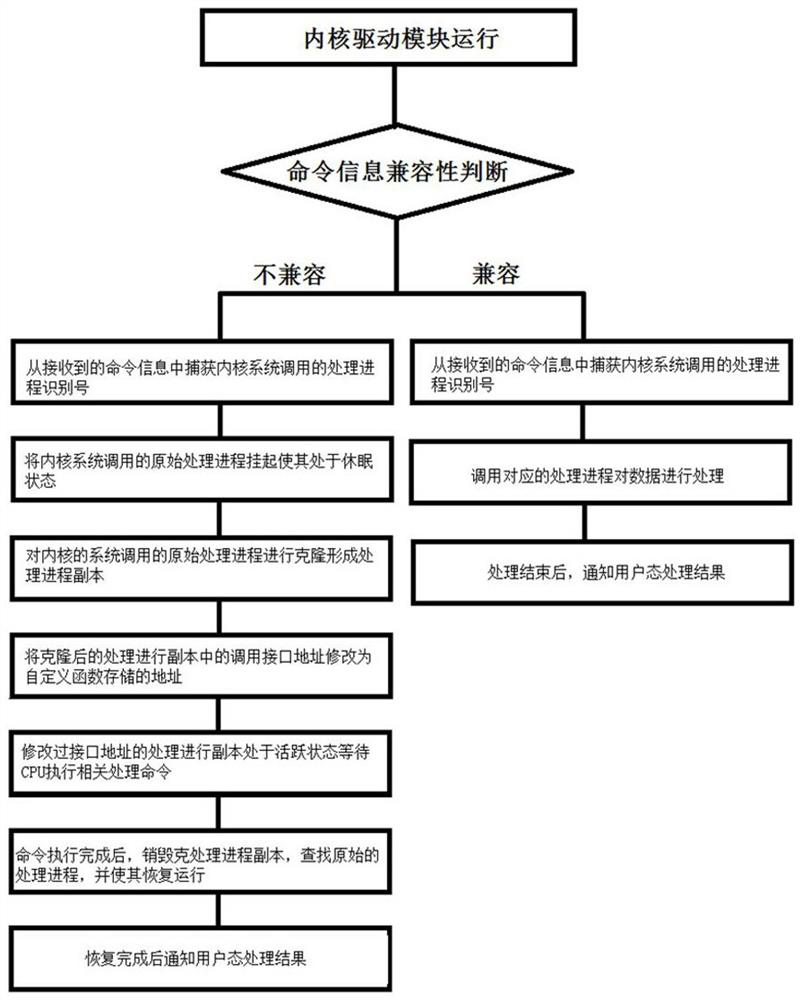
[0025] Such as figure 1 As shown, this embodiment discloses a method for improving software compatibility for a linux system, which mainly includes the following steps:
[0026] Step 1: The kernel driver module runs in the kernel, and judges the compatibility of the received command information sent by the user mode. If you need to call a custom kernel function, perform steps 2 to 4; otherwise, perform step 5; Among them, the method to judge the compatibility of the received command is: multiply and hash the original call interface address of the received command to obtain the corresponding first key 1 Value, according to the first key 1 The value is queried in the preset mapping table. If the received command is in the preset mapping table, it is a command that needs to call a custom kernel function; otherwise, the kernel system call is captured according to the received command Process process identification number, call the corresponding process process to process the data; amo...
Embodiment 2
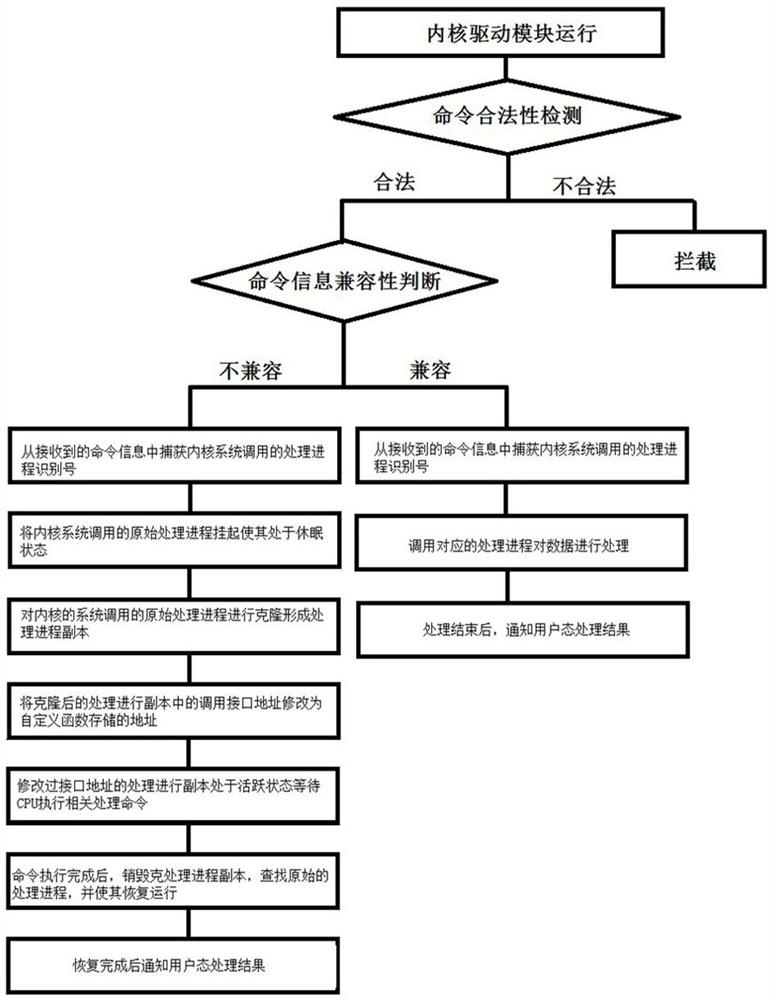
[0032] Such as figure 2 As shown, this embodiment discloses a method for improving the compatibility of software used in a linux system, which mainly includes the following steps:
[0033] Step 1: The kernel driver module runs in the kernel and checks the legality of the received command information sent by the user mode. If it passes the legality test, proceed to step 2; if it fails the legality test, the command information is directly intercepted ;
[0034] Among them, the method of legality detection is:
[0035] Step 101: Pre-set the format of the legal command during initialization, which is mainly the string key generated by the multiplication hash algorithm through the command name and the length of the command parameter in the legal command 2 , Extract string key 2 The odd bits of the form a substring, and the substring and the command name and the length of the command parameter are arranged in order to form a string by two characters (&&) to form a string key 3 , The stri...
Embodiment 3
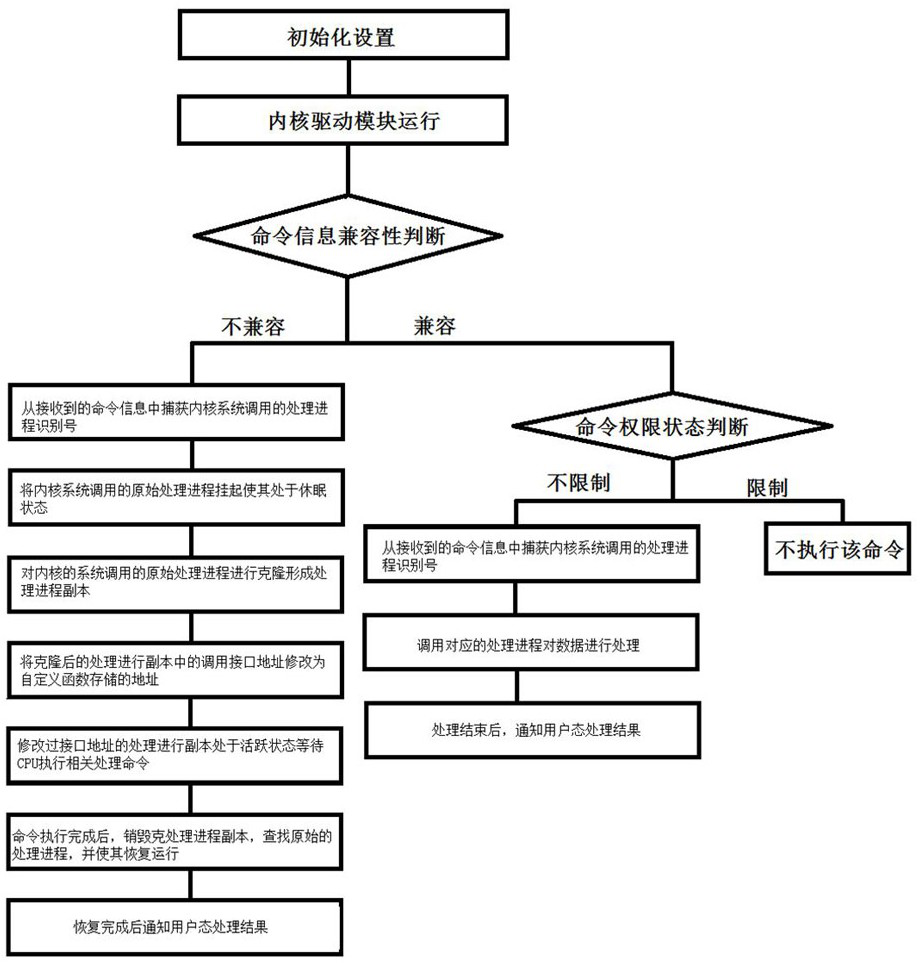
[0045] Such as image 3 As shown, this embodiment discloses a method for improving the compatibility of software used in a linux system, which mainly includes the following steps:
[0046] Step 1: Initialize the command permission control table preset in the kernel driver module, where the command permission control table is an array. According to the original call interface address of each command, do multiplication and Hash operation to get the position of the corresponding command in the array. , And then this location stores the data corresponding to the command authority status, that is, the data of the command authority status is 1, which means that restriction processing is required, that is, the command will not be executed; the data of the command authority status is 0, which means that the original call interface can be submitted to the command Carry out execution. The command authority control table can be dynamically adjusted.
[0047] Step 2: The kernel driver module...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com