DDoS attack detection method combining SVM and optimized LSTM model under SDN network architecture
A technology for network architecture and attack detection, applied in the field of information and communication, can solve problems such as loss of relevant information, no time sequence processing, and inability to forward data packets
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
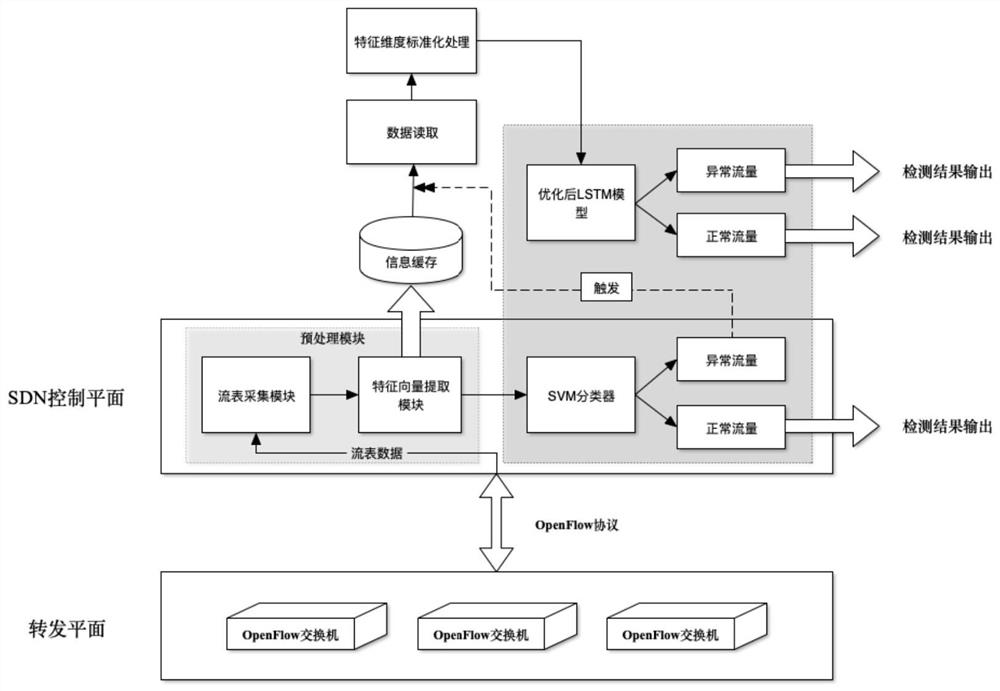
[0022] Step 1: According to the existing LSTM model, use an improved genetic algorithm to optimize the LSTM model to obtain an optimized LSTM model;
[0023] Step 2: Build a virtual SDN network topology structure;
[0024] Step 3: Perform data collection on the virtual SDN network topology structure built in Step 2, to obtain an SDN network data set;
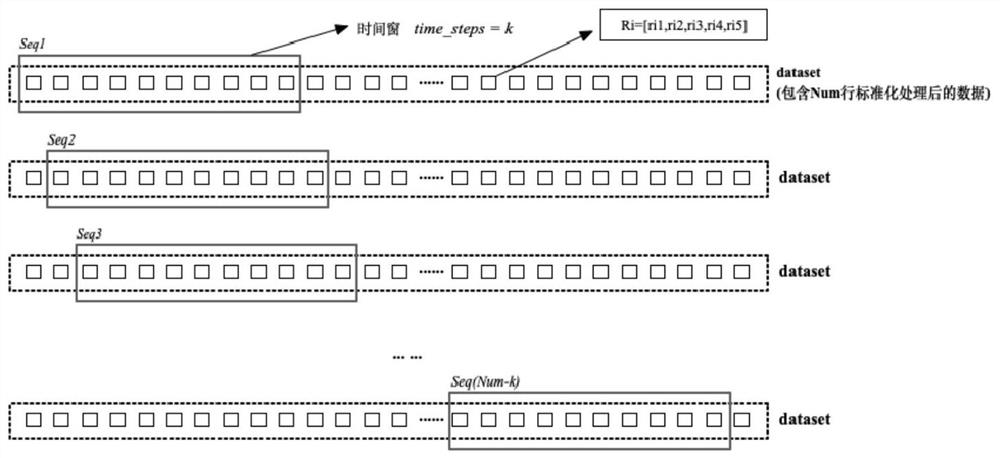
[0025] Step 4: Use step 3 to obtain the SDN network data set, and after standard deviation normalization and time series processing, train the optimized LSTM model obtained in step 1;
[0026] Step 5. Use the SDN network data set obtained in step 3 to train the support vector machine SVM;
[0027] Step 6. After using the SDN controller to collect the flow table information in the virtual SDN network, extract the feature vector according to the feature extraction method, and cache the real-time extracted data into a file for storage;
[0028] Step 7. The flow table feature vector extracted in step 6 is sent to the SVM model for detection. T...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com