A secure transmission method against active eavesdropping in 5G system
A secure transmission and active technology, applied in security devices, electrical components, wireless communications, etc., can solve the problems of high precision, poor performance, and susceptibility to frequency deviation of channel state information CSI, and achieve the goal of resisting active spoofing attacks Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0042] Hereinafter, specific embodiments of the present application will be described in detail with reference to the accompanying drawings. According to these detailed descriptions, those skilled in the art can clearly understand the present application and can implement the present application. Without departing from the principle of the present application, the features in different embodiments can be combined to obtain new implementations, or some features in certain embodiments can be replaced to obtain other preferred implementations.
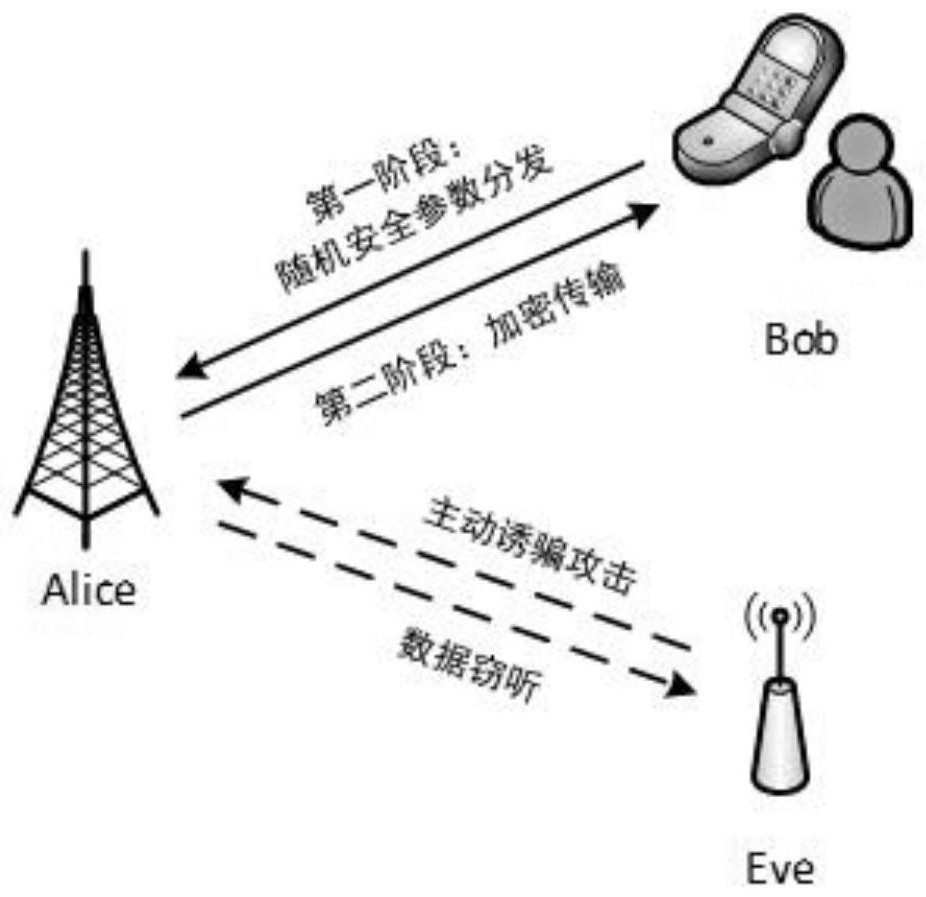
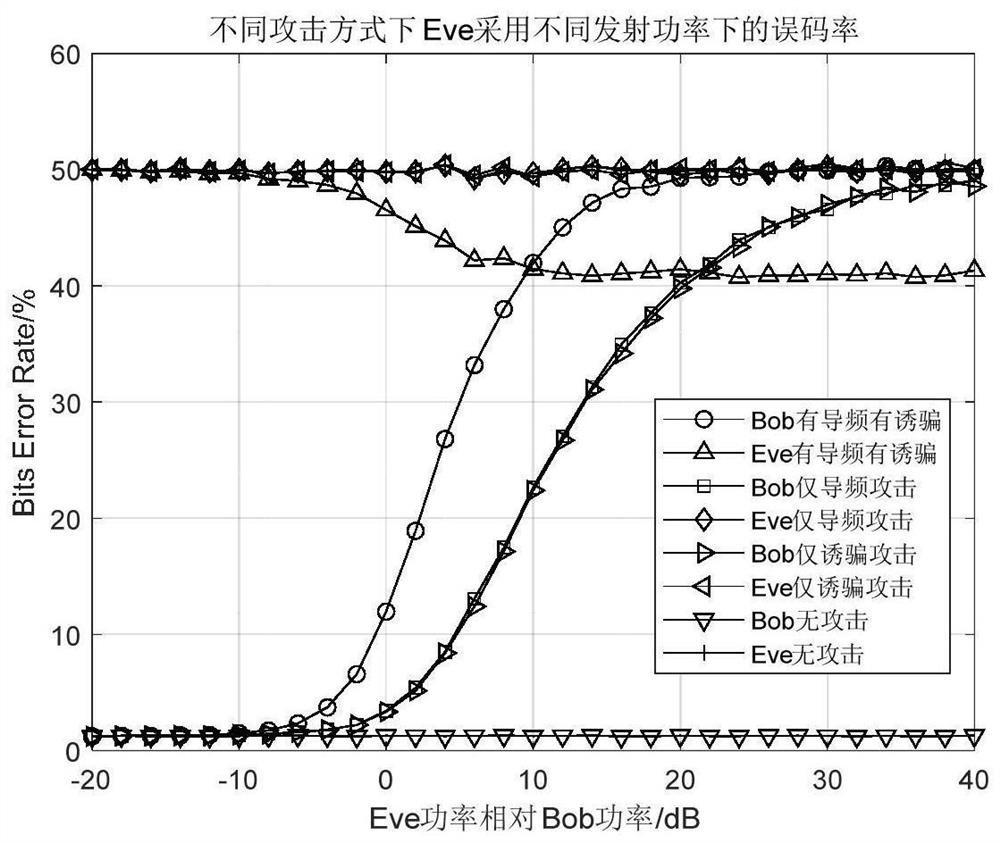
[0043] refer to Figure 1~4 , the present application provides a secure transmission method against active eavesdropping in a 5G system, the method comprising the following steps:
[0044] Step 1): Initiated by the legal receiving node, the coupled encrypted distribution of security parameters;
[0045] Step 2): Authenticate the coupling characteristic parameters, so that the source node restores the security parameters;
[0046] Step 3):...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com