Verifiable Distributed Database Access Control Method
An access control and database technology, applied in the database field, can solve problems such as security user private key leakage, single point of failure, and responsibility cannot be identified, and achieve high security, easy audit and verification, and good practicability
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
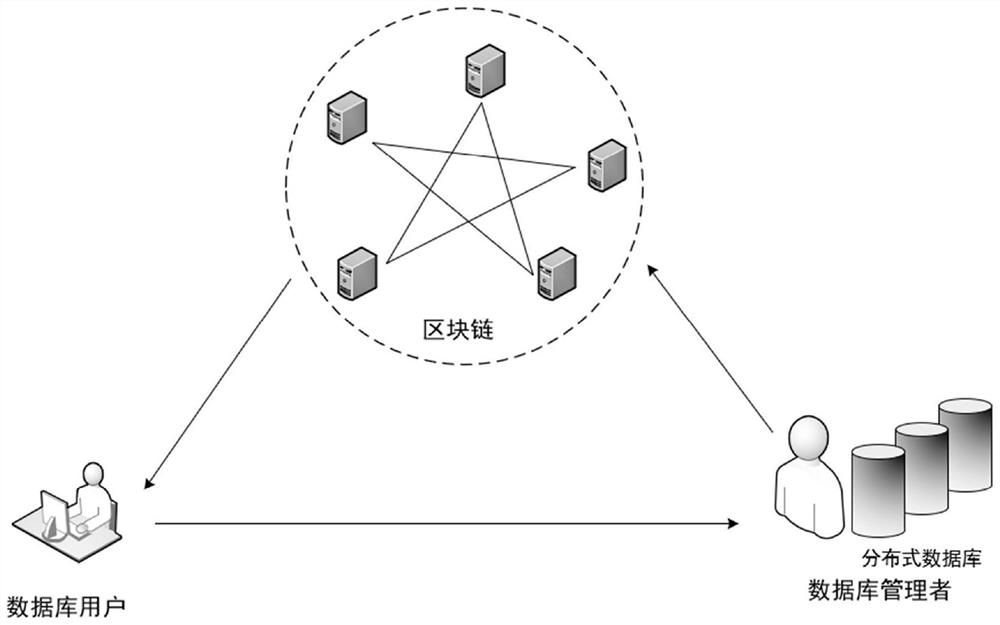
[0032] Such as figure 1 Shown is a schematic diagram of the method flow of the method of the present invention: the verifiable distributed database access control method provided by the present invention includes three participating roles: database user, database manager, and block chain, such as figure 2 shown, including the following steps:
[0033] The step of initializing the encryption parameters; specifically, the administrator selects hidden security parameters, generates a set of key pairs (PSK, MK) through the initialization function of the CP-ABE attribute encryption algorithm, and generates an asymmetric encryption key pair using the public key encryption algorithm (PAK, SK); Among them, PSK and PAK are public encryption parameters, MK is an attribute encryption master key saved only by the manager, and SK is a public key encrypted private key saved only by the manager;
[0034] During specific implementation, the manager selects a hidden security parameter λ, set...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com