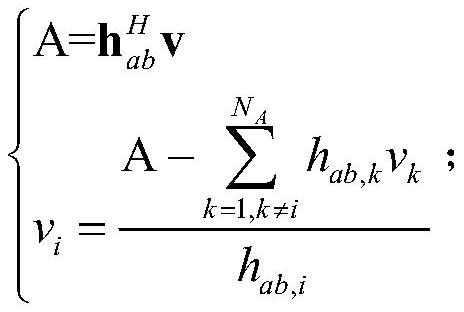Physical layer key distribution method based on random beams and edge calculation
A technology of key distribution and edge computing, which is applied to key distribution, can solve the problems that key distribution cannot be carried out at the same time, the complexity of communication protocols is high, and the hidden danger of information leakage is increased, so as to avoid the hidden danger of information leakage, improve security, The effect of increasing the hidden danger of information leakage
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0040] The technical solution of the present invention will be further described in detail below in conjunction with the accompanying drawings, but the protection scope of the present invention is not limited to the following description.
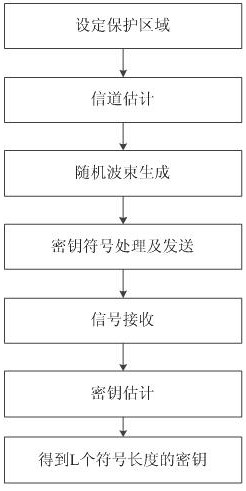
[0041] Such as figure 1 As shown, a physical layer key distribution method based on random beam and edge computing includes the following steps:
[0042] S1. Set the protection area:
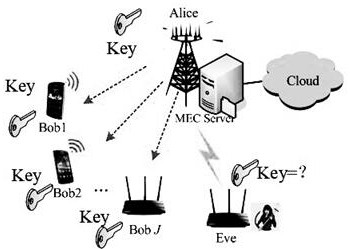
[0043] Suppose the edge device Alice and the legitimate terminal Bob need to share the key, and Eve is the eavesdropper;
[0044] The edge device Alice and the legitimate terminal Bob respectively surround themselves with a protection area with a radius of R. The protection area is the area where the eavesdropper Eve is prohibited from entering, so that the eavesdropper Eve cannot enter the protection area to eavesdrop. , the fence is realized, and it can also be a forbidden area on manual duty; that is, the distance between Eve and Alice is guaranteed to b...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com