Electronic cigarette encryption authentication method and system and electronic cigarette
An encryption authentication and electronic cigarette technology, applied in the field of electronic cigarettes, can solve the problems of no authentication process, complex communication circuits, and less smoke, and achieve the effect of saving chip IO ports, simple circuit structure, and small occupied area
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
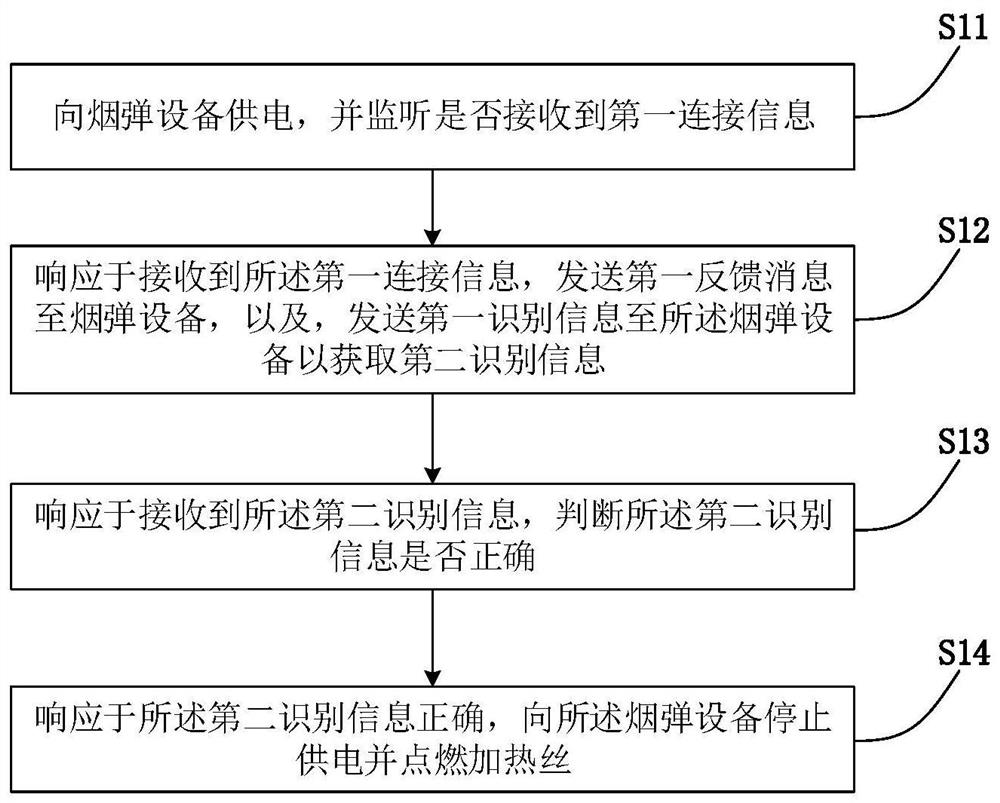
[0057] See figure 1 , figure 1 A flow chart of an electronic cigarette encryption authentication method provided by the embodiment of the present invention, which is applied to cigarette device, includes:
[0058] S11. Supply power to the pod device, and monitor whether the first connection information is received;
[0059]In this embodiment, the pod device does not have an independent power supply unit. After the pod device needs to be electrically connected to it, the pod device can supply power to the pod device through the power supply interface. In one example, the power supply interface can be used simultaneously. Signal transmission, that is, power supply and communication through a single line, reduces the design complexity of the device, effectively saves the chip I / O port, reduces the size of the device, thereby improving chip performance and reducing power consumption.
[0060] After the power supply is normal, the pod device can receive and process information no...
Embodiment 2
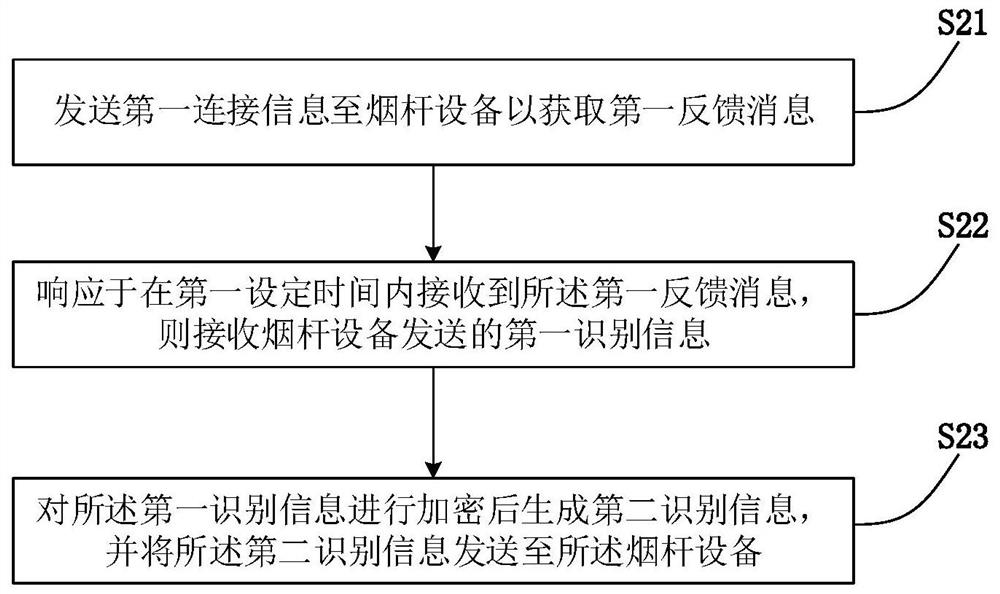
[0073] See image 3 , image 3 An electronic cigarette encryption authentication method provided by the embodiment of the present invention is a flow chart of the pod terminal, which is applied to the pod device, including:
[0074] S21. Send the first connection information to the tobacco device to obtain the first feedback message;
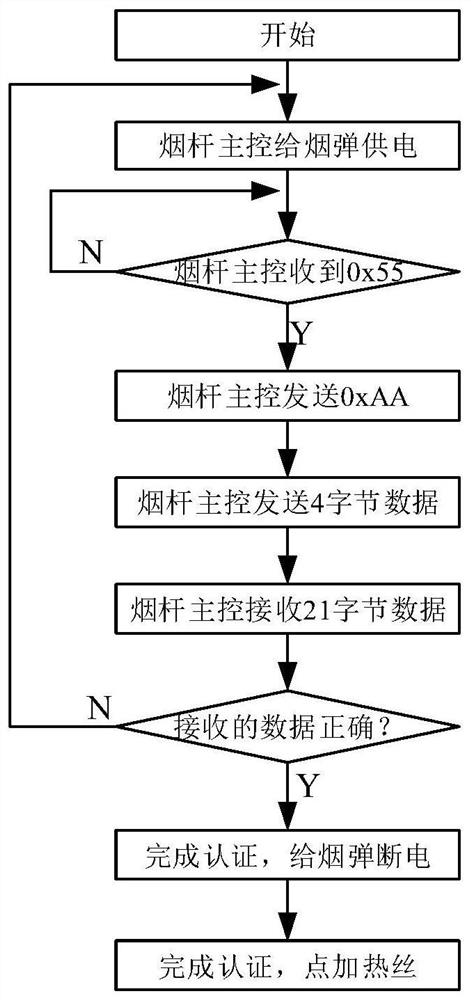
[0075] After the device is powered normally, the pod device actively sends the first connection information to the device to inform the device that it can send information normally, so as to request the device for identity authentication information. Correspondingly, the pod device needs to monitor whether the first connection information sent by the pod device is received, so as to confirm whether the pod device is working normally. For example, see Figure 4 , Figure 4 It is a specific example diagram of the pod end of an electronic cigarette encryption authentication method provided by the embodiment of the present invention. The first co...
Embodiment 3
[0088] See Figure 5 , Figure 5 A circuit structure schematic diagram of an electronic cigarette encryption authentication system provided by an embodiment of the present invention, including:
[0089] The main control chip set on the device of the cigarette rod, the main control chip includes a voltage source VCC, a main power supply communication interface IO1, a ground terminal GND, and a resistor R, wherein the resistor R is connected between the voltage source VCC and the main power supply Between the communication interface IO1;
[0090] The slave chip set on the pod device, the slave chip includes a first power interface Y1, a second power interface Y2, a slave power supply communication interface IO, a capacitor pin CAP, a capacitor ground pin CAPGND, a capacitor C, A heating wire F, wherein the capacitor C is connected between the capacitor pin CAP and the capacitor ground pin CAP GND, and the heating wire F is arranged between the first power supply interface Y1 a...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com