Software authentication method and device, processing node and storage medium
An authentication method and a technology of an authentication device, applied in the information field, can solve the problems of increasing the risk of the license issuance mechanism being cracked, the difficulty of changing the form and content, and the difficulty of dynamic adjustment.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
example 1
[0163] This example provides an authentication system consisting of:
[0164] Terminal for software installation. Responsible for the interaction with the blockchain authentication system.
[0165] Authentication module: through the interaction with the blockchain authentication system, send the license information (license) encrypted by the public key and receive the authentication message returned by the blockchain system, and execute the instructions returned by the blockchain authentication system.
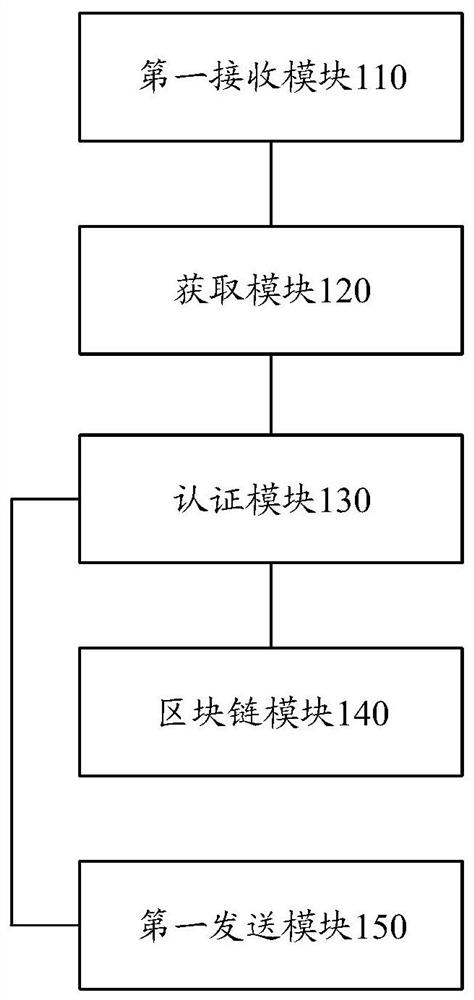
[0166] The blockchain authentication system is responsible for authenticating and updating the license information of the management software and storing transaction records, including: smart contract module, state storage database module and transaction information storage module.
[0167] Smart contract module: responsible for monitoring and receiving software license authentication requests and returning authentication results to the software. The license information encr...
example 2
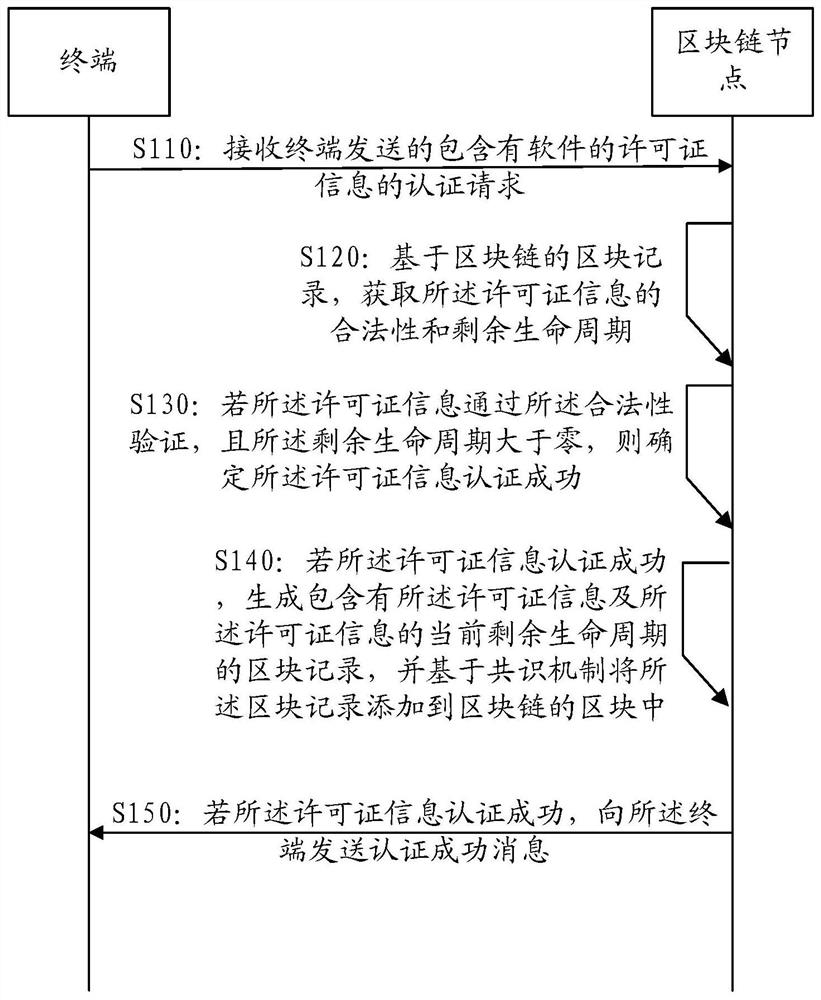
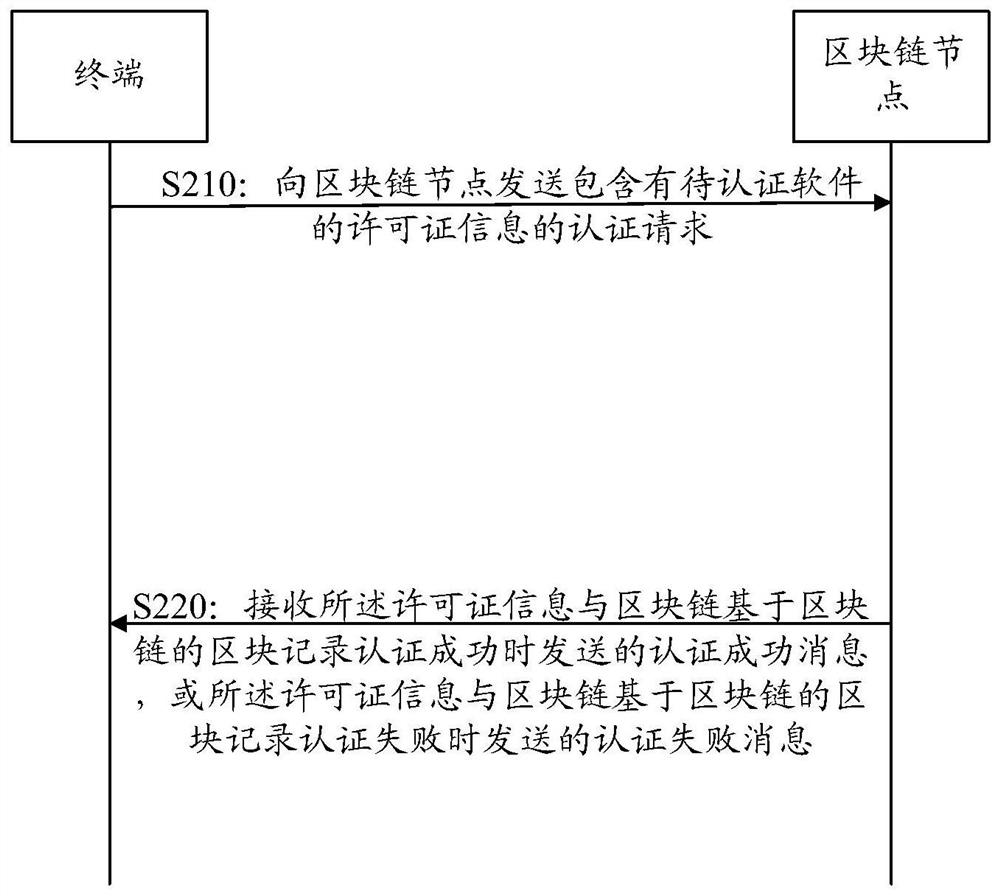
[0171] The software application certification process may include:
[0172] The connection with the nodes in the blockchain system is normal: when the software starts authentication, according to the configured blockchain node server address list, select any node to actively initiate a connection, and send the license encrypted by the public key to the smart contract module of this node Information, if the license information is legal and valid and the remaining number of authentications is greater than 0, the smart contract module responds that the authentication is successful. At this time, the software authentication is successful and the authentication process ends; if the license information is legal and valid but the remaining number of authentications is 0, the smart contract module returns the license If the authentication message with the remaining number of authentications is 0, the license authentication fails; if the license information is invalid, the smart contrac...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com