Internal and external network system data transmission encryption method and device, equipment and medium
A system data and encryption method technology, applied in the computer field, can solve the security risks of data exchange schemes, and it is difficult to meet the problems of security, efficiency, convenience, and management of file exchange inside and outside the enterprise, so as to avoid the risk of data leakage and improve reliability. Visibility, the effect of improving work efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
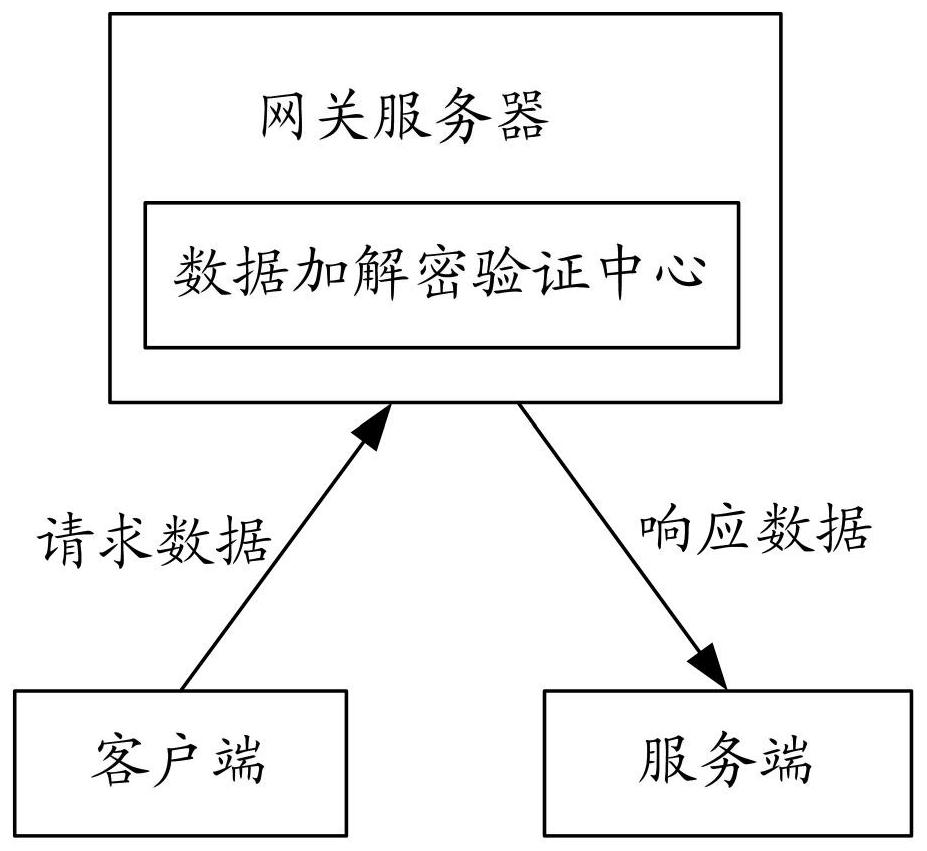
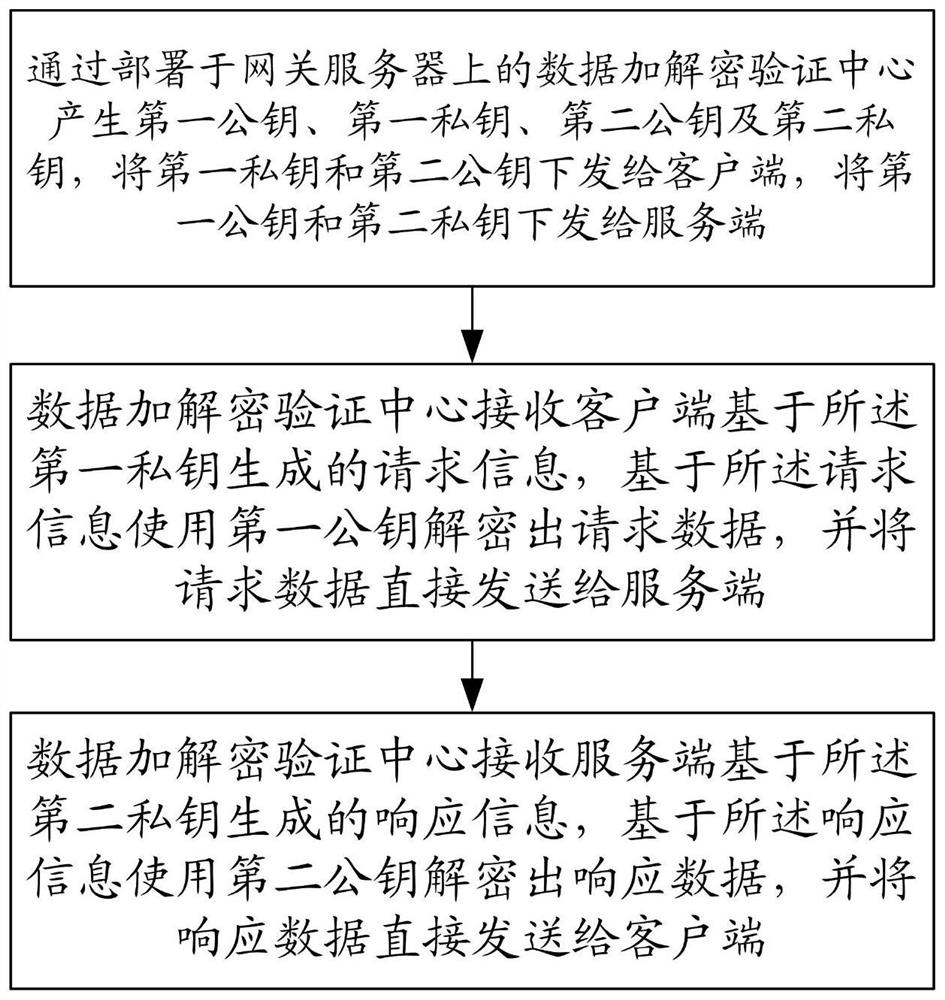
[0057] This embodiment provides a data transmission encryption method for internal and external network systems, such as figure 2 As shown, the method includes:
[0058] Generate the first public key, the first private key, the second public key and the second private key through the data encryption and decryption verification center deployed on the gateway server, and send the first private key and the second public key to the client, Send the first public key and the second private key to the server. Of course, in the actual implementation, you can also send the first private key and the second public key to the server, and send the first public key and the second private key to the server. The key is issued to the client; wherein, the first private key and the second private key are used to implement the signature function of data, and the first public key and the second public key are used to implement the signature verification function; for example, the present inventio...
Embodiment 2
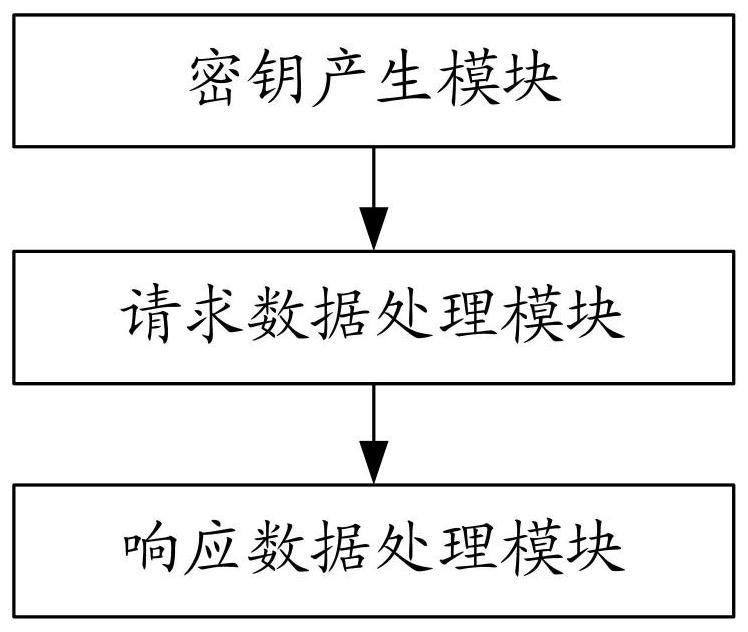
[0075] In this embodiment, a data transmission encryption device for internal and external network systems is provided, such as image 3 As shown, the device includes a key generation module, a request data processing module and a response data processing module;
[0076] The key generation module is used to generate the first public key, the first private key, the second public key and the second private key through the data encryption and decryption verification center deployed on the gateway server, and combine the first private key and the second private key The second public key is sent to the client, and the first public key and the second private key are sent to the server. Of course, in the actual implementation, the first private key and the second public key can also be sent to the server. Send the first public key and the second private key to the client; wherein, the first private key and the second private key are used to implement the data signature function, and...
Embodiment 3
[0094] This embodiment provides an electronic device, such as Figure 4 As shown, it includes a memory, a processor, and a computer program stored in the memory and operable on the processor. When the processor executes the computer program, any implementation manner in Embodiment 1 can be realized.
[0095] Since the electronic device introduced in this embodiment is the device used to implement the method in Embodiment 1 of this application, based on the method described in Embodiment 1 of this application, those skilled in the art can understand the electronic device of this embodiment. Specific implementation methods and various variations thereof, so how the electronic device implements the method in the embodiment of the present application will not be described in detail here. As long as a person skilled in the art implements the equipment used by the method in the embodiment of the present application, it all belongs to the protection scope of the present application. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com