Crawler recognition method, device and equipment and computer storage medium
A crawler and algorithm technology, applied in the field of computer security, can solve the problems of inability to identify, low crawler identification accuracy, etc., and achieve the effect of improving the identification accuracy.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
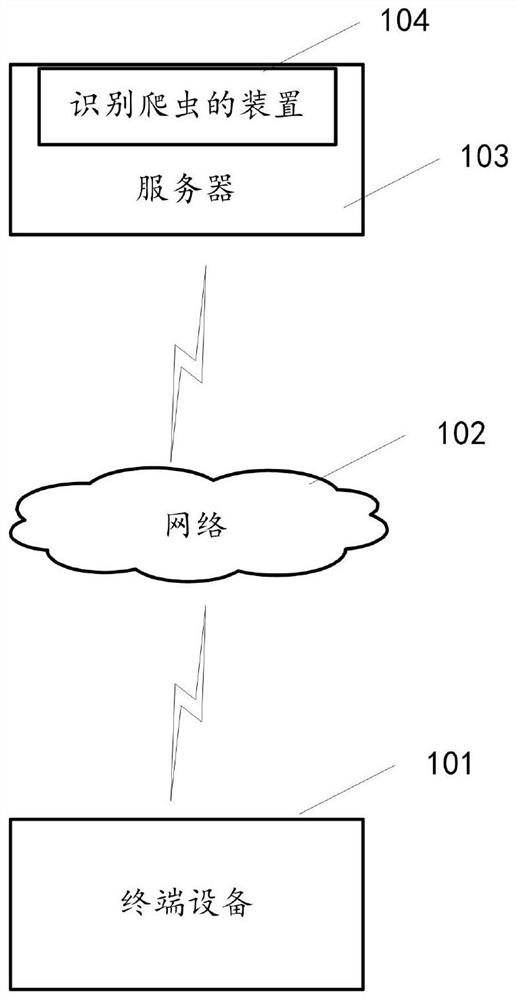
[0075] figure 1 An exemplary system architecture of the method or apparatus for identifying crawlers in the embodiments of the present invention can be applied.
[0076] like figure 1 As shown, the system architecture may include a terminal device 101 , a network 102 and a server 103 . The network 102 is used as a medium for providing a communication link between the terminal device 101 and the server 103 . Network 102 may include various connection types, such as wires, wireless communication links, or fiber optic cables, among others.
[0077] A user can use a terminal device 101 to interact with a server 103 through a network 102 . Various applications may be installed on the terminal device 101, such as voice interaction applications, web browser applications, communication applications, and the like.
[0078] The terminal device 101 may be any terminal device, including but not limited to a smart phone, a smart tablet, a notebook computer, a PC, a smart wearable devic...
Embodiment 2
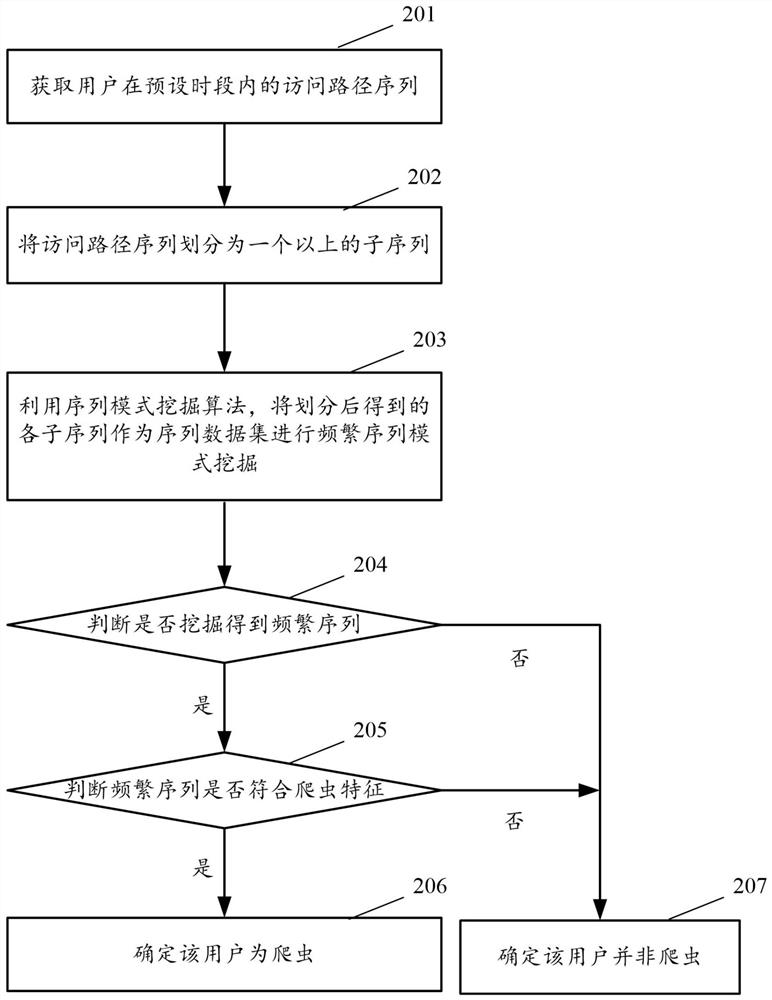
[0081] figure 2 It is a flow chart of a method provided by the embodiment of the present application. The execution body of the method flow can be a device for identifying crawlers. The device can be an application located on the server side, or it can also be a plug-in or software development tool in an application located on the server side. A functional unit such as a software development kit (Software Development Kit, SDK) may also be located in a terminal device with relatively strong computing capabilities, which is not particularly limited in this embodiment of the present invention. like figure 2 As shown in , the method may include the following steps:
[0082] In 201, an access path sequence of a user within a preset period is acquired.
[0083] After the user visits the website, the server may record the user's access log, which may include information such as the user's access path and access time. In this step, the user's access paths during the preset time p...
Embodiment 3
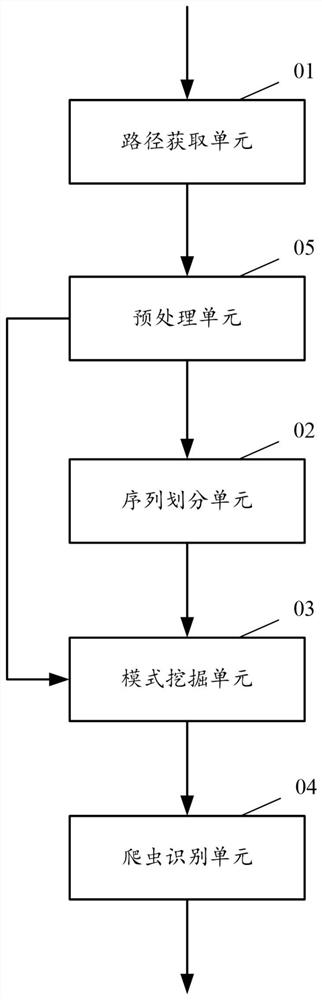
[0132] image 3 Schematic diagram of the structure of the device for identifying reptiles provided by the embodiment of the present application, such as image 3 As shown in , the device may include: a path acquisition unit 01 , a sequence division unit 02 , a pattern mining unit 03 and a crawler identification unit 04 , and may further include: a preprocessing unit 05 . The main functions of each component unit are as follows:
[0133] The path acquisition unit 01 is configured to acquire the user's access path sequence within a preset period of time.
[0134] The preprocessing unit 05 is configured to preprocess the access path sequence, and provide the preprocessed access path sequence to the sequence division unit 02 .
[0135] Wherein, the above-mentioned pretreatment includes at least one of the following:
[0136] Delete non-actively requested access paths in the access path sequence;
[0137] Merge adjacent and identical access paths in a sequence of access paths. ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com