Network killing chain detection method, prediction method and system
A detection method and network technology, applied in the field of network security, can solve the problems such as the underlying implementation of the analysis method not given, the lack of visualization effect, and the difficulty in obtaining
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
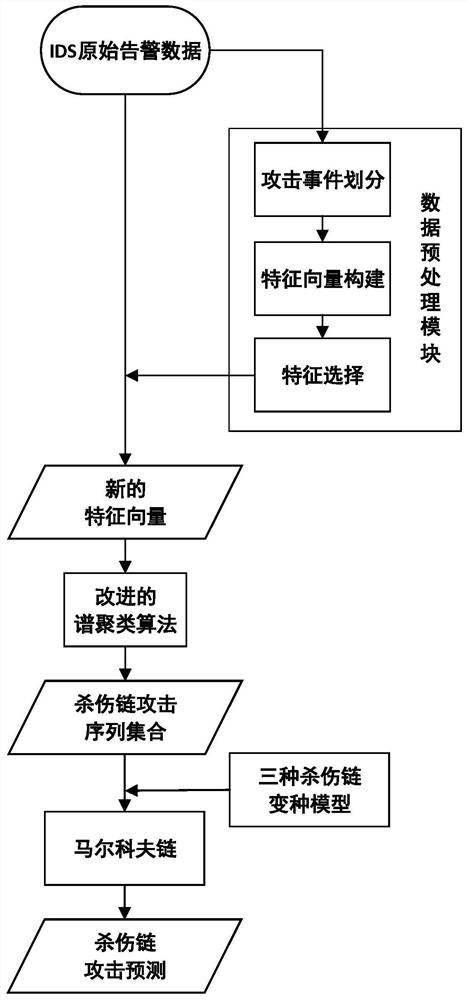
[0068] This embodiment provides a specific kill chain detection and prediction method, which is implemented according to the following steps:
[0069] Step 1, construct a d-dimensional feature vector:
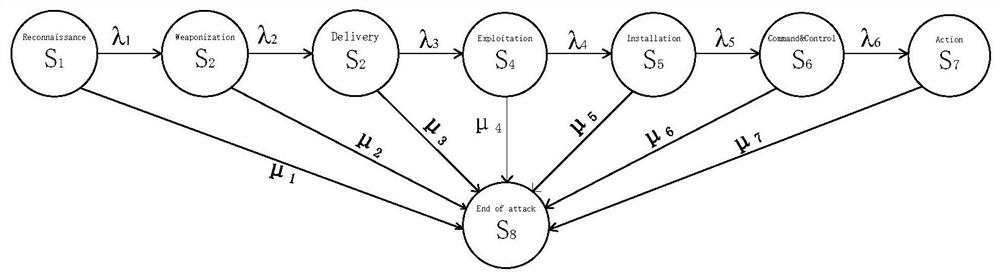
[0070] (1.1) Count all attack event types in the IDS alarm log data, divide the attack events into seven stages of the kill chain model according to their characteristics, and add the number of stages as a new field to the IDS alarm log data. Among them, the IDS alarm log data is used to record the detailed information of the host or server being attacked;
[0071] (1.2) select the d fields relevant to the kill chain analysis in the IDS alarm log data;
[0072] (1.3) Suppose a f and a g Represent two records or two pieces of data in the IDS alarm log data respectively, the subscripts f and g represent the sorting numbers of the data, and n≥g>f>0. Then define the similarity measure of each field, as follows:
[0073] (1) The date and time reflect the contextual relationship...
specific example
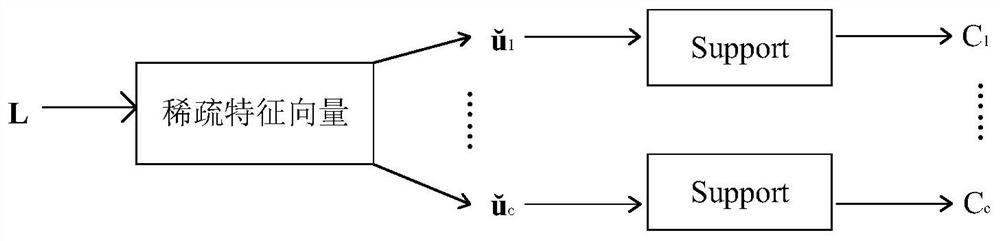
[0128] Step 1, construct a 9-dimensional feature vector:
[0129] (1.1) Count all attack event types in the IDS alarm log data, divide the attack events into seven stages of the kill chain model according to their characteristics, and add the number of stages as a new field to the IDS alarm log data. The specific attack events are divided into the following table:
[0130]
[0131] (1.2) Select 9 fields related to network kill chain analysis in the IDS alarm log data, as shown in the following table:
[0132] field illustrate LocalDateTime date and time RequestMethod HTTP request method IP IP address SeverPort server port number ClientPort client port number ClientEnv client environment HTTPCode HTTP response code Locate geographic location event The stage in the kill chain of the attack
[0133] (1.3) Suppose a f and a g Represent two records or two pieces of data in the IDS alarm log data re...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com