Image compression encryption method and cloud auxiliary decryption method based on compressed sensing and optical transformation
An optical transformation and image compression technology, applied in the field of cloud-assisted decryption, which can solve the problems of limited algorithm security, low quality of compressed sensing reconstruction, and poor security.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
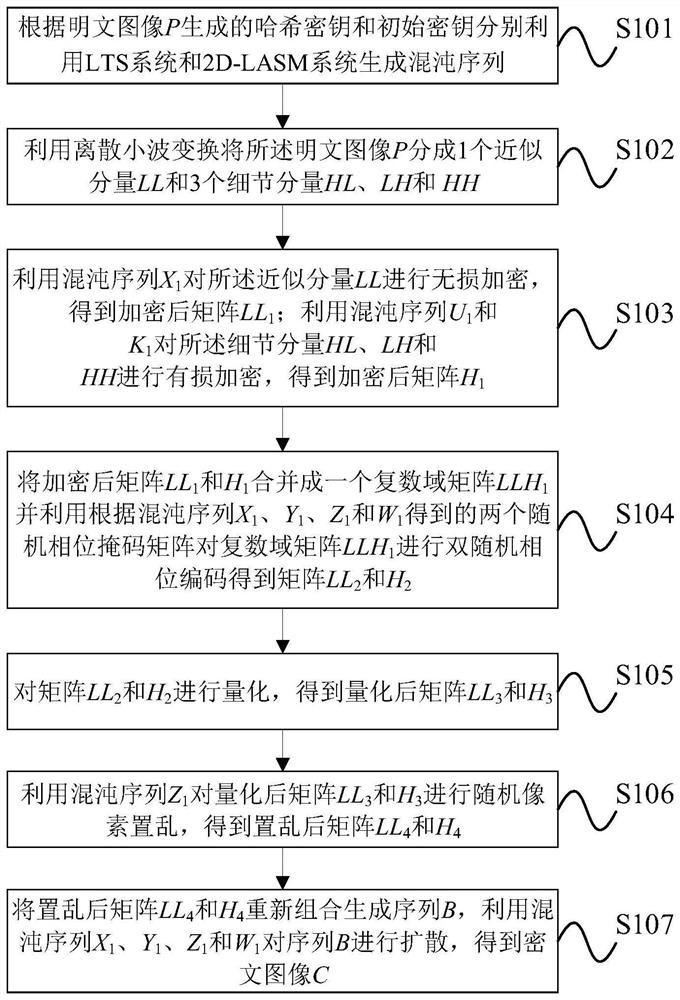
[0095] Such as figure 1As shown, the embodiment of the present invention provides an image compression encryption method based on compressed sensing and optical transformation, comprising the following steps:
[0096] S101: The hash key and the initial key generated according to the plaintext image P use the LTS system and the 2D-LASM system to generate a chaotic sequence, wherein the LTS system is used to generate a chaotic sequence U 1 and K 1 , the 2D-LASM system is used to generate the chaotic sequence X 1 , Y 1 ,Z 1 and W 1 ; The size of the plaintext image P is M×M;
[0097] Specifically, the LTS system refers to the Logistic-tent system, which has good chaotic cryptographic properties, which is a nonlinear combination of the Logistic map and the tent map, and is considered as a seed map. The LTS system is defined by equation (1):
[0098]
[0099] where μ is a control parameter in the range (0,4], and the state value z n ∈[0,1]. The output sequence of LTS fo...
Embodiment 2
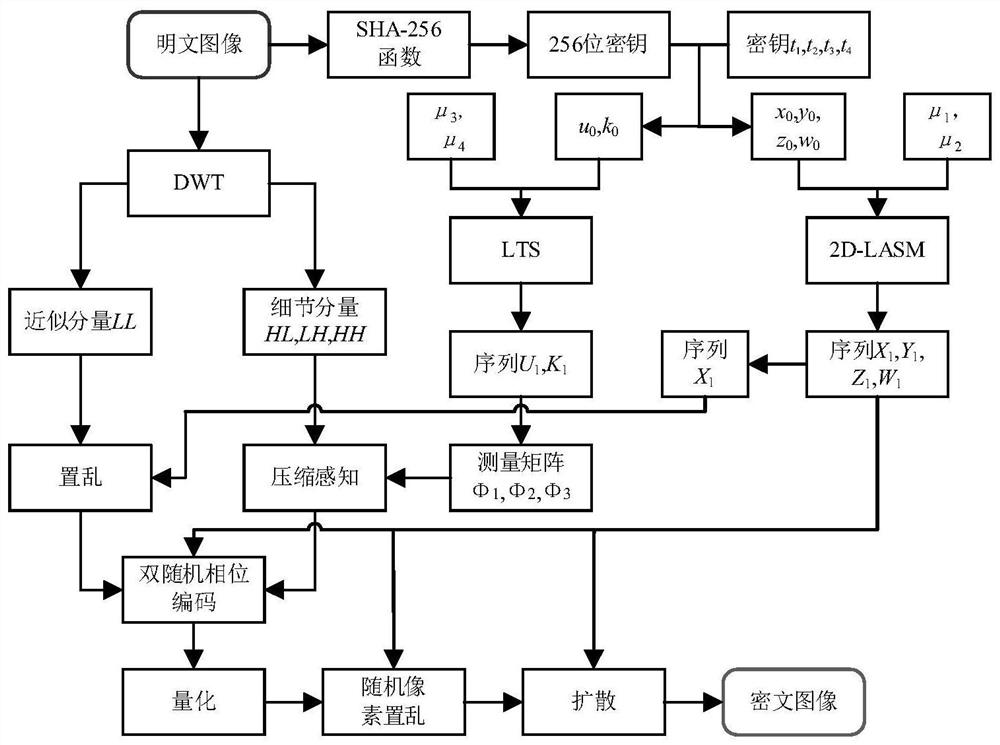
[0111] Such as figure 2 As shown, the embodiment of the present invention provides another image compression encryption method based on compressed sensing and optical transformation, including the following steps:
[0112] S201: Generate the initial value x of the LTS system and the 2D-LASM system according to the hash key and the initial key generated by the plaintext image P according to formula (3) 0 、y 0 ,z 0 、w 0 , u 0 and k 0 :
[0113]
[0114] Among them, t 1 , t 2 , t 3 and t 4 Indicates the given initial key; k i Indicates the hash key, i=1,2,...,32; Indicates bitwise XOR operation; | indicates bitwise OR operation; & indicates bitwise AND operation; for example: Indicates the bitwise exclusive OR operation of x and y, x|y indicates the bitwise OR operation of x and y, and x&y indicates the bitwise AND operation of x and y.
[0115] Specifically, the SHA-256 function is used to generate a 256-bit hash key for the M×M plaintext image P, and then t...
Embodiment 3
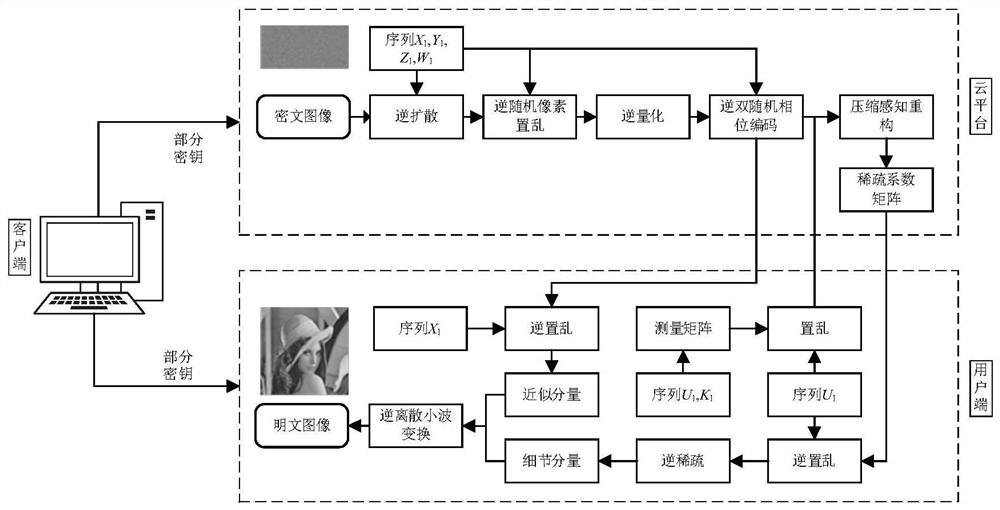
[0159] Corresponding to the above encryption methods, such as image 3 As shown, the embodiment of the present invention also provides a cloud-assisted decryption method based on compressed sensing and optical transformation, including the following steps:
[0160] S301: Using the chaotic sequence X on the cloud platform 1 , Y 1 ,Z 1 and W 1 Perform inverse diffusion on the ciphertext image to obtain the matrix LL 4 and H 4 ;
[0161] S302: Using the chaotic sequence Z on the cloud platform 1 pair matrix LL 4 and H 4 Perform inverse random pixel exchange to obtain matrix LL 3 and H 3 ;
[0162] S303: On the cloud platform, the matrix LL 3 and H 3 Perform inverse quantization to obtain the matrix LL 2 and H 2 ;
[0163] S304: On the cloud platform, the matrix LL 2 and H 2 Combined into a complex field matrix LLH 2 , using according to the chaotic sequence X 1 , Y 1 ,Z 1 and W 1 The resulting two random phase mask matrices pair the complex field matrix LLH ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com