Unauthorized access vulnerability detection method and system, server and storage medium
An unauthorized access and vulnerability detection technology, applied in the field of security testing, can solve problems such as large manpower demand, easy to miss unauthenticated identity access logic loopholes, etc., and achieve the effect of saving manpower and material resources
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
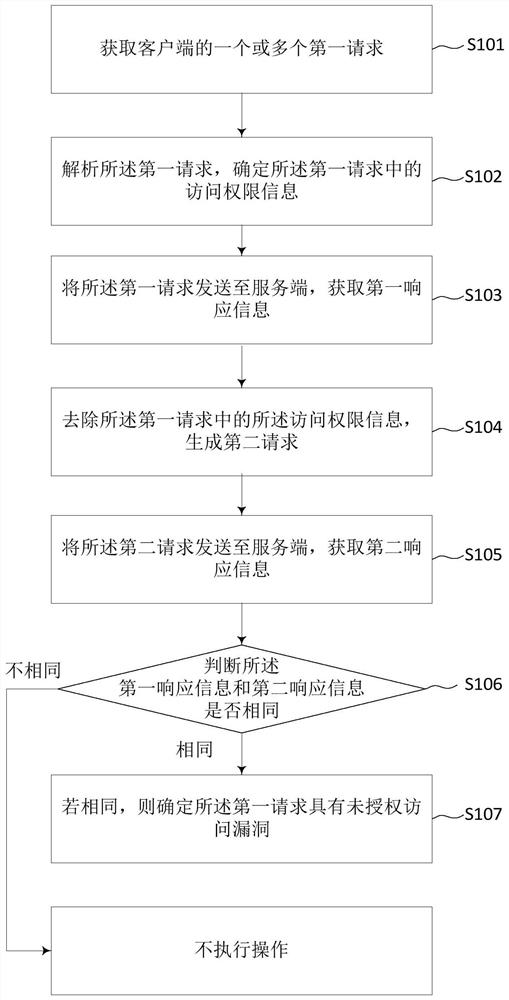
[0060] This embodiment provides a method for detecting unauthorized access vulnerabilities, which is executed by a detection terminal independent of the client and server, such as figure 1 shown, including:
[0061] S101. Obtain one or more first requests from the client;
[0062] The first request in this step refers to the request initiated by the client to realize the target service. By setting proxy access, the first request initiated by the client is first captured by the detection end, and after detection and judgment, it is sent to the server or marked according to whether the first request has a loophole. This step implements a large number of complete and automated captures of user service requests for system access through the test terminal to ensure the integrity of the tested service traffic.
[0063] In an alternative embodiment, since the request business flow is often relatively large and contains a large number of resource requests, such as pictures and other...
Embodiment 2
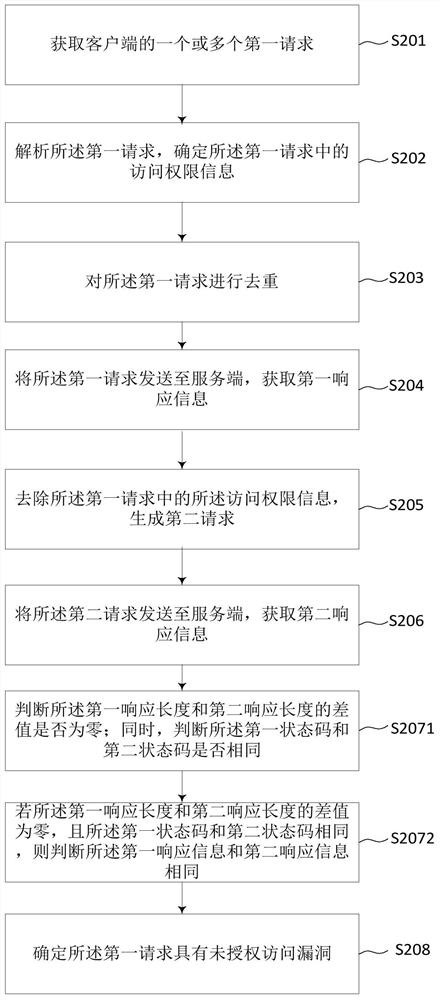
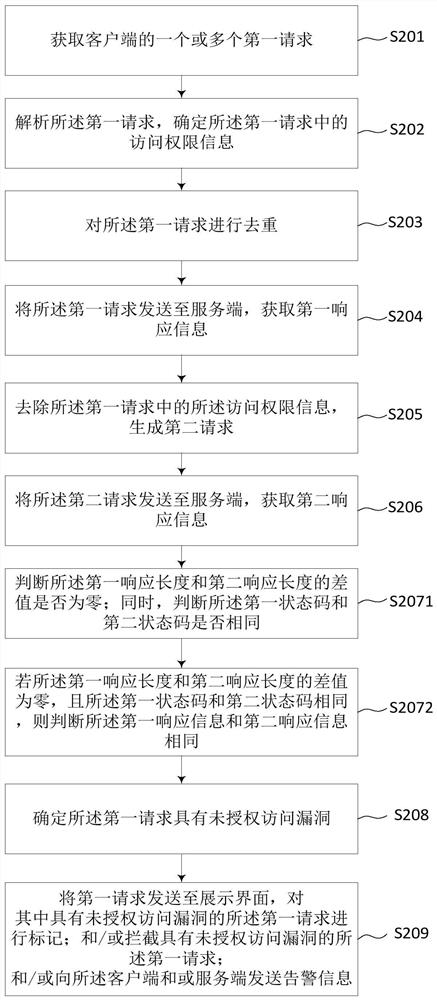
[0078] In this embodiment, on the basis of the above embodiments, a step of deduplicating the first response request is added, and a detailed description of the judging process is added, such as figure 2 , including the following steps:
[0079] S201. Acquire one or more first requests from a client.
[0080] S202. Parse the first request, and determine access right information in the first request.
[0081] S203. Deduplicate the first request.
[0082] In this step, the same request may be repeatedly initiated by the client, and duplicate requests are avoided by deduplication to be imported into subsequent tests to save detection time. Specifically, the deduplication method may be: calculating first request fingerprints of the one or more first requests based on a preset algorithm; and judging whether there are duplicate first request fingerprints. If repeated, delete the first request corresponding to the repeated first request fingerprint.
[0083] In this step, the fi...
Embodiment 3
[0096] Such as Figure 4 , the present embodiment provides an unauthorized access vulnerability detection system 3, comprising the following modules:
[0097] The first obtaining module 301 is configured to obtain one or more first requests from the service flow sent from the client to the server. The module is further configured to filter the service traffic based on preset filtering rules, so as to obtain the one or more first requests. Optionally, the detection end may store one or more global variables in advance, and deploy them in a distributed manner through the detection branch of the detection end, so as to deal with the situation that multiple clients of the detection distributed system initiate one or more first requests. Then, the module is also used for: acquiring requests from one or more clients to the server at the same time.
[0098] The parsing module 302 is configured to parse the first request and determine the access right information in the first reques...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com