Unauthorized email determination device, unauthorized email determination method and unauthorized email determination program
A technology for judging devices and emails, applied to electrical components, computer components, machine learning, etc., can solve problems such as inability to detect counterfeit emails
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment approach 1
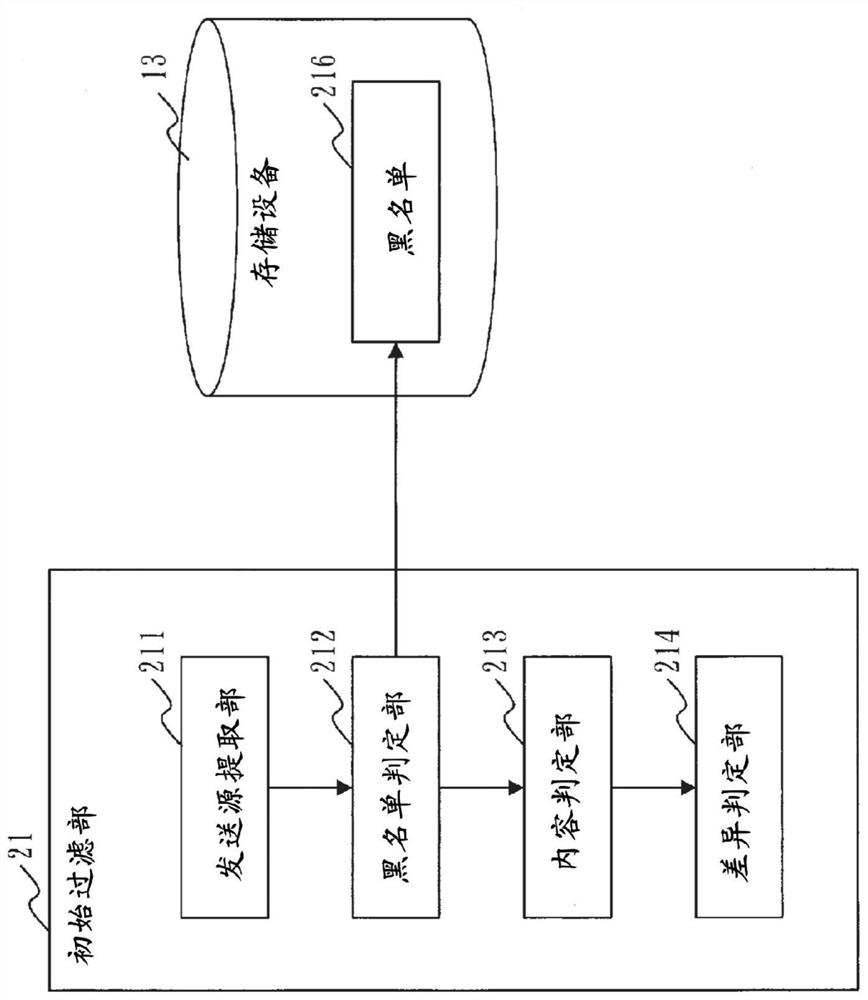
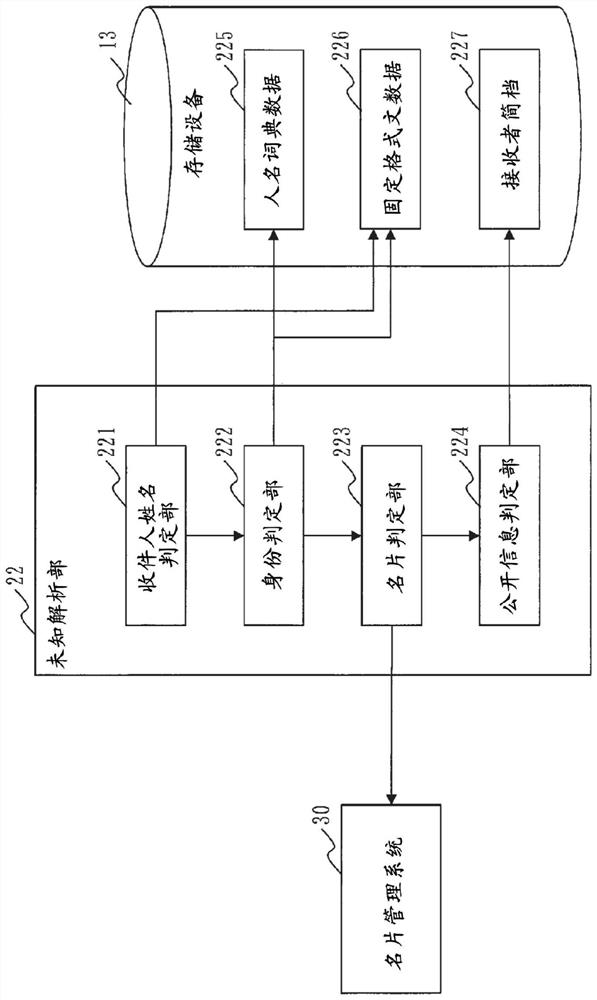
[0043] ***Description of structure***
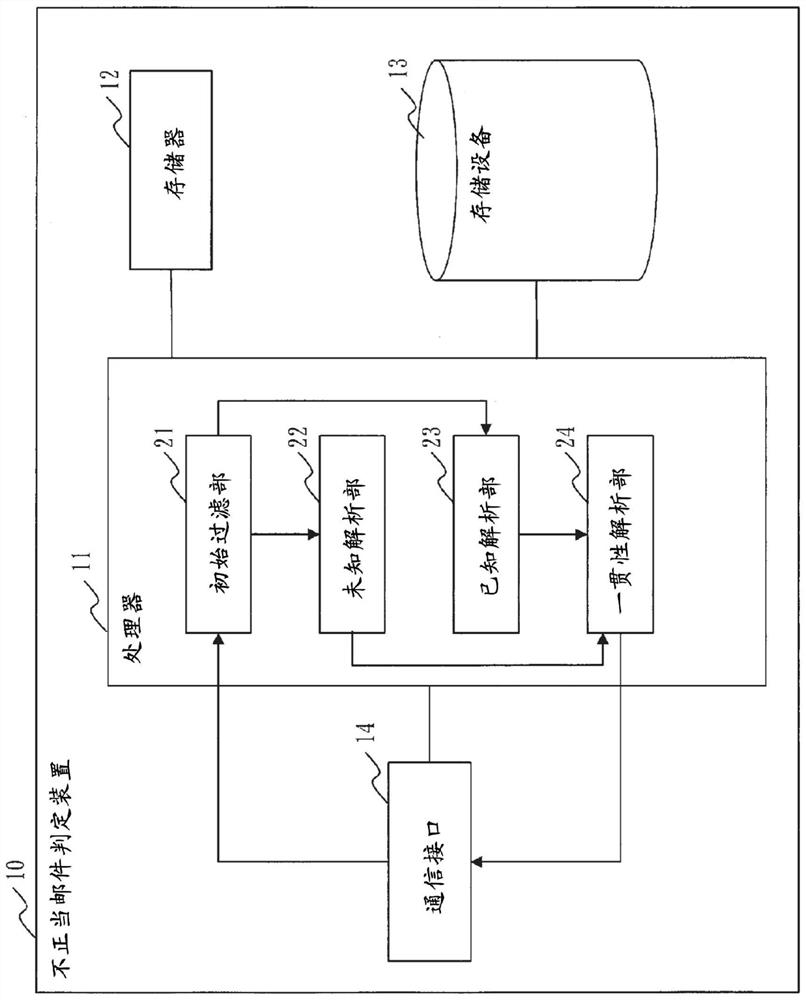
[0044] refer to figure 1 The configuration of the fraudulent mail determination device 10 according to Embodiment 1 will be described.
[0045] The fraudulent mail determination device 10 is a computer.
[0046] The fraudulent mail determination device 10 includes hardware such as a processor 11 , a memory 12 , a storage 13 , and a communication interface 14 . The processor 11 is connected to other hardware via signal lines, and controls these other hardware.
[0047] The processor 11 is an IC (Integrated Circuit) that performs processing. As a specific example, the processor 11 is a CPU (Central Processing Unit: Central Processing Unit), a DSP (Digital Signal Processor: Digital Signal Processor), and a GPU (Graphics Processing Unit: Graphics Processing Unit).
[0048]The memory 12 is a storage device that temporarily stores data. As a specific example, the memory 12 is SRAM (Static Random Access Memory: Static Random Access Memory)...
Deformed example 1
[0204] In Embodiment 1, each functional component is realized by software. However, as Modification 1, each functional component can also be realized by hardware. Regarding this Modification 1, differences from Embodiment 1 will be described.
[0205] refer to Figure 17 The configuration of the fraudulent mail determination device 10 according to Modification 1 will be described.
[0206] When realizing each functional component by hardware, the fraudulent mail determination apparatus 10 is equipped with the electronic circuit 15 instead of the processor 11, the memory 12, and the storage device 13. The electronic circuit 15 is a dedicated circuit that realizes the functions of each functional component, the memory 12 , and the storage device 13 .
[0207] As the electronic circuit 15, a single circuit, a composite circuit, a programmed processor, a parallel programmed processor, logic IC, GA (Gate Array: Gate Array), ASIC (Application Specific Integrated Circuit: Applicat...
Deformed example 2
[0210] As Modification 2, some functional constituent elements may be realized by hardware, and other functional constituent elements may be realized by software.
[0211] The processor 11, the memory 12, the storage device 13 and the electronic circuit 15 are referred to as processing circuits. In other words, the functions of each functional structural element are realized by the processing circuit.
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com