Permission monitoring processing method and device, computer equipment and medium
A processing method and permission technology, applied in the computer field, can solve problems such as a large amount of labor costs, low audit efficiency, and undetectable upgrade codes, and achieve the effect of strengthening control rights
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
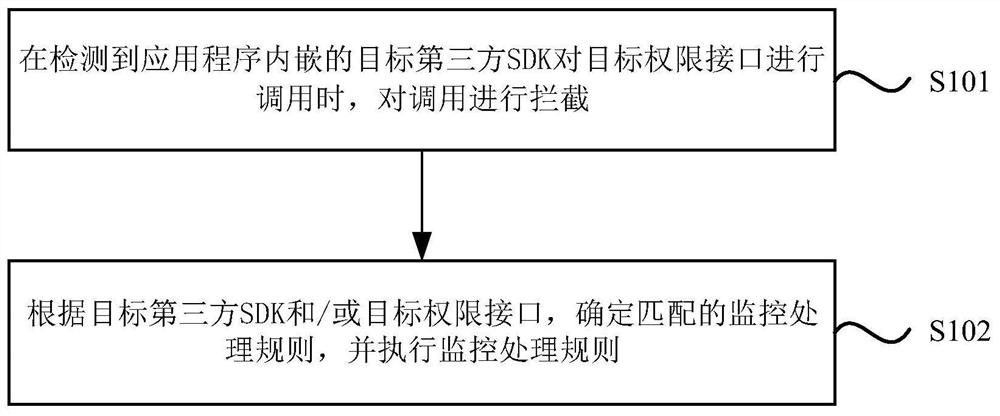
[0042] figure 1 It is a flow chart of a rights monitoring and processing method provided in Embodiment 1 of the present invention. This embodiment is applicable to the situation of managing the rights of third-party SDKs accessed inside the application program. This method can be executed by a rights monitoring and processing device. The device can be implemented in the form of software and / or hardware, and generally can be integrated into the application program in the form of SDK, plug-in or program code. Such as figure 1 As shown, the method includes:
[0043] Step S101, when it is detected that the target third-party SDK embedded in the application program calls the target permission interface, intercept the call.
[0044] The application program can be various programming languages that users can use, and a collection of programs written in various programming languages to meet the application requirements of users. For example, it can include general-purpose applic...
Embodiment 2
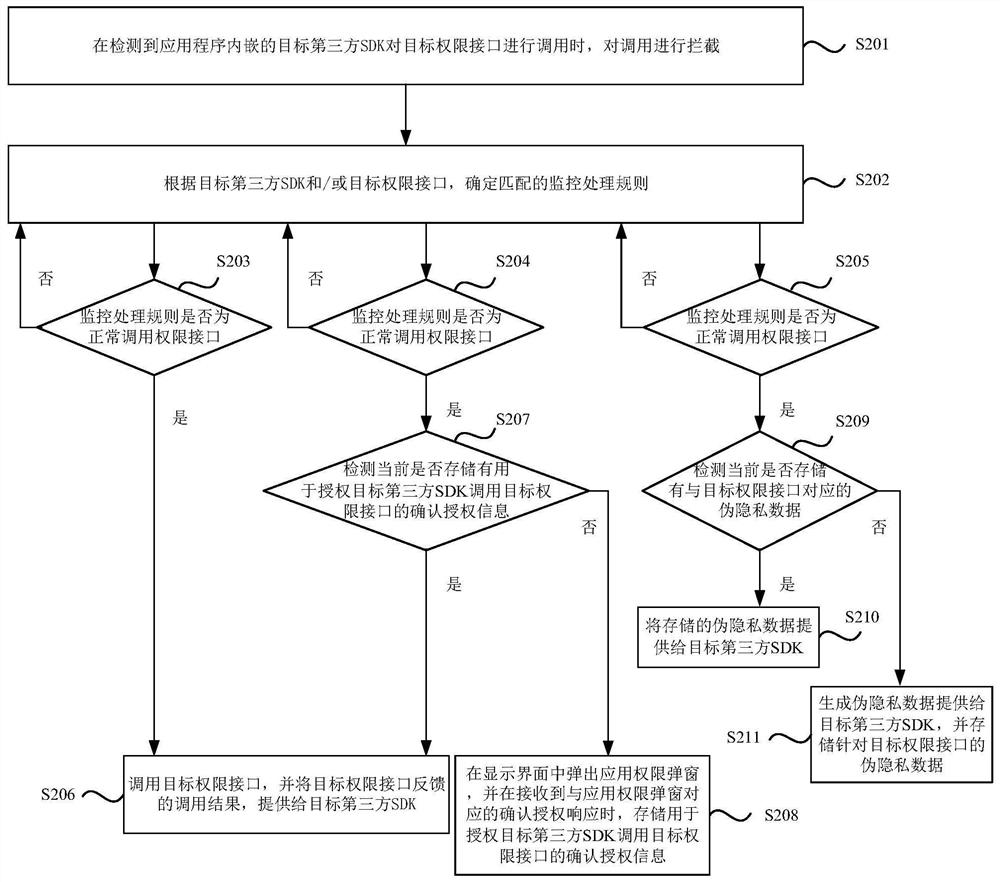
[0062] figure 2 It is a flow chart of another permission monitoring processing method provided by Embodiment 2 of the present invention. This embodiment is optimized on the basis of the above-mentioned embodiments, such as figure 2 As shown, the method includes:
[0063] Step S201, when it is detected that the target third-party SDK embedded in the application program calls the target permission interface, intercept the call.
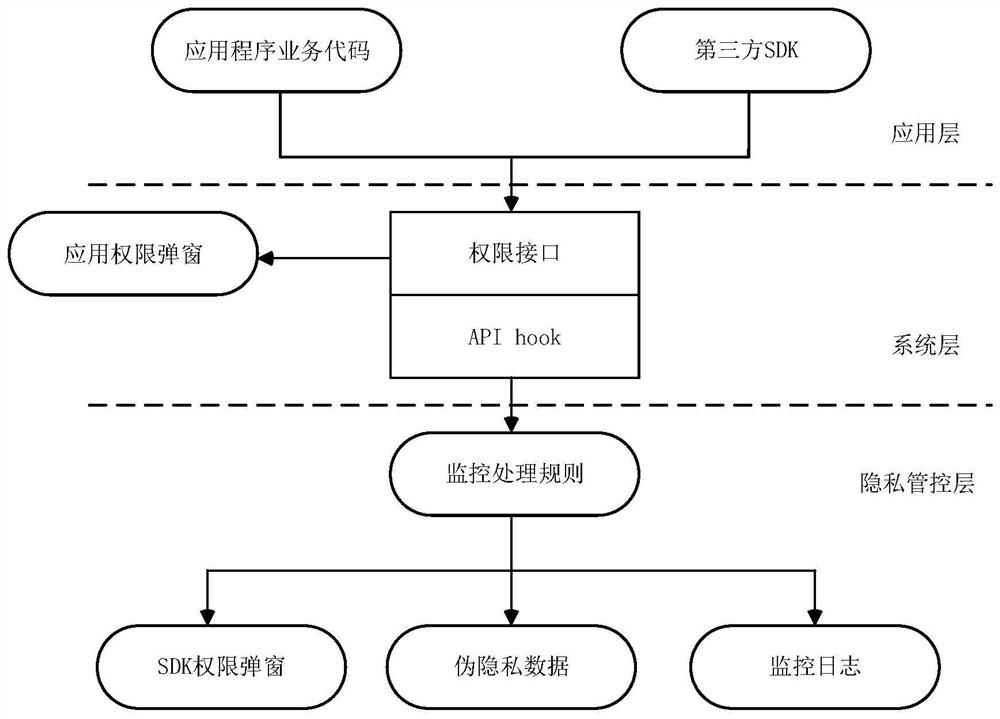
[0064] image 3 It is a system architecture diagram of an application program provided by Embodiment 2 of the present invention. Such as image 3 As shown, the system architecture of the application program may include an application layer, a system layer, and a privacy control layer. The application layer can include application business codes and third-party SDKs. Wherein, the application business code can be understood as other code modules except the third-party SDK, and the third-party SDK can be understood as the third-party SDK that needs ...
Embodiment 3
[0087] Figure 4 It is a flow chart of another permission monitoring processing method provided by Embodiment 3 of the present invention. This embodiment is optimized on the basis of the above embodiments, as shown in Figure 4 As shown, the method includes:
[0088] Step S301, when it is detected that the target third-party SDK calls the target permission interface, intercept the call, and jump to execute the permission monitoring and processing interface.
[0089] The permission monitoring and processing interface may be an interface for performing permission monitoring and processing on the target third-party SDK when the target third-party SDK calls the target permission interface, and is used to monitor the legitimacy of the call.
[0090] In this embodiment, the target third-party SDK can be a compiled language SDK or a high-level interpreted language SDK. For SDKs of different programming languages, different interception and jump methods can be adopted to intercept ca...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com