Malicious software confrontation sample generation method combined with API fuzzy processing technology
A malware and obfuscation technology, applied in the direction of electrical digital data processing, genetic rules, genetic models, etc., can solve the problem that it is difficult to ensure that the malware function is not damaged, the malware classifier has a high success rate of deception, and it is impossible to create an adversarial sample and other problems, to achieve the effect of improving the damage of malicious software functions, improving the low success rate of deception, and meeting the actual needs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0026] In order to better illustrate the purpose and advantages of the present invention, the implementation of the method of the present invention will be further described in detail below in conjunction with examples.
[0027] The specific process is:
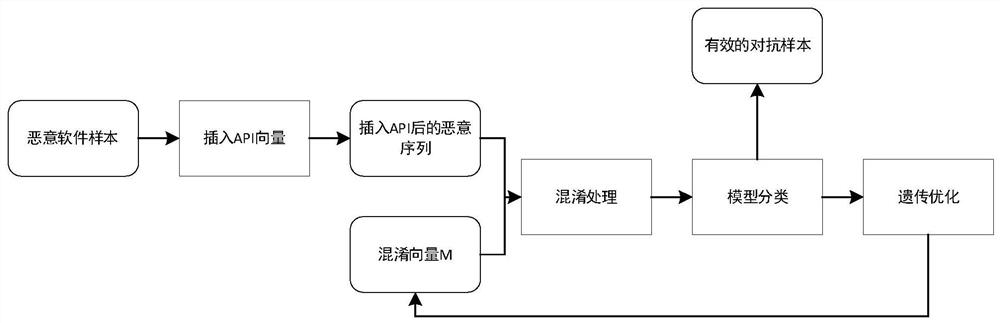
[0028] Step 1, insert irrelevant API vectors into the original API call sequence, and generate malware feature vector X according to the modified API call sequence P , by adding redundant codes to preliminarily realize the obfuscation of malware features and functions.
[0029] Step 1.1, determine an ordered set V, which contains all API functions that PE programs can call.
[0030] Step 1.2, let l be the length of the API call sequence used in the attack, X be the malicious API sequence with length l, divide X into w of length n j ,in n is w j The number of API calls in each w j Randomly select an API position i ∈ {1...n} in , and insert an API vector at position i: where ⊥ represents the concatenation operation, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com