Detection method, system and device for detecting abnormal behaviors of user and storage medium
A detection method and detection system technology, applied in the computer field, can solve the problems of bad social influence, leakage of sensitive information, false positives and false negatives, etc., so as to reduce the cost of manual detection, improve the detection efficiency, and achieve accurate and effective detection and identification. Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043]The various aspects of the present invention will be described in detail below with reference to the accompanying drawings and specific embodiments. Among them, well-known modules, units, and their connectors, links, communication, or operations are not shown or not described in detail. Also, the features, architectures, or functions described may be combined in any manner in one or more embodiments. Those skilled in the art will appreciate that various embodiments described below are intended to illustrate, rather than limiting the scope of the invention. It is also possible to understand that modules or units or processing methods in the respective embodiments shown in this article and the drawings may be combined and designed in a variety of different configurations.
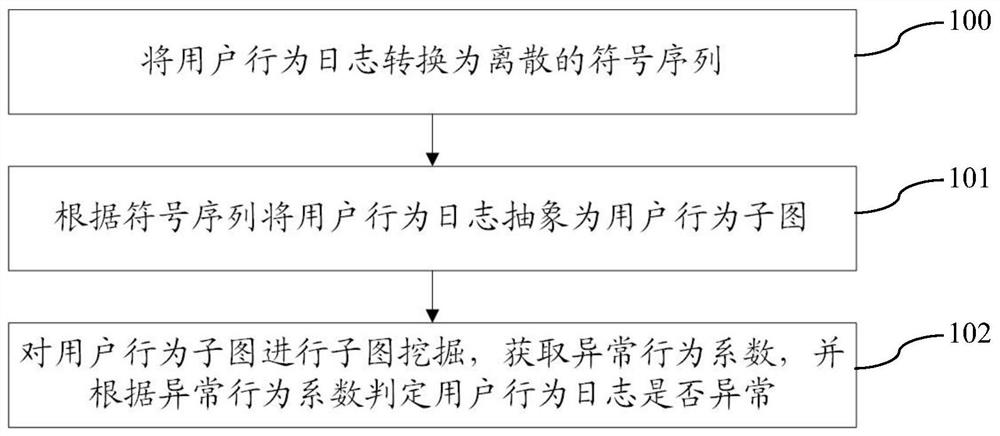
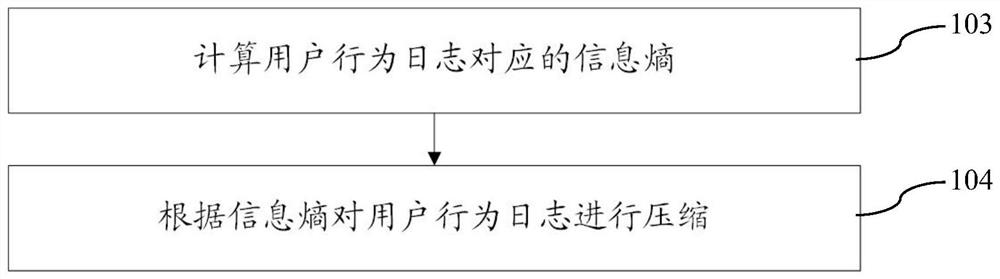
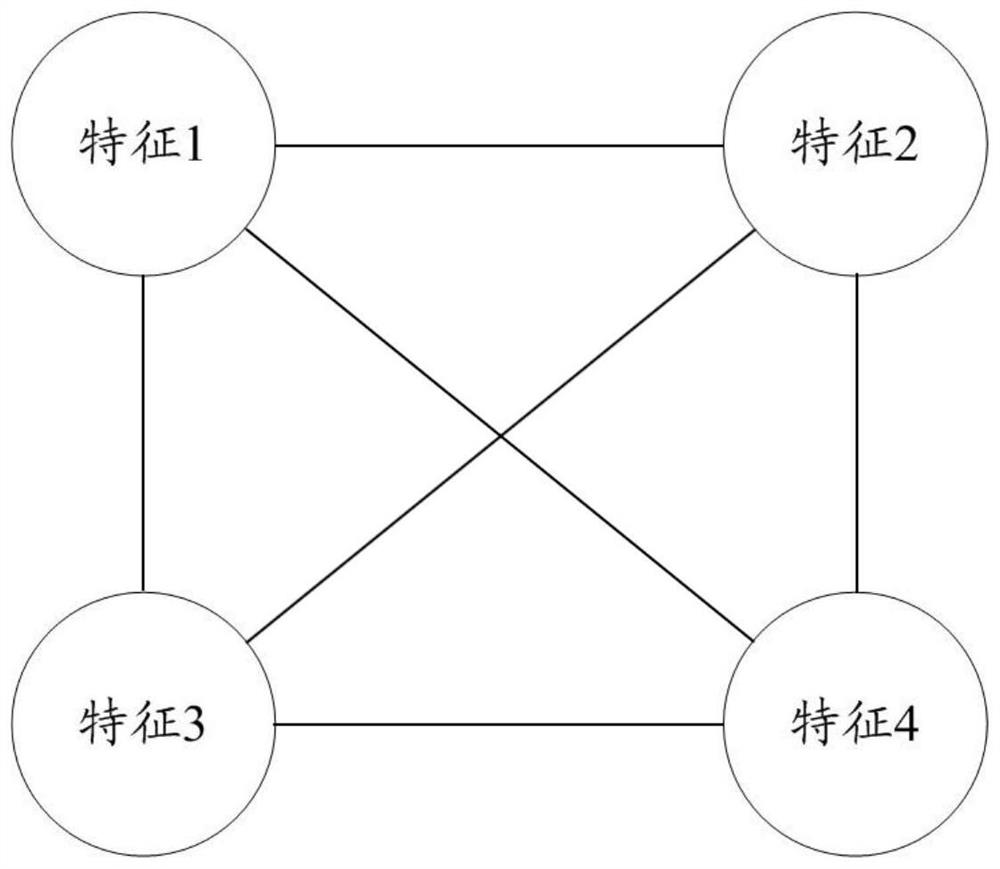
[0044] One embodiment of the present invention provides a method of detecting user abnormal behavior, such as figure 1 As shown in the embodiment of the invention, the method includes:
[0045] 100: Conver...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com