SSH man-in-the-middle attack detection system based on session similarity analysis
A technology of similarity analysis and attack detection, applied in transmission systems, electrical components, etc., can solve problems such as undetectable, unguaranteed server, abnormal time interval, etc., to avoid the impact of attack detection, improve detection efficiency, reduce effect of scale
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0036] Embodiments of the present invention will be described in detail below with reference to the accompanying drawings.
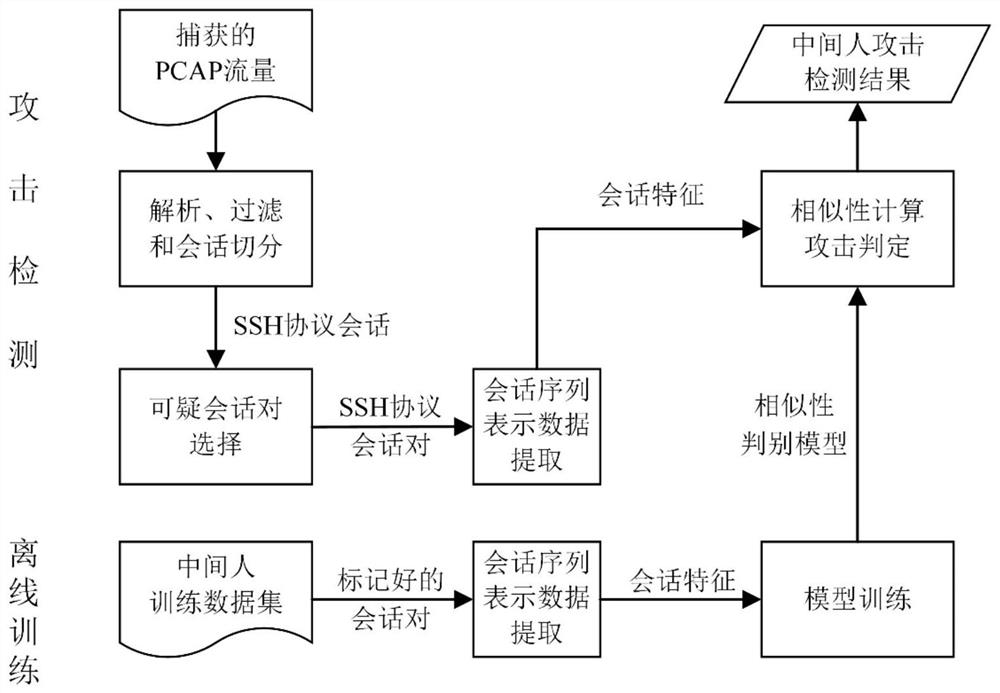
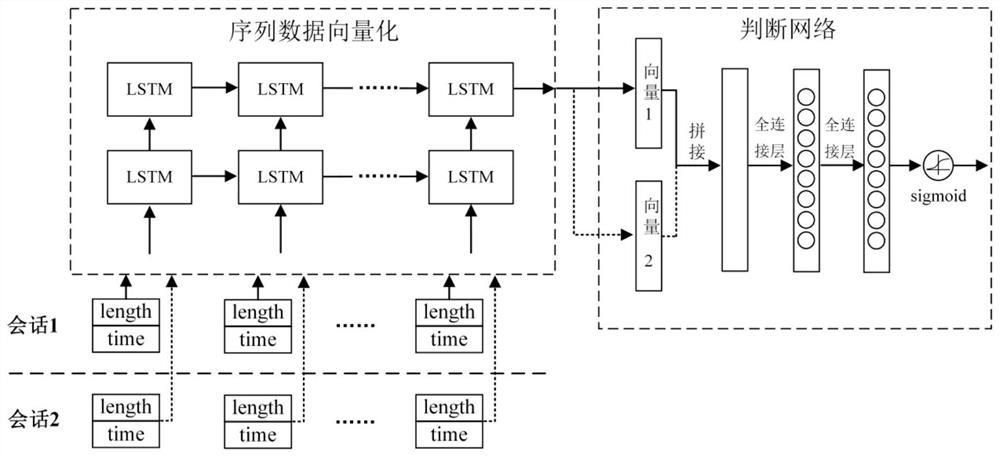
[0037] The invention is an SSH man-in-the-middle attack detection system based on session similarity analysis, which selects suspicious SSH session pairs from network traffic data, and then uses neural network technology to discriminate the similarity between encrypted session pairs, thereby completing the network The detection of man-in-the-middle attack events in traffic data includes: designing a SSH man-in-the-middle attack detection process framework based on session similarity analysis, which defines the components and detection steps of the detection scheme; designing an SSH suspicious session pair selection algorithm to effectively reduce The scale of session pairs that require similarity discrimination is identified; the sequence data representation of SSH sessions is proposed, which can effectively identify the similarity and uniqueness of SSH s...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com