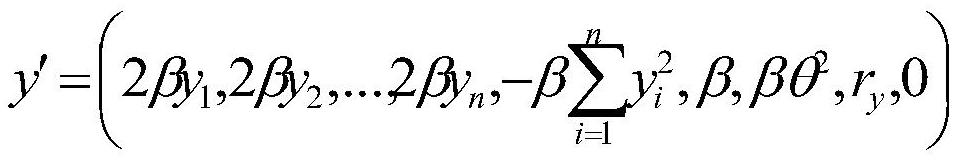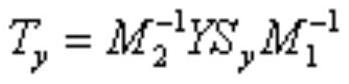Privacy-protected encrypted image retrieval method and system
A technology for encrypting images and protecting privacy, applied in the field of image processing, can solve the problem of privacy leakage of retrieval results and retrieval efficiency, and achieve the effect of simplifying the image feature calculation process, ensuring privacy security, and realizing secure retrieval.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0043] The present invention will be further described in detail below in conjunction with the accompanying drawings, which are explanations rather than limitations of the present invention.
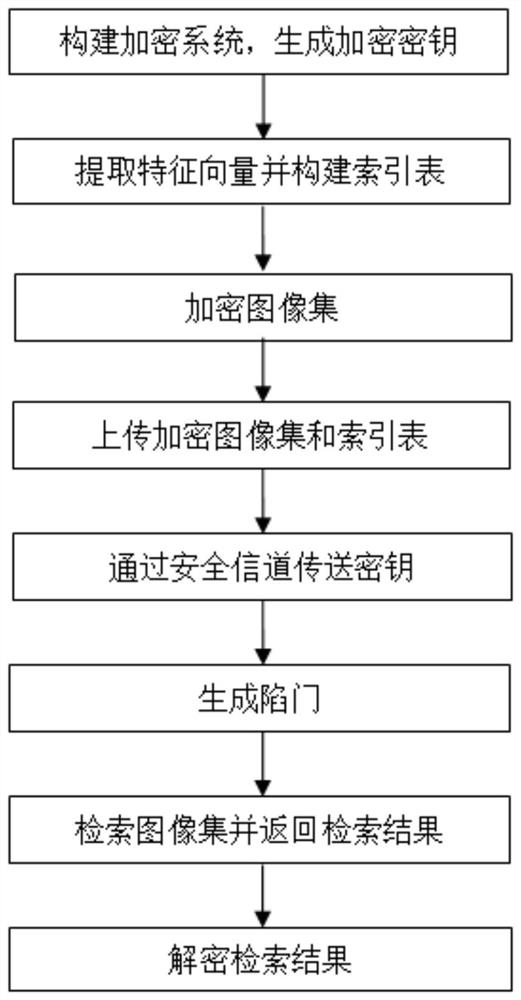
[0044] refer to figure 1 , a privacy-preserving encrypted image retrieval method, comprising the following steps:
[0045] Step 1, build an image encryption system and generate the key required for the encryption algorithm.
[0046] The key is generated using the key generation algorithm as follows:
[0047] Among them, M 1 ,M 2 Represents two invertible matrices randomly generated by the image owner, Respectively represent M 1 ,M 2 The inverse matrix of , π represents a random permutation function, which can randomly disrupt the order of elements in the vector, kmg represents the key required for image encryption using the chaotic mapping algorithm;
[0048] Step 2, extract the feature vector of the image and build the index table.
[0049] Step 1: The image owner extracts the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com