A network intrusion detection method for industrial control system based on improved suricata engine
A network intrusion detection and industrial control system technology, applied in the field of network security, can solve the problems that cannot meet the real-time transmission requirements of industrial control system network data, can not reduce the hardware system CPU usage, detection speed and memory consumption defects, etc., to speed up Matching processing speed, meeting real-time detection requirements, and avoiding the effect of decision-making lag
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0024] Specific examples of the present invention are given below. The specific embodiments are only used to further describe the present invention in detail, and do not limit the protection scope of the claims of the present application.
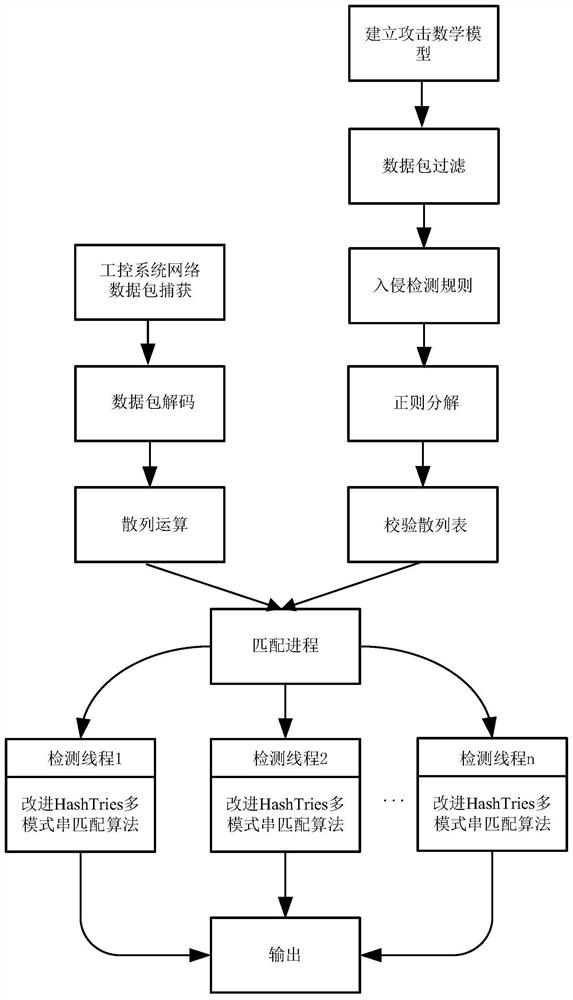
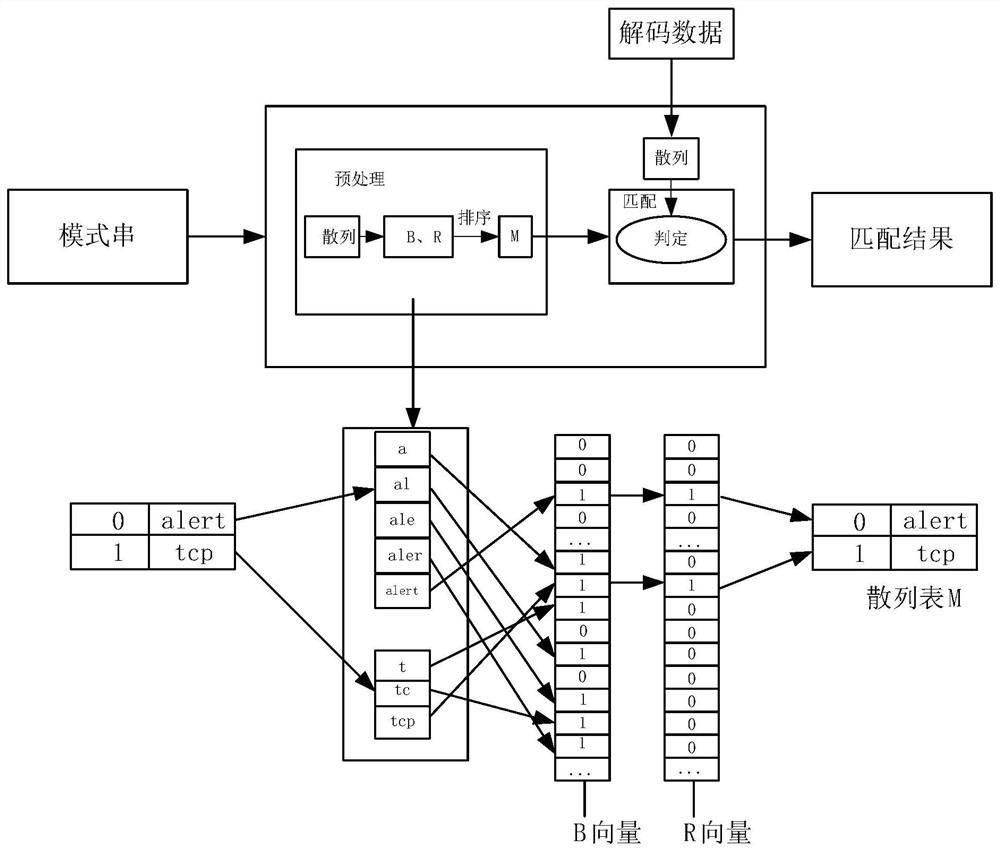
[0025] The present invention provides a kind of industrial control system network intrusion detection method based on improved Suricata engine (method for short, refer to figure 1 ), characterized in that the method comprises the following steps:
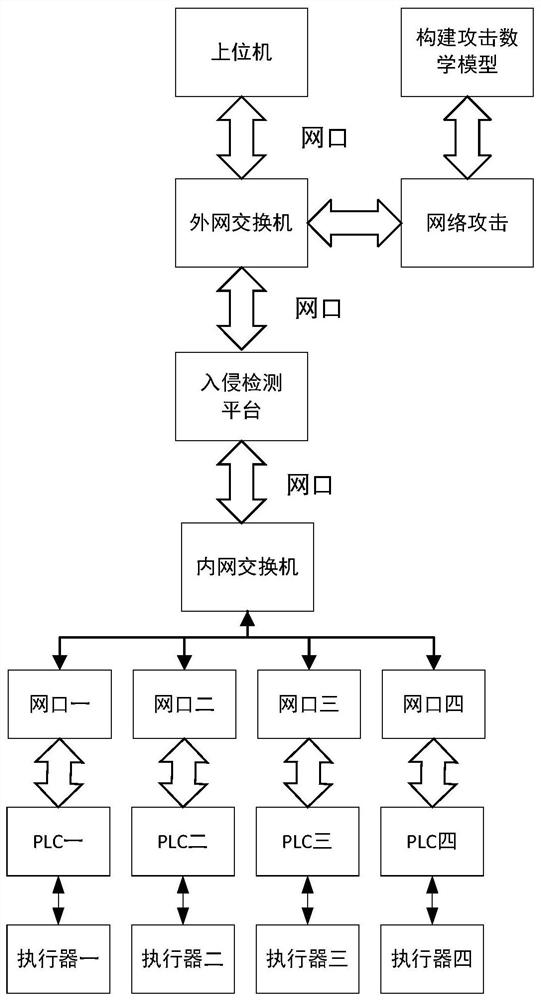
[0026] Step 1. Establish an attack mathematical model for the network attacks that can be carried out in the network environment of the industrial control system;
[0027] Preferably, in step 1, the network attack includes a tampering attack, a replay attack, an injection attack and a denial of service attack; use Attack(pl(i)) to describe the means of the network attack uniformly:
[0028]
[0029] In formula (1), pl(i) is the message at time i, sender represents the sender of the message i...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com