A blockchain-based cloud storage data integrity detection method
A technology of data integrity and detection methods, applied in the field of cloud storage, can solve problems such as lack of trust between cloud service providers and users, and achieve the effects of ensuring transparency and open auditing, ensuring correctness and effectiveness, and reducing computing difficulty
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
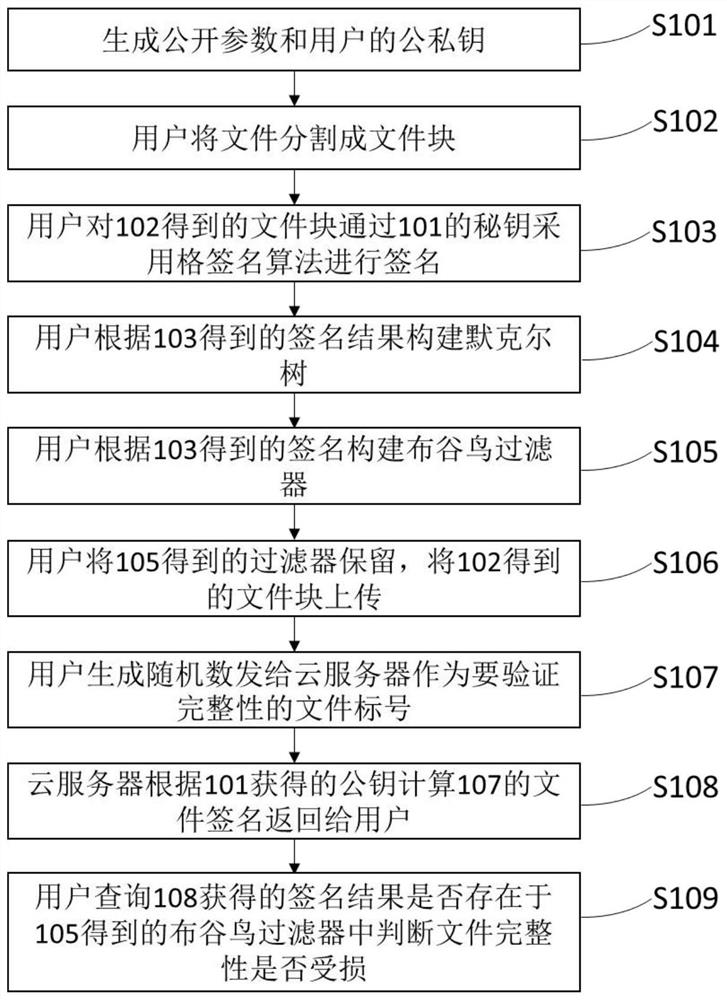
[0042] The present invention provides a blockchain-based cloud storage data integrity verification method, the process of which is as follows figure 1 As shown, it mainly includes:
[0043] S101: Generate system public parameters and user public and private keys.
[0044] Specifically, first generate public parameters P={q, m, n, σ, I n , M}, these public parameters are not confidential, and are the basic data required for other subsequent calculations.
[0045] Then generate a random matrix As the user's private key, generate the matrix As the user's public key, the matrix A needs to satisfy AS=A(-S)=qI n (mod 2q).
[0046] The private key is kept by the user locally, and the public key can be published to the blockchain together with the public parameters, or can be sent to the cloud server together with the file.
[0047] S102: The user divides the file into file blocks.
[0048] Specifically: the user divides the file into several file blocks with the same size b...
Embodiment 2
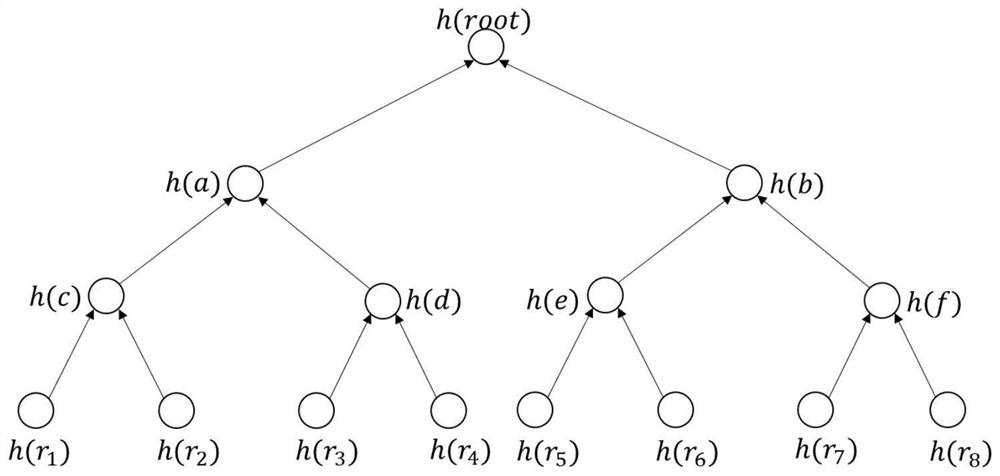
[0075] The present invention also provides a blockchain-based cloud storage data integrity verification system, such as Figure 4 As shown, the system mainly includes: users, cloud servers, and blockchain. in,
[0076] The user is the file owner, and the local storage space is limited, so the file is entrusted to be stored on the cloud server. There are many users in the system, so users can also interact with each other, such as downloading files publicized by other users, acting as a proxy for integrity verification requests of other users, etc.
[0077] Cloud servers, with large storage space and strong computing power, provide users with storage and computing services, enabling users to upload and download data anytime and anywhere. Similarly, there can be multiple cloud servers in the system, and when a user uploads a file, the file blocks divided from the same file should be uploaded to one cloud server in a unified manner.
[0078] Blockchain, a communication and sup...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com