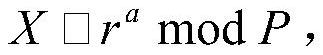Blockchain-based intelligent data rapid encryption transmission system
An encrypted transmission and data encryption technology, applied in the blockchain field, can solve problems such as low speed, being stolen, and existing risks, so as to improve security, reduce risks, and improve the effect of being easily stolen
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
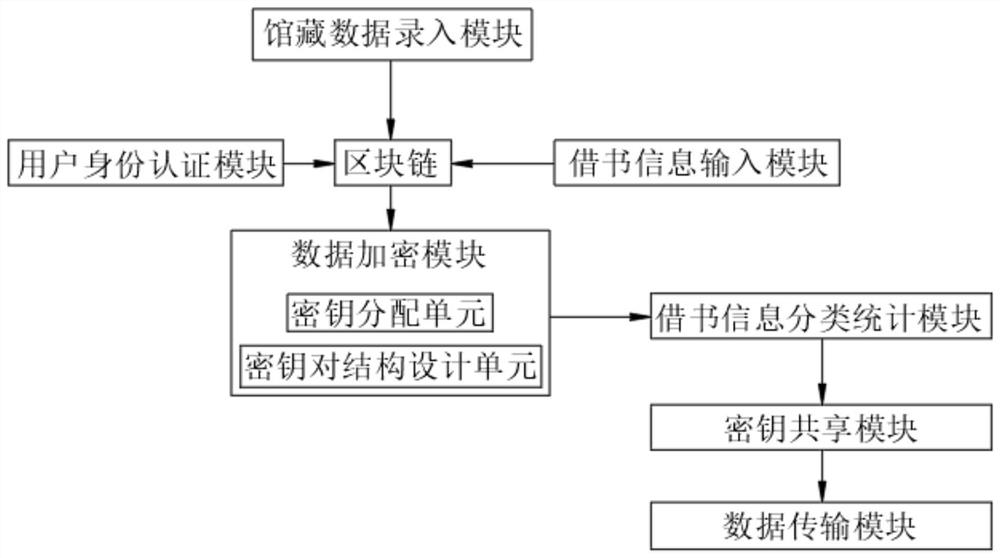
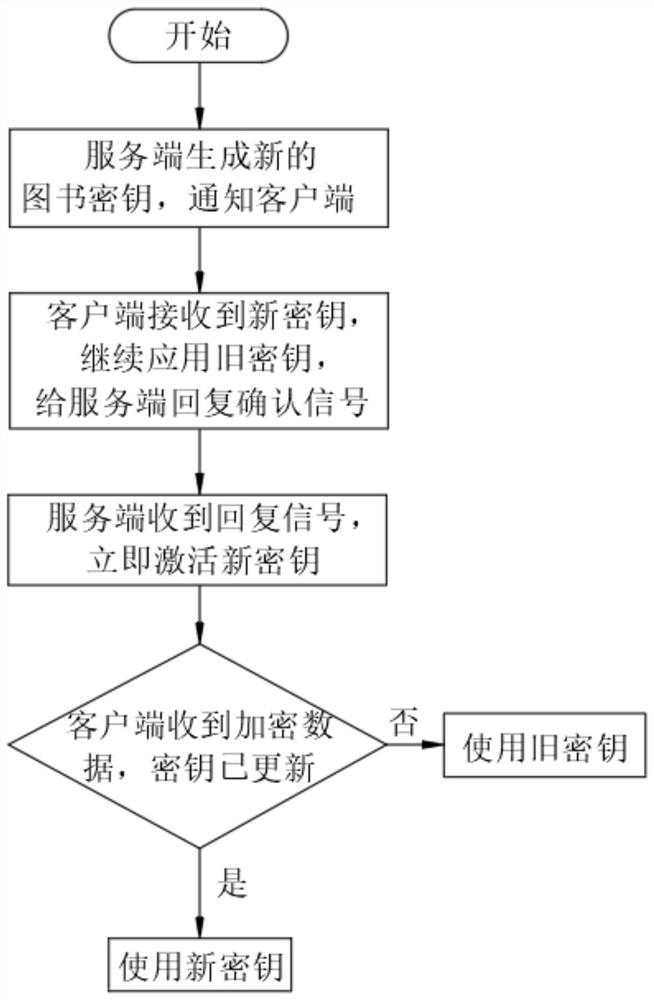
[0050] Embodiment 1: Randomly set a prime number P=4049, the original element r=3 of the prime number P module, and randomly set a number a=5 for the user terminal 1, through the formula Calculate and obtain the public key X=243 of a book in the library, randomly set a number b=6 for client 2, and use the formula Calculate and obtain the public key Y of another book of the same type = 729, client 1 and client 2 exchange key X and key Y through plaintext, according to the formula Calculate the secret key K of client 1 = 2239, according to the formula Calculate the secret key K'=K=2239 of client 2, even if P, r, X and Y are intercepted by the eavesdropper, it is difficult to deduce a and b mathematically, so the eavesdropper cannot obtain the secret key K and K', send the public key and secret key K to the authenticated user who borrows the corresponding book, the user obtains the book information by entering the key, and the user who borrows the same book at the same time ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com