Hidden attack detection method based on multi-scale sample entropy and Bayesian network
A Bayesian network and attack detection technology, applied in special data processing applications, complex mathematical operations, electrical components, etc., can solve the problems of industrial control system protocol complexity, computer security technology is difficult to implement and difficult to obtain, etc. The effect of improving the ability of transformation, better effect, and high computational efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0057] In order to make the technical scheme and design idea of the present invention clearer, we describe it in detail in conjunction with the accompanying drawings.
[0058] The research object is a repetitive machining process, and the sampling data is the X and Y axis parameter information, which is periodic and has natural disturbances.
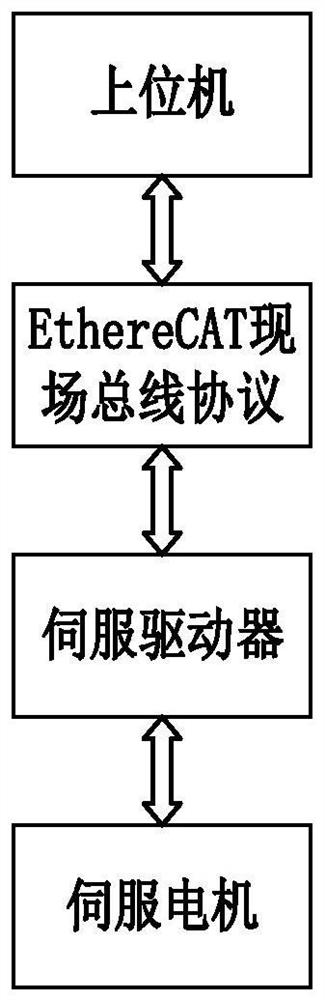
[0059] refer to figure 1 , most of the existing networked motion control systems are usually composed of a host computer, a lower computer and a servo drive system on the industrial site. The communication between the upper computer and the lower computer is realized through the EtherCAT fieldbus protocol.
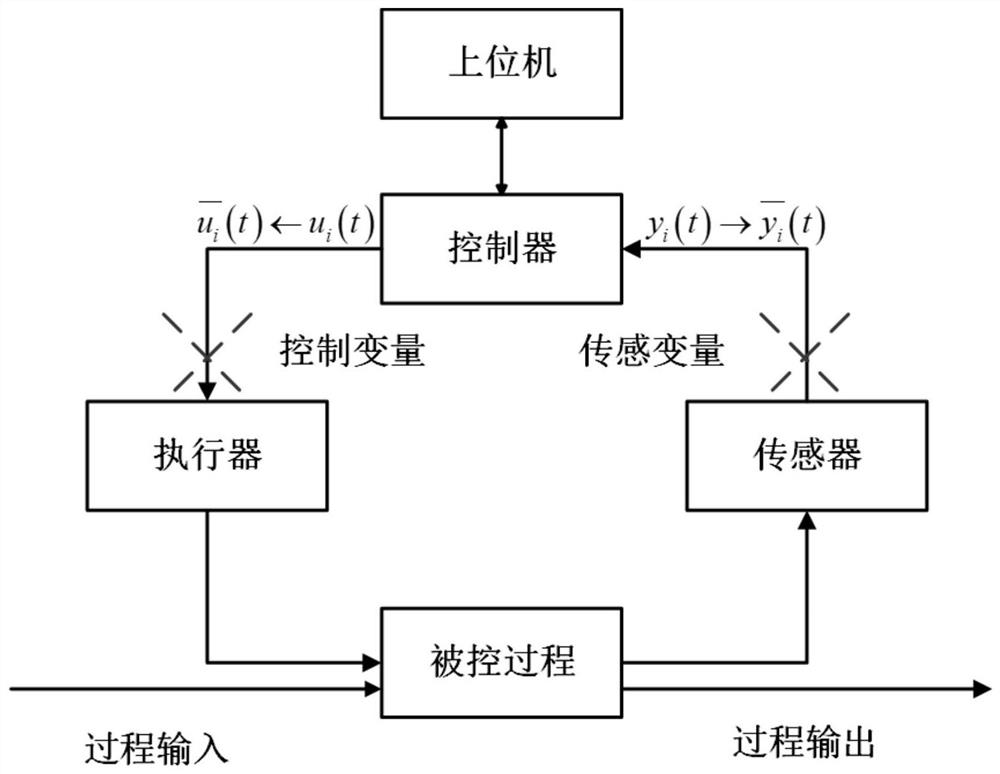
[0060] refer to figure 2 , the sinusoidal attack is a covert attack. When the networked motion control system is attacked, the output of the controller in the control system is injected with a sinusoidal signal of a certain amplitude and frequency. The control process variable always fluctuates slightly within the working range, ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com