Network malicious encrypted traffic identification method and system
A network traffic and traffic identification technology, applied in the field of encrypted traffic identification, can solve the problem of low identification accuracy and efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
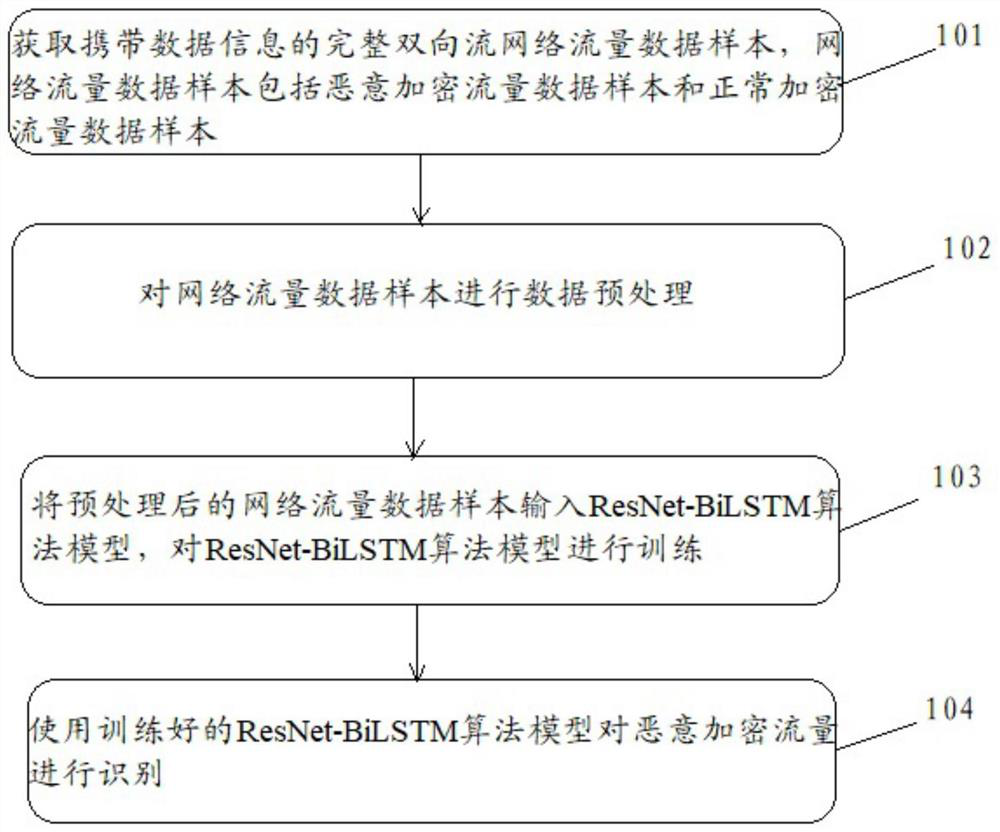
[0040] For ease of understanding, see figure 1 , the present application provides an embodiment of a network malicious encrypted traffic identification method, including:
[0041] Step 101. Obtain a complete two-way flow network traffic data sample carrying data information. The network traffic data sample includes a malicious encrypted traffic data sample and a normal encrypted traffic data sample.
[0042] It should be noted that, in the embodiment of the present application, network traffic data collection is first performed, and qualified traffic data samples are extracted. Among them, the traffic data samples that meet the conditions are: the total number of network traffic data packets is between 20 and 1000, carrying information, and it is a complete two-way flow. At the same time, the collected traffic data should be all encrypted traffic, and normal encrypted traffic data The number of samples ranges from 100,000 to 500,000, so that the number of samples is sufficien...
Embodiment 2
[0054] The present application provides an embodiment of a network malicious encrypted traffic identification system, including:
[0055] The acquiring unit is configured to acquire a complete bidirectional flow network traffic data sample carrying data information, and the network traffic data sample includes a malicious encrypted traffic data sample and a normal encrypted traffic data sample.
[0056] The preprocessing unit is configured to perform data preprocessing on the network traffic data samples.
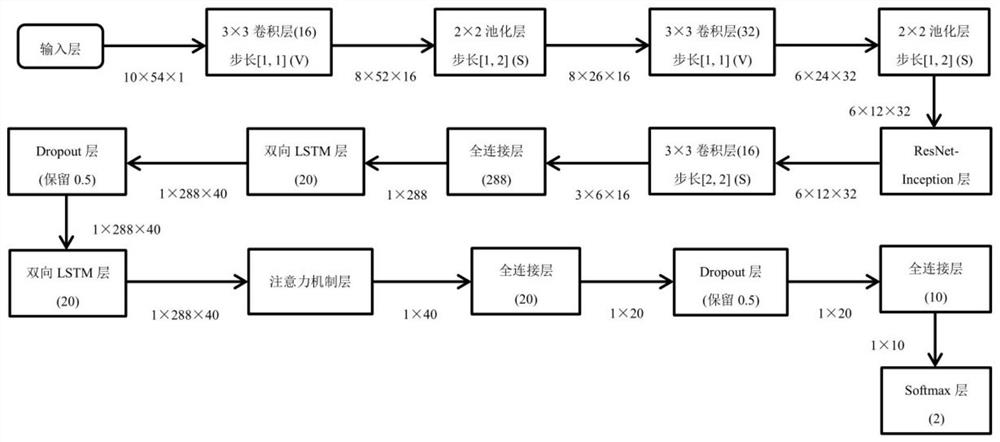
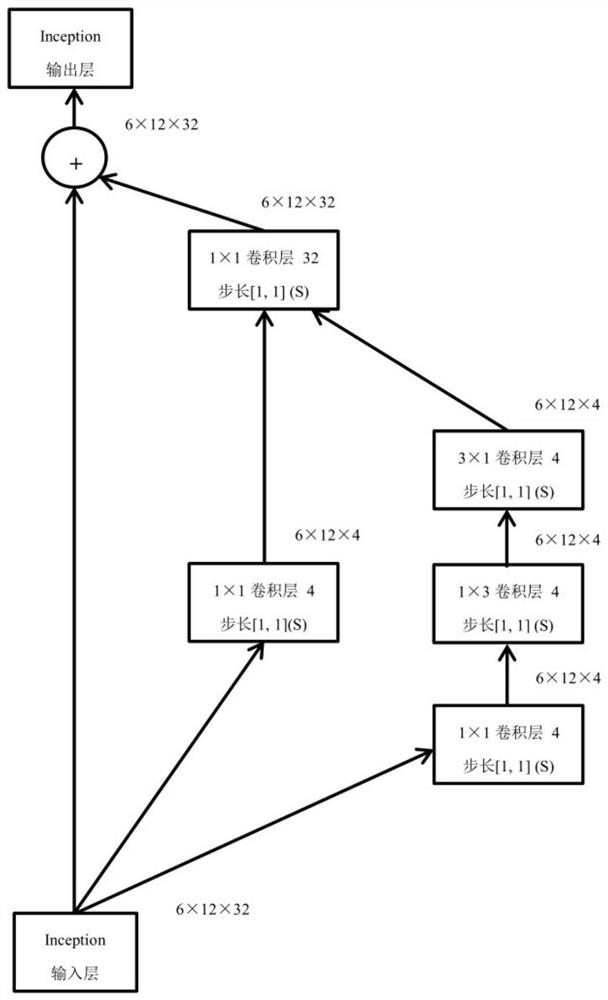
[0057] A modeling unit, configured to input the preprocessed network traffic data samples into the ResNet-BiLSTM algorithm model, and train the ResNet-BiLSTM algorithm model.
[0058] The identification unit is used to identify malicious encrypted traffic using the trained ResNet-BiLSTM algorithm model.
[0059] In the embodiment of the present application, network traffic data collection is first performed, and qualified traffic data samples are extracted. Among them, th...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com