Method and device for detecting result privacy of multi-party safety computing, equipment and medium
A technology of calculation results and detection methods, which is applied in the field of privacy detection of results of multi-party secure computing, and can solve problems such as affecting calculation efficiency and difficulty in direct detection by manual review.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
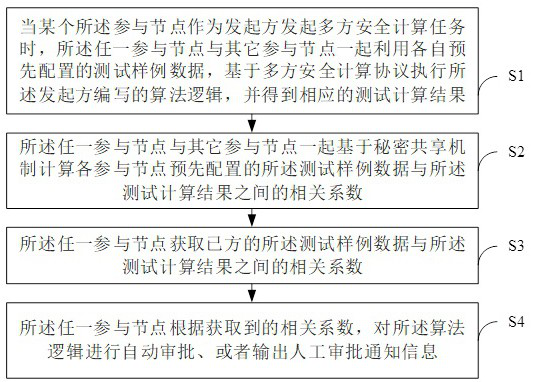
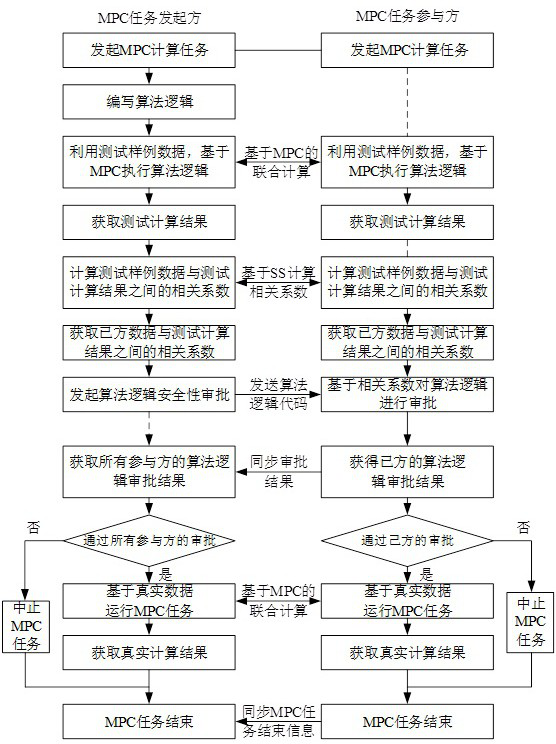
[0043] This embodiment provides a method for detecting the privacy of multi-party secure computing (MPC) results, which is applicable to any participating node among multiple participating nodes deployed in a distributed network. Each participating node can jointly Participate in multi-party secure computing. Such asfigure 1 and 2 As shown, the method specifically includes the following steps:
[0044] S1. When one of the participating nodes initiates a multi-party secure computing task as the initiator, any of the participating nodes and other participating nodes use their pre-configured test sample data to execute the initiator based on the multi-party secure computing protocol. Write the algorithm logic to get the test calculation results.
[0045] In this embodiment, each participating node is pre-configured with test sample data for result privacy detection, and the test sample data is data desensitized by ID.
[0046] When one of the participating nodes initiates a mu...
Embodiment 2
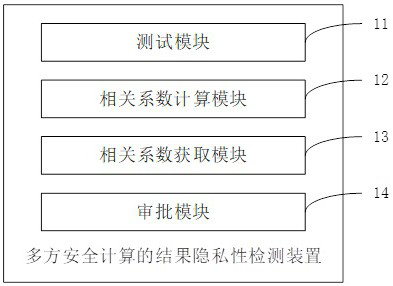
[0066] This embodiment provides a device for detecting the privacy of the results of multi-party secure computing, which is suitable for any participating node among multiple participating nodes deployed in a distributed network, such as image 3 As shown, the device includes:
[0067] The testing module 11 is used for when one of the participating nodes initiates a multi-party secure computing task as an initiator, together with other participating nodes, they use their pre-configured test sample data to execute the program written by the initiator based on the multi-party secure computing protocol. Algorithmic logic, and get the corresponding test calculation results;
[0068] The correlation coefficient calculation module 12 is used to calculate the correlation coefficient between the test sample data pre-configured by each participating node and the test calculation result based on a secret sharing mechanism with other participating nodes;
[0069] The correlation coeffic...
Embodiment 3
[0081]This embodiment provides an electronic device, which can be expressed in the form of a computing device (for example, it can be a server device), including a memory, a processor, and a computer program stored on the memory and operable on the processor, wherein the processor When the computer program is executed, the method for detecting the privacy of the result of the multi-party secure calculation provided in Embodiment 1 can be realized.
[0082] Figure 4 A schematic diagram of the hardware structure of this embodiment is shown, as Figure 4 As shown, the electronic device 9 specifically includes:
[0083] At least one processor 91, at least one memory 92, and a bus 93 for connecting different system components, including the processor 91 and the memory 92, wherein:
[0084] The bus 93 includes a data bus, an address bus, and a control bus.
[0085] The memory 92 includes a volatile memory, such as a random access memory (RAM) 921 and / or a cache memory 922 , and ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com