Mobile terminal APP security interaction system and method thereof
An interaction system and interaction method technology, applied in the field of mobile APP security interaction system, can solve the problems affecting the interaction security between mobile APP and business system, many page verification jump times, and low resource reuse rate, etc. The effect of access fluency, improved interaction security, and high resource reuse rate
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
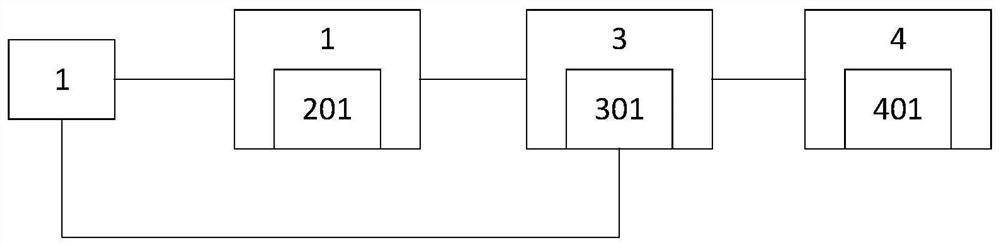
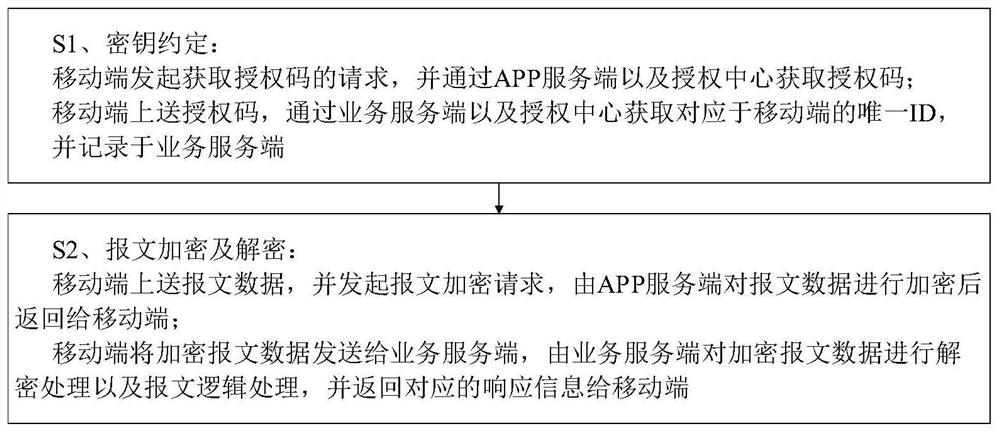
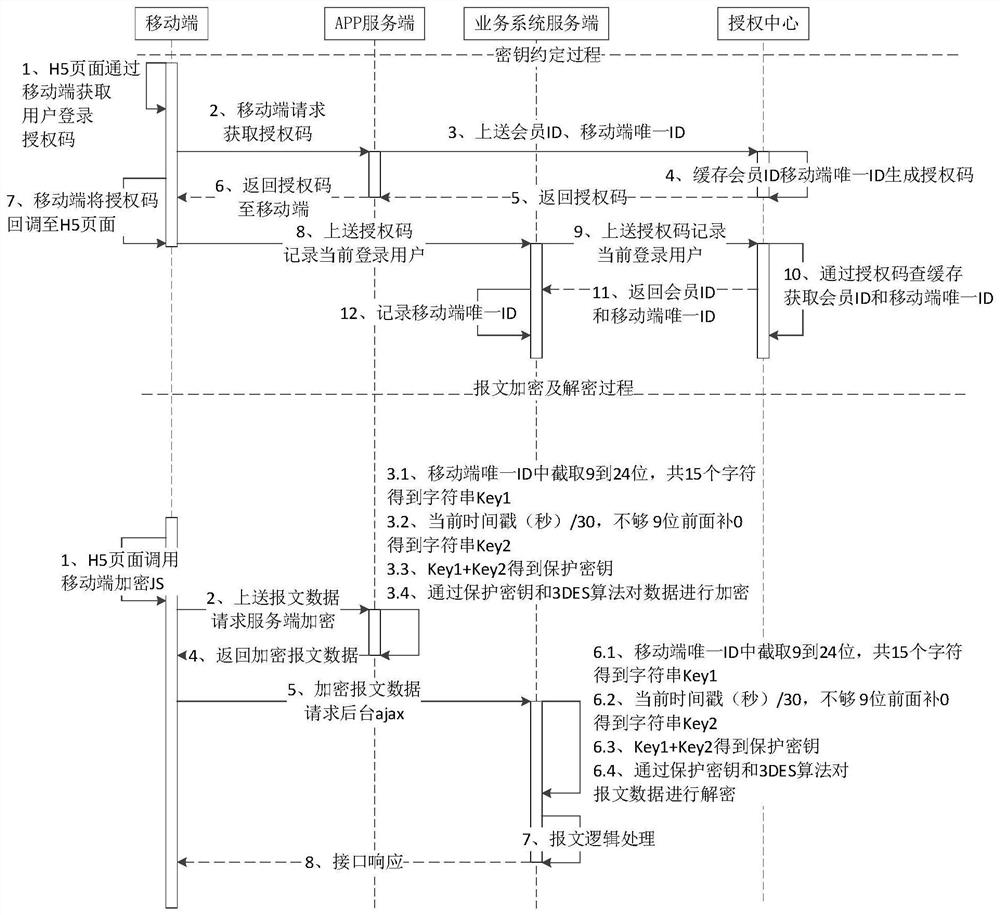
[0039] Such as figure 1 As shown, a mobile terminal APP security interaction system includes a mobile terminal 1, an APP server terminal 2, a business server terminal 3 and an authorization center 4 which are sequentially connected in a closed loop. The mobile terminal 1 is also directly connected to the business server terminal 3, and the mobile terminal 1 Terminal 1, APP server 2, business server 3 and authorization center 4 realize the key agreement process through data interaction, and mobile terminal 1, APP server 2 and business server 3 realize message encryption and decryption through data interaction process, wherein the mobile terminal 1 is embedded with an H5 page;
[0040] The APP server 2 is used to encrypt the message data sent by the mobile terminal 1, and the APP server 2 is provided with an encryption unit 201 for encrypting the message data;
[0041] The business server 3 records the unique ID of the mobile terminal corresponding to the mobile terminal 1. The...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com