Malicious code family classification method based on fuzzy assembly instruction sequence
A technology of compiling instructions and malicious codes, applied in neural learning methods, biological neural network models, instruments, etc., can solve problems such as inaccurate classification results and poor robustness, and achieve enhanced characterization capabilities, high accuracy, and low time cost Effect
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
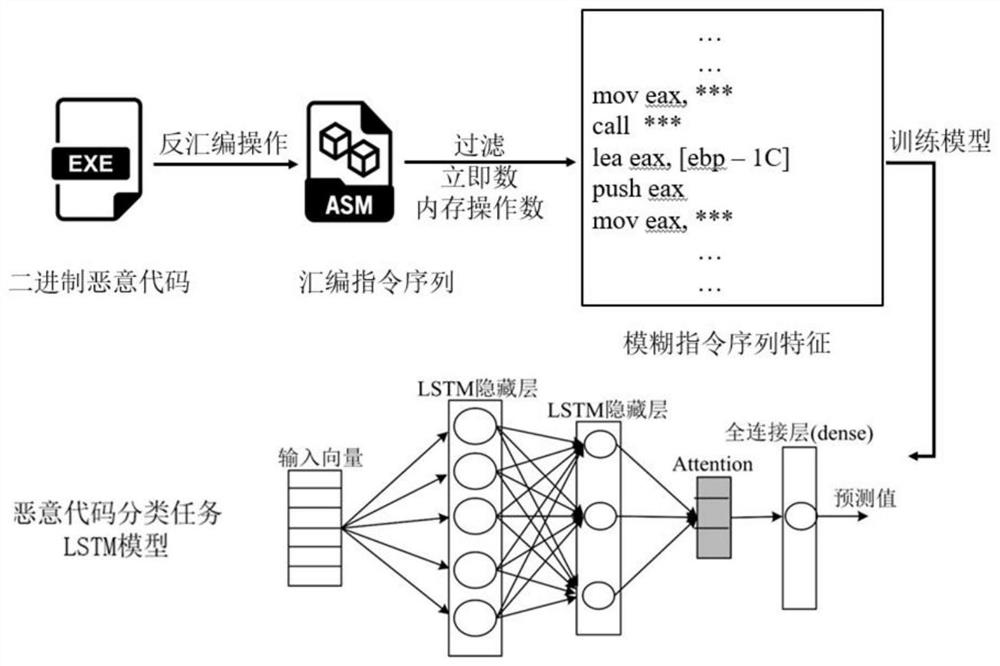
[0030] In the present invention, the immediate data and the constant memory address type operand filtered from the precise assembly instruction are as figure 2 shown.
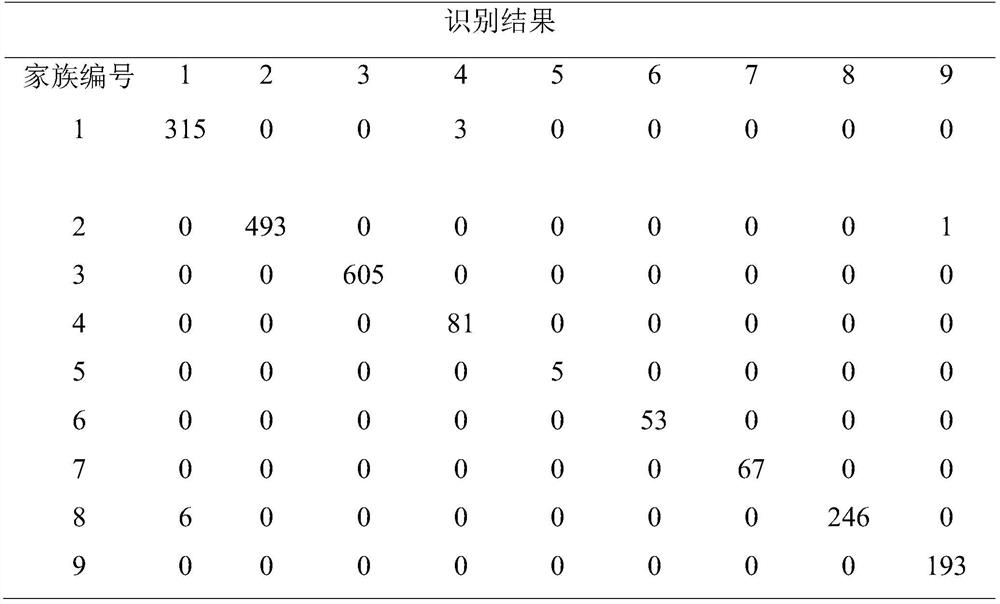
[0031] In order to test the malicious code results of the present invention, the "BIG 2015" standard data set was selected to verify the performance of the classification model trained by the present invention. The experimental results are shown in Table 2. The classification model generated by the present invention can accurately identify 96% of malicious codes. To a certain extent, the classification performance of polymorphic variant malicious code is improved.
[0032] Table 2 Classification and recognition results of malicious code families based on fuzzy assembly instruction sequences
[0033]
PUM
 Login to view more
Login to view more Abstract
Description
Claims
Application Information
 Login to view more
Login to view more - R&D Engineer
- R&D Manager
- IP Professional
- Industry Leading Data Capabilities
- Powerful AI technology
- Patent DNA Extraction
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic.
© 2024 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap