Method and device for recognizing abnormal operation in database
A database and abnormal technology, applied in the computer field, can solve problems such as system failures and privacy data leakage, achieve high accuracy and reduce labor costs
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0048] The solutions provided in this specification will be described below in conjunction with the accompanying drawings.
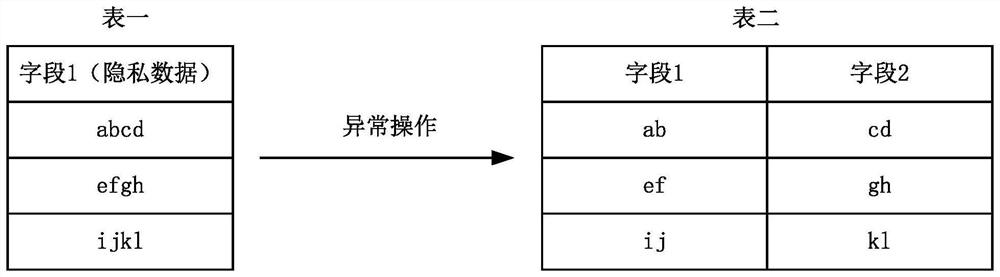
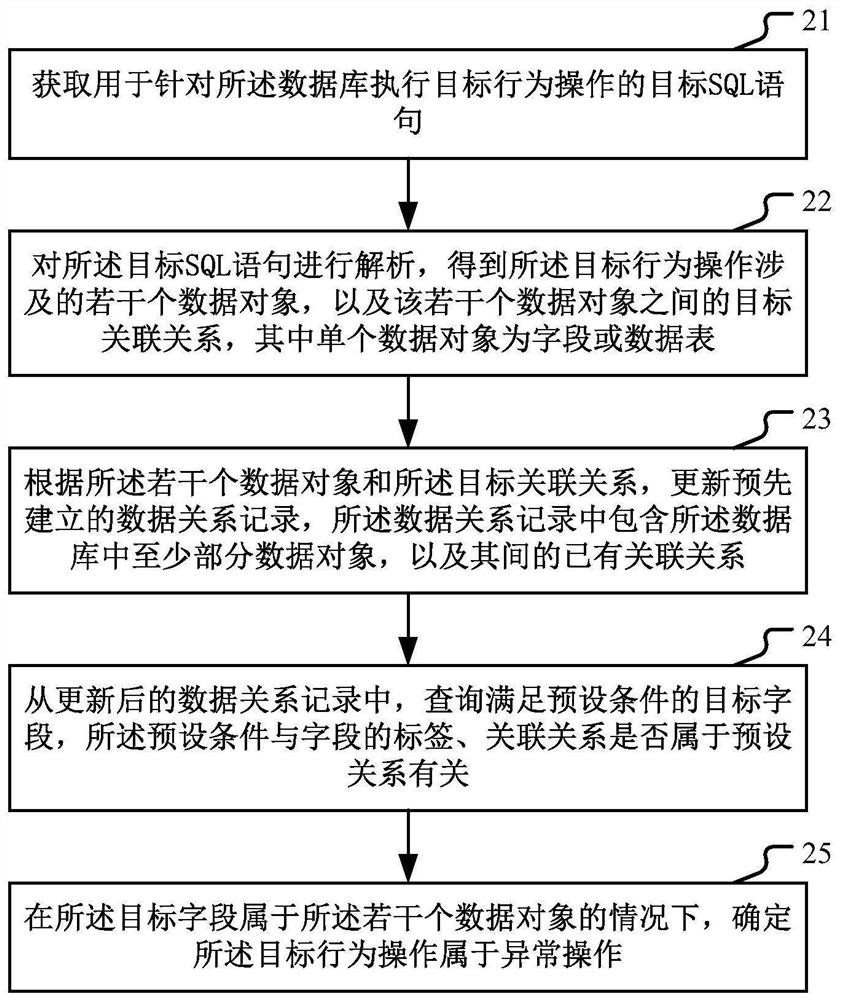
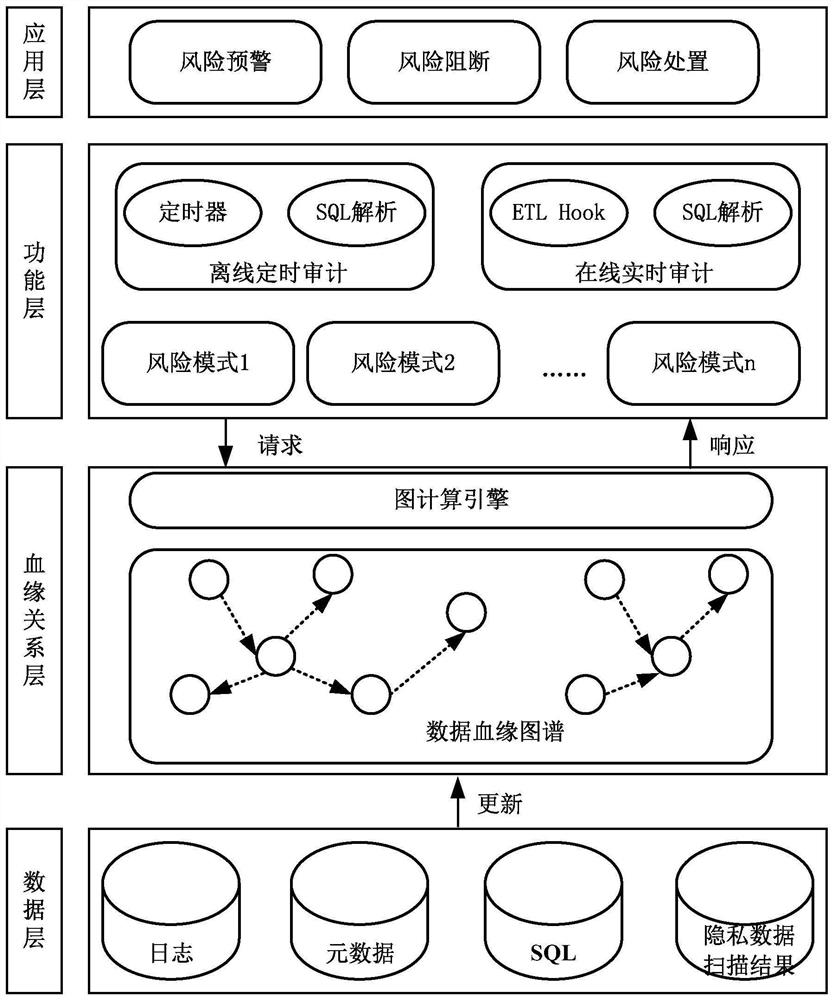
[0049] figure 1 It is a schematic diagram of an implementation scenario of an embodiment disclosed in this specification. This implementation scenario involves identifying abnormal operations in the database. The database includes multiple data tables, and each data table includes multiple fields. Each field corresponds to a label whether it belongs to private data, where the fields correspond to columns. Abnormal operations are also known as risky behaviors, which can easily lead to consequences such as privacy data leakage and system failures, usually including bypassing the platform desensitization mechanism to collect private data, illegal credentialing, etc. refer to figure 1 , Table 1 is the original data table in the database. Field 1 included in Table 1 belongs to private data. The operation for the database is to create Table 2. Field 1 in Tab...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com