Terminal security legality verification method
A verification method and terminal security technology, applied in the field of ad hoc networks, to achieve the effects of high work efficiency, simple algorithm, and improved compatibility
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment Construction
[0016] The present invention will be described in further detail below with reference to the drawings and examples, but the present invention is not limited to the following embodiments.
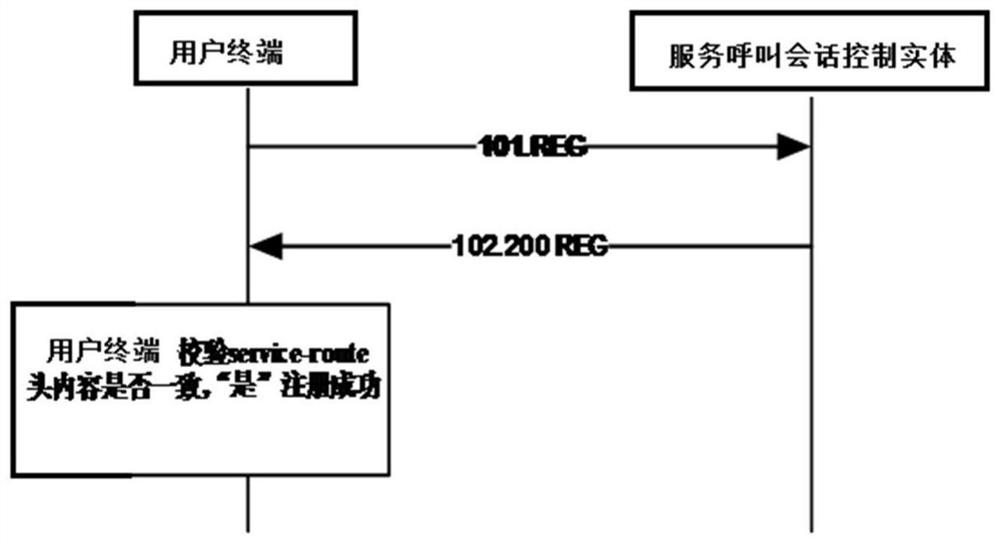
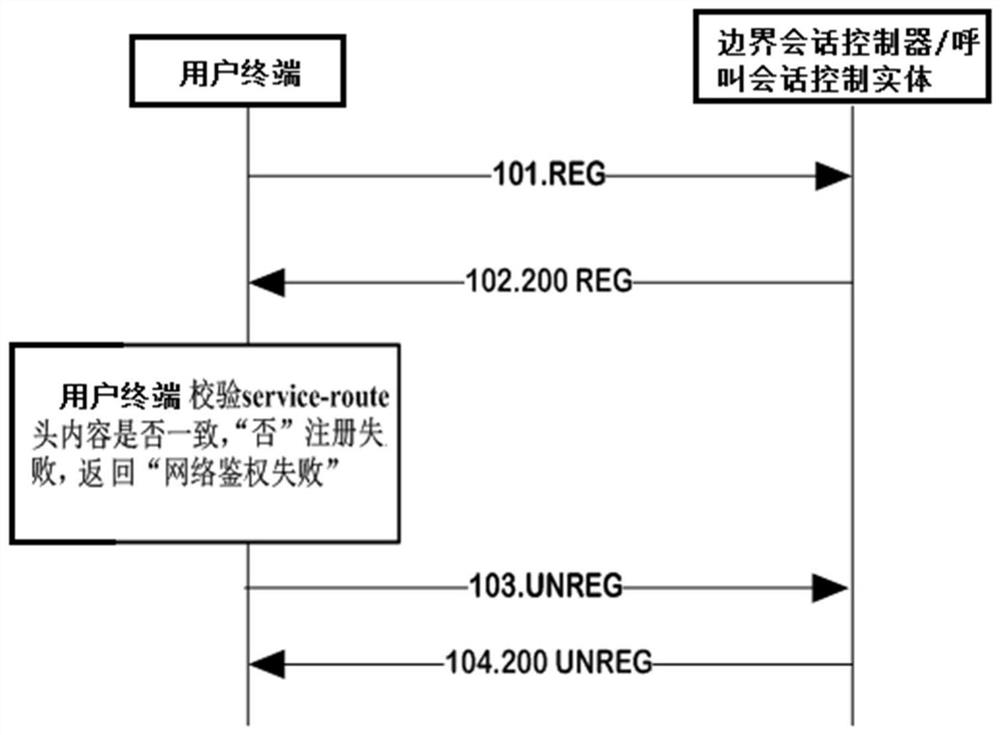
[0017] exist figure 1 Among them, a method for verifying the validity of terminal security in this embodiment consists of the following steps:
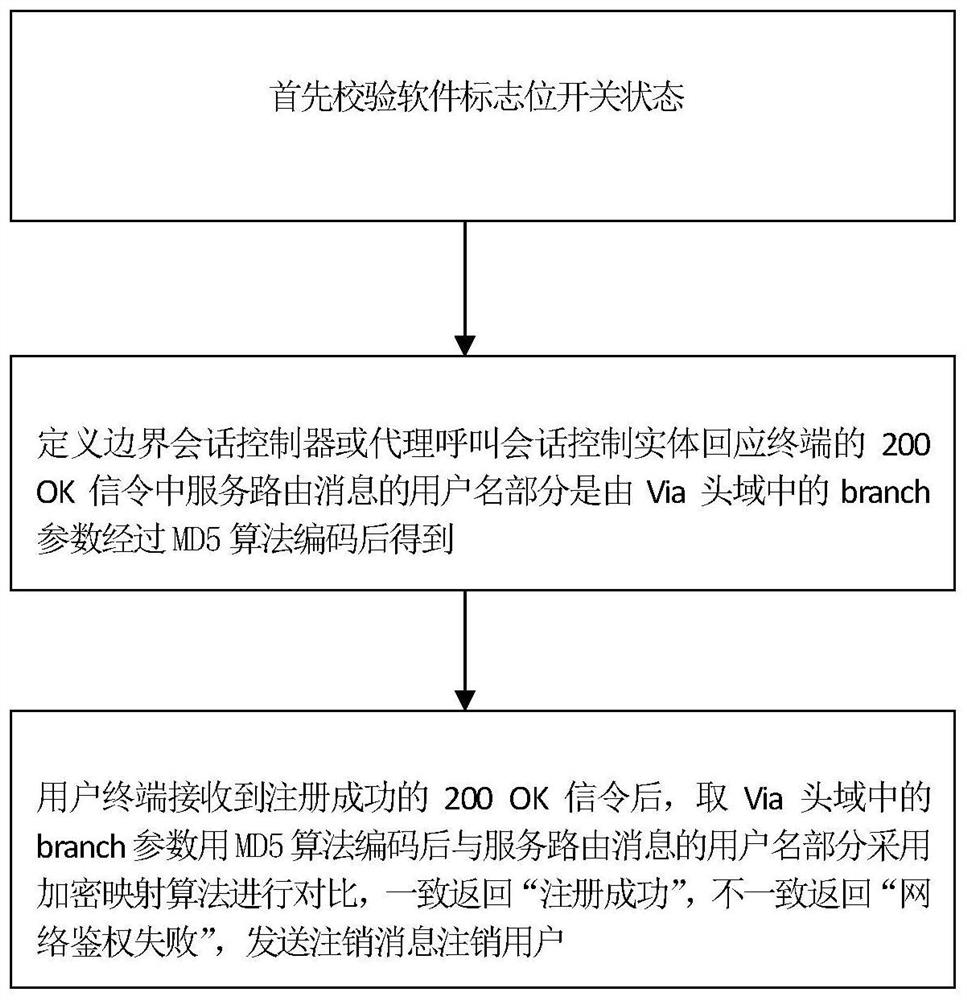
[0018] S1. Verify the status of the software flag switch
[0019] The operation of step S2 is performed in the "on" state, and the operation in "off" state is performed according to the normal process stipulated in the international agreement;
[0020] S2. Define the user name part of the service routing message in the 200 OK signaling that the boundary session controller or proxy call session control entity responds to the user terminal is obtained by encoding the branch parameter in the Via header field through the MD5 algorithm;
[0021] The realization of the content of the user name in the service routing message header in the 200 OK signalin...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com