A Deep Structure Pointer Analysis Optimization Method for Analyzing Source-Database Pattern Defect Detectors
A technology of pointer analysis and optimization method, applied in the direction of instrument, calculation, reverse engineering, etc., can solve the problems of narrowing the scope of influence, reducing the false and missing rate of code analysis results, and reducing the cost of manual auditing, so as to reduce the scope of influence and reduce labor costs. Audit costs and the effect of reducing false and false negative rates
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
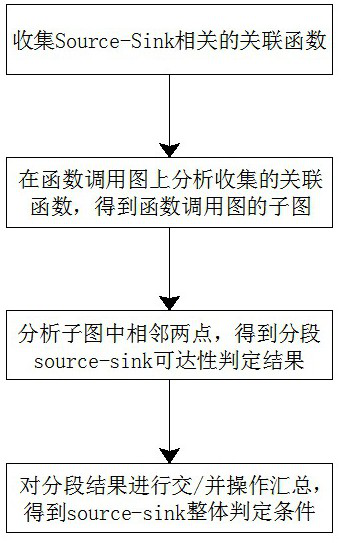
[0032] see figure 1 , 2 , 3, 4, the present embodiment provides a deep structure pointer analysis and optimization method for analyzing source library pattern defect detectors, including the following steps:
[0033] step one
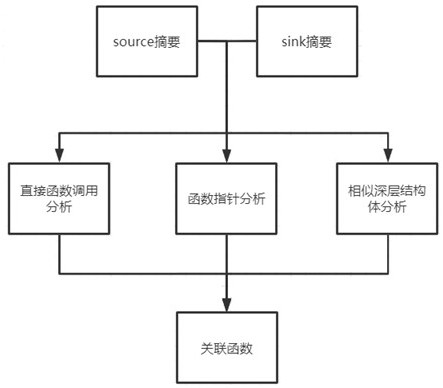
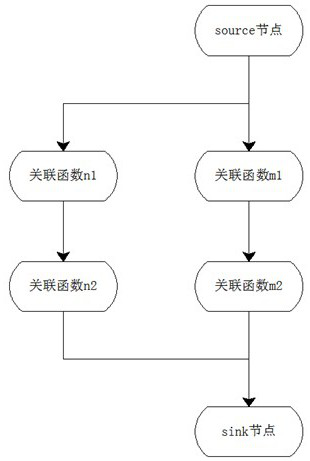
[0034] First construct the source summary and sink summary according to the Source-Sink judgment. The content of the source summary and the sink summary are consistent. Taking the source summary as an example, the source summary directly obtains the name of the function where the source is located and the names of the core variables involved, and then combines binding analysis and Alias analysis collects function names, aliases of core variable names and their locations, and then finds associated functions through direct function call analysis, function pointer analysis, and similar deep structure analysis based on the source summary and sink summary respectively. Each method collects The confidence of the correlation function is different, and then...
Embodiment 2
[0047] According to the description of CVE-2021-29649, analyze the kernel code of linux-5.11.1 version. This CVE example has a clear definition of Source-Sink, and the relationship is relatively complicated. According to the CVE description and git modification records, the defect here is an actual memory leak It will be corrected by developers after it occurs, and it will be corrected after scanning by non-static analysis tools. According to the present invention, CVE-2021-29649 is analyzed as follows:
[0048] 1. Find the paired source-sink definition [umd_info->tgid = get_pid(task_tgid(current));] and [put_pid(umd_info->tgid);] in linux-5.11.1\kernel\usermode_driver.c;
[0049] 2. Associate the Source-Sink of umd_info, and find that it involves global variables, deep pointers and multi-level function pointer calls at the same time, and it is difficult to directly associate data streams;
[0050] 3. Analyze the Source function umd_setup:
[0051] 3.1. Directly analyze the c...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com