NFC label data writing method and terminal
A tag data and terminal technology, which is applied to the NFC tag data writing method and the terminal field, can solve problems such as low efficiency, tag failure, and affecting the efficiency of batch reading and writing of NFC card readers, so as to shorten the writing cycle, The effect of improving writing efficiency
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
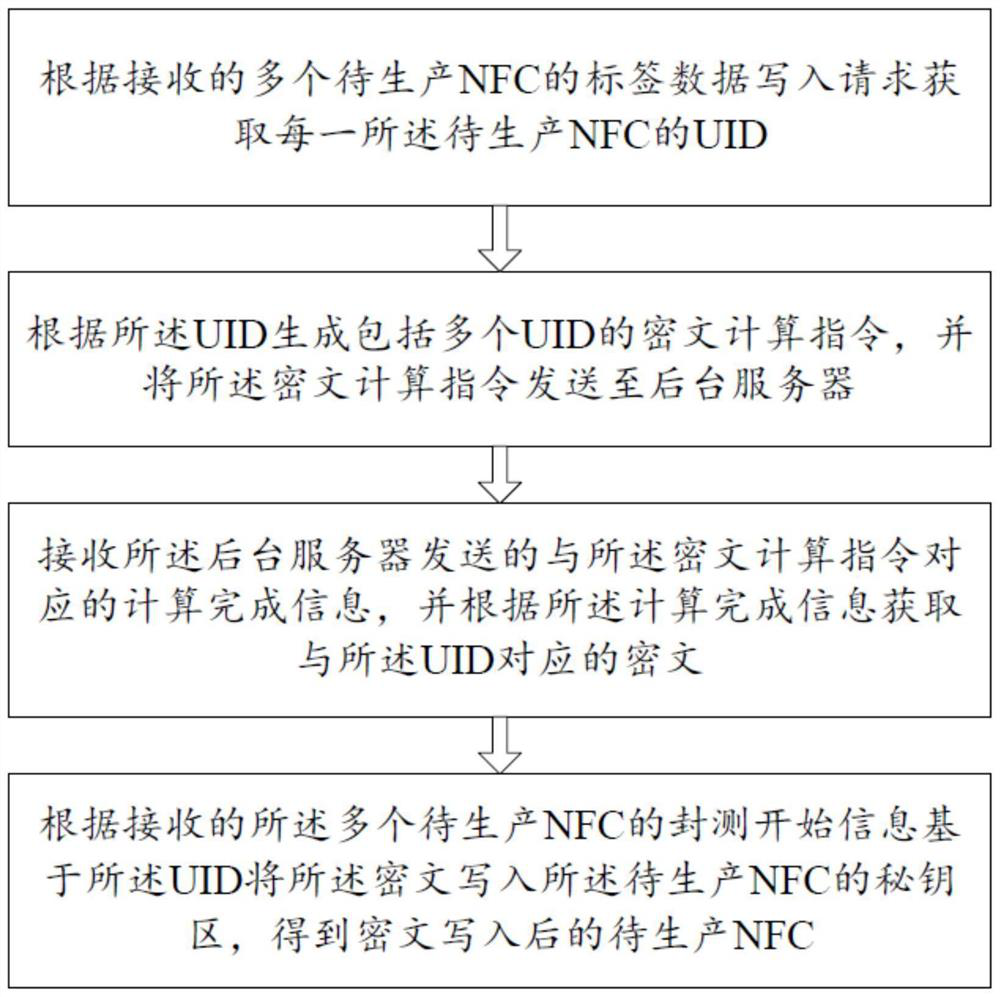
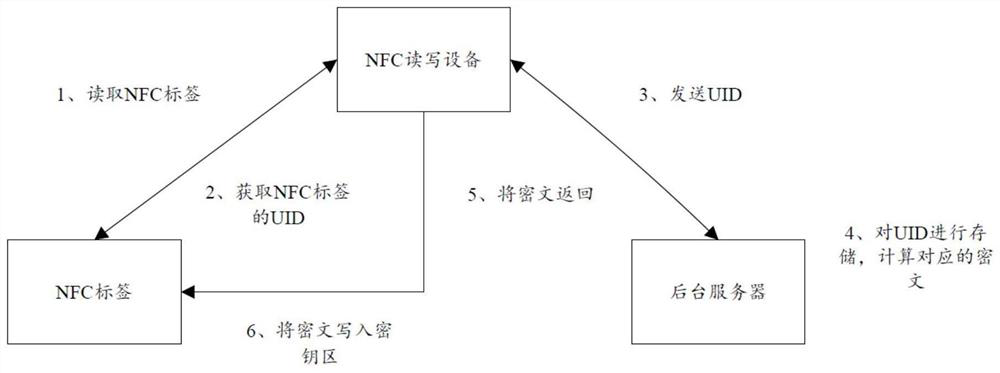
[0095] Please refer to figure 1 , 7 -8, a kind of writing method of NFC label data of the present embodiment, comprises:
[0096] S1. Obtain the UID of each NFC to be produced according to the received tag data writing requests of multiple NFCs to be produced;
[0097] Specifically, such as Figure 7 , 8 As shown, in the chip processing stage, the UID of each NFC to be produced is obtained according to the received tag data write request of multiple NFCs to be produced;
[0098] Or, customize the UIDs of multiple NFCs to be produced in advance for each batch, and directly obtain the customized UIDs of each NFC to be produced according to the received tag data writing request of multiple NFCs to be produced;
[0099] Or, in the test stage after chip processing, obtain the UID of each NFC to be produced according to the received tag data writing requests of multiple NFCs to be produced;
[0100] S2. Generate a ciphertext calculation instruction including multiple UIDs acco...
Embodiment 2
[0110] Please refer to Figure 7-9 , on the basis of Embodiment 1, this embodiment further defines how to obtain the ciphertext corresponding to the UID and write the ciphertext into the key area, specifically:
[0111] The calculation completion information includes encrypted ciphertext corresponding to the UID;
[0112] The acquiring the ciphertext corresponding to the UID according to the calculation completion information includes:
[0113] Such as Figure 7 , 8 As shown, obtain the preset decryption algorithm;
[0114] Wherein, the preset decryption algorithm corresponds to the first preset encryption algorithm;
[0115] Decrypt the encrypted ciphertext corresponding to the UID according to the preset decryption algorithm to obtain the ciphertext corresponding to the UID;
[0116] Writing the ciphertext into the key area of the NFC to be produced based on the UID according to the received packaging and testing start information of the plurality of NFCs to be produc...
Embodiment 3
[0123] Please refer to Figure 8 , this embodiment further defines how to verify the ciphertext on the basis of Embodiment 1 or Embodiment 2, specifically:
[0124] S5. Verifying the ciphertext of the secret key area of the NFC to be produced after the ciphertext is written, and obtaining a verification result;
[0125] Specifically, read the ciphertext of the secret key area of the NFC to be produced after the ciphertext is written, and obtain the ciphertext to be verified;
[0126] Obtain the UID of the NFC to be produced after the ciphertext is written;
[0127] Judging whether the ciphertext to be verified is consistent with the ciphertext corresponding to the UID obtained according to the calculation completion information, if yes, the verification is successful, if not, the verification fails;
[0128] generating verification data according to the verification result;
[0129] Write the verification data into the storage area of the NFC to be produced after the ...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com