Security risk detection processing system and method thereof
A security risk and disposal system technology, which is applied in the field of network security risk detection and security protection, can solve the problems of protocol non-awareness, false positives, false positives, etc., and achieve the effect of ensuring normal operation, reducing impact, and improving accuracy
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
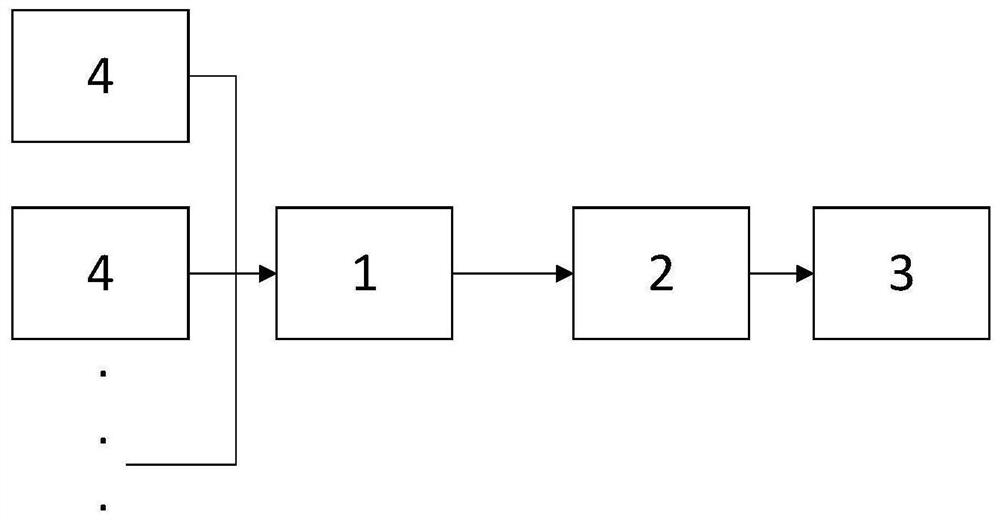
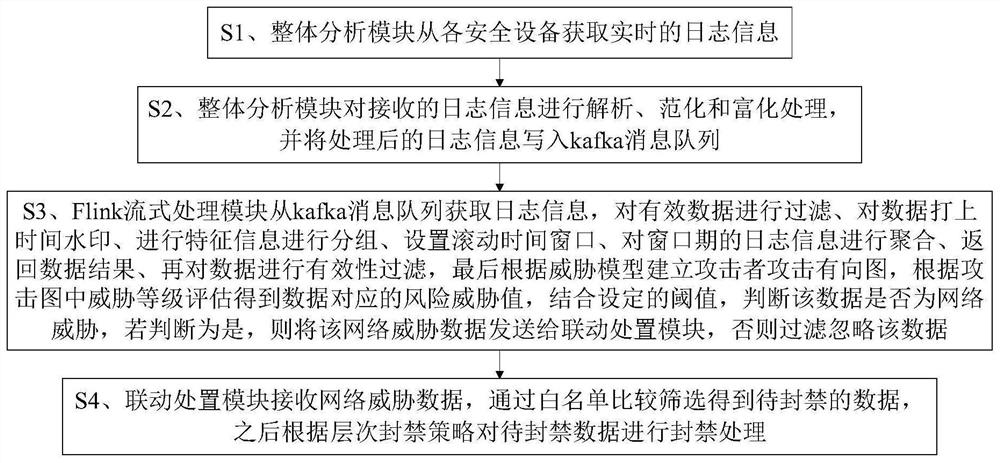
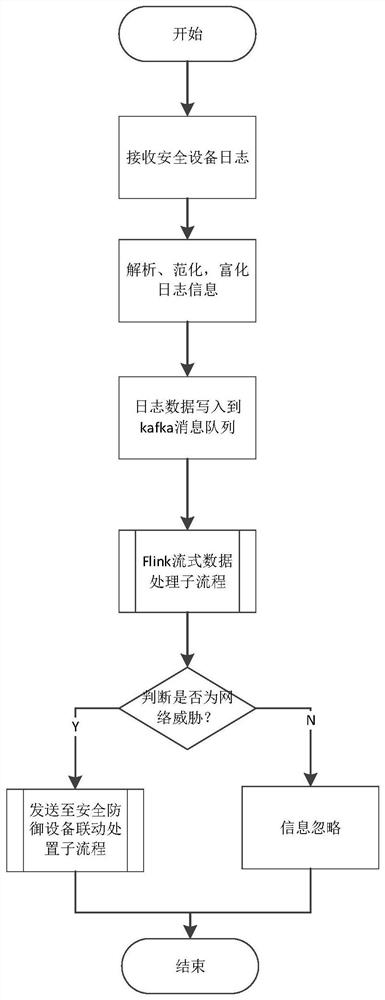
[0052] A security risk detection and disposal system, including an overall analysis module 1, a Flink stream processing module 2, and a linkage disposal module 3 connected in sequence, the overall analysis module 1 is respectively connected to multiple security devices 4, and is used to receive multiple security devices 4 The log information sent in real time, through processing the received log information, publishes the processed log information to the kafka message queue for consumption by other information consumers, and enters the Flink stream processing module 2 for data analysis. Specifically, The overall analysis module 1 includes an information processing unit, and the information processing unit is used to analyze, normalize and enrich the log information;
[0053]The Flink stream processing module 2 is used to analyze and judge whether the data is a network threat, and send the data judged to be a network threat to the linkage processing module 3 for processing. Spec...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com