Flow control method and device and computer readable storage medium
A technology for flow control and configuration data, applied in the field of data transmission, it can solve the problems of overrunning back-end systems or database services, low verification accuracy, downtime, etc., to meet the needs of business scenarios and improve flexibility.
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment 1
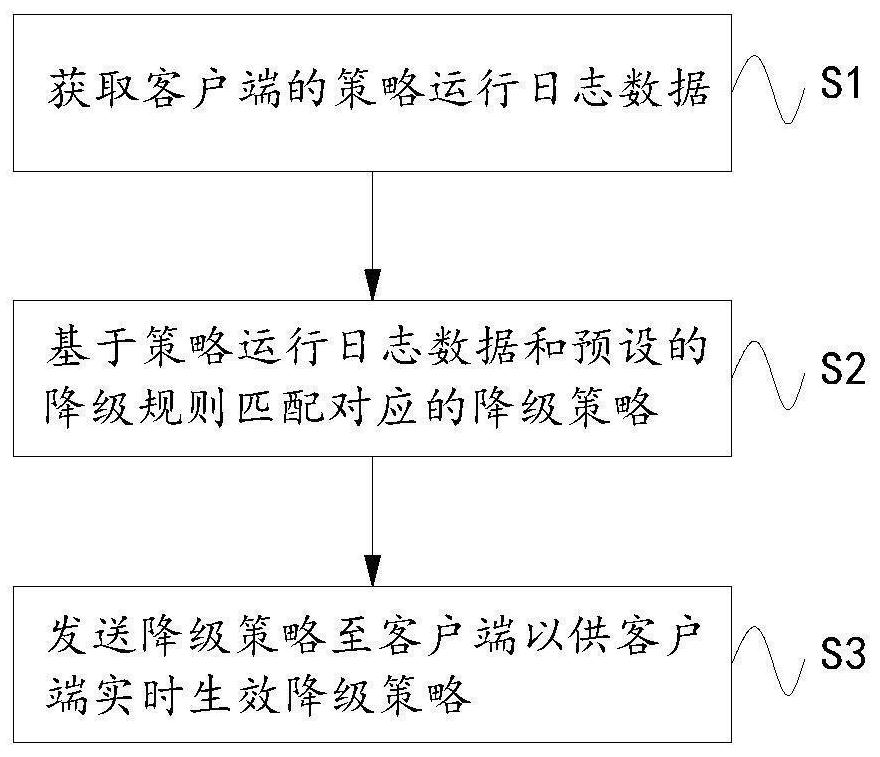
[0041] Embodiment 1: This embodiment provides a flow control method, refer to figure 1 As shown, the method includes:
[0042] S1. Obtain policy operation log data of the client.
[0043] Preferably, this step includes:
[0044] S11. Extract the policy operation log of the client in real time.
[0045] Specifically, the background includes a traffic control server and a unified monitoring platform. The unified monitoring platform extracts the policy operation logs of the client in real time.
[0046] Preferably, this step includes:
[0047] In a preferred implementation manner, the real-time extraction of the policy operation log of the client includes:
[0048] S111. Collect monitoring data of the client in real time based on Flume.
[0049] Specifically, the business system in the client outputs system operation log data, and the unified monitoring platform extracts the business system operation log data from the client through Flume as monitoring data. Flume is a rea...
Embodiment 2
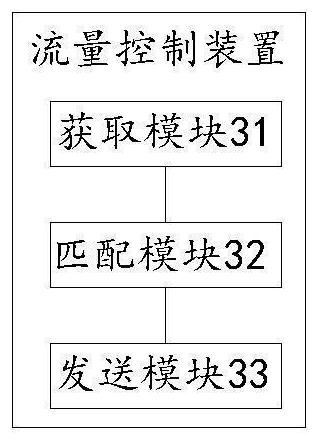
[0101] Embodiment 2: This embodiment provides a flow control device, refer to image 3 As shown, the system includes:
[0102] An acquisition module 31, configured to acquire policy operation log data of the client;
[0103]A matching module 32, configured to match the corresponding downgrading strategy based on policy operation log data and preset downgrading rules;
[0104] The sending module 33 is configured to send the downgrading policy to the client for the client to take effect of the downgrading policy in real time.
[0105] In a preferred embodiment, the acquisition module 31 includes:
[0106] An extracting unit 311, configured to extract the policy operation log of the client in real time;
[0107] The parsing and filtering unit 312 is configured to parse and filter policy operation logs to obtain policy operation log data.
[0108] More preferably, the extraction unit 311 includes:
[0109] The collection subunit 3111 is used to collect monitoring data of the ...
Embodiment 3
[0125] Embodiment 3: This embodiment provides a computer-readable storage medium on which a computer program is stored, and when the computer program is executed by a processor, any of the following steps is implemented:
[0126] Obtain the policy operation log data of the client;
[0127] matching the corresponding downgrading policy based on the policy operation log data and the preset downgrading rule;
[0128] Sending the downgrading policy to the client for the client to take effect of the downgrading policy in real time.
[0129] As a preferred implementation mode, in the embodiment of the present invention, when the processor executes the computer program, the following steps are also implemented:
[0130] Real-time extraction of client policy operation logs;
[0131] Analyzing and filtering the policy operation log to obtain policy operation log data.
[0132] As a preferred implementation mode, in the embodiment of the present invention, when the processor executes...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com