Face spoofing detection method and system based on meta-pseudo labels and illumination invariant features
A technology of constant illumination and spoof detection, which is applied in spoof detection, biometric recognition, character and pattern recognition, etc. It can solve the problem of face spoof detection model relying on the generalization of training data, so as to improve learning ability and reduce impact , the effect of improving robustness
- Summary
- Abstract
- Description
- Claims
- Application Information
AI Technical Summary
Problems solved by technology
Method used
Image
Examples
Embodiment
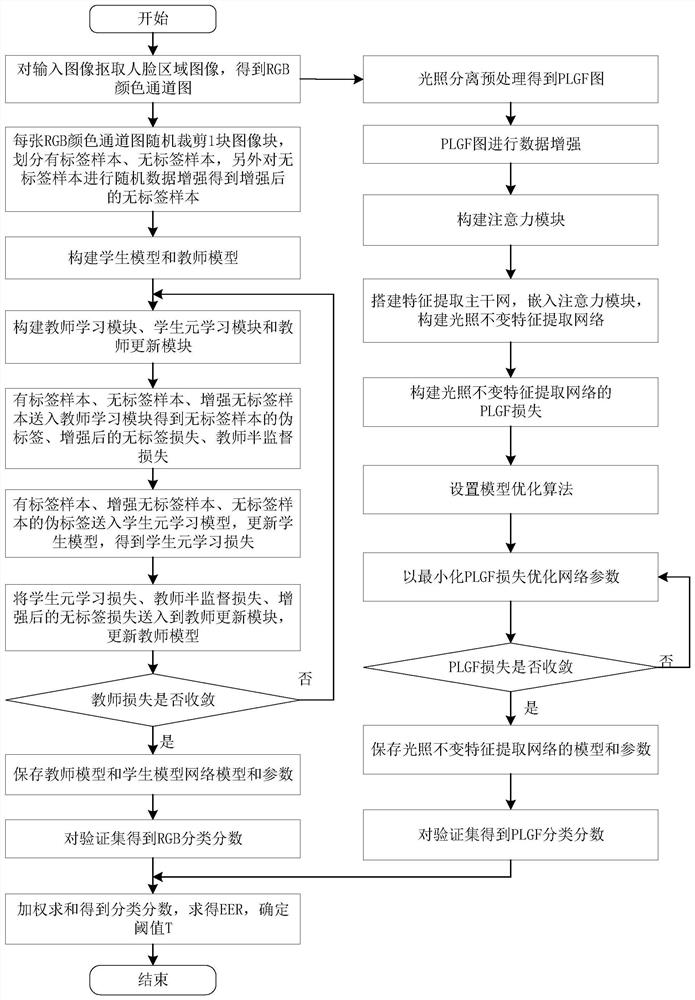
[0108] This embodiment uses the Replay-Attack, CASIA-MFSD, and MSU_MFSD living body detection data sets as examples for training and testing, and introduces the implementation process of this embodiment in detail. Among them, the Replay-Attack dataset contains 1200 videos. Using a MacBook camera with a resolution of 320×240 pixels, the real faces from 50 testers and the generated spoofed faces are collected, and the ratio of 3:3:4 It is divided into training set, verification set and test set; the CASIA-MFSD dataset contains 600 videos, which are collected from 50 The real face of the tester and the deceptive face generated accordingly are divided into a training set and a test set according to 2:3; the MSU_MFSD data set includes 280 videos, and the real faces from 35 testers are collected. The generated spoofed faces, 15 of them are used in the training set and 20 of them are used in the test set. Since the CASIA-MFSD and MSU_MFSD living body detection data sets do not inclu...
Embodiment 2
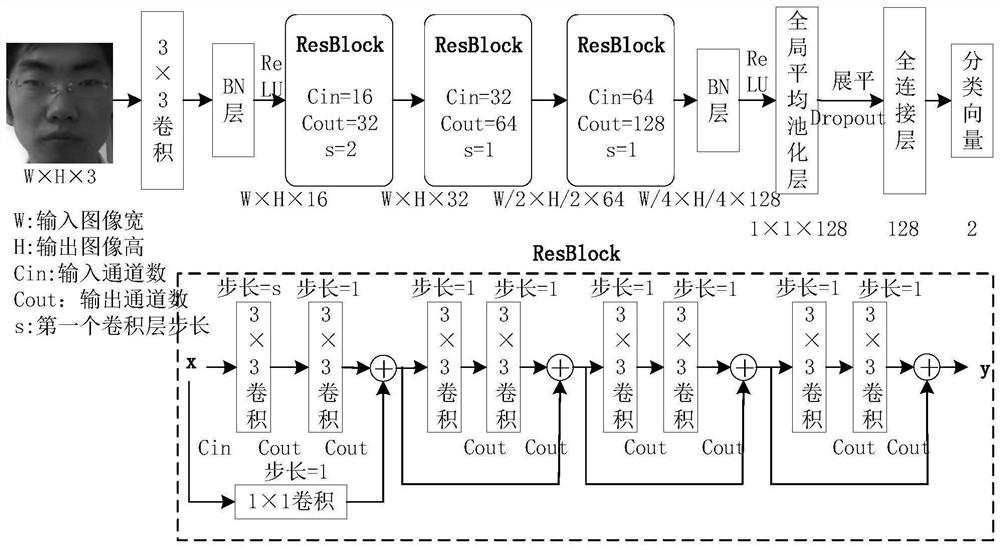
[0222] Such as Image 6 As shown, the present embodiment provides a face deception detection system based on meta-pseudo-labels and illumination invariant features, including: data preprocessing module, student model and teacher model building module, teacher learning module, student meta-learning module, teacher update module, attention module, illumination invariant feature extraction network building block, illumination invariant feature learning module, verification module and testing module;
[0223] In this embodiment, the data preprocessing module is used to extract the image of the face area to obtain the RGB color channel map, and the RGB color channel map to be trained is randomly cut out image blocks, which are divided into labeled samples and unlabeled samples. The unlabeled sample obtained by performing random data enhancement on the label sample is used as a sample for RGB branch training; the RGB color channel image to be trained is preprocessed by light separat...
PUM
 Login to View More
Login to View More Abstract
Description
Claims
Application Information
 Login to View More
Login to View More - R&D
- Intellectual Property
- Life Sciences
- Materials
- Tech Scout
- Unparalleled Data Quality
- Higher Quality Content
- 60% Fewer Hallucinations
Browse by: Latest US Patents, China's latest patents, Technical Efficacy Thesaurus, Application Domain, Technology Topic, Popular Technical Reports.
© 2025 PatSnap. All rights reserved.Legal|Privacy policy|Modern Slavery Act Transparency Statement|Sitemap|About US| Contact US: help@patsnap.com